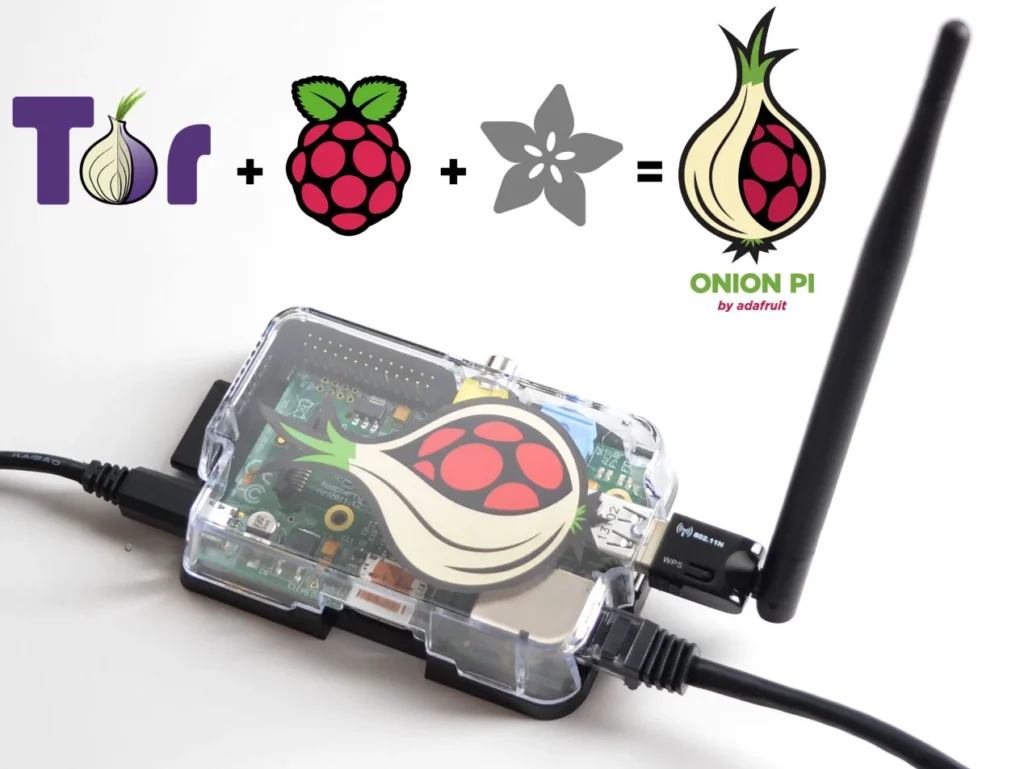
VPN and Tor Routers
By effectively utilizing both virtual and hardware routers, along with Tor and VPNs, users can significantly enhance their security, privacy, and anonymity. These tools provide essential protection against various cyber threats and offer peace of mind in today’s digital landscape. Ensure that the latest versions of software and firmware are used and adhere to best ...