Table of Contents
By understanding the strengths and weaknesses of Tor, you can use it more securely and effectively. This section aims to give you a comprehensive understanding of how to maintain anonymity and security while using Tor.
Anonymizing Network and Browser
What is Tor?
- Anonymizing Network: Tor, or “The Onion Router,” anonymizes internet traffic by routing it through multiple relays.
- Software Component: The Tor Browser, formerly known as Tor Browser Bundle (TBB), is the software that allows access to the Tor network.
Tor Network and Browser
- Network Coverage: Most Tor relays are located in Europe and the US, with increasing bandwidth over time. This results in improved speed and latency.
- Browser Composition: The Tor Browser is built on Mozilla Firefox ESR, including components like Tor Button, Tor Launcher, NoScript, and HTTPS Everywhere. It can run from removable media and is available for Windows, Mac OSX, Linux, and mobile platforms.
Setting Up Tor
- **Download and Install:**
- Obtain the Tor Browser from verified sources and install it on your device.
- Available for Windows, Mac OSX, and Linux with installation instructions provided.
- Using Tor:
- The browser interface resembles Firefox, with additional privacy tools like NoScript.
- Test Tor Network settings to confirm that it’s configured for anonymity.
- Understanding Circuits:
- New Identity vs. New Tor Circuit:
- New Identity: Clears all identifiable data and restarts the browser.
- New Tor Circuit: Changes the IP address and circuit without restarting, but may not clear trackable information.
- New Identity vs. New Tor Circuit:
Privacy and Security Settings
- Set Privacy to High: Ensuring maximum anonymity by disabling potential tracking features.
- Avoid Recording History: Disable plugins like Flash and restrict third-party cookies.
Accessing Tor Despite Censorship
- Download via Email: If Tor is blocked, email gettor@torproject.org for download links.
- Verify Software: Use signatures to verify the legitimacy of the Tor Browser.
Resources and Community
- Tor Forum and FAQ: Engage with the community for support and read FAQs for common questions.
- Tor Blog and Wiki: Stay updated with the latest news and technical articles.
- Third-Party Resources: Follow subreddits and explore design documents for in-depth understanding.
The Tor Project / Organization · GitLab
Understanding Tor’s network and browser, configuring it correctly, and utilizing community resources significantly enhance your anonymity and security online. Reading the design documents provides a comprehensive understanding of its workings.
What Tor Can and Can’t Do
What Tor Does
- Anonymize Browser Connections:
- Tor anonymizes the connection of the Tor Browser to websites, not other applications unless specifically configured.
- Data Transport Protection:
- Prevents your ISP or local network from knowing the sites you visit.
- Stops websites from identifying you unless you log in or provide personal information.
- Evade Censorship and Access Darknet:
- Helps bypass censorship and access hidden services via .onion addresses.
What Tor Does Not Do
- Complete Anonymity:
- Your ISP can see you’re using Tor unless special configurations are made.
- Tor traffic can be detected by deep packet inspection.
- Application Anonymity:
- Other applications do not automatically use Tor. Only the Tor Browser is routed through Tor unless configured otherwise.
- Downloaded Content Risks:
- Files downloaded through Tor, like PDFs, may reach out over the internet, exposing your real IP.
- Browser Vulnerabilities:
- Does not eliminate all browser vulnerabilities or protect against active content like JavaScript without specific settings.
- Additional Protection:
- No protection from malware, OS or hardware compromises, or physical observation.
Best Practices for Using Tor
- Use the Tor Browser:
- For maximum privacy, use the Tor Browser rather than configuring other browsers or applications yourself.
- Avoid Torrents:
- Torrent applications may leak your real IP, even when configured to use Tor.
- Disable Plugins:
- Don’t install additional plugins or add-ons to prevent altering your browser fingerprint.
- Use HTTPS:
- Ensure traffic is encrypted end-to-end to prevent exit nodes from reading or injecting into your data.
- Offline Document Opening:
- Do not open downloaded documents while online to prevent accidental IP exposure.
- Use Bridges and VPNs:
- Consider using Tor bridges or combining with VPNs for additional layers of anonymity.
Tor is a powerful tool for anonymity and privacy, but it has limitations. Understanding these helps you use it more effectively and safely. Always verify your settings and practices to maintain the desired level of anonymity.
Directory Authorities and Relays in the Tor Network
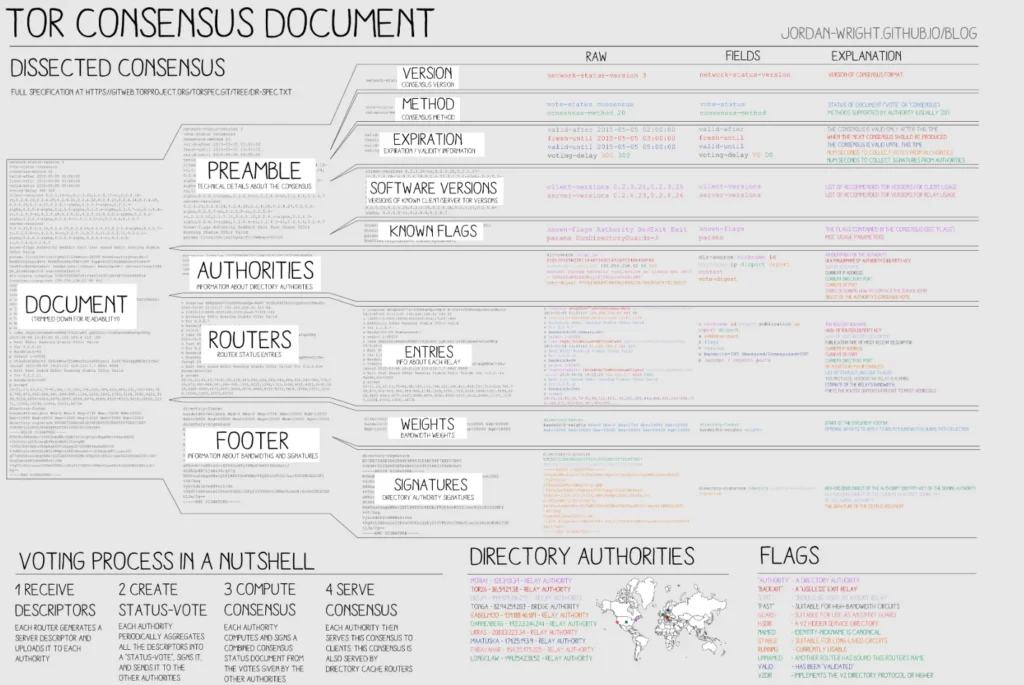
What are Directory Authorities (DAs)?
- Role and Function:
- There are 10 DAs globally that maintain a master list of all known Tor relays, known as the consensus.
- They act as gatekeepers, validating and distributing relay information.
- Importance of DAs:
- DAs ensure that only valid relays participate in the network, maintaining integrity and security.
Understanding Tor Relays
- Relay Types:
- Guard (Entry) Relays: Initial entry points into the Tor network, selected for stability and bandwidth.
- Middle Relays: Transport traffic from guard to exit relays, preventing direct connections between entry and exit points.
- Exit Relays: Send traffic from Tor to its final destination. They can see unencrypted traffic.
- Security Implications:
- Exit relays can read or inject into traffic if it is unencrypted, highlighting the importance of using HTTPS.
Running Your Own Relay
- Anonymity Considerations:
- Running a relay may not enhance anonymity; it might signal to adversaries your interest in privacy.
- Adversaries owning multiple relays can potentially conduct correlation attacks to trace activity.
- Legal and Practical Risks:
- Running an exit node carries legal risks due to potential misuse of its traffic.
- Guard or middle relays are less risky, dealing only with encrypted data.
- Community and Legal Support:
- The Tor project provides resources and support for running relays.
- Transparency about running a relay can help differentiate your intentions from the traffic passing through.
ZMap: Fast Internet-wide Scanning and its Security Applications
AChildsGardenOfPluggableTransports · Wiki · Legacy / Trac · GitLab
Running a relay supports the Tor network but comes with risks, especially legal ones for exit nodes. Weigh the risks against the benefits, and consider starting with guard or middle relays. It’s essential to stay informed about legal responsibilities and be transparent about your operations.
Tor Bridges and Their Role
What are Tor Bridges?
- Purpose and Functionality:
- Bridges are unpublished relays used to connect to the Tor network, especially when access to standard relays is blocked.
- They serve as the first relay in the circuit instead of the usual entry guard relay.
- When to Use Bridges:
- Necessary if Tor is blocked due to censorship, or if using Tor is illegal or suspicious in your location.
- In uncensored areas, bridges are not necessarily more secure than regular entry guards.
How to Acquire and Use Bridges
- Obtaining Bridges:
- Bridges can be obtained via the Tor Project’s bridge page or by emailing bridges@torproject.org with “get bridges” in the message body.
- Options include vanilla bridges, pluggable transports, and IPv6.
- Setting Up Bridges:
- Copy the obtained bridge information into the Tor network settings in the Tor browser.
- Custom bridges can help bypass ISP blocks.
Challenges and Considerations
- Reliability and Speed:
- Bridges are typically less reliable and slower than guard relays.
- Continuous surveillance or scanning can identify and block these bridges.
- Security Risks:
- Be cautious of bridges provided by untrusted sources as they may be monitored or set up as traps.
- Consider the legal and personal risks of using bridges in areas where Tor usage has consequences.
- Alternatives to Bridges:
- Using VPNs, nested VPNs, or SSH tunneling to tunnel Tor traffic may offer safer alternatives.
- Off-site connections can also bypass Tor blocks under the right circumstances.
SampleClientHellos · Wiki · Legacy / Trac · GitLab
Tor bridges are tools designed to help users access the Tor network when normal relays are blocked. While they provide a valuable workaround for censorship, they come with limitations and risks. Always assess the potential repercussions in your context and explore alternative solutions for safer access.
Tor Pluggable Transports and Traffic Obfuscation
What are Pluggable Transports?
- Purpose and Functionality:
- Pluggable transports are tools that transform Tor traffic between the client and the bridge to bypass network censorship, especially those using deep packet inspection (DPI).
- Why Use Pluggable Transports:
- They help make Tor traffic appear as innocuous or unrelated data to avoid detection by advanced network monitoring systems.
How do Pluggable Transports Work?
- Transforming Traffic Signatures:
- Pluggable transports change the appearance of Tor traffic so it doesn’t match known patterns.
- Examples include OBS2, OBS3, which alter the traffic fingerprint.
- Types of Pluggable Transports:
- Various transports like OBS Proxy, Flash Proxy, Meek, and ScrambleSuit make traffic look like different protocols or random data.
Challenges with Pluggable Transports
- Detection and Evasion:
- While they help evade basic DPI, sophisticated analysis might still identify pluggable transport traffic.
- Continual adaptation is necessary to stay ahead of detection methods.
- Configuration and Compatibility:
- Pluggable transports must be supported by the bridge or relays in use.
- It’s crucial to configure them correctly in the Tor browser settings to work effectively.
Risks and Considerations
- Short-term Solutions:
- They are temporary workarounds and may not provide long-term security against determined adversaries.
- In regions where Tor usage has serious consequences, alternatives might be safer.
- Alternatives:
- Other methods like VPN tunneling, SSH, and offsite connections can offer additional layers of anonymity and may be more secure.
Pluggable transports are valuable for obfuscating Tor traffic but come with limitations. They need constant updating to remain effective. Users should consider the risks involved, especially in high-risk areas, and explore alternative methods for secure, anonymous browsing.
Configuring Tor: GUI vs TORRC File
Two Main Configuration Methods
- Graphical User Interface (GUI):
- Accessible through the Tor browser, allowing users to adjust settings visually.
- Recommended for most users, as it automatically updates the TORRC file.
- TORRC Configuration File:
- A more advanced method, this file (spelled T-O-R-R-C) contains Tor’s configuration settings.
- Located in different directories based on the operating system (OS). For Windows, it’s found in the Tor browser’s data folder. For Mac, it’s accessed through application package contents. On Linux, it’s in the installation directory.
- Editing requires knowledge of Tor’s syntax and functionality.
Default Settings and Caution
- Default Configuration:
- The default settings in the TORRC file are generally sufficient for most users.
- Changes should only be made after thoroughly reading Tor documentation.
- Finding and Editing TORRC:
- Use the OS-specific path to locate TORRC. If you can’t find it, searching for “TORRC” can help.
- The file looks similar across Windows, Mac, and Linux.
Advanced Configuration Options
- Geographic Node Selection:
- Users can specify entry and exit nodes by country code (e.g., DE for Germany).
- This can affect anonymity and performance based on the type of threat being mitigated.
- Relay and Bridge Setup:
- Users can choose specific relays by their fingerprint.
- Setting up relays or bridges involves specifying ports and directory settings.
Security and Operational Concerns
- Risks of Manual Configuration:
- Manual circuit changes can make users stand out, potentially compromising anonymity.
- Restarting the Tor browser is necessary for changes to take effect.
- Logging and Forensics:
- Logs should be disabled if local forensics are a concern.
- Running Tor as a daemon is possible, although not on Windows.
The TORRC file allows for detailed and customized Tor configurations but requires caution and understanding. For most users, sticking to the GUI and default settings is advisable unless advanced knowledge is acquired. Always restart Tor after making changes to ensure they’re applied.
Tunneling Traffic Through Tor: Applications and Considerations
Using Tor with Other Applications
- Caution Required:
- Tor is designed to prevent protocol leaks, but other applications may not be.
- Be cautious when configuring non-Tor applications, like email clients, to avoid unintentional data leaks.
- Common Issues:
- Applications may send data (like DNS requests) outside of the Tor network, even when set to use Tor.
Configuring SOX Proxy for Applications
- SOX Proxy Setup:
- Tor uses a SOX proxy, typically at port 9150, to route application traffic through Tor.
- Applications supporting SOX proxies can be configured to use this port.
- Example with Ice Weasel (Firefox on Debian):
- Navigate to preferences, set the SOX proxy to localhost and the correct port.
- Ensure changes are applied by checking Tor settings.
Risks of Traffic Leaks
- Potential Leaks:
- Even with proper configuration, applications may not route all traffic through Tor.
- DNS queries are commonly sent outside of Tor, posing a risk.
- Testing for Leaks:
- Use the TestSox option in the TORRC file to monitor SOCKS connections for proper routing.
- Tools like WireShark can help monitor traffic for leaks in real-time.
Advanced Tools and Recommendations
- Provoxy and Proxy Chains:
- Advanced users can use tools like Provoxy to manage proxy settings for applications without built-in support.
- Proxy chains can force applications to use a proxy, but trust in these tools is necessary.
- Using Hoonix:
- Hoonix offers a transparent gateway for routing all workstation traffic through Tor.
- Provides a safer environment for applications lacking proxy support.
- Hardware and Software Solutions:
- Tor hardware routers can ensure all traffic is routed through Tor.
- Open-source solutions like Tortilla and Corridor help manage and secure Tor traffic on Windows.
ISO 3166-1 alpha-2 – Wikipedia
Configuring applications to use Tor requires careful attention to avoid leaks and maintain anonymity. Tools like Hoonix and WireShark can assist in ensuring secure traffic routing. It’s important to understand the limitations and risks involved in order to make informed decisions regarding network security.
Tor Weaknesses and De-Anonymization Risks
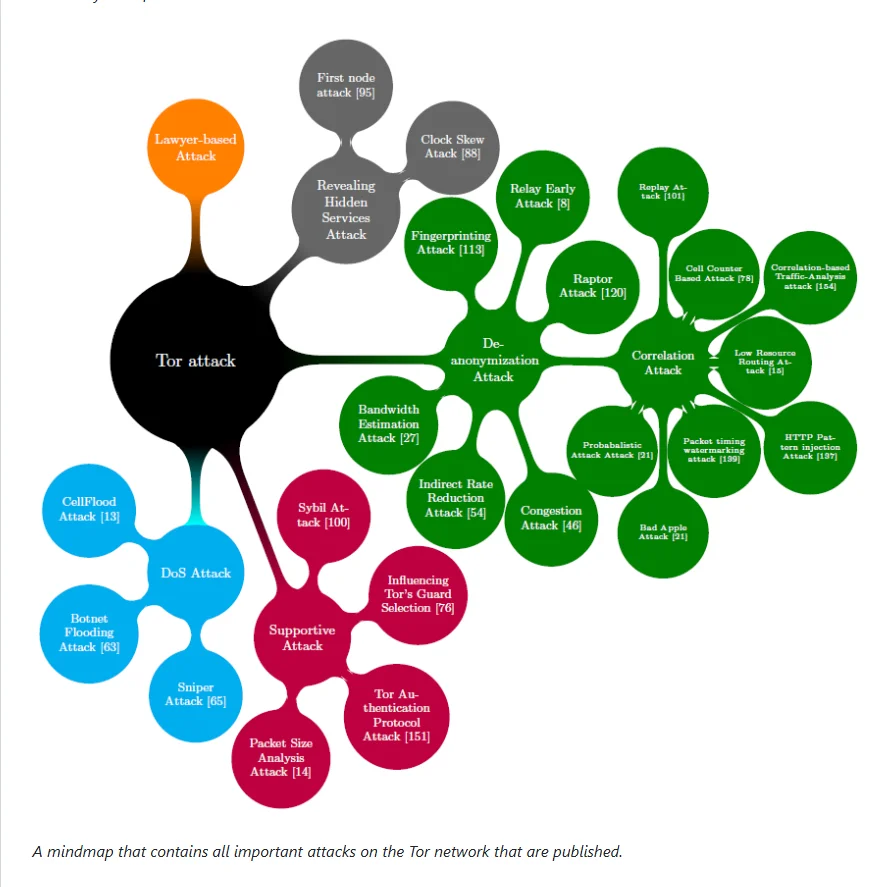
Tor’s Public Profile and Complexity
- High-Profile Target:
- Tor is a focus for nation-state intelligence agencies due to its anonymity features.
- Usage can lead to being automatically profiled and targeted for de-anonymization efforts.
- Complexity and Security:
- Tor’s complexity can lead to security vulnerabilities.
- Customizing configurations can introduce risks if not done correctly.
Browser Exploits and Mitigation
- Browser Vulnerabilities:
- Tor Browser, based on Firefox, has been targeted with exploits.
- Past attacks have exploited JavaScript vulnerabilities to extract user data.
- Mitigation Strategies:
- Disable scripts (JavaScript, Flash) and avoid installing unnecessary plugins.
- Utilize virtual machines or sandboxes for browser isolation.
Persistence and Data Management
- Data Persistence Risks:
- Browser data persistence can expose user activities.
- Regularly clear cached data and consider non-persistent operating systems like Tails.
- Improving Non-Persistence:
- Use live operating systems or virtual machine snapshots to ensure data is not retained.
Traffic Analysis and Attacks
- Traffic Confirmation Attacks:
- These occur when an attacker controls entry and exit relays, correlating traffic patterns.
- Tor’s design allows anyone to run a relay, increasing the risk of these attacks.
- Sybil Attacks:
- Attackers run many relays to observe and influence network traffic.
- This can lead to successful de-anonymization through correlation.
- DDoS and Autonomous Systems:
- Adversaries can disrupt relay nodes, forcing traffic through controlled nodes.
- Autonomous systems can perform traffic analysis if both ends of a connection are within the same system.
Proxifier – The Most Advanced Proxy Client
ProxyCap – Proxifier and SSH Tunneler for Windows/macOS
ProxyChains – TCP and DNS through proxy server. HTTP and SOCKS
GitHub – cpatulea/TorCap2: Transparent SOCKS4a-ifier for Windows
GitHub – dgoulet/torsocks: Library to torify application – NOTE: upstream has been moved to https://gitweb.torproject.org/torsocks.git
To maintain anonymity on Tor, users should minimize their exposure by disabling scripts, using non-persistent systems, and understanding the risks of traffic correlation attacks. While Tor can provide robust anonymity, these strategies are crucial for those concerned about advanced de-anonymization techniques.
Tor Vulnerabilities: Traffic Fingerprinting and Other Risks
Website Traffic Fingerprinting
- How It Works:
- This attack analyzes encrypted data streams based on size and timing to deduce which web pages are being visited.
- Although the content remains encrypted, traffic patterns can reveal the website if attackers know its pattern in advance.
- Current Threat Level:
- While these risks are noted in research, they are not yet a significant problem but should be monitored.
Exit Node Eavesdropping
- Risks at the Exit Node:
- Tor cannot protect data exiting through the final node, exposing unencrypted traffic to those who control the exit.
- Mitigation involves using end-to-end encryption tools like TLS or PGP.
- Hidden Services:
- Tor’s hidden services (e.g., .onion sites) offer end-to-end encryption, making them more secure than surface web browsing.
Traffic Analysis and Man-in-the-Middle Attacks
- Traffic Analysis Vulnerability:
- Passive observers can conduct traffic analysis if they have visibility on enough relays.
- Man-in-the-middle attacks can mislead users into thinking they’re communicating with the intended target.
- Underlying Technology Vulnerabilities:
- Flaws in the internet’s infrastructure (e.g., Heartbleed bug) can compromise Tor’s anonymity.
General Tor Weaknesses
- Relay and Bridge Blocking:
- Simple to block Tor relays, making it difficult for users in restricted areas to access Tor.
- Protocol and DNS Leaks:
- When using Tor with other applications, there’s a risk of leaking protocols like DNS, especially with applications like BitTorrent.
- Usability Issues with Tor:
- Speed and latency remain issues, though improvements are ongoing.
- Some sites block Tor users or flag them as suspicious due to IP and location discrepancies.
Mitigation Strategies
- Chained Anonymizing Services:
- Employ multiple anonymizing tools or off-site connections to enhance privacy.
- Continuous Monitoring:
- Stay informed about the latest research on Tor vulnerabilities and apply recommended practices for security enhancements.
- Use of Encrypted Communication:
- Always ensure data is encrypted end-to-end, especially when traveling through exit nodes.
GitHub – dgoulet/torsocks: Library to torify application – NOTE: upstream has been moved to https://gitweb.torproject.org/torsocks.git
While Tor provides excellent anonymity, understanding its weaknesses and taking proactive steps can help mitigate risks. Users should remain vigilant and adapt to new security information to protect their privacy effectively.
Concluding Thoughts on Tor and Mitigation Strategies
Tor’s Advantages and Limitations
- Benefits of Tor:
- Protects against ISP and local network monitoring.
- Masks your identity from visited websites unless disclosed.
- Helps evade corporate tracking and censorship.
- Challenges with Advanced Adversaries:
- Intelligence agencies actively target Tor due to its anonymity capabilities.
- Against well-resourced adversaries, staying anonymous remains challenging.
Key Weaknesses
- Operational Security (OPSEC):
- Human error is a significant vulnerability.
- Maintaining strong OPSEC is critical to reducing risks.
- Technical Vulnerabilities:
- Traffic correlation and Sybil attacks pose significant threats.
- Browser and host operating system attacks need diligent mitigation.
Mitigation Strategies
- Strengthen OPSEC:
- Regularly review and improve your operational security practices.
- Isolation and Compartmentalization:
- Use virtual machines, physical isolation, and sandboxes to limit browser exploit impacts.
- Avoid installing Tor on your primary operating system for high-stakes situations.
- Non-Persistence:
- Utilize live operating systems like Tails and VM snapshots to avoid data retention.
- Employ secure deletion and full disk encryption techniques.
- High Security Settings:
- Use Tor Browser with maximum security settings and refrain from adding extensions.
- Consider using Hoonix or Tails for enhanced security.
- Layered Anonymizing Systems:
- Implement multiple anonymizing tools and off-site connections cautiously.
- Misconfiguration can increase risks, proceed with care.
- Continuous Monitoring:
- Regularly check the Tor Project blog for updates.
- Monitor Tor client and relay counts for anomalies.
- Assume Adversary Control:
- Assume adversaries control the network and locations you visit.
- Prepare for potential zero-day exploits and active attacks.
Why the Tor attack matters – A Few Thoughts on Cryptographic Engineering
A Critique of Website Traffic Fingerprinting Attacks | The Tor Project
Experimental Defense for Website Traffic Fingerprinting | The Tor Project
ListOfServicesBlockingTor · Wiki · Legacy / Trac · GitLab
While Tor offers strong anonymity, understanding its weaknesses and implementing comprehensive security controls can significantly enhance your privacy protection. Stay informed and vigilant to adapt to changing security landscapes.
NSA’s Tor De-Anonymization Tactics and Mitigation Strategies
Overview of NSA’s Techniques
- Quantum System & Fox Acid:
- The NSA uses systems like Quantum and Fox Acid to de-anonymize Tor users.
- These methods involve redirecting Tor traffic to exploit vulnerabilities.
- Partnerships and Monitoring:
- NSA’s collaborations with telecom firms enable extensive internet monitoring.
- They create fingerprints to identify Tor traffic and use these for targeted attacks.
- Fox Acid Server Exploits:
- Fox Acid servers are used to execute attacks on targets identified via Tor.
- Techniques include browser exploits, particularly targeting Firefox vulnerabilities.
- Man-in-the-Middle Attacks:
- The NSA employs these attacks using Quantum servers, impersonating trusted websites.
- These are difficult for non-state actors due to the required internet backbone control.
Mitigation Strategies
- Operational Security (OPSEC):
- Strong OPSEC is crucial; human errors are a major vulnerability.
- Regularly review and improve security practices.
- Isolation and Compartmentalization:
- Use virtual machines, sandboxes, and physical isolation to contain potential exploits.
- Avoid using Tor on primary systems for high-risk activities.
- Non-Persistence Techniques:
- Use live OS like Tails and VM snapshots to minimize data retention.
- Implement secure deletion and full disk encryption.
- Browser Hardening:
- Use Tor Browser with high security settings, disable scripts and plugins.
- Consider using tools like Hoonix for added isolation.
- Layered Anonymizing Services:
- Use multiple anonymizing services cautiously to avoid misconfigurations.
- Adding complexity can increase risk if not done properly.
- Continuous Monitoring and Updates:
- Stay updated with Tor Project announcements and security patches.
- Monitor for unusual Tor relay and client activity.
Attacking Tor: how the NSA targets users’ online anonymity | NSA | The Guardian
Understanding NSA’s sophisticated de-anonymization techniques highlights the importance of robust security measures. Proactive mitigation strategies can help maintain anonymity, but users must remain vigilant against evolving threats.
Tor Hidden Services and Access Methods
Setting Up Hidden Services
- What are Hidden Services?
- Hidden services are like relays that also offer web or other internet services accessible via a .onion URL.
- They mask the real IP address behind a Tor circuit for privacy.
- Setting Up a Hidden Service:
- Set up Tor normally and install your desired web service.
- Add specific configurations to your Tor config file to enable hidden services.
- Tor generates a public-private key pair for your service, stored as
Private_keyandhostname.
- Security Considerations:
- Ensure your web server is securely hardened to prevent leaking the real IP address.
- Tools like Hoonix can further secure your hidden service by routing it through a gateway.
Accessing Hidden Services
- Direct Access via Tor:
- Access hidden services directly through the Tor network using a Tor browser.
- This method maintains user anonymity and privacy.
- Tor to Web Services:
- Hidden services can be accessed from regular browsers via services like Tor2Web.
- Replace the .onion part of the URL with .onion.to or .onion.com for direct access.
- Limitations of Tor to Web:
- Tor2Web protects publishers but not readers, offering no anonymity or privacy.
- It’s a straightforward access method but lacks the protections of using the Tor network.
Hidden services provide a layer of anonymity for both service providers and users. However, when accessing these services, especially through Tor2Web, it’s important to understand the privacy limitations involved. Always prioritize secure configurations and consider potential risks when engaging with hidden services.
Navigating and Finding Tor Hidden Services
Challenges in Finding Hidden Services
- Non-indexed by Traditional Search Engines:
- The dark web is not indexed by common search engines like Google.
- Finding .onion links can be tricky as they are not easily searchable.
- Common Sources for Links:
- Popular places to find .onion links include Pastebin, Twitter, Reddit, and other forums.
- You can search for terms like “Pastebin Tor links” to find lists of .onion sites.
- Decentralized Nature:
- Tor is decentralized, meaning there isn’t a direct list of all hidden services.
- Some sites catalog known onion addresses, but caution is advised when accessing them.
Caution and Tips
- Use Reliable Sources:
- Be cautious of sites like the “uncensored hidden wiki,” as they might lead to unwanted content.
- Verify the reliability of hidden service directories before using them.
- Available Search Engines:
- Tor-specific search engines like Torch, Not Evil, and Sinbad can help, but their effectiveness varies.
- Lists of .onion addresses are often more reliable for finding specific services.
- Exploring Safely:
- Use trusted sources like Pastebin, Twitter, and Reddit to find links.
- Hidden wikis may provide additional starting points, but proceed with caution.
DARPA’s Memex Project
- Developing Advanced Search Tools:
- DARPA’s Memex aims to help law enforcement with domain-specific searches on the dark web.
- While intended to prevent crime, it raises privacy concerns for lawful users.
- Potential Implications:
- Memex has the potential to become a “Google of the Darknet.”
- Its evolution will impact privacy and anonymity seekers on the dark web.
Ahmia — Search Tor Hidden Services
Navigating the dark web requires caution and awareness of potential risks. While various methods and tools exist to find hidden services, always prioritize safety and verify sources before proceeding. Keep an eye on projects like Memex, as they may change the landscape of dark web search capabilities in the future.
Exploring Tor Applications for Mobile and Other Platforms
Mobile Tor Applications
- Orbot:
- Orbot is a Tor proxy app for Android developed by the Guardian Project.
- It functions similarly to the desktop Tor app and can be used with apps that support proxy features, like Twitter and DuckDuckGo.
- Note: It’s not personally tested by me.
- Orfox:
- Orfox is a Tor browser for Android, currently in beta.
- It offers Tor browsing capabilities on mobile devices.
- Onion Browser for iOS:
- This is the Tor browser equivalent for iOS devices like the iPhone.
- Also not personally tested by me.
Considerations for Mobile Use
- Privacy Concerns:
- Mobile devices are inherently less private compared to desktops.
- Use these apps where potential consequences of privacy breaches are minimal.
- They should not be considered as secure as the standard Tor browser for desktop.
Other Tor-Related Tools
- Tor Messenger:
- A cross-platform chat program that routes all traffic over Tor for enhanced security.
- Supports various protocols like XMPP (Jabber), IRC, Google Talk, Facebook Chat, Twitter, Yahoo, etc.
- Enables Off-the-Record (OTR) messaging by default and offers a user-friendly GUI with multiple language support.
- Still in beta, but promising for secure communications.
- OnionCat:
- A VPN adapter that connects computers or networks via VPN tunnels.
- Uses Tor or I2P networks for anonymous transport.
- Provides location-based anonymity while assigning unique private IP addresses to tunnel endpoints.
- An interesting concept for creating virtual networks with anonymized connections.
Orbot: Proxy with Tor – Guardian Project
Tor applications extend beyond the traditional desktop browser, offering various tools for secure and private communications. While mobile versions provide convenience, they come with inherent privacy limitations. Additional tools like Tor Messenger and OnionCat offer unique functionalities for secure messaging and network connections. Always consider the security implications and use these tools judiciously.
Conclusion
Tor is an anonymizing network that routes internet traffic through multiple servers to protect user privacy and access darknet sites. It has weaknesses, such as exit node vulnerabilities and browser exploits, but these can be mitigated by using HTTPS, keeping software updated, and combining with tools like VPNs. Tor is not foolproof against state-level adversaries but offers significant privacy benefits when used correctly. Understanding Tor’s limitations and employing best practices are crucial for maintaining anonymity online.


