Table of Contents
The objective of this post is to understand the possible attack vectors on a wireless network, understand the weaknesses in wireless and how to test for those weaknesses, then how to best architect and configure your wireless network for maximum security. And we also cover mitigating radio frequency attack vectors and how to monitor your network for rogue clients.
Wi-Fi Security and Its Vulnerabilities
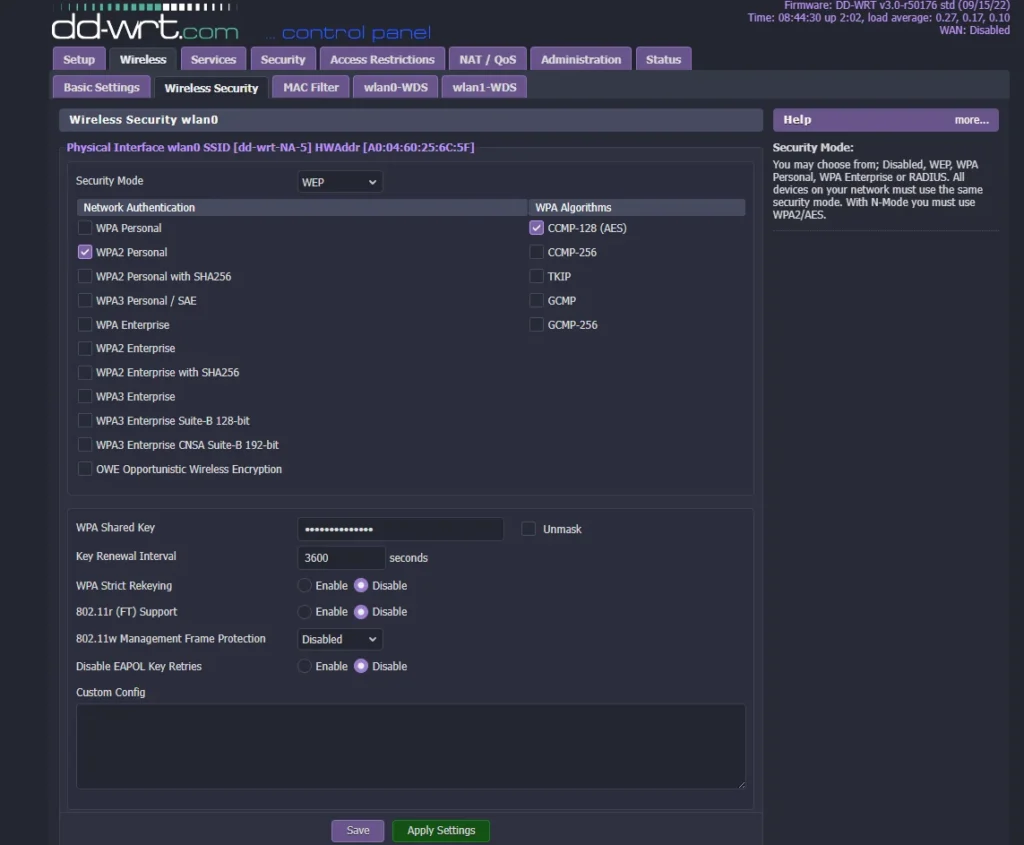
Let’s talk about Wi-Fi security and its vulnerabilities. You probably know that WEP, or by its official name IEEE 802.11, has a tremendous number of security flaws. If you use WEP on your Wi-Fi, your password can be cracked in a matter of seconds.
There are roughly three core deficiencies with WEP:
- Use of Static Encryption Keys: There are no session keys, so it encrypts with the same symmetric key for every packet, and the weak RC4 stream cipher is used to do it.
- Lack of Packet Integrity Assurance: You can change bits and alter the integrity check value, and the receiver doesn’t know.
- Ineffective Use of Initialization Vectors (IVs): IVs are random values used with algorithms to ensure patterns are not created during the encryption process. If IVs are not used, then two identical plaintext values that are encrypted with the same key will create the same ciphertext. For example, if I encrypt my name Nathan without an IV, the ciphertext might be 123. Anyone else that encrypts the name Nathan will get the same ciphertext 123.
The IVs in WEP are not random enough and only 24 bits, leading to reused IVs with the same key which lead to it being easily cracked. Packet injection allows for WEP to be cracked in as short as several seconds. This ultimately led to the deprecation of WEP or death of WEP. WEP should never ever be used because anyone who knows what they’re doing can get access to a WEP network in just a few seconds and are able to reveal the WEP password.
WPA and WPA2 Security Standards
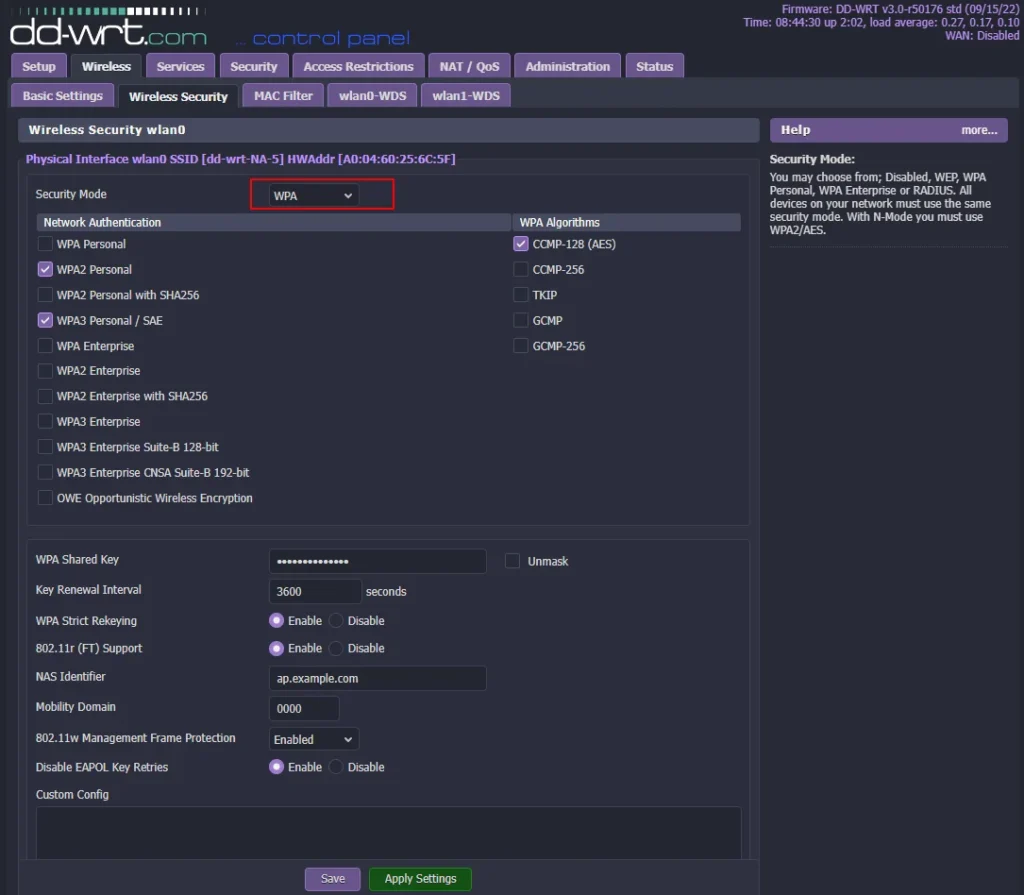
The WPA draft IEEE 802.11i standard came out in 2003. This was the initial WPA version to supply enhanced security over the older WEP protocol. Typically, it uses the TKIP encryption protocol, TKIP stands for Temporal Key Integrity Protocol.
And you can see it here, it’s been selected with WPA as the WPA algorithm within DDWRT, and you have the same equivalent in other routers. The RC4 stream cipher is used with an 128-bit per packet key, meaning that it dynamically generates a new key for each packet. The resulting encryption key will be different for each and every frame.
That’s WEP key plus IV value plus MAC address equals new encryption key, which is good. The IV length was increased over WEP, which again is good. TKIP is backwards compatible with the 802.11 standard, which may not be a good idea. It works with WEP by feeding it more keying material which is dated to be used for generating new dynamic keys.
TKIP provides a key mixing function which allows the RC4 algorithm to provide a higher degree of protection than WEP. It also provides a sequence counter to protect against relay attacks and implements a message integrity check mechanism.
But TKIP is susceptible to packet injection attacks, which could decrypt arbitrary packets sent to the client. And this was the first research that pointed that out. The report details how the attack can be used to hijack TCP connections, allow an attacker to inject malicious JavaScript when the victim visits a website.
So avoid using TKIP if you can. You would only use it for backwards compatibility or if you had an old access point, which if you do get rid of it, replace it and get a new one. So that was a draft standard we’ve just been talking about. The full WPA2 standard IEEE 802.11i came out officially in 2004.
And this added support for CCMP which is Counter Cipher Mode and Block Chaining Message Authentication Code protocol which is intended to replace the TKIP encryption protocol mandatory for Wi-Fi certified devices since 2006.
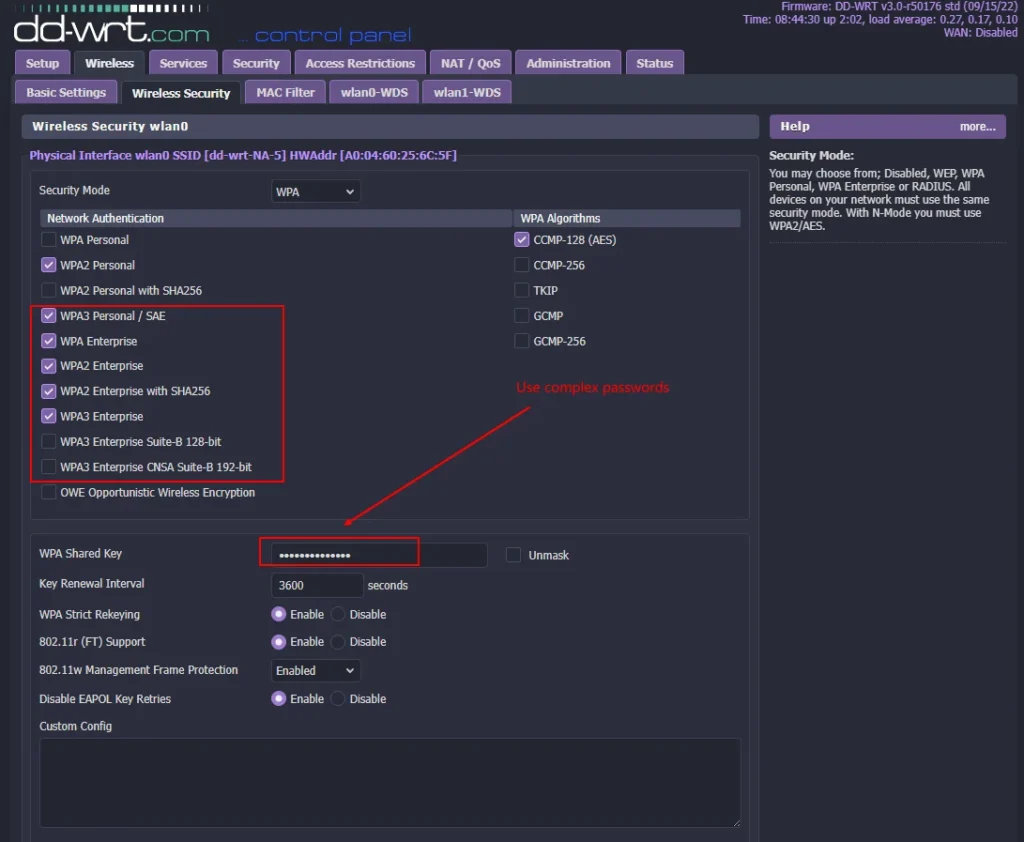
So when you are selecting a WPA algorithm, instead of using TKIP, always use CCMP instead or often you will see it as AES as you see it in this option here. And sometimes you even get the option of using both, which can be for backward compatibility. But the best option is CCMP or as they put it here AES.
They’re calling it AES because CCMP is an AES based encryption counter mode mechanism, CTR. And it is stronger than TKIP. AO2.11x technology in the new AO2.11 standard provides access control by restricting network access until full authentication and authorization has been completed, which is good.
CCMP uses CCM that combines CTR for data confidentiality and CBC-MAC for authentication and integrity again, which is all improvements. On the downside, AES is actually slower than TKIP so it does need a more powerful access point. And that might be one reason why some legacy access points are using TKIP.
So the recommendation here, WPA2 with AES or CCMP, as you might see it which is essentially the same thing. CCMP, AES, it’s the same option. So that was the encryption algorithm. Now we have to consider the access control method.
So let’s talk about WPA2 personal or also known as WPA PSK, pre-shared key. And if we look here, we have WPA personal. We don’t want that because we want to be using WPA2. So you’ve got WPA2 personal there and there’s also WPA2 personal mixed.
Now the mixed mode allows for the coexistence of WPA and WPA2 clients on a common SID. We don’t want to be using WPA so we don’t want to be using the mixed mode. So we want to be using this as our optimal option if we’re not using an enterprise mode. And we’ll discuss the enterprise mode in a second.
So WPA2 personal with pre-shared key, which is this, is designed for home and small business networks. And it doesn’t require an authentication server. Each wireless network device authenticates with the access point using the same 256-bit key generated from a password or passphrase.
This is the mode you will probably be most familiar with. You set a password on the router, the wireless access point, and everyone just uses the same password on every device. That is WPA2 pre-shared keys. The pre-shared password, but it’s poor. It’s poor because everyone shares the same password and if you want to change it you have to change it on all devices, which is a pain.
But it does do the job on a small network, a home network, a business network and you can, with modern firmware like this one, you can have separate Wi-Fi networks as discussed that you can have separate passwords for. So this helps to mitigate the password sharing problem.
In most cases, you want to use for a home network, a small business network you want to be using WPA2 personal with a pre-shared key and AES CCMP which is what it is set at here. The other option for access control method is what we have selected here. It’s WPA2 Enterprise.
It’s WPA802.X mode. This is designed for enterprise or company networks and requires a RADIUS authentication server. And if we look here, you can see we have one with DDWRT. And with custom router firmware and dedicated firewalls you will be able to get a RADIUS server which is an authentication server.
This requires a more complicated setup but provides additional security through multiple passwords. And you can use an extensible authentication protocol, EAP which means you can use stronger authentication mechanisms like dual certificate authentication.
So you authenticate both the client and the server with a certificate. That’s an example of what you can use if you use EAP. This will be too complex of a setup for most home networks and probably overkill but is viable for a technical user with high security needs.
Creating separate Wi-Fi networks of different trust levels with different passwords is actually easier and is probably enough in most cases, if of course your Wi-Fi supports that functionality. So you probably won’t use the enterprise mode, but if you want the best security then you’re looking for dual certificate authentication or dual factor authentication with EAP through this WPA2 enterprise.
That’s what you’d be wanting. Both WPA and WPA2’s handshakes are susceptible to dictionary and brute force password guessing of the pre-shared key. For this reason, pre-shared keys or the Wi-Fi password needs to be complex. It needs to be very complex. They are only entered once per device so should be both complex and long using special characters, letters upper and lower case, and numbers.
See the recommendations in the section on passwords. Password complexity, this password complexity is the main mitigation against password guessing dictionary brute force attacks against WPA and WPA2.
So even if you’re selecting WPA2 with all the right settings like AES it is still susceptible to this dictionary and brute force attack. So the mitigation is a strong password. So you must have a strong password.
And what you see here in front of you is the webpage for a tool called CowPatty which is available in Kali which is used for that very same attack.
There is a SALT issue, or a weakness, with the SALT in both WPA and WPA2. Both use the SSID as a SALT value. The SSID, if you’re not familiar, is a synonym for the network name.
Sols, and thus this SSID, should be random values that are added to the encryption process to add more complexity and randomness to it. The use of a sol means that the same password can be encrypted into several thousand different formats. This makes it much more difficult for an attacker to uncover the right format for your system if the sol is random.
And as I said, WPA and WPA2 uses the SID of the network as the sole value, i.e. the network name. Your network name or SID might be one that is commonly used, a name that is commonly used, and this would not be good. Access points with common SSIDs are more vulnerable to password guessing and dictionary attacks if they have a common name.
Common names include things like and you’ll have potentially seen these yourself Linksys, Default, Netgear, Wireless, WLAN. These are all common SSIDs or network names that you can see. And the reason they are more vulnerable if they have a common SSID is that hackers can pre-compute common passwords against or with common SSIDs to make password cracking faster.
And these are referred to as rainbow tables. But in reality, hackers don’t even really need to pre-compute them themselves. They can download ones that have already been made. Here is the Church of Wi-Fi and they have a whole bunch of rainbow tables one million common passwords or passphrases for 1000 common SSIDs and that’s a 33 gig file download which will help speed up the cracking of a WPA or WPA2 password if the SSID is in this rainbow table.
So default or common SSIDs should not be used because of this attack. So change your SSID if it is a common one and especially if it’s on this list.
Wi-Fi Protected Setup (WPS) Security Flaws
Now, the next major Wi-Fi mess up, or Wi-Fi protected setup WPS mess up, one of the methods this WPS is implemented is to enter a short pin number instead of a password to gain access to your Wi-Fi network. And a person would get this by reading it either from a sticker or somewhere where it is displayed maybe on the back of the wireless device and you enter this PIN instead of a password to get access to the wireless network.
A major security flaw in the WPS PIN feature was revealed in around December 2011. Many routers have WPS PIN enabled by default. The flaw allows a remote attacker to recover the WPS pin in a few hours with a brute force attack. And when you have the WPS pin you can then get the network’s WPA, WPA2 pre-shared key or password. Essentially you’ve got access to the network.
If you want to play around with this in Kali there is a tool called Reaver that can be used to do this very attack. So WPS must be turned off and it’s actually another reason for having custom firmware as some routers don’t even allow you to switch this WPS feature off. And there have even been reports of routers showing that WPS is switched off in the GUI and yet it continues to function and the attack is successful.
Encryption is hard to get right. They are very delicate systems and the Wi-Fi alliance has demonstrated it perfectly. Unfortunately, the encryption is hard to get right. More weaknesses will be found in Wi-Fi as time goes by as they always are.
What makes this more relevant to you is that Wi-Fi is, well, it’s wireless. Anyone can potentially connect to it and not, they don’t even need to be that close. With serious antennas you can connect at even miles away. So we have to protect our Wi-Fi and in fact all of our wireless technology.
Another issue you might have is your evil twin. Well, not actually your real evil twin, but an attacker can set up an access point a wireless access point with a SSID or network name that is the same as a real Wi-Fi network that you connect to. Because it has the same name your devices will automatically connect to it instead of the real one if the signal is stronger.
This is effectively a man in the middle attack. If your traffic isn’t encrypted they will be able to see it and they’ll be able to inject into it which means they can do a lot of damage. They can also try other attacks such as SSL stripping. If you are using SSL encryption they can do browser attacks, et cetera.
Evil Twin access points is actually a hard attack to mitigate against. You should use encryption as usual and you should try to notice anything unusual like not being able to access your internal devices. Authenticating the access point using WPA2 Enterprise with EAP and using a method like dual certificate authentication for access point authentication can mitigate the issue of the evil twin as the access point is being authenticated to the client as well as the client authenticating to the access point.
If the access point is authenticated to the client the client cannot be fooled into thinking or connecting to an evil twin. A commercial version of the evil twin you can see here in front of you which is called the pineapple, which can be bought. It also has lots of other hacking features. The evil twin attack is quite a common attack. It might be easier for people than trying to crack your Wi-Fi password.
In the section on Wi-Fi security, I cover more on general security mitigations. When we start talking about really serious adversaries, then we get into the realm of the unknown and the speculative when it comes to wireless security.
It is possible that especially nation states and agencies have exploits against the core components of Wi-Fi and wireless technology such as Wi-Fi drivers, protocol stack, DHCP or even attacks and vulnerabilities against WPA2 with AES that the community isn’t aware of. But of course, this is speculation.
Devices such as the one you see here are reported to be able to do that very thing but the accuracy of that statement is unknown. Plus, lately it is known that drones are equipped with Wi-Fi crackers attached to them, also drones with evil twins and other nastiness.
So there is an unknown component there in terms of what are the latest high end attacks. In the section on Wi-Fi security, as I’ve already said, we’ll discuss more mitigations. It’s obvious, but if you connect to an untrusted access point, you need to take more precautions because they essentially own the network.
They are a man in the middle, and if you connect to an untrusted access point, this is called a rogue access point, where the owner of this is a bad actor. They could, if they so chose to, strip the SSL, or they could attempt to, the access point can then potentially see all of the things that you are doing, the sites that you are visiting, and you might not notice if you’re in your browser the change from HTTP to HTTPS.
This is why VPNs are required on untrusted networks. If you really want to dig further into Wi-Fi weaknesses, this is a good report here with lots of detail on WiFi security and its weaknesses. So that’s WiFi weaknesses.
Using Kali Linux for Wi-Fi Security Testing
To do Wi-Fi security testing with Kali Linux, a compatible USB network adapter or dongle network device is needed. This allows the device to be put into monitor mode and to perform packet injection. Let’s explore the types of adapters and tools you can use for effective security testing.
Compatible USB Network Adapters
- Selecting an Adapter:
- You need a USB network adapter that uses compatible chipsets. Many adapters work well with Kali Linux. For instance, an Alpha adapter is widely used and available for around $35.
- Examples of Working Adapters:
- Here’s a list of known USB network adapters that function with Kali:
- Alpha (multiple models)
- TP-Link
- Panda (small model)
- Here’s a list of known USB network adapters that function with Kali:
Key Tools for Wi-Fi Security Testing
- Aircrack NG:
- This is the main tool for cracking Wi-Fi security protocols like WEP and WPA/WPA2. It can recover keys once enough data packets are captured. More information can be found at aircrack-ng.org.
- CowPatty:
- An implementation of an offline dictionary attack against WPA and WPA2, focusing on PSK-based authentication.
- Reaver:
- This tool implements a brute force attack against Wi-Fi Protected Setup (WPS) to recover WPA/WPA2 passphrases. It’s typically used in combination with Aircrack to ensure you’re targeting the correct network.
- Fern Wi-Fi Cracker:
- A GUI front end for cracking and recovering WEP, WPA, and WPS keys. It simplifies the process through a point-and-click interface, making it user-friendly for those new to security testing.
Live CD for Wi-Fi Security Testing
- Specialized Tools:
- There is a dedicated Live CD for Wi-Fi security testing that contains most of the tools available in Kali. This can be helpful if you want a focused environment for your testing.
Steps to Enhance Your Testing
- Familiarize Yourself with Tools:
- Spend time learning each tool mentioned above as this guide does not cover penetration testing in detail.
- Practical Experience:
- Using tools like Fern Wi-Fi Cracker can help you get hands-on experience, making it easier to understand Wi-Fi security vulnerabilities.
Using Kali Linux for Wi-Fi security testing requires the right hardware and tools. By leveraging compatible USB adapters and powerful tools like Aircrack NG and Reaver, you can effectively test and improve the security of your Wi-Fi networks.
Wi-Fi Security Best Practices
We’ve already spoken about ways to strengthen your Wi-Fi security as we went through all of the security disasters in Wi-Fi and the security weaknesses. We have also talked about network isolation for Ethernet, physical networks. I’m now going to go through a full list of ways to secure and strengthen Wi-Fi including network isolation.
Network Isolation
Wireless networks should be considered less trusted than physical networks. Physical and wireless networks, ideally, should be isolated from each other where possible. What I mean by that is that traffic from your wireless devices, ideally, should not be able to reach your wired devices. Wi-Fi devices are less trusted because Wi-Fi is simply more vulnerable to attack. It can be attacked from many miles away, whereas obviously your physical cables need somebody to be physically close to it in order to perform an attack. So Wi-Fi is intrinsically more risky.
VLANs do not work on Wi-Fi, but they have an equivalence, which is having separate Wi-Fi networks for devices of different trust levels. In this diagram here, you can see I have it illustrated as we have SSID 1. So we have our untrusted guest Wi-Fi network here, a 192.168.4 network. And we have our semi-trusted Wi-Fi network, which is on SSID 2 and on 192.168.5, and then these two networks are running from the same wireless access point. These are effectively separate Wi-Fi networks, even though they’re connected to the same access point.
These two networks would have separate passwords and are totally separated from each other as far as the devices are concerned. In DDWRT, for example, you set up a bridge, a bridge is used to enforce the separation between those two Wi-Fi networks on the same access point, and firewall rules could be used too. Untrusted wireless devices would not be able to communicate outbound to the rest of the network.
If on your untrusted network, say for example, this is a smart TV, it would just simply be given access to go out to the internet. Nothing would be able to go from here and out, as I’ve just said. Traffic potentially could be allowed from one of your trusted or semi-trusted networks to go inbound and connect to this if you had some sort of need to do that like administration. But it’s best to keep it fully isolated if you can and if there is no need for that inbound connection.
Wi-Fi Access Point Features
The semi-trusted network would not be allowed to connect outbound to trusted networks. It may be allowed to connect to untrusted networks. Trusted devices may choose to connect in if required. Additionally, some router access points have a feature called AP isolation. It does go by different names like wireless isolation and other things, so it requires some investigation to work out whether or not your access point will support it.
AP isolation prevents access to and from other wireless clients even on the same network. This setting isolates wireless clients so that they cannot communicate with one another on the same network. It’s a great feature for isolation.
Keep Your Devices Updated
Like all devices, your wireless access point and router need to be kept up to date with the latest security critical updates. Make sure this is done, as it is critical to keep everything updated with the latest patches.
Secure Configuration
To facilitate your ability to adequately securely configure your network, consider the installation of custom firmware on your router or access point as this may be your only option for enabling good security for your wireless devices. If you want to reduce the wireless attack surface, disconnect your Wi-Fi when you are not using it, like when you go on holiday. Disable your network cards on devices when they are not used and switch off your access point when it’s not in use.
SSID and Password Management
Change the default SSID to something random or at a minimum make sure that your SSID isn’t a common SSID name. Each access point comes with a pre-configured default SSID value. Changing it to something random makes rainbow table attacks to crack the password impossible. For access control, the best option is WPA2 Enterprise. This requires a RADIUS authentication server, which can provide additional security through multiple passwords.
Encryption and Security Protocols
Where possible, always encrypt network traffic over your wireless networks. I use TLS where possible or VPNs. Disable Wi-Fi Protected Setup (WPS) as it is a serious security vulnerability.
If your access point and router can implement ARP spoof protection, enable this. Implement technology to discover rogue or evil twin wireless access points and devices. Change the default password for accessing administrative interfaces and close any interfaces that you do not use.
Wired Connections
If you don’t need Wi-Fi, stick with Ethernet. This may not be possible but it is more secure. If your adversary is of sufficient means, you should avoid the use of all wireless technologies apart from where absolutely necessary.
Optional Security Practices
Some people recommend disabling the broadcast of your SSID network on the access point, but it provides little protection. If you are implementing WPA2 Enterprise, consider implementing 802.1x device registration. MAC address filtering is not necessarily recommended as it does not provide real risk mitigation.
As discussed, you could have a VPN overlay network on your wireless network which would add additional layers of encapsulation and encryption. You could conduct your own penetration tests on the WLAN. Some routers have a maximum associated client setting; reducing this number could limit the scope of attack.
Finally, consider radio frequency RF isolation and reduction methods.
RF Isolation and Reduction for Enhanced Security
Something else that you may want to consider is RF or radio frequency isolation and reduction. This is if you are concerned about neighbors, local-based adversaries, or even potentially people at a distance with boosters and long-range antennas from attacking your network, and also to prevent other radio attacks as well.
Mitigating Local Attacks
To mitigate these local attacks, you can consider physically putting the access point at the center of the building that it is in. The access point should have a specific zone of coverage that you have designed for it. In order to do that, perform a wireless signal detection survey to identify the boundaries of your wireless perimeter.
To do this, you simply just need a portable wireless device to find out where you can no longer receive a signal. Once you know this, limit the range of the signal to just the areas that you need it to be in by changing the access point location or changing the power output on the access point.
Adjusting Access Point Settings
Custom firmware such as DDWRT allows you to change the power output to reduce the range of the Wi-Fi. You can possibly change the antenna to a directional antenna to reduce the scope, and you can also consider dampening materials for further isolation.
Dampening Materials
Dampening materials are not just for Wi-Fi but are for protecting against all air-gapped electromagnetic attacks. If you’re concerned about this, consider shielding the electromagnetic fields by blocking them from coming in and going out. You can use special materials such as curtains and paints, which can block mobile phone signals, CCTV, AM/FM signals, Bluetooth, Wi-Fi, radio frequency radiation, and even microwaves.
Faraday Protection
If you have the need to completely block all fields, people use Faraday rooms or cages. Additionally, Faraday bags are available for your phone, laptop, other mobile devices, car keys, credit cards, and any other device that may be attacked by RF.
Bluetooth Security Guidance
If you’re using Bluetooth and want some guidance for your Bluetooth devices, the US government provides quite useful guidance. Check out the provided link and go through the recommendations to lock down your Bluetooth security.
In-Depth Resources
If you’re looking for something a bit more in-depth, particularly at the business level, consider checking out the comprehensive guide from NIST.
Monitoring Your Wi-Fi Network
If you are concerned that someone might be connected to your Wi-Fi network, you can monitor who is on your Wi-Fi network very easily, and there are many different ways you can attempt to do this.
Check Your Router
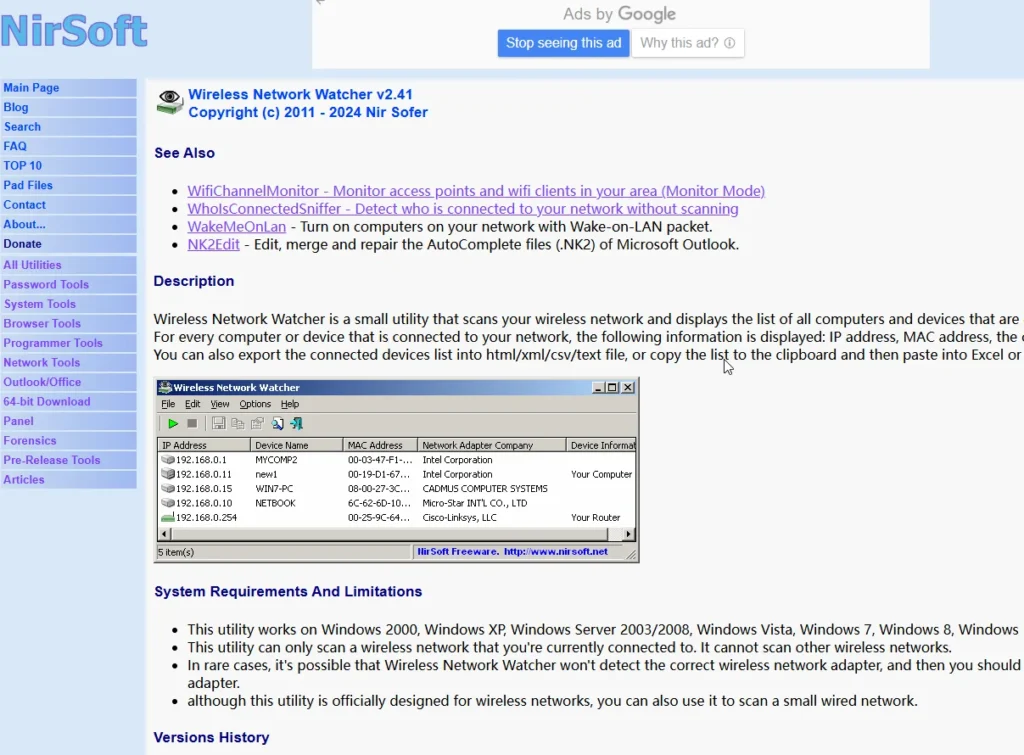
First, you can just look on your router or your access point. Somewhere on there, if it’s a reasonably good access point, you should see a list of the devices that are actually connected, along with their corresponding MAC address and IP address. Here’s an example where you can see the MAC addresses, but there should be something similar in most routers or access points.
Network Scanning Applications
Then, there are any number of applications that can scan your wireless network and display a list of all the computers and devices currently connected to your network. Here are some examples:
- Wi-Fi Inspector (works with Windows and Mac)
- Wi-Fi Network Monitor (for Windows)
- Wireless Network Watcher (another for Windows)
- GlassWire (a firewall that also shows devices on your wireless network)
You can also use network scanners to find devices on your network. Remember, I’ve mentioned before that you can scan your network using your mobile device to see who’s on it, applicable for both Android and iPhone users.
Using Nmap
We can also use Nmap to scan the network. Nmap does a ping sweep; it tries to ping the given IP address range to check if the hosts are alive and responding. If ping fails, it tries to send a SYN packet to port 80, performing a SYN scan.
This is not perfect because devices on the network may not respond to ping or those SYN packets, but it is one way to attempt to do it. You can also try a regular port scan to see if any devices respond. You can use Zenmap, which is the GUI for Nmap.
Advanced Tools
In Kali Linux, there’s a tool called ARPscan, which you can get for Debian and Debian-based systems by using sudo apt-get install arp-scan. This will scan whatever range of IP addresses and provide you with their MAC addresses.
You would need to specify the correct local network. You could also simply use arp -a to look at your existing ARP cache to see if you have communicated with any devices that may be lurking on the network.
Other Methods
You can use aerodump-ng to detect access points and list the connected clients. Additionally, you can utilize protocol analyzers like Wireshark, TCP Dump, or T-Shark. These tools can be used to look at network traffic, allowing you to see who is using the network.
Conclusion
This article discusses wireless network security and vulnerabilities, including the flaws in WEP, the security standards of WPA and WPA2, the security risks of WPS, and how to use Kali Linux for Wi-Fi security testing. It emphasizes the importance of using WPA2 with AES or CCMP encryption and avoiding WPS and common SSIDs to enhance security. Best practices such as network isolation, keeping devices updated, secure configuration, SSID and password management, and encryption protocols are covered. Finally, the article touches on RF isolation and reduction methods, as well as monitoring Wi-Fi networks to identify unauthorized clients.


