Table of Contents
By understanding how browsers can be targeted and implementing these strategies, you can significantly improve your browser’s security and privacy. The following sections will delve deeper into specific techniques for hardening Firefox.
- Understanding Browser Vulnerabilities:
- Learn about common techniques used to hack browsers and the various attack vectors that can be exploited.
- Mitigation Strategies:
- Discover methods to mitigate these vulnerabilities and protect your browser from potential threats.
- Deep Dive into Firefox:
- This section will provide an in-depth look at the Firefox browser, exploring its features and how to harden it for better security.
Key Techniques to Consider
- Regular Updates:
- Always ensure that your browser is up-to-date to protect against known vulnerabilities.
- Security Extensions:
- Use security-focused extensions that enhance privacy and security, such as ad blockers and script blockers.
- Privacy Settings:
- Adjust your browser’s privacy settings to limit tracking and data collection by websites.
- Sandboxing Features:
- Take advantage of browser sandboxing features to isolate processes and reduce the risk of exploitation.
- Disable Unnecessary Features:
- Turn off features that you don’t use, as these can create additional vulnerabilities.
Overview of Browsers and Their Security Features
We will explore the various choices of web browsers available today, their security features, and how they can affect your overall online safety.
The Importance of Browser Security
- Browser and Extension Security:
- The security of your browser and its extensions is vital for maintaining your overall security online. Your choice of browser plays a significant role in this.
- Personality Reflection:
- Interestingly, the browser you choose can say something about your personality. Are you a Firefox person, or do you prefer Internet Explorer (IE)?
Main Browsers Overview
- Opera:
- While Opera has a small number of vulnerabilities, it typically takes about 50 days on average to provide updates. Due to its low market share, it is a less appealing target for hackers. However, it lacks security extensions, limiting its security functionality.
- Safari:
- Apple’s Safari browser also does not support security extensions, which restricts user options for enhancing security.
- Internet Explorer (IE):
- IE has a poor security record and is known for being slow. Microsoft has even abandoned IE, making it wise for users to follow suit.
- Microsoft Edge:
- Edge is the new browser from Microsoft, designed to replace IE and comes pre-installed with Windows 10.
- Maxthon
- Maxthon is a multifunctional browser that offers various features to enhance your online experience, including cloud synchronization, ad blocking, video downloading, and privacy protection.
- Secure Browsers:
- There are several browsers designed specifically with security in mind, including:
- Aviator by White Hat Sec
- Iron Browser
- John Doe Fox, a secure version of Firefox
- Tor Browser, focused on anonymizing browsing
- Epic Privacy Browser
- Komodo Browsers: Includes the Komodo Ice Dragon (Firefox variant) and Komodo Dragon (Chromium-based).
- There are several browsers designed specifically with security in mind, including:
Main Contenders: Chrome vs. Firefox
- Google Chrome:
- Currently the most popular browser, Chrome has a high number of vulnerabilities but excels in providing quick updates (about every two weeks). It features safe browsing technology to warn users about phishing or malware sites and employs sandboxing technology to help prevent malware installation. Chrome also supports security extensions.
- Mozilla Firefox:
- Firefox has had the highest number of vulnerabilities among major browsers, but most are not critical. It offers built-in malware and phishing protection and also supports auto updates and additional security features through extensions and plugins.
Recommendations
- While technically, Chrome may be the safer option due to its quick updates and sandboxing features, I personally recommend Firefox. The reason being, Google’s business model relies heavily on user tracking for advertisements, which creates a conflict of interest regarding privacy. In contrast, Mozilla, the organization behind Firefox, does not have such a business model and hence has no need for tracking users.
- For optimal security, I advise using Firefox with specific configurations and security extensions.
Additional Note on Debian Users
- If you are using Debian or Debian-based distributions, consider the iSweasel browser, a fork of Firefox that comes with these distributions. iSweasel retains many of Firefox’s features but utilizes system libraries for updates, aligning with the Debian update system. This way, security updates for system binaries will also apply to iSweasel without waiting for updates in the Firefox release cycle.
- However, be aware that iSweasel may take one or two days for the Debian team to merge changes from Mozilla releases, and some extensions may not work with iSweasel as they do with Firefox. You can still install Firefox on Debian if preferred.
Reducing Your Browser’s Attack Surface
We will discuss effective strategies to minimize the attack surface of your browser, ensuring enhanced security.
Key Strategies for Reducing Attack Surface
- Remove Unused Components:
- Disable, remove, or uninstall anything you don’t actively use. If it’s not installed, it cannot be exploited, which helps reduce your attack surface.
- Focus on Internet-Interfacing Tools:
- Pay particular attention to tools that interact directly with the internet, such as browsers, plugins, and extensions.
Priority Components to Manage
- Java, Flash, and Silverlight:
- Top Priority: Remove, disable, or limit the use of Java, Flash, and Silverlight. These tools frequently have vulnerabilities, and if you are slow on patches, you risk being exploited.
- Browser Plugins and Extensions:
- Particularly for browsers like Firefox, take a look at the most exploited applications in exploit kits. Java and Flash are frequently targeted.
Understanding the Technologies
- Java:
- Java is used to create applications that run in browsers or on virtual machines. However, the usage is minimal, with less than 0.1% of websites utilizing it.
- Flash:
- Flash is used for videos and animations but has been largely replaced by HTML5, which is safer. About 10% of websites still use Flash, so if you encounter one, consider urging them to upgrade.
- Silverlight:
- Similar to Flash but has an even smaller usage base (around 0.1%). It provides applications within the browser.
- JavaScript:
- JavaScript is essential for most websites, used by about 90% of sites. However, it can also be a security risk as it is commonly exploited by malicious actors.
Recommendations for JavaScript Management
- QuickJava Plugin: This plugin allows you to quickly enable and disable JavaScript, Flash, and Java. It’s a useful tool to manage risks associated with these technologies.
Managing Browser Plugins in Firefox
- Accessing Plugins:
- Go to your add-ons and select the Plugins tab to manage your installed plugins.
- Disabling Unsafe Plugins:
- Change settings for Java and Silverlight to “Never Activate” to avoid potential vulnerabilities.
- Managing Extensions:
- Remove any extensions you no longer use.
- Handling PDF Files:
- Change the PDF settings to “Always Ask” or “Save to Disk” to avoid exploits from PDF files.
- Refreshing Firefox:
- If your browser is cluttered with plugins and extensions, you can refresh Firefox to return to a clean state.
How Browsers Get Hacked: A Demonstration
I will demonstrate how browsers can be compromised, providing insight into the methods attackers may use and the risks involved.
Setting the Scene
- Environment Setup:
- We are using the latest version of Firefox, fully updated on Windows 7, with no known exploits available.
- The browser is equipped with Flash, JavaScript, Java, and Silverlight.
- Objective:
- As an attacker, my goal is to execute a payload within this browser.
Attack Vector Overview
- Delivery Methods:
- I could embed JavaScript in an email and send it to you. If your email client executes scripts, I could gain access.
- Alternatively, I could exploit vulnerabilities on websites you visit (Cross-Site Scripting, or XSS vulnerabilities).
- I might purchase an ad from an ad network to embed my script, or send you a link to my malicious site.
- Automation vs. Manual Hacking:
- While manual hacks are possible, most attacks are automated to maximize victim capture.
Demonstration of a Manual Hack
- Embedded Script:
- I have embedded a script on a site that appears legitimate. By using tools like Firebug, I can locate and manipulate this script to reach out to my server.
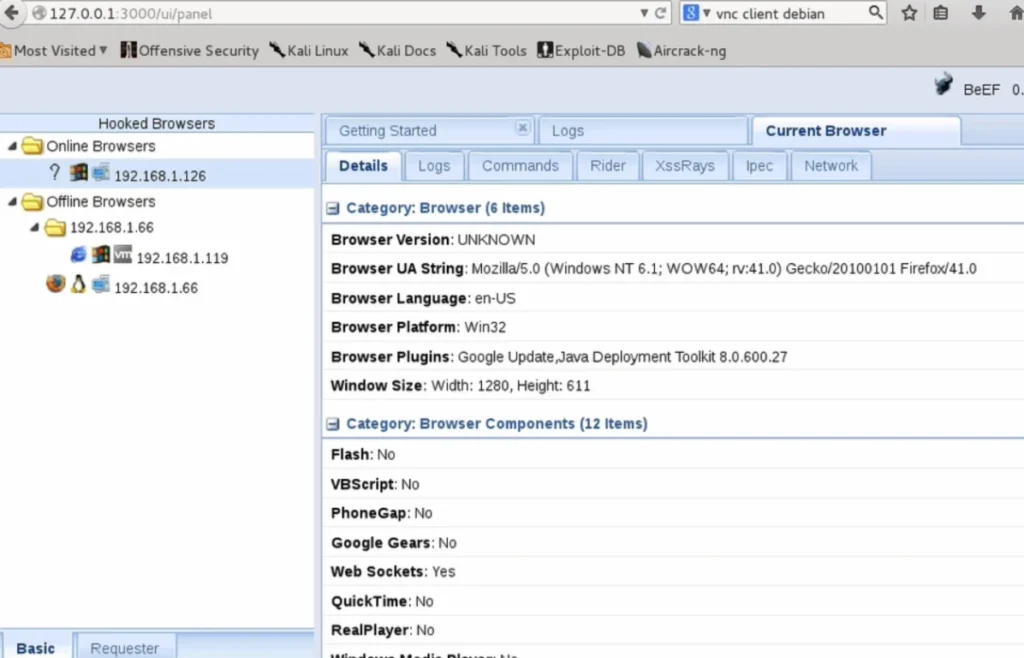
- Pen Testing Tools:
- I’ll utilize Kali Linux, specifically the Metasploit framework and the Browser Exploitation Framework (BEEF) designed for browser exploitation.
Information Gathering
- Initial Connection:
- Once the script is executed, I can see your browser’s details, including OS and installed plugins. This information helps me understand your vulnerabilities.
- Exploiting JavaScript:
- I can use social engineering techniques to display fake notifications that mimic legitimate browser extensions, tricking you into executing malicious code.
Credential Theft Demonstration
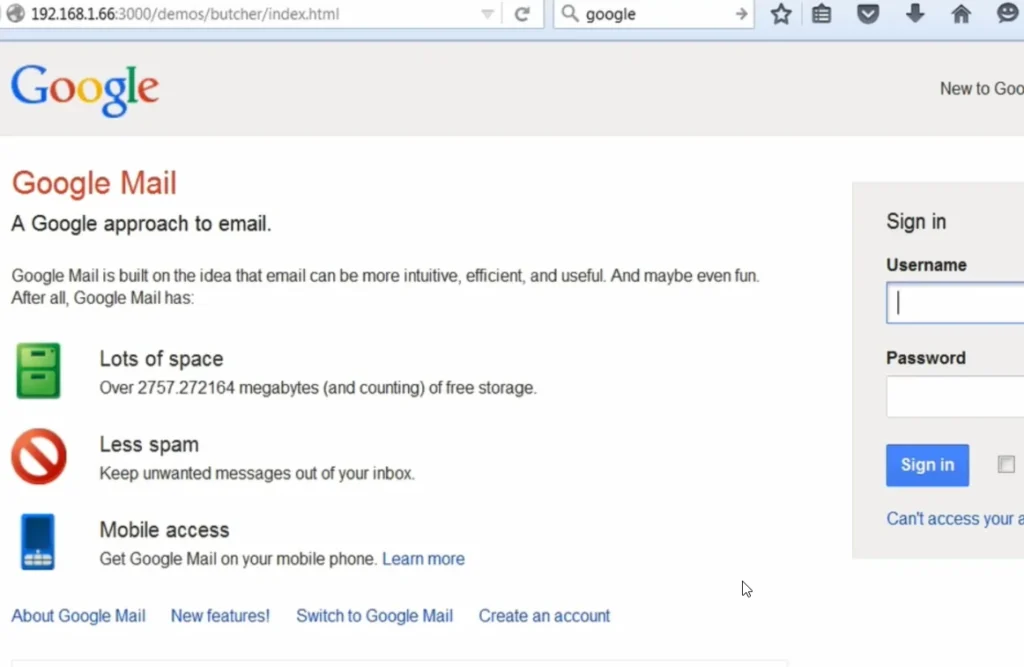
- Fake Login Pages:
- I can create fake login forms for Facebook or Google. Any credentials entered here will be sent directly to me, unencrypted.
Exploiting Vulnerabilities
- Java Exploit:
- If there are available exploits for vulnerabilities in Java, Flash, or Silverlight, I can gain more control over your system. By exploiting a Java vulnerability, I could create a reverse shell to your machine.
- Accessing Your System:
- From this reverse shell, I can execute commands as the current user, potentially gaining further access if the user account has administrative privileges.
Remote Access via VNC
- Using VNC:
- With a reverse shell, I can implement tools like VNC, allowing me to control your desktop remotely, remaining hidden from the user.
Summary
- Understanding the Risks:
- This demonstration illustrates the potential for harm when even a small script runs in your browser. Without proper patches or defenses, attackers can create reverse shells and gain full control of your machine.
- Importance of Security Measures:
- It is crucial to stay updated and aware of security vulnerabilities in the tools we use daily to mitigate these risks.
Protecting Against Hacking and Tracking: Isolation and Compartmentalization
For optimal security, consider physical isolation through different devices or at least use virtualization tools like VMs to prevent cross-contamination between different browsing contexts.
Importance of Isolation and Compartmentalization
- Protection Against Common Threats:
- Isolation and compartmentalization help mitigate risks faced by all internet users, as everyone shares common online threats.
- Beyond Browser Configuration:
- Relying solely on browser settings, hardening features, or privacy-focused plugins is insufficient. The threat landscape is constantly evolving, necessitating a layered defense strategy to withstand zero-day attacks.
Implementing Isolation and Compartmentalization
- Sandboxing and Virtual Machines:
- Consider utilizing sandboxing techniques or running your browser in a virtual machine (VM) to enhance security. Tools like AppArmor, Firejail, and Sandboxie can help in this regard.
- Combined Approaches:
- Using both a VM and a sandbox can substantially reduce the risk of browser attacks and isolate the browser from the operating system.
- Cloud Browsers:
- As discussed previously, cloud browsers can be an option if concerned about hackers and malware. By moving the browser to a remote server, you experience a virtual browsing environment, making it much harder for attackers to access your local machine.
Risks and Limitations
- Information Exposure:
- While cloud browsers protect against direct hacking attempts, they could still capture sensitive information entered during your browsing session.
- Privacy Concerns:
- Be aware that cloud service providers may log the sites you visit, raising privacy concerns.
- Browser in a Box:
- This tool combines a browser application with a preconfigured virtual machine, effectively isolating your browsing activities. However, ensure it is up-to-date before use.
Browser Profiles for Isolation
- Using Firefox Profiles:
- Firefox allows users to create separate profiles, each with its own configuration. This can be useful for isolating different browsing contexts.
- Managing Profiles:
- You can manage profiles using command-line switches when launching Firefox (e.g., using
Pto access the profile manager). Here, you can create, delete, and switch between profiles.
- You can manage profiles using command-line switches when launching Firefox (e.g., using
- Profile Management Plugins:
- Consider using plugins like Profile Switcher or Switchy for improved management of Firefox profiles.
Contextual Identity Separation
- Draft Proposal for Contextual Identities:
- Firefox is working on implementing contextual identities, which could enhance isolation and compartmentalization efforts, similar to the cube container concept.
Enhancing Privacy and Security
- Tab Management Plugins:
- Certain plugins allow you to manage tabs in sandboxes, enabling multiple logins to the same site without them interfering with each other.
- Portable Applications:
- Using portable versions of Firefox can help maintain separate contextual identities, allowing for hidden browsing sessions on encrypted drives.
Firefox Security and Privacy Features
Firefox is known for providing excellent security and privacy features. Unlike Chrome, Firefox allows security extensions to make low-level changes essential for enhancing your security. Although Chrome has superior sandboxing, it is developed by Google, which has a business model centered around tracking users.
Key Features of Firefox
- Do Not Track (DNT) Feature:
- When enabled, Firefox adds a DNT flag in the HTTP headers when you visit websites, signaling them not to track you. However, websites are not obligated to comply with this request, so results may vary.
- Tracking Protection in Private Windows:
- Firefox provides tracking protection that can be enabled in private windows. It uses services like disconnect.me to block requests from known tracking domains.
- History Management Options:
- Users can choose from three history options:
- Remember History: Records all browsing activity, allowing full tracking.
- Never Remember History: Stops most tracking by preventing the storage of cookies and other data.
- Use Custom Settings for History: Allows for exceptions for certain sites while blocking third-party cookies.
- Users can choose from three history options:
- Private Browsing:
- Firefox has a private browsing mode that operates under the “never remember history” setting. This means it won’t save history, searches, cookies, or temporary files.
Security Settings in Firefox
- Add-on Installation Alerts:
- Users can enable alerts for when sites attempt to install add-ons. This is crucial for preventing unwanted installations.
- Block Reported Attack Sites:
- This feature helps protect against websites that might attempt to install malware.
- Block Reported Web Forgeries:
- Similar to attack site protection, this feature protects against phishing attacks.
- Google Safe Browsing:
- Firefox uses the Google Safe Browsing service to check URLs against a list of known malicious sites. Users should be aware that using this service could compromise privacy, as Google may track users’ browsing habits.
- Password Management:
- Firefox can save usernames and passwords, but using external password managers is recommended for better security.
Firefox offers strong security and privacy features that make it a good choice for users concerned about online tracking. By utilizing its built-in options and being aware of the potential privacy implications of certain features, users can better protect themselves while browsing.
Blocking Undesirable Content with uBlock Origin
We will explore methods to block unwanted malware, advertisements, phishing links, and tracking techniques using HTTP filtering and script blocking. These techniques enhance your privacy and security while improving your browsing speed by reducing unnecessary content.
Importance of HTTP Filtering and Script Blocking
- Enhanced Security:
- HTTP filters can block malware and phishing attempts, protecting your personal information.
- Improved Browsing Experience:
- By filtering out unwanted content, your browser can operate more efficiently, leading to faster loading times.
Recommended Extensions for Full Protection
While Firefox offers built-in protections like Google Safe Browsing and disconnect.me tracking protection, additional extensions can further enhance your security.
- uBlock Origin:
- This is the primary extension recommended for all users, regardless of technical expertise. It is not to be confused with the original uBlock.
- Key Features:
- User Control: uBlock Origin allows users to decide what web content is acceptable.
- Community-Driven: The extension is developed voluntarily, without corporate influence, ensuring unbiased ad-blocking.
- Lightweight: It consumes less memory and CPU compared to other extensions.
Using uBlock Origin
- Installation & Setup:
- Always install extensions in a test environment first to avoid issues with your main browsing profile.
- Basic Functionality:
- When visiting sites like Forbes.com, you can see how many objects have been blocked. For example, it might block 31 objects, which represents 15% of the content.
- Logging Requests:
- uBlock Origin includes a logger to view every request and see what has been blocked based on the rules applied.
- Advanced Features:
- Users can enable advanced mode from the dashboard, which gives more detailed control over what gets blocked.
- Preventing WebRTC Leaks:
- It’s recommended to prevent WebRTC to protect your real IP address when using VPNs.
Configuring Filters
- Filter Lists:
- uBlock Origin allows you to manage various filter lists, including third-party filters that can be updated regularly.
- Resource Management:
- Users can monitor memory usage with
about:memoryto manage filters based on resource consumption.
- Users can monitor memory usage with
- Personalized Filters:
- You can create your own filters to block specific content that you find undesirable.
Modes for Blocking Content
uBlock Origin provides several modes for blocking content:
- Easy Mode:
- Uses basic uBlock filters and is suitable for most users.
- Medium Mode:
- Blocks third-party scripts and frames globally, providing more security while still allowing website functionality.
- Hard Mode:
- A stricter approach that blocks more content, ideal for users who want maximum protection.
- Nightmare Mode:
- Blocks nearly everything except the main document. For granular control, other tools like U-Matrix are recommended.
uBlock Origin is a highly effective tool for improving your online privacy and security. By spending some time customizing it, you can block unwanted tracking from sites like Google or Twitter while allowing trusted sites. The filters also protect against ads, malware, and phishing attempts, making it a necessary addition to your browsing toolkit.
Introducing U-Matrix for Enhanced HTTP Filtering
U-Matrix is another extension designed for HTTP filtering, ad blocking, and tracking prevention, created by Raymond Hill, the same developer behind uBlock Origin. This tool is geared towards more technically inclined users and can be used alongside uBlock Origin, although there is some overlap in functionality.
Key Features of U-Matrix
- Matrix-Based Firewall:
- U-Matrix acts as a point-and-click matrix-based firewall that enhances privacy while allowing granular control over what content is loaded by your browser.
- User Agent and Referrer Spoofing:
- Users can spoof their user agent and referrer, allowing them to appear as different browsers or operating systems. This helps to protect privacy by not revealing your browsing origin.
- Strict HTTPS Enforcement:
- U-Matrix can enforce the use of HTTPS when available, ensuring a secure connection.
- Customizable Filters:
- Users can configure various filters to block elements such as cookies, images, scripts, and more, according to their preferences.
Using U-Matrix
- Installation and Setup:
- Just like with uBlock Origin, you will need to spend some time configuring U-Matrix to suit your browsing habits.
- Scope Configuration:
- The scope determines what elements are affected by the filters. For example, setting the scope to “star” means all sites are affected, while a specific domain like Forbes would apply only to that website.
- Visibility of Blocked Elements:
- By enabling certain scripts, you can see how websites function and identify which elements are causing issues. For instance, if scripts are blocked, the site may not load correctly.
- Logger Functionality:
- U-Matrix includes a logging feature similar to uBlock Origin, enabling users to see which requests have been blocked.
Privacy and Security Settings
- Cookie Management:
- Users have the option to delete cookies from known bad URLs, which can help enhance privacy.
- Session Cookies:
- Similar to the “never remember history” feature in Firefox, U-Matrix allows users to delete session cookies to prevent tracking.
- Host Files and Bad Domains:
- U-Matrix automatically updates lists of bad domains, ensuring ongoing protection against known tracking and advertising threats.
Important Considerations
- Data Persistence:
- Be aware that extensions like U-Matrix store settings related to the sites you visit. This can lead to potential leakage of information about your browsing habits.
- Complex Customization:
- U-Matrix requires a greater degree of customization compared to other extensions. While it provides powerful tools for those willing to invest the time, it may not be suitable for casual users.
U-Matrix is an excellent tool for users who want detailed control over their browsing experience. With its advanced privacy features and matrix-based filtering, it can significantly enhance your online security. However, it does require technical knowledge and careful configuration to make the most of its capabilities.
Overview of Privacy-Focused Browser Extensions
We will discuss several privacy-focused browser extensions that can be used to enhance your online security and privacy. These include Disconnect Private Browser, Ghostery, and Request Policy. Each extension has its own features and limitations, making them suitable for different user needs.
Disconnect Private Browser
- Basic Features:
- Disconnect Private Browser is an open-source and free alternative to uBlock Origin, designed for non-technical users.
- It is relatively easy to configure, reducing the chances of incorrect settings.
- However, it does not possess the extensive options and power that uBlock Origin provides for rigorous privacy and security.
- Functionality:
- It blocks privacy-invasive ads and objects that could be responsible for distributing malware.
- However, it may not block ad tracking sites that comply with the Do Not Track (DNT) standard set by the Electronic Frontier Foundation (EFF).
- Granularity:
- While it offers a more user-friendly interface, it lacks the advanced features found in uBlock Origin. Users can view blocked content but still miss out on some functionalities.
Ghostery
- User-Friendly Interface:
- Similar in operation to uBlock Origin, Ghostery offers an easy-to-understand interface with good features and advanced options.
- Ad and Tracker Blocking:
- Ghostery identifies advertising objects and allows users to enable or disable tracking based on their preferences.
- However, it is important to note that Ghostery was acquired by an ad company and is no longer open-source, raising potential privacy concerns.
- Data Practices:
- Ghostery claims to sell user data without personal information. Still, this practice can be unsettling as it is not verifiable.
- Comparison with uBlock:
- Ghostery does not provide any additional benefits over uBlock Origin, and due to its questionable business model, it is generally regarded as an inferior option.
Request Policy
- Core Functionality:
- Request Policy functions differently from uBlock Origin by blocking all cross-site requests unless explicitly allowed by the user.
- This feature is beneficial for preventing unwanted connections to third parties and protecting against cross-site request forgery attacks.
- User Experience:
- However, this extension may be intimidating for non-technical users who might not understand the implications of blocking cross-site requests.
- It operates similarly to U-Matrix, and while it has its benefits, it may not be necessary if you’re already using uBlock Origin and U-Matrix together.
- Usage with Sites:
- For websites like Forbes, blocking cross-site requests may lead to some content not loading correctly, such as images served from external domains.
While all these extensions provide varying levels of protection and features, it is crucial to choose the ones that best fit your needs for privacy and control. For most users, uBlock Origin remains the primary choice due to its comprehensive filtering capabilities and open-source nature. Other options like Disconnect, Ghostery, and Request Policy may offer additional features but often come with drawbacks.
Overview of Various Ad Blockers and Privacy Tools
We will discuss several popular ad blockers and privacy tools, including Adblock Plus (ABP), Privacy Badger, and Web of Trust (WOT). Each of these tools has distinct features, benefits, and limitations that cater to different user needs regarding online privacy and security.
Adblock Plus (ABP)
- Basic Features:
- Adblock Plus is a well-known and powerful ad blocker that is widely used. However, it displays “acceptable ads” by default, which contradicts its primary purpose of blocking unwanted ads.
- User Interface:
- The interface allows users to open blockable items, where they can choose what to block. However, it may not be as intuitive or powerful as uBlock Origin for advanced users.
- Configuration:
- Designed for non-technical users, ABP is more of an “install and forget” type of plugin, making it easier for less tech-savvy individuals to use.
- Users can add custom filters and manage filters like the EasyList, which is already included in uBlock Origin.
- Performance:
- Reports indicate that Adblock Plus is slower than uBlock Origin and uses more system resources. Although changes have been made to improve its speed, it still lags behind.
- Conclusion:
- Overall, Adblock Plus offers limited configurability and does not provide significant advantages over uBlock Origin, making it less necessary for users already using uBlock.
Privacy Badger
- Overview:
- Developed by the Electronic Frontier Foundation (EFF), Privacy Badger is an HTTP filter designed to block unwanted ads and malware while focusing on user privacy.
- Functionality:
- Privacy Badger automatically analyzes user traffic and identifies tracking behavior without requiring user configuration. It blocks third-party ads while allowing first-party ads.
- Privacy Focus:
- The goal is to prevent non-consensual tracking rather than just blocking annoying ads. However, it is not capable of distinguishing between good and bad ads concerning potential malware.
- User Experience:
- Privacy Badger is suitable for non-technical users and provides a simple way to enhance privacy without much setup. The settings allow for whitelisting and adjusting permissions.
- Conclusion:
- Overall, while Privacy Badger is a good privacy tool, it doesn’t offer substantial benefits over uBlock Origin and lacks its power.
Web of Trust (WOT)
- Basic Features:
- WOT is a plugin that informs users about the trustworthiness of websites based on community contributions, indicating whether sites are safe for children as well.
- Color-Coded Ratings:
- When visiting a website, users see a color-coded circle indicating its trust level (green for trusted, yellow for cautious, red for threats, and gray for unknown).
- This system also appears in search results, alerting users about potential risks.
- Privacy Concerns:
- WOT requires constant communication with its servers to provide real-time trust ratings, raising potential privacy concerns.
- Limitations:
- Security-wise, WOT has limited effectiveness as it may not quickly update its list of bad links. It may be more useful for well-known bad sites but is less effective for newly created phishing or malware sites.
- Conclusion:
- While WOT can provide some level of security, its reliance on community-sourced data and constant server communication may not be ideal for privacy-conscious users.
Overall Conclusion
When considering ad blockers and privacy tools, users should evaluate their specific needs and preferences. Tools like uBlock Origin are generally preferred for their comprehensive filtering capabilities and configurability. Other options like Adblock Plus, Privacy Badger, and WOT may offer additional features but often come with drawbacks, making them less necessary for users already employing robust solutions like uBlock.
Overview of NoScript Firefox Extension
NoScript extension for Firefox, which is a powerful security tool designed to enhance your browsing safety by controlling what scripts run on the websites you visit.
Key Features of NoScript
- Security Mechanism:
- NoScript allows active content to run only from trusted sites, significantly reducing risks from cross-site scripting (XSS) attacks and clickjacking.
- It effectively locks down the functionality of scripts and executable content, focusing primarily on JavaScript, which is a common target for security breaches.
- Integration with Tor Browser:
- NoScript is the main extension used by the Tor browser, providing necessary restrictions on browser functionality to enhance user privacy.
- Performance Improvement:
- By blocking scripts, NoScript can improve website loading times, as it prevents the downloading of large scripts and other potentially harmful content.
- Default Blocking:
- By default, NoScript blocks all scripts from all domains, requiring users to enable them selectively for sites they trust.
User Interface and Functionality
- Blocking Status:
- When you visit a site like Forbes, NoScript will display a message indicating how many scripts and objects have been blocked. Users can view the blocked domains and manage permissions accordingly.
- Options for Permissions:
- Users can temporarily enable scripts, permanently untrust domains, or allow certain scripts to run. This flexibility helps manage which sites can execute scripts while maintaining control over privacy.
- Comprehensive Control:
- NoScript allows users to disable Java, Flash, Silverlight, and other plugins, giving full control over what content can run in the browser.
Considerations for Use
- Usability vs. Security:
- While NoScript provides a high level of security, it comes at the cost of usability. Many websites rely on JavaScript for their functionality, meaning that blocking all scripts by default can lead to broken sites and a frustrating browsing experience.
- Finding a Balance:
- It is essential to find a balance between security and usability. Users may find themselves frequently enabling scripts to get websites to function, which can detract from the overall security benefits that NoScript offers.
- Alternative Solutions:
- Tools like uBlock Origin and UMatrix also provide script-blocking capabilities while maintaining a more user-friendly experience, making them suitable for everyday use.
NoScript is an excellent tool for users who want to lock down their browser completely and are willing to sacrifice some usability for increased security. It is particularly beneficial for creating a secure browsing profile but may be burdensome for general use due to the constant need to manage script permissions. Users are encouraged to explore their options and find the best setup according to their individual needs for both security and usability.
Overview of the Policeman Add-in
We will explore the Policeman add-in, an extension that enhances browsing security by controlling which types of content can be loaded from websites.
Key Features of Policeman
- Purpose:
- The Policeman add-in serves a similar purpose to Request Policy and NoScript but offers additional flexibility by allowing users to set rules based on content type.
- Content Type Control:
- Users can customize which types of content they want to allow or block, including images, media, styles, scripts, objects, and frames. This means you can permit certain types of content while blocking others for specific sites.
- Mini Language for Advanced Rules:
- Policeman features a mini programming language that allows users to write complex rules for content management, giving more control over browsing behavior.
- Blacklist Functionality:
- It can be configured to act as a blacklist, enabling users to prevent certain domains from loading any content.
User Experience
- Example in Action:
- When visiting a site like Forbes, you may notice that almost nothing loads initially. This is due to the strict blocking policies of Policeman.
- If you want to allow images from a specific domain (like Forbes), you can easily add that domain and specify which types of content to allow.
- Interface and Preferences:
- Policeman has a user-friendly interface for managing settings, allowing you to set advanced rules and tweak permissions based on your browsing needs.
- Comparison with Other Tools:
- While Policeman is effective, tools like NoScript and uBlock Origin are seen as more intuitive and user-friendly by many users.
Additional Tools and Considerations
- VirusTotal:
- For assessing the safety of suspicious websites, users can check URLs on VirusTotal. By entering a URL, the tool provides a safety report based on multiple security vendors’ opinions.
- Tracking Protection:
- The text briefly mentions another company offering tracking protection without specific details. Users should conduct their research on such tools.
- iOS Recommendation:
- For iOS users, Purify is recommended as one of the best ad blockers available on the platform.

Impact of Ads on Download Speed
- Download Speed Analysis:
- There are statistics available regarding how ads affect download speeds on top news sites. Typically, a significant portion of page content is advertising, which can slow down the user’s browsing experience.
- Example Findings:
- In analyzing the top 50 news sites, it was found that advertising content often constitutes nearly half of the page load, with The Guardian being cited as one of the better performers.
Final Considerations on Ad Blocking
- The Balance of Ads and Accessibility:
- While users generally want to block ads, it’s important to remember that many websites rely on advertising revenue to operate. Blocking ads on sites you enjoy may lead to their closure due to loss of income.
- Trust and Support:
- Consider unblocking ads on trusted sites; however, be aware that even trusted sites can have malicious advertisements. Supporting your favorite sites through donations is a good alternative.
- Caution Against Malvertisement:
- Always be cautious, as ads can carry malware, even on reputable sites. It’s essential to strike a balance between enjoying content and maintaining security.
Understanding Browser History, Cookies, and Privacy Mitigations
Browser history, cookies, and super cookies can track your online activities, affect your privacy, and provide evidence during forensic examinations. We will also explore methods to mitigate tracking and enhance your privacy.
Tracking Mechanisms
- Cookies and Super Cookies:
- Cookies are small pieces of data stored by your browser to remember your preferences and login details. Super cookies, on the other hand, are a more persistent form of tracking that can remain even after regular cookies are deleted.
- Even if you set your browser to never store history or delete your history, certain browser plugins and extensions can still retain information that may expose your activities.
- Types of Data Collected:
- Various types of data can potentially be used to track you, including:
- Browsing history
- Search queries
- Temporary files
- Super cookies and crypto tokens
- Various types of data can potentially be used to track you, including:
Analyzing Browser Data
- Viewing Browser History:
- You can view your browsing history and cache by navigating to specific browser settings. For example, entering
about:cachein the address bar shows cached data.
- You can view your browsing history and cache by navigating to specific browser settings. For example, entering
- Memory and Disk Storage:
- It is possible to view what is stored in memory and on disk, providing insight into the data retained by your browser.
- Using a Sandbox:
- For those wanting to conduct a deeper examination of what data is stored, using a sandbox environment, like Sandboxie, allows for isolated testing of browser behavior without affecting your main operating system.
Privacy Mitigations
- Non-Persistent Operating Systems:
- The best way to avoid tracking is to use a non-persistent operating system. This ensures that no data is permanently stored during browsing.
- Options include Tails, Knoppix, Live Debian, and Hoonix Disposable VMs. Using VM snapshots allows you to revert to a clean state after use.
- Setting Browser Preferences:
- Always set your browser to never remember history and regularly delete cookies to minimize tracking.
- Use private browsing modes to ensure less data is retained during active sessions.
- Utilizing Ad Blockers:
- Tools like uBlock Origin, uMatrix, and NoScript can prevent the storage of tracking data like cookies. For example, you can configure uMatrix to block cookies from specific sites like Google.
Clearing History and Evidence Elimination
- Clearing Browsing Data:
- Browsers like Firefox allow you to clear your history and cookies via privacy settings. You can select the timeframe for which you want to clear data.
- Using Evidence Elimination Tools:
- CCleaner vs. BleachBit:
- CCleaner is available for Windows and Mac with both free and paid versions. The paid version offers features like automatic cleaning after browser shutdown.
- BleachBit is recommended for Linux users and offers similar functionality.
- Enhanced Cleaning with Extra Signatures:
- To improve cleaning efficiency, you can download the WinApp2.ini file, which adds extra software signatures to CCleaner and BleachBit. This allows for the deletion of over 2,000 additional items, including those related to Firefox.
- Configuring Deletion Methods:
- Both CCleaner and BleachBit allow you to configure how data is deleted. You can set it to perform multiple passes for more secure deletion.
By understanding how browser history, cookies, and related tracking mechanisms work, and implementing effective mitigations, you can significantly enhance your online privacy. Remember to regularly clean your browsing data and utilize privacy-focused tools to minimize your digital footprint.
Exploring Privacy Tools for Browsing
Various browser extensions and tools designed to enhance your online privacy by managing cookies and tracking mechanisms. We’ll look at BetterPrivacy, Click and Clean, Quick Java, Advanced Cookie Manager, Self-Destructing Cookies, and Decentralize.
BetterPrivacy
- Functionality:
- BetterPrivacy is an extension designed to find and delete a specific type of super cookie known as Local Shared Objects (LSOs) or Flash cookies.
- It automatically deletes Flash cookies on browser exit, helping to validate whether other methods are effectively blocking these cookies.
- Installation:
- You can download BetterPrivacy and test it to see if it detects any super cookies on your system.
Click and Clean
- Purpose:
- Click and Clean is a handy tool to delete browser history, erase temporary internet files, remove download files, cookies, and Flash LSOs.
- It enables users to delete private data quickly when Firefox closes.
- Integration:
- This extension provides quick access to Firefox’s built-in cookie cleaner and supports evidence elimination tools like CCleaner to enhance privacy.
Quick Java
- Control Over Content:
- Quick Java allows you to enable or disable Java, JavaScript, cookies, image animations, Flash, Silverlight, style sheets, and proxies directly from your toolbar.
- Users can easily switch cookies on or off for all sites visited.
Advanced Cookie Manager
- Enhanced Features:
- This tool offers more advanced features than the built-in cookie management options, enabling users to add, delete, modify, export, backup, and restore cookies.
- It provides detailed insights into cookie values, perfect for users who want more control over their cookie data.
Self-Destructing Cookies
- Functionality:
- Self-Destructing Cookies automatically deletes cookies and local storage when you close a browser tab.
- Users can customize the settings to destroy cookies upon tab closure or browser exit, or even temporarily disable the self-destruct feature.
- Usage:
- This extension offers a user-friendly interface for managing cookies on a per-tab basis.
Decentralize
- Purpose:
- Decentralize protects users from tracking by replacing requests to content delivery networks (CDNs) with local files, thus minimizing tracking across websites.
- It works well with uBlock Origin and uMatrix to enhance privacy.
- How It Works:
- By preventing requests to major CDNs like Google, Decentralize helps users maintain privacy while browsing.
- It serves local files instead of relying on potentially tracking CDNs.
Testing Your Defenses
- Super Cookie Test:
- Users can test their current defenses against super cookies using a test URL to create an Ever Cookie, checking if their privacy tools effectively prevent its creation.
- The demonstration illustrates how even after deleting history, super cookies can remain.
- Cleaning with CCleaner:
- CCleaner can be used to analyze and clean cookies, ensuring that remnants from browsing sessions are removed effectively.
By using these tools, you can significantly enhance your browsing privacy, preventing unwanted tracking and managing cookies more effectively. It’s essential to regularly test these tools to ensure they are functioning correctly and keeping your online activities secure.
Understanding HTTP Referrer and Privacy Controls
HTTP Referrer, how it tracks your online activities, and methods to control or spoof the referrer data sent from your browser.
What is HTTP Referrer?
- Definition:
- HTTP Referrer is an HTTP header that informs a website about the last page you visited before clicking a link to their site.
- Functionality:
- When you click a link (e.g., google.co.uk), your browser loads the new webpage and tells that website where you came from, effectively sharing the referrer information.
- The HTTP Referrer is also sent when loading content on a webpage, such as ads or tracking scripts, allowing advertisers to know which page you are currently viewing.
Controlling HTTP Referrer
- Referrer Spoofing:
- You can manage what referrer information is sent to websites through various methods, including browser extensions.
- Useful Plugins:
- RefControl: This extension allows you to control the HTTP referrer on a per-site basis. For example, you can choose to send the actual referrer, block it, or forge it to a different value.
- Smart Referrer: This plugin only sends referrer information when you are navigating within the same domain, providing an extra layer of privacy.
- Firefox Built-in Option:
- Firefox has a built-in feature that can disable the referrer completely. You can access this by typing
about:configinto the address bar. After acknowledging the warning, search for the relevant setting and change its value to zero to disable the referrer.
- Firefox has a built-in feature that can disable the referrer completely. You can access this by typing
- UMatrix for Spoofing:
- UMatrix, another privacy-focused tool, also has the ability to spoof referrer data. By adjusting its settings, you can control how referrer information is sent during third-party requests.
By understanding how the HTTP Referrer works and utilizing tools to control or spoof its data, you can enhance your online privacy and reduce the amount of tracking that occurs as you browse the web. It is important to take proactive steps to manage your privacy settings and protect your online identity.
Understanding Browser Fingerprinting and Privacy Controls
We’ll dive into browser fingerprinting, how it works, the various methods used for tracking, and ways to mitigate the risks associated with it.
What is Browser Fingerprinting?
- Definition:
- Browser fingerprinting is a tracking technique that collects information about your browser’s configuration, such as user agent, fonts, browser type, and add-ons, to create a unique profile of you.
- How it Works:
- When you visit a webpage, your browser sends this information voluntarily. Websites can also actively query your browser to gather more details. If the combination of this information is unique enough, it can be used to identify and track you without relying on cookies.
Fingerprinting Statistics
- Study Insights:
- According to a study by the Electronic Frontier Foundation (EFF), 83.6% of browsers that visited their testing site had a unique fingerprint, with the percentage increasing to 94.2% for those with Flash and Java enabled. This demonstrates that browser fingerprinting can effectively identify users.
Attack Vectors for Fingerprinting
- Common Methods:
- Fingerprinting methods include plugins, HTML5 Canvas image extraction, open TCP ports, and local network fingerprinting.
- For example, the plugins you have installed can significantly contribute to your uniqueness as they can be actively queried by websites.
- Demonstration:
- By visiting sites like ipleak.net, you can see how much information can be extracted from your browser, including details about plugins like Flash.
Mitigation Techniques
- Disabling JavaScript:
- Disabling JavaScript can reduce the ability of sites to enumerate your plugin information, but it does not completely eliminate the risk of tracking.
- Using Privacy Plugins:
- Tools like Quick Java can help you manage when plugins like Java or Flash are active. This can reduce the amount of information available for fingerprinting.
- Canvas Blocker:
- This add-on prevents sites from using the Canvas API for fingerprinting by blocking or faking responses.
- Random Agent Spoofer:
- This extension randomizes your user agent, allowing you to appear as different browsers at different times, further complicating attempts to track you.
The Challenge of Randomization vs. Uniformity
- Strategies:
- Strategies to combat fingerprinting include uniformity (making your browser look like many others) and randomization (frequently changing your browser profile).
- While randomization can provide some protection, striving for a uniform profile may sometimes be more effective.
- Testing Effectiveness:
- It’s important to test the effectiveness of your anti-fingerprinting measures regularly. Tools like Panopticlick can help you see how unique your browser appears to tracking scripts.
Advanced Measures and Tools
- Using the Tor Browser:
- The Tor browser is designed to offer strong fingerprint protection. However, it requires using the Tor network, which can be slower and may not be suitable for all users.
- John Doe Fox Browser:
- An alternative to Tor, this hardened browser provides a certain level of uniformity since many users share the same profile.
- Virtual Machines and Default Installs:
- Operating in a virtual machine or using a default browser installation can help achieve uniformity, which can be beneficial in reducing fingerprinting risks.
By understanding browser fingerprinting and taking proactive measures, you can significantly enhance your online privacy. It’s essential to stay informed about the latest tracking techniques and regularly test the effectiveness of your chosen privacy tools.
Browser Certificates and Encryption: Best Practices for Security, Privacy, and Anonymity
Browser uses secure connections, the importance of HTTPS, and various tools and practices to enhance your online security and privacy.

HTTPS Everywhere
- Overview:
- HTTPS Everywhere is a popular browser extension that automatically enables HTTPS encryption on websites that support it. This helps protect your data from interception and ensures a secure connection.
- Functionality:
- The extension will only connect you to supported sites using HTTPS. For example, searching for BBC will show various BBC sites that you can access securely.
- Blocking HTTP:
- You can configure the extension to block all HTTP requests. While this provides added security, it may lead to blank pages on sites that don’t support HTTPS.
SSL Observatory
- Purpose:
- SSL Observatory is a feature that sends copies of HTTPS certificates to a centralized service. This helps detect man-in-the-middle attacks and improve overall web security.
- Warnings:
- It will alert you about insecure connections or potential attacks against your browser. However, using this feature may raise privacy concerns since it communicates with an external service.
- Using with Tor:
- If you’re using Tor, you can still utilize SSL Observatory to benefit from its security features while maintaining some level of anonymity.
Forcing HTTPS
- Importance:
- It’s crucial to enforce HTTPS connections using tools like HTTPS Everywhere or similar extensions.
- Firefox Configuration:
- You can make HTTPS connections explicit in Firefox by adjusting settings. For instance, changing
browser.urlbar.trim.urlsto false allows you to see whether a site is using HTTP or HTTPS explicitly.
- You can make HTTPS connections explicit in Firefox by adjusting settings. For instance, changing
Certificate Patrol Plugin
- Functionality:
- This plugin alerts you when a website’s certificate is updated. If you revisit a site and notice a different certificate, it will notify you, allowing you to determine if the change is legitimate.
- Limitations:
- Due to frequent certificate changes by many sites (like Google), this tool might generate numerous notifications, which can be overwhelming.
Perspectives Add-on
- Overview:
- The Perspectives add-on checks HTTPS certificates against network notaries. This decentralized approach helps identify authentic server certificates by comparing them with what other users have seen.
- Community Input:
- The effectiveness of this tool improves with more users. If many users see the same certificate, it is likely to be genuine.
Windows Tools
- Certificate Scanning:
- On Windows, tools are available to scan and audit your certificates, highlighting any potentially rogue root certificates based on established trust guidelines.
- Calomel SSL Validation:
- This add-on scores the strength of SSL connections in your toolbar. It provides a visual indication of encryption strength, helping you quickly assess the security of a connection.
Cipher Suite Management
- Toggle Cipher Suite:
- This tool allows you to enable or disable specific cipher suites supported by your browser. You can make adjustments to improve security by removing weak ciphers.
- Testing with SSL Labs:
- You can test your browser’s security with SSL Labs, which will inform you about supported protocols and any vulnerabilities present, ensuring you are using strong and secure configurations.
Implementing these practices and tools will significantly enhance your browser’s security and privacy. It’s important to stay informed and regularly update your tools to protect against emerging threats while balancing privacy and usability.
Browser Hardening for Security, Privacy, and Anonymity
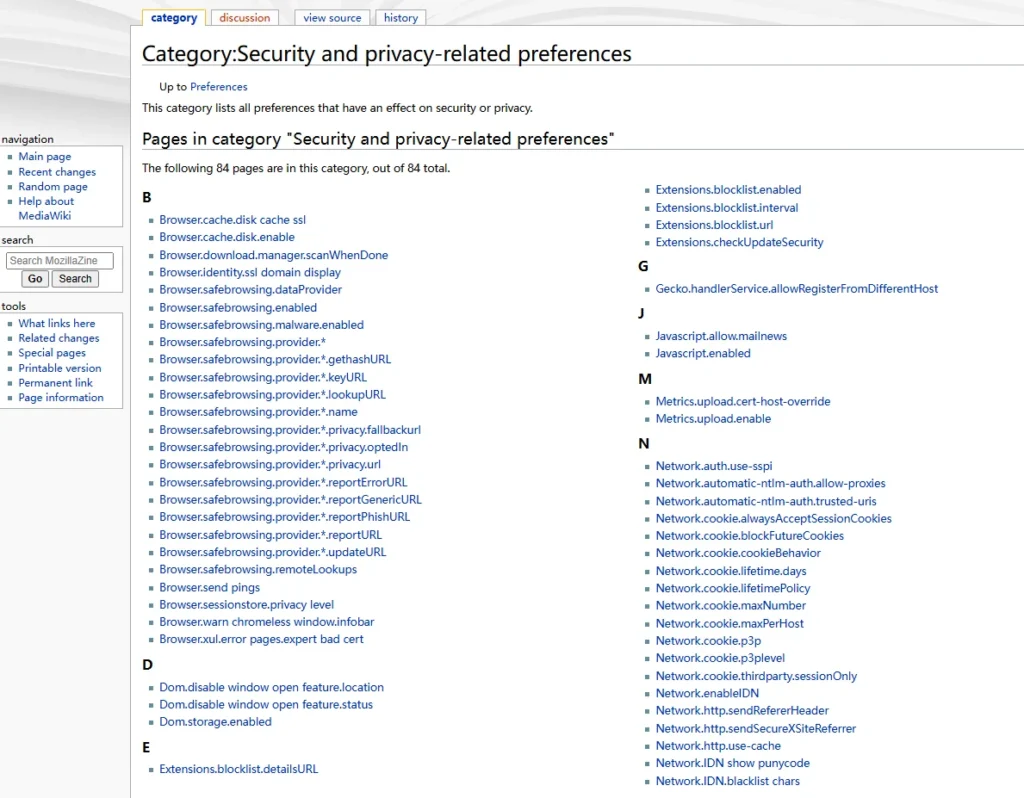
To ensure security, privacy, and anonymity while browsing, it’s essential to harden your browser beyond what standard extensions offer. Here’s a detailed approach to effectively harden your browser.
Understanding about:config
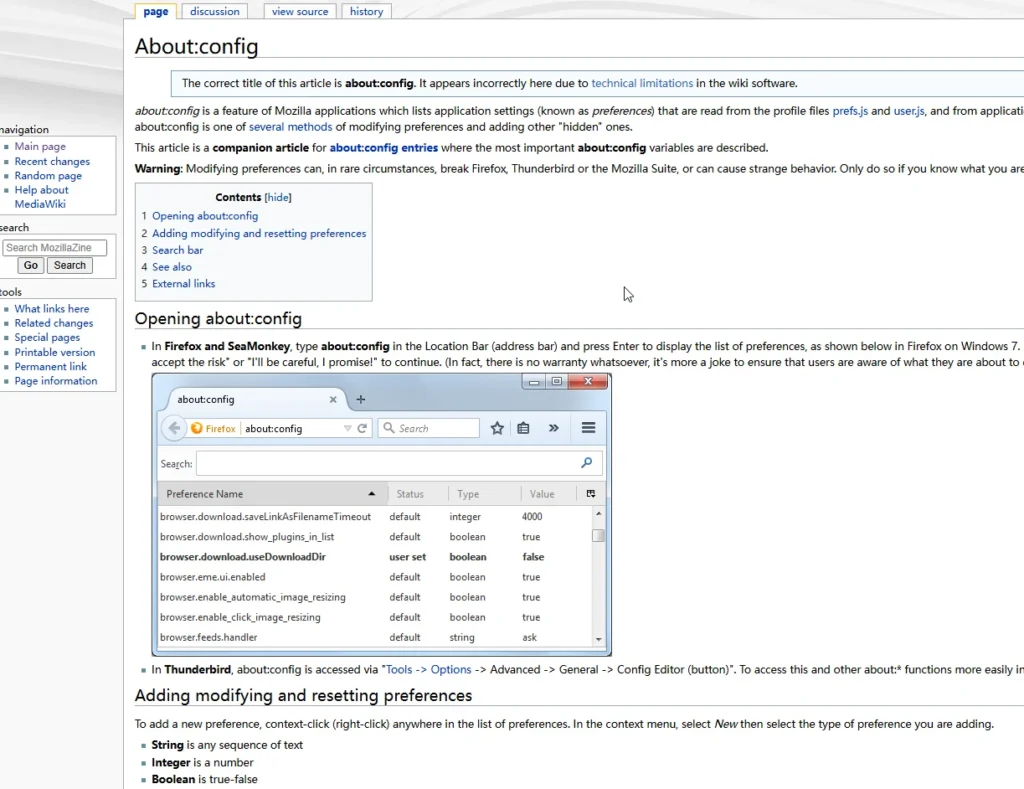
- What is
about:config?- This is a configuration interface in Firefox where advanced settings can be adjusted for enhanced security and privacy. It’s a critical area for making necessary changes.
- Resources for Learning
about:config:- There are various online resources that provide guidance on the features of
about:configand list the entries you can modify. Exploring these can help you understand how to enhance your browser settings effectively.
- There are various online resources that provide guidance on the features of
- Security and Privacy Changes:
- A comprehensive list of security and privacy-related changes can be found in
about:config, making it easier to assess what needs adjustment.
- A comprehensive list of security and privacy-related changes can be found in
Tools for Automating Browser Hardening
- Profile Creation Tool:
- This tool allows you to create a Firefox profile that can be imported into your browser as a ZIP file. It is configurable, enabling you to choose privacy and security options you prefer.
- It is advisable to test this with a new profile to avoid disrupting your existing settings.
- User.js for Firefox Hardening:
- The
user.jsfile can be placed in your Firefox profile directory to apply a set of comprehensive security and privacy configurations automatically. - This file contains settings that can enhance protection against various online threats, such as tracking and fingerprinting.
- The
Key Configuration Settings
- Tracking Prevention:
- Disable tracking features and consider blocking all cookies to minimize tracking.
- DOM Storage:
- Disabling DOM storage can help prevent supercookies, though it may cause some websites to malfunction.
- Search Engine Interaction:
- Reduce the data sent to search engines by disabling certain features, such as automatic URL completion and search suggestions.
- WebGL and Automatic Updates:
- Disable WebGL to prevent potential fingerprinting and ensure automatic updates are enabled for security patches while retaining control over privacy settings.
- Add-ons Management:
- Regularly review installed add-ons; only keep those that are necessary for your browsing experience.
Additional Tools for Hardening
- Privacy Settings GUI:
- This graphical interface allows you to easily enable and disable privacy settings, although it may not cover all configurations found in
user.js.
- This graphical interface allows you to easily enable and disable privacy settings, although it may not cover all configurations found in
- John Doe Fox Browser:
- A hardened browser designed for anonymity, which can function without routing through the Tor network if desired.
- Tor Browser:
- The Tor browser is an excellent option for anonymity and security. It is regularly updated to counteract new threats and provides a portable version for convenience.
Best Practices for Ongoing Security
- Regular Updates:
- Keep your browser, plugins, and extensions up to date to protect against vulnerabilities.
- Virtual Machines:
- Ensure that virtual machines are updated regularly, as they might not receive automatic updates while powered off.
- Trustworthy Plugins:
- Only install plugins from reputable sources, as they can introduce risks if compromised.
- Awareness of Threats:
- Stay informed about potential threats, such as techniques targeting outdated browsers.
By implementing these strategies, you can significantly improve your browser’s security, privacy, and functionality. Regularly review and adjust your settings to adapt to new threats and maintain optimal protection.
Browser Privacy, Security and Tracking test sites:
- https://privacy.net/analyzer/
- https://panopticlick.eff.org/about
- https://amiunique.org/fp
- http://ip-check.info/
- https://www.browserleaks.com/canvas
- https://ipleak.net/
- http://samy.pl/evercookie/
- http://html5test.com/
- http://browserspy.dk/
- https://thehackerblog.com/addon_scanner/
- http://www.computec.ch/projekte/browserrecon/
- http://get.webgl.org/
- https://robnyman.github.io/battery/
- http://www.filldisk.com/
- https://www.mozilla.org/en-US/plugincheck/
- https://mozilla.github.io/webrtc-landing/
Conclusion
This article delves into browser security and privacy concerns, offering techniques to harden the Firefox browser. It covers understanding browser vulnerabilities, mitigation strategies, regular updates, security extensions, privacy settings, sandboxing features, and disabling unnecessary features. The article compares the security of different browsers, favoring Firefox for its privacy protections over Chrome.
It discusses reducing the browser attack surface, managing plugins like Java, Flash, and Silverlight, and demonstrates how browsers can be compromised by hackers. Finally, it provides recommendations for using tools like uBlock Origin and U-Matrix to block unwanted content and enhance privacy. By implementing these strategies, users can significantly improve their online privacy and security.


