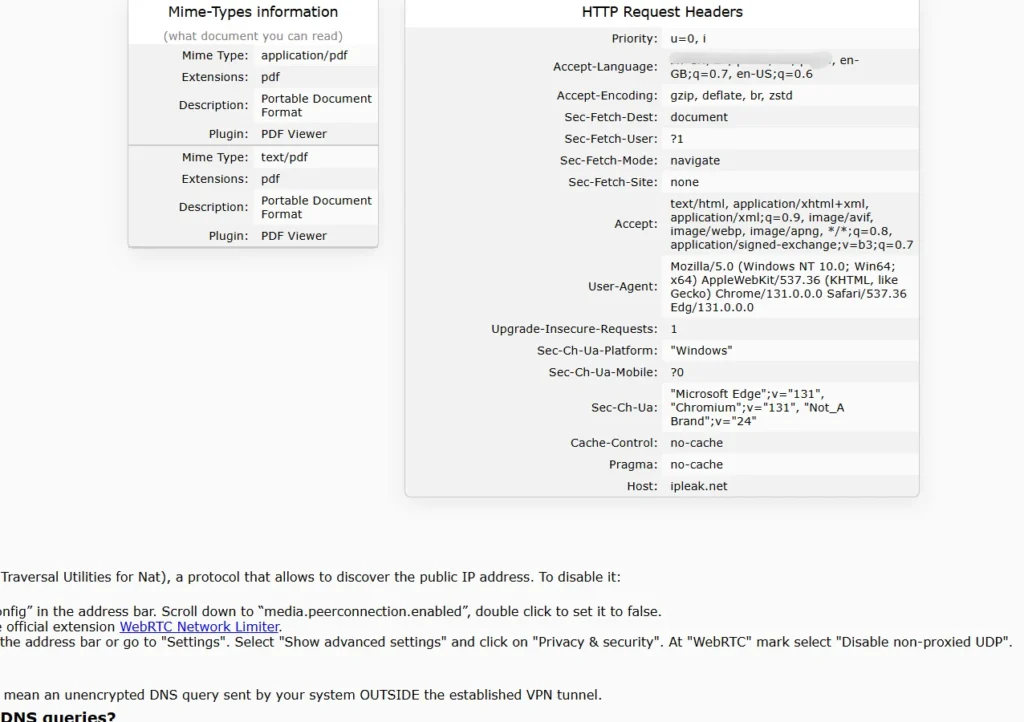
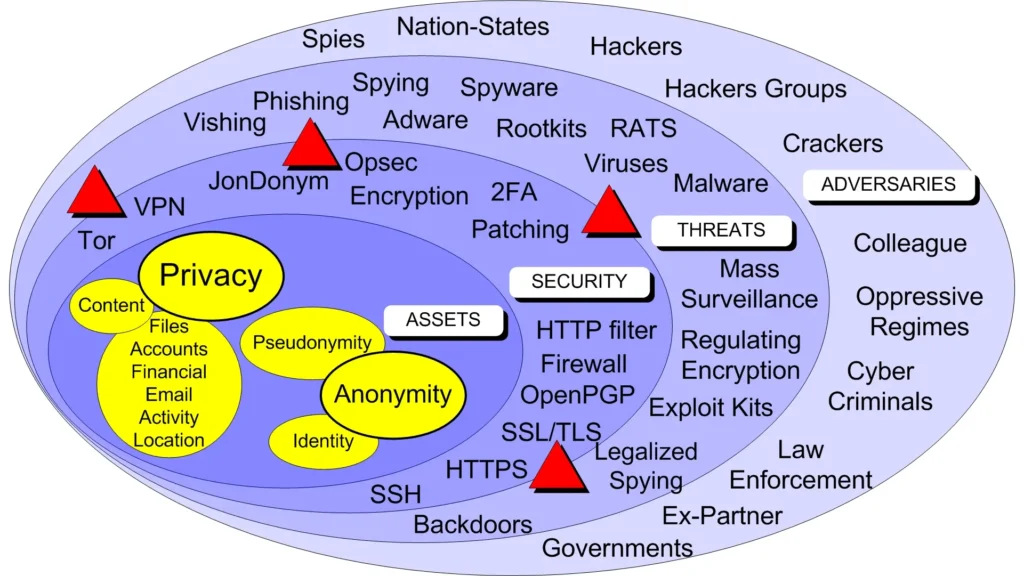
Virtual Private Networks (VPNs)
This article is to provide you with a comprehensive overview of how to use a VPN or Virtual Private Network for enhanced security and privacy protection. At the same time you will learn about the best protocols and encryption methods associated with VPN use and why, the weaknesses of VPNs and how to mitigate them. ...