Table of Contents
We understand the basic concepts of encryption. We need to learn about different types of encryption, such as symmetric and asymmetric encryption, as well as hash functions, SSL, TLS, and certificates. Additionally, we should be aware of SSL stripping and the inherent weaknesses of encryption. Mastering these topics is crucial for selecting appropriate security measures to mitigate risks.
Symmetric Encryption
here’s the deal with symmetric encryption. To make smart choices about your privacy and security, you don’t need to dive deep into the math, but you should understand the basics. Encryption is basically a way to turn readable data (called plaintext) into something that looks like gibberish (ciphertext). This keeps your data safe when you store or send it.
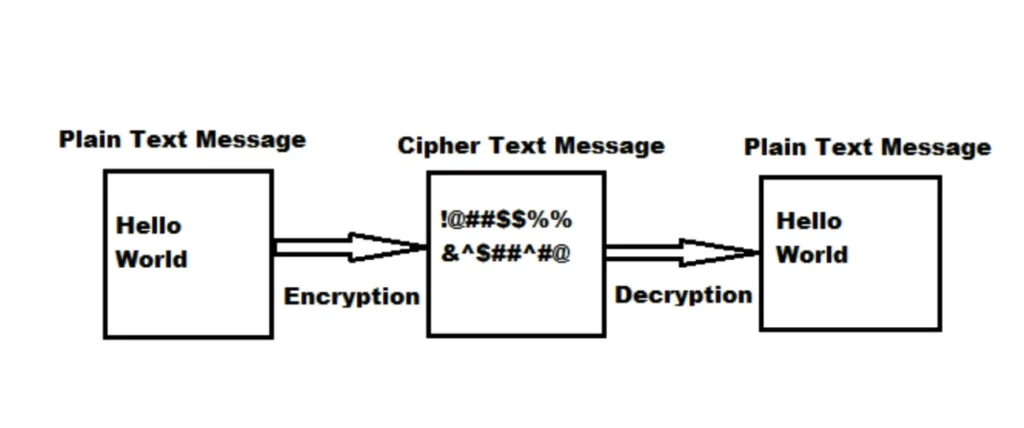
When you want to read that gibberish again, you use decryption, which turns it back into plaintext. A great example of this is HTTPS—when you see that in a URL, it means your browsing data is secure and no one can snoop on what you’re doing online, except for the destination website itself.
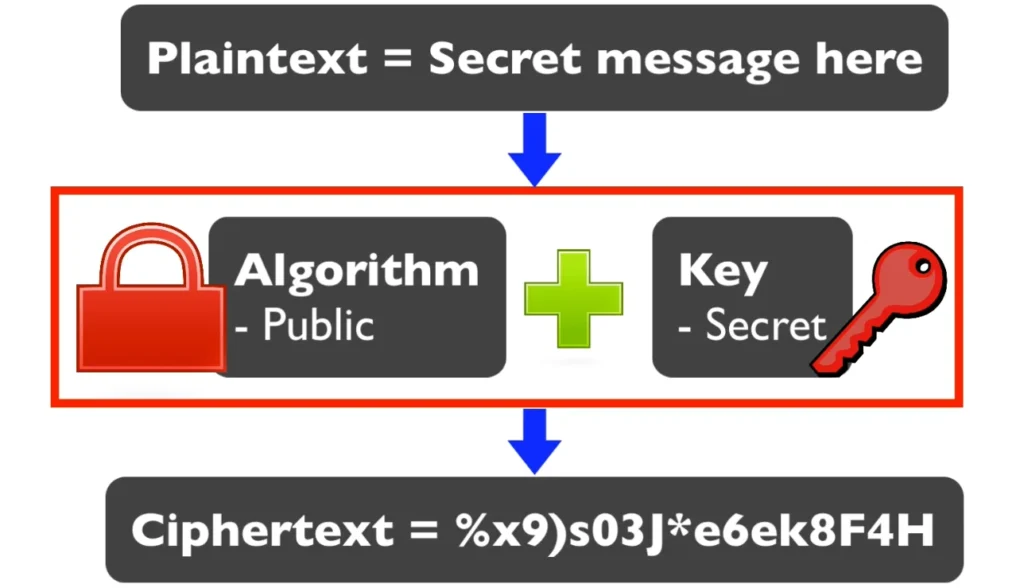
Now, symmetric encryption has two main parts: the algorithm and the key. The algorithm is usually public and has been tested a lot to make sure it’s strong, while the key is your secret password. Think of the algorithm like a padlock and the key as the key to that lock. The way the algorithm and key work together determines how your plaintext gets scrambled.
Let’s say I want to send a file to my buddy Bob, but I want to keep it private. I can use WinZip, which is a tool that compresses files but also has an option to encrypt them. When I go to encrypt the file, I can choose different levels of encryption, like 256-bit AES (which is strong) or 128-bit AES (less strong).
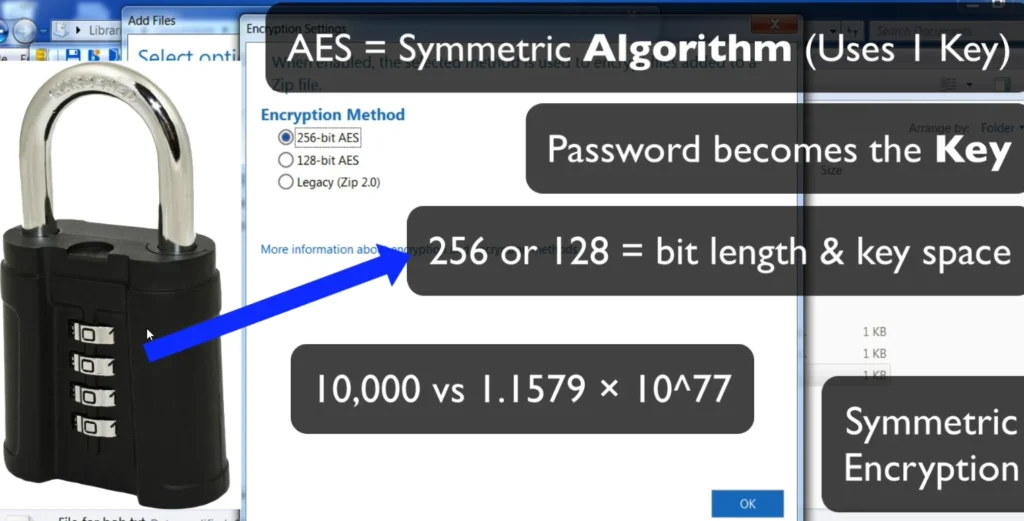
The password I create turns into a key through something called a key derivation function. So, the stronger the password, the harder it is to crack. For example, 256-bit AES has an absurd number of possible keys—like 1.1579 × 10^77—which makes it nearly impossible to guess even with the most powerful computers.
If someone tries to crack the key by checking every possible option, that’s called a brute force attack. There’s also a dictionary attack, which uses common words found in dictionaries, and a hybrid method that combines human behavior patterns with both previous methods.
Now, back to WinZip, when I set my password, if it’s strong, I can send the encrypted file to Bob. Even well-resourced entities like governments would struggle to crack AES encryption as long as the password is solid. We’ll talk more about strong versus weak passwords later.
For symmetric encryption, you’ll come across algorithms like:
- DES
- Triple-DES
- Blowfish
- RC4
- RC5
- RC6
- AES (which is the go-to option)
In everyday life, you’ll find symmetric algorithms used all over the place, like in HTTPS, file encryption, and VPNs. For the best protection, go for AES 256 and steer clear of weaker options like RC4 and DES if you can.
Asymmetric Encryption
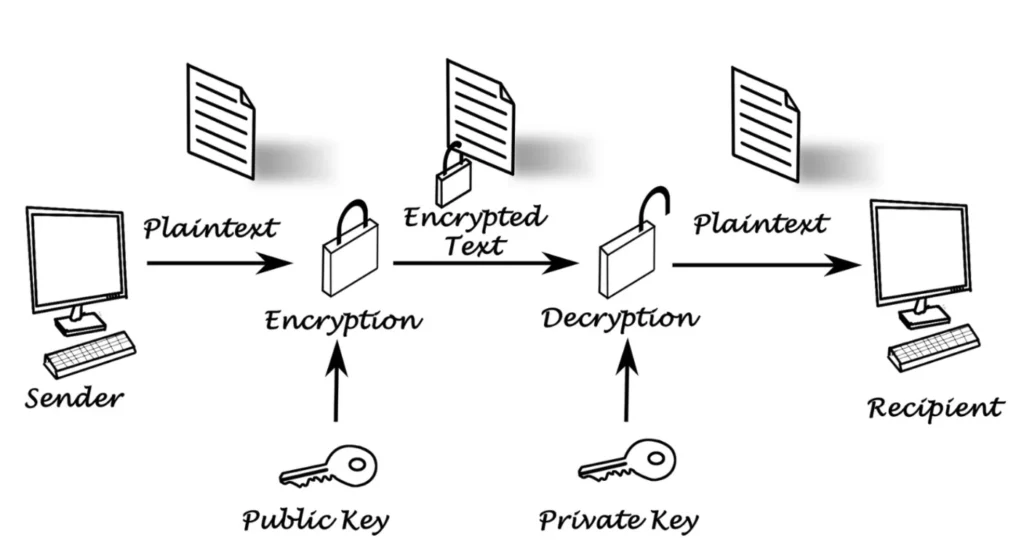
We just encrypted a file for Bob using AES and a strong password, but now we have to figure out how to get that password to him without sending it over email. Sending it that way isn’t secure. We could call or text him, but that’s not really practical for large-scale use. This is where asymmetric encryption comes in, which uses two keys instead of just one—often referred to as public and private keys.
So, to sum it up:
- Symmetric encryption uses one key (private).
- Asymmetric encryption uses two keys (public and private).
Smart folks came up with this idea based on certain complex math problems, but you don’t need to dive into the details to keep your data safe. You just need to know the basics to make smart choices about which algorithms and systems to use.
Some common asymmetric algorithms you might bump into include:
- RSA
- Elliptic Curve Cryptography (ECC)
- Diffie-Hellman (DH)
- El Gamal
RSA is one of the most well-known and is based on the difficulty of breaking down large numbers into their prime factors. ECC is gaining popularity because it’s based on elliptic curve math, and Diffie-Hellman is valued for its forward secrecy. El Gamal also relies on discreet algorithms in finite fields.
These asymmetric algorithms help solve the problem of securely exchanging keys and allow for digital signatures. Basically, you can send Bob your secret key securely without worrying about someone else intercepting it.
So here’s how it works:
- The public key is meant to be shared with everyone, while the private key is kept secret.
- These two keys are mathematically linked and generated together.
When you see a website using HTTPS, it’s using a public-private key pair to share a symmetric session key for encrypting data.
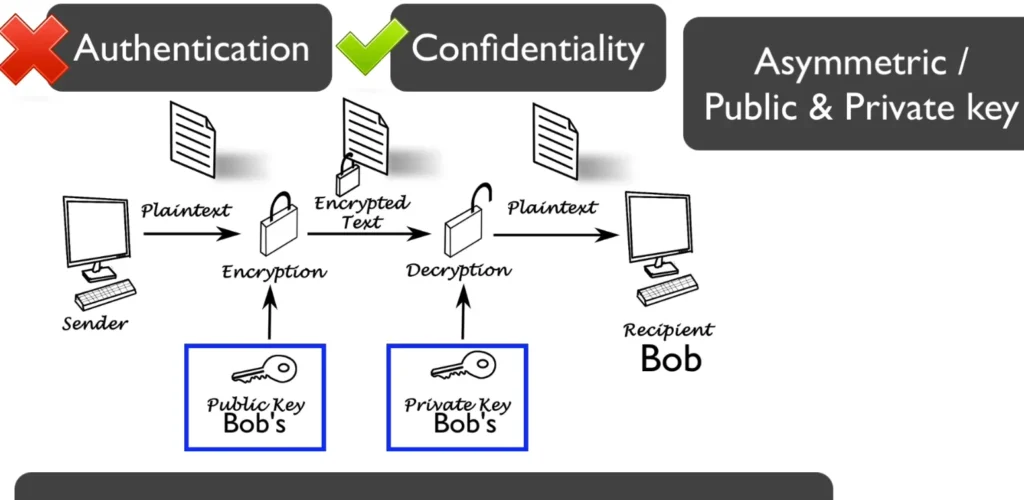
Here’s the catch with asymmetric encryption: if you encrypt a message with one key, you need the other key to decrypt it. If you encrypt with the private key, you need the public key to decrypt. Conversely, if you encrypt with the public key, you need the private key for decryption.
So why would you want to use both keys? Let’s look at two scenarios:
- Using Bob’s Public Key: If you’re sending Bob a file and you encrypt it with his public key, only he can decrypt it with his private key. This ensures privacy, but it doesn’t confirm who sent it—anyone could use his public key to encrypt a message.
- Using Your Private Key: If you encrypt a message with your own private key, you’re showing Bob that it’s really you sending it. This gives him confidence that only you could have sent that message since only you have the corresponding private key.
In this case, it’s called an “open message format” because anyone with your public key can decrypt it, confirming you’re the sender.
Asymmetric encryption provides several security services like confidentiality, authentication, non-repudiation (you can’t deny sending a message), and integrity (the message hasn’t been altered).
Crypto systems combine different encryption technologies, like PGP or BitLocker, to provide these services. For example, to send Bob the encrypted file, you’d use his public key, and you only need to receive that key securely once.
However, one challenge with asymmetric encryption is key exchange—it can be complicated and not user-friendly, which is partly why it hasn’t been widely adopted in email systems.
Now, let’s talk about the pros and cons:
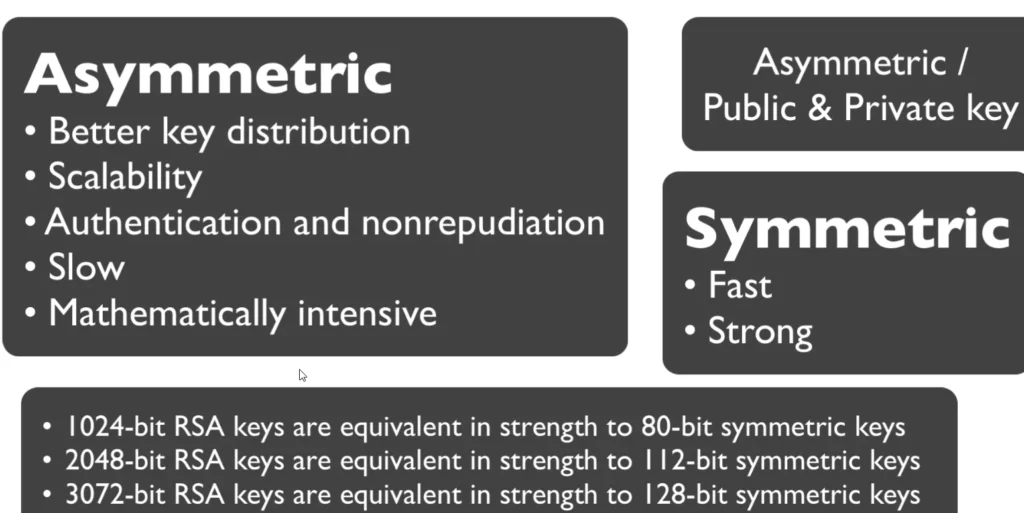
Pros of Asymmetric Encryption:
- Better key distribution—Bob can put his public key online, and anyone can send him encrypted messages.
- Scalability—no need to share a password with everyone since you can use the public key.
Cons:
- Slower than symmetric systems.
- More mathematically intense and requires more CPU power.
1024-bit RSD keys are equivalent in strength to 80-bit symmetric keys
2048-bit RSD keys are equivalent in strength to 112-bit symmetric keys
3072-bit RSD keys are equivalent in strength to 128-bit symmetric keys
15360-bit RSD keys are equivalent in strength to 256-bit symmetric keys
To get the best of both worlds, we often use hybrid systems. For example, public-private keys can be used to exchange keys, and symmetric algorithms like AES can encrypt the actual data. HTTPS using TLS and SSL is a great example of this hybrid approach.
Hash Functions
Let’s talk about hash functions and their importance in securely exchanging keys. Before sharing a key with Bob, we need to ensure that Bob is actually who he claims to be. If a malicious actor is in the middle, they might attempt to send a fake public key, pretending to be Bob’s. Therefore, we can’t just trust a public key—we need to verify its authenticity first. This is where hash functions and digital signatures come into play; they help us verify the legitimacy of both the sender and the receiver.
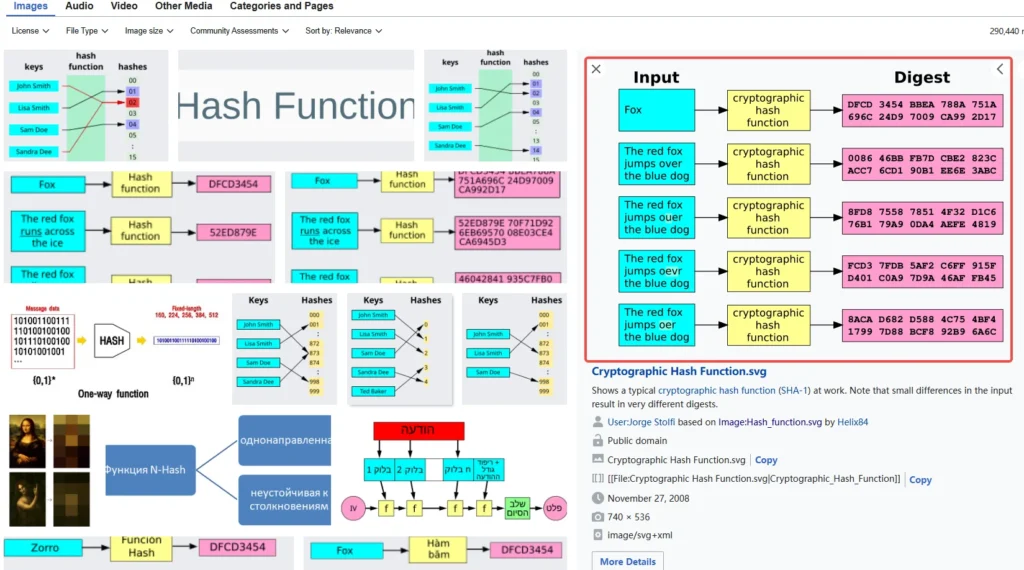
A hash function takes data of any size (like an email or a file) and converts it into a fixed-size string of characters. For example, if you input “fox,” the hash function produces a hash, which can also be called a message digest. Here’s a cool fact: you can never reverse-engineer a hash back to its original input. This makes hash functions one-way and doesn’t require any keys—just the input and the hash function.
Hash functions provide a way to ensure data integrity—they can detect unintentional changes but can’t confirm if something was intentionally altered. Common hash functions include MD5, SHA-1, SHA-256, and others. Today, you should really use at least SHA-256 or better for crypto systems.
How Hash Functions Work
When you hash a file (like downloading software), you can verify its integrity by checking the hash. For instance, let’s say you download TrueCrypt, a disk encryption tool. The website provides a hash for the file. After downloading, you can use a tool like Quick Hash to check that the hash matches. If it does, you can be pretty sure the file hasn’t been tampered with.
However, if the website itself is compromised, an attacker could change both the download and the hash, making the hash useless for detecting that kind of manipulation. This is why we need digital signatures and certificates to verify the website’s authenticity.
Password Hashing
Another practical example of hash functions is in password management. Storing plain text passwords in a database is dangerous since if that database is hacked, your password is compromised. Instead, passwords should be hashed using a password key derivation function. For instance, Windows converts user passwords into hashes and stores them in a secure place called the SAM database.
HMAC
Hashes can also be used to create a Hash Message Authentication Code (HMAC). This involves taking a message and a pre-agreed shared secret, hashing them together, which helps provide both authentication and integrity.
So, while you don’t need to know all the nitty-gritty details, understanding that hash functions are a key part of crypto systems will help you grasp how secure communication works.
Digital Signatures
A digital signature is essentially a hash value that we just discussed. It’s the fixed-length result of a hash function, and it’s encrypted using the sender’s private key to create what we call a digital signature or a signed message. Think of it as a stamp of approval from the signer, guaranteeing the authenticity of the signed content.
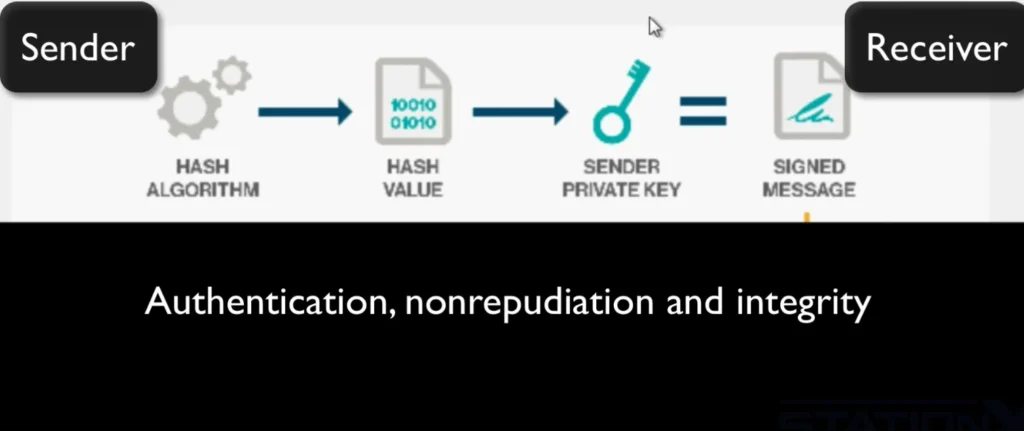
So, what does a digital signature provide?
- Authentication: Since it’s encrypted with the sender’s private key, only the person who owns that key can create it.
- Non-repudiation: The sender can’t deny having sent the message since their private key was used.
- Integrity: It ensures that the content hasn’t been altered because it’s based on a hash.
Digital signatures are often used for software, like drivers or certificates, to validate that everything is genuinely from the claimed sender and that it hasn’t been tampered with.
For example, let’s say you download a Chrome installation file. If you check its properties, you’ll find a section for digital signatures. When you click on it, you might see that this software has been signed by a trusted authority like VeriSign. They used their private key to digitally sign the software, indicating that it’s legitimate and unchanged.
To verify this digital signature, we reverse the process:
- You take the signed message and use the sender’s public key (in this case, VeriSign’s) to decrypt it and reveal the hash.
- Then, you run the downloaded file through the same hashing algorithm to generate a hash on your end.
- Finally, you compare the two hashes. If they match, the software is intact and authentic.
This all happens behind the scenes, so you might not even notice it. If the verification fails, you’ll typically see warning messages, like “Windows cannot identify the publisher of this driver software.” This means the driver either lacks a digital signature or that your OS doesn’t trust the certifying authority (like VeriSign).
Windows 10 has introduced a feature called Device Guard, which uses digital signatures to control what software can run on your system. Device Guard only allows certain signed files to execute, aiming to prevent malware from running since most malicious software won’t have valid signatures.
To wrap it up:
- A digital signature combines a hash value encrypted with the sender’s private key.
- It provides authentication, non-repudiation, and integrity.
- If you also encrypt the content along with the digital signature, you’ll get confidentiality too.
Digital signatures ensure that the software or message came from the right sender and that it hasn’t been changed after being sent.
Secure Sockets Layer (SSL) and Transport layer security (TLS)
Having introduced the topic, let’s break down SSL and TLS. Both are encryption protocols designed to ensure secure communication over networks like the Internet. SSL is the older version, while TLS is the newer version. Unfortunately, many people habitually refer to both as SSL, which can be confusing. Some websites still use the older SSL for compatibility reasons, despite its known security vulnerabilities.
What SSL and TLS Do
When you see “HTTPS” in a URL, that means TLS is being used. But it’s worth noting that TLS can work with protocols beyond just HTTP, like FTP or VPNs. TLS is crucial for online security and privacy since it’s the most common way to encrypt data on the Internet.
Key Features of TLS
- Privacy: TLS encrypts the data being sent, protecting it from eavesdroppers.
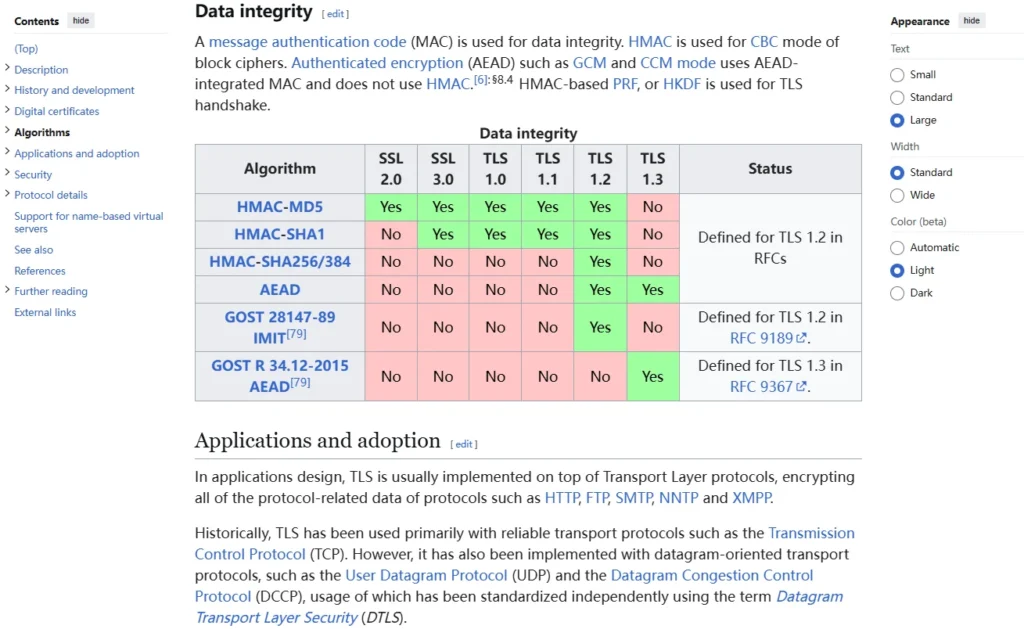
- Integrity: It uses message authentication codes (MACs) to ensure the data hasn’t been altered during transmission.
- Authentication: It verifies the identity of the communicating parties, usually requiring the server to have a digital certificate.
For instance, when your browser connects to your online bank, that communication is encrypted from start to finish using TLS. A symmetric algorithm, like AES, is often used for this encryption, and the keys are generated uniquely for each session.
Key Negotiation and Security
Before any data is sent, the server and client negotiate which encryption methods and keys to use. This negotiation is secure and can’t be intercepted by an attacker. If anything is modified during this process, it can be detected. The identities of the parties involved are authenticated using public key cryptography and digital signatures.
Forward Secrecy
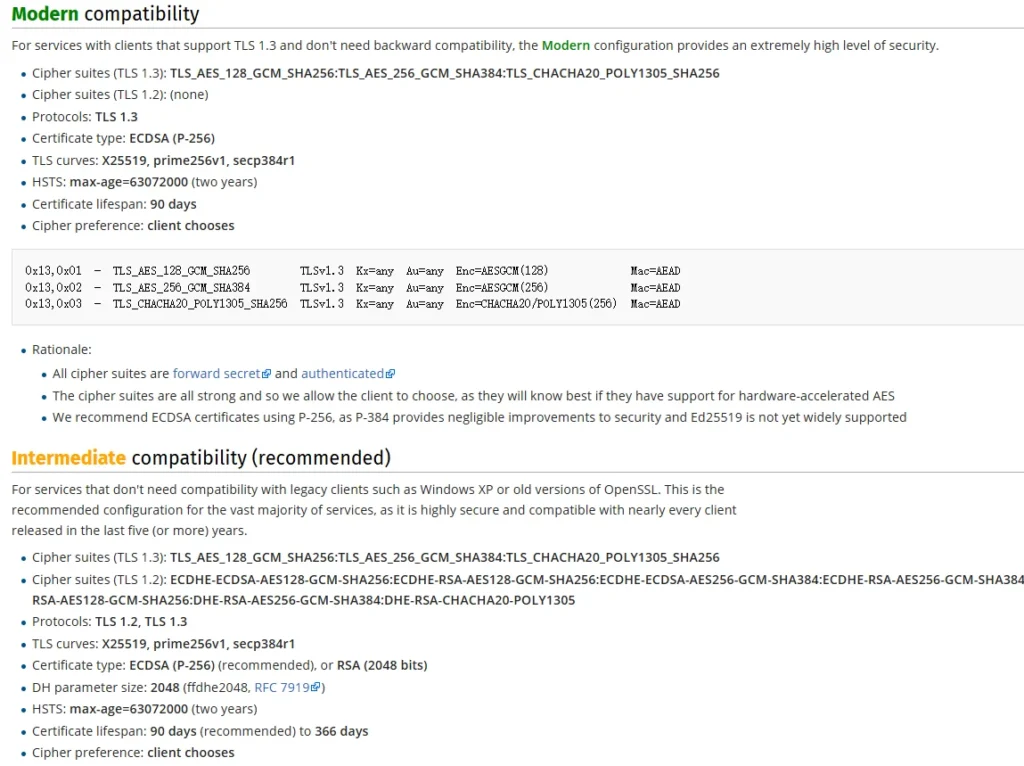
One of the best practices in TLS is using “forward secrecy.” This means that even if a server’s private key gets compromised, previous session keys can’t be decrypted because each session has a unique key. This significantly enhances data protection.
Symmetric Algorithms
When it comes to the actual data encryption, symmetric algorithms like AES are preferred because they are faster. There are various symmetric encryption options, and knowing which ones are secure is important. AES is a strong choice, but it’s essential to be aware of its mode of operation, which determines how it scrambles the data.
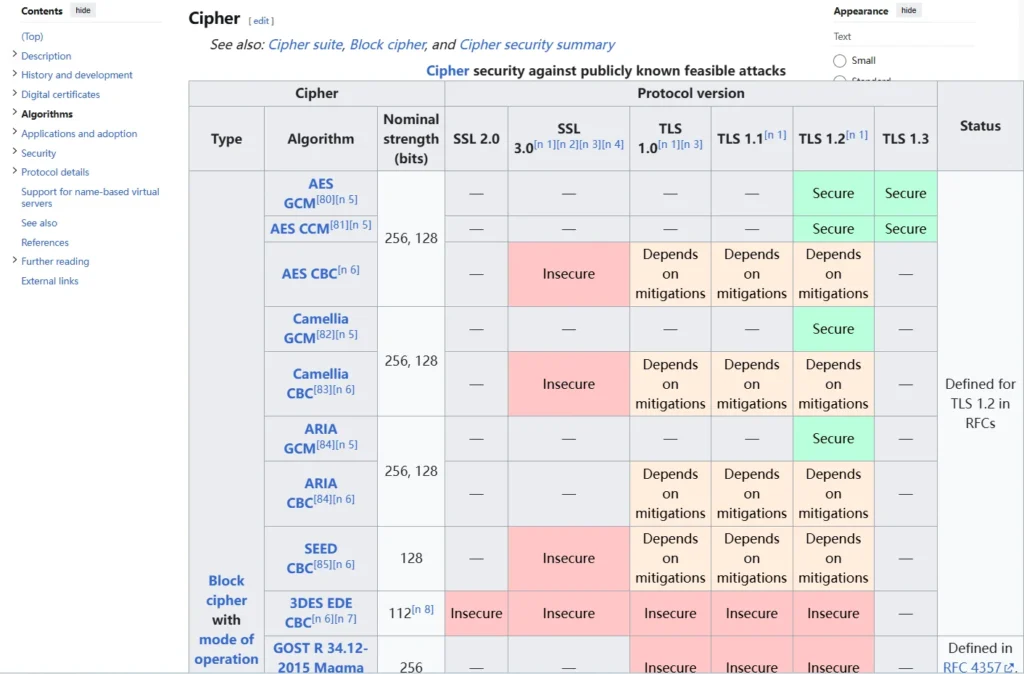
TLS Versions
When discussing TLS, you might see various versions—SSL 2.0, SSL 3.0, TLS 1.0, and so on. TLS 1.3 is the latest and most secure version, but it might not always be compatible with older browsers. Ensuring you’re using TLS 1.0 or above is generally recommended.
Hashes and MACs
For maintaining data integrity, older hash functions like MD5 and SHA1 are outdated and should be replaced with newer versions like SHA-256 or SHA-384.
Vulnerabilities and Updates
TLS has gone through several updates to address vulnerabilities over the years, like the BEAST, CRIME, and POODLE attacks. Browsers and servers need regular updates to stay secure.
Cipher Suites
When we talk about the combination of algorithms used in TLS, we refer to them as cipher suites. It’s crucial to choose strong and compatible cipher suites. Resources like Mozilla’s documentation can help you find the best options.
Configuration Tools
If you’re configuring a server, there are tools available to generate secure configurations, ensuring you’re not using outdated protocols like SSL v2 or v3.
Summary
In a nutshell, SSL and TLS are essential for securing online communications, and while TLS is preferred, both are crucial in understanding how our data is protected online. Keeping software up to date and using strong encryption methods are key steps in maintaining security.
SSL Stripping
Let’s dive into SSL stripping! This is a type of “man-in-the-middle” attack that allows an attacker to intercept and manipulate the traffic between a user and a website. The attacker acts as a proxy, converting secure HTTPS connections into unsecure HTTP connections.
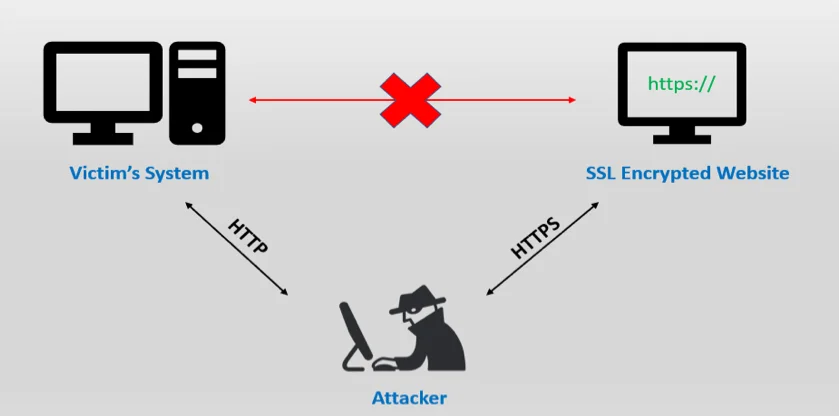
How SSL Stripping Works
Imagine you’re trying to visit a website. Usually, you might just type in the website’s name without the “https://”. Most browsers will then connect to the HTTP version of the site and might get redirected to the HTTPS version via a 302 redirect. Now, SSL stripping takes advantage of this process.
When you try to connect:
- The attacker intercepts your HTTP request and forwards it to the server.
- The server thinks it’s communicating with your browser and sends back a HTTPS redirect.
- Instead of sending you straight to the HTTPS site, the attacker sends back an HTTP version, making it look identical to the original site. Most people won’t even notice the missing “https://”.
Getting in the Middle
To execute this attack, the attacker must be able to sit in the middle of the traffic. This is easier if you’re on someone else’s network, like at a café or workplace, because the network administrators can see and control the traffic. Governments can also do this since they control many network pathways.
However, a random attacker from a distance would struggle to position themselves in the middle. It’s much simpler for them to target your device directly instead of trying to intercept traffic.
Local Network Attacks
If the attacker is on the same local network, they can use a method called ARP spoofing. This involves sending fake ARP packets that make your machine think the attacker’s device is the default gateway (router). As a result, all your traffic gets sent through the attacker’s device first, where they can strip out the SSL.
Tools for SSL Stripping
There are tools to facilitate SSL stripping attacks, like SSL Strip created by Moxie Marlinspike, and tools included in Kali, like Ettercap and Arpspoof. If you want to try it out, SSL Strip provides commands for setting up the attack.
Rogue Access Points
Another method to perform SSL stripping is by setting up a rogue access point. This fake Wi-Fi network can trick users into connecting, allowing the attacker to intercept traffic and remove SSL encryption.
Prevention Measures
To protect against SSL stripping, it’s crucial to:
- Always check for HTTPS in the URL.
- Use encrypted tunnels like SSH or VPNs to ensure your traffic is secure, regardless of the network.
- Be cautious when connecting to untrusted networks.
Local Network Detection
On your local network, you can use tools like Arpwatch to monitor for ARP spoofing. If you manage the server, enabling HTTP Strict Transport Security (HSTS) can help by instructing browsers to only accept HTTPS connections.
Network Isolation
Implementing virtual LANs (VLANs) can also enhance security by preventing traffic from different network segments from interacting. Firewalls can be configured to control traffic flow, adding another layer of protection.
So, that’s a wrap on SSL stripping! It’s a straightforward attack, but being aware of it and taking preventative measures can keep your data safe.
HTTPS (HTTP Secure)
You probably know that HTTP is the protocol used by websites, which is why we see URLs starting with HTTP://. When you visit a site like www.google.com, it typically connects to the HTTP version. This protocol sends data in plain text, which means anyone can see the information being transmitted.
What Happens with HTTPS?
When you switch from HTTP to HTTPS, you’re using HTTP over TLS (or SSL). HTTPS adds a layer of security by using TLS to encrypt data, authenticate the server, ensure message integrity, and optionally authenticate the client.
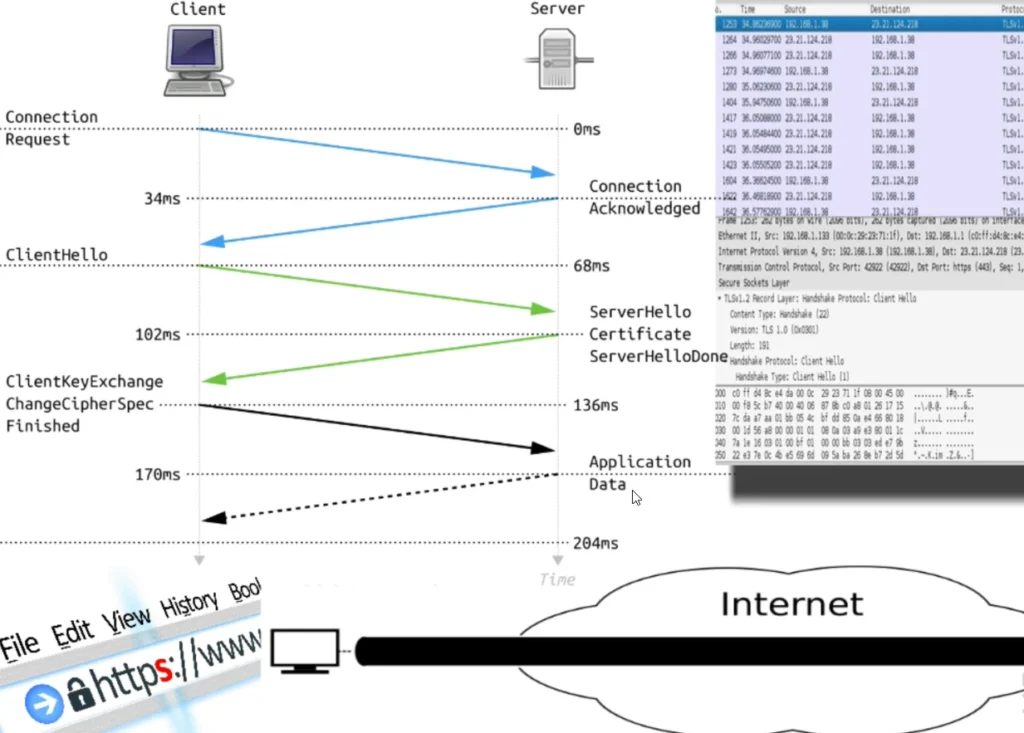
How It Works
When you access an HTTPS site:
- The web server initiates a secure session.
- The server sends a message to your browser, indicating that a secure connection should be established.
- Your browser then sends back its security parameters, like which algorithms and keys it supports. This process is known as the “handshake phase.”
- The server authenticates the client by sending a digital certificate. If the client trusts this certificate, the session continues.
Mutual authentication can happen if the server requests a digital certificate from the client, which isn’t very common in everyday browsing but is used in more secure environments.
Establishing a Secure Channel
The client generates a symmetric session key (like using AES) and encrypts it with the server’s public key. This encrypted key is then sent to the web server. Both the client and the server use this symmetric key to encrypt any data sent back and forth, establishing a secure channel.
Indicators of Security
You’ll notice a padlock icon in the browser’s address bar when you’re on an HTTPS site, indicating that TLS is being used. If it’s not shown, that means your connection isn’t secure, and your data is being sent in plain text.
Checking Encryption Details
If you click on the padlock icon, you can often see technical details about the encryption algorithms being used. For example, it might show that the site uses TLS with AES as the symmetric key and SHA256 for data integrity. Tools like Wireshark can help you analyze this traffic in real time.
Testing SSL Configurations
You can use sites like SSL Labs to check the security of a specific HTTPS site. Just enter the URL, and it’ll give you details about the encryption options the site supports and a rating of its security.
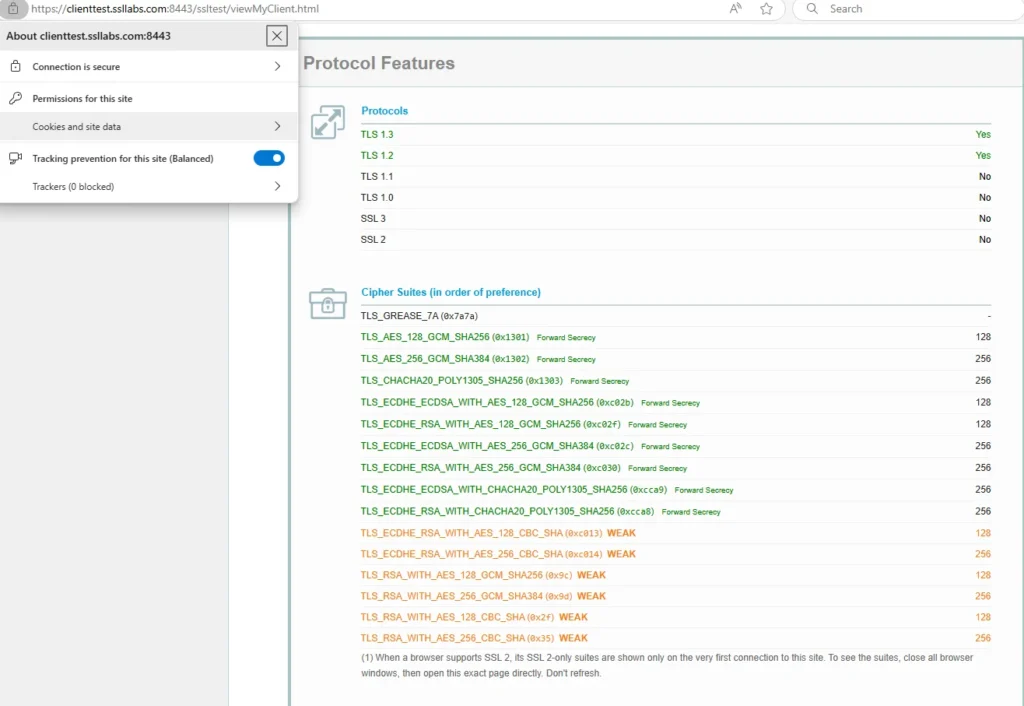
Understanding Firefox Security Indicators
In Firefox, different icons and colors indicate the level of security:
- Gray Globe: No identifying information; not fully secure.
- Gray Triangle: Partially secure; contains unencrypted elements.
- Orange Triangle: Partially secure with unverified identity.
- Gray Padlock: Verified address; encrypted connection.
- Green Padlock: Verified with an Extended Validation certificate, meaning more rigorous checks were performed on the website owner.
Summary
HTTPS is vital for secure communication online. It encrypts your data, verifies the identity of the site, and helps ensure that no one can intercept your traffic. Always look for that padlock icon and check the details to make sure your connection is safe!
Digital Certificates
When we want to securely exchange keys with someone like Bob, we need to make sure Bob is really who he says he is. If an attacker is in the middle, they could easily send a fake public key posing as Bob. That’s where digital certificates come in, using hashes and digital signatures to authenticate.
What are Digital Certificates?
Digital certificates are electronic documents that help confirm the identity of a party (like a website) and contain important information, such as the owner’s details, their public key, and a digital signature from a trusted certificate authority (CA). One of the most widely used standards for these certificates is X.509.
When you visit an HTTPS website, the server presents its digital certificate, which includes:
- The public key you’ll use to encrypt data.
- A digital signature from the CA, verifying that the certificate is legitimate.
The Chain of Trust
For example, if you see that a site is verified by DigiCert, that means DigiCert is the authority vouching for that website’s identity. Clicking on the padlock icon in your browser will let you view the specific certificate and its details.
- Valid for Domain: The certificate is only valid for the specific domain.
- Public Key: This is an RSA public key. Anything encrypted with this can only be decrypted by the corresponding private key.
- Digital Signature: It’s created using SHA-256 and RSA. The signature is a hash value encrypted with the CA’s private key.
Verifying Validity
To ensure the certificate is valid, your browser or operating system checks it against a list of trusted root certificates. These root certificates are issued by trusted CAs, so if they say a certificate is good, you can trust it too.
You can view the trusted CAs in Firefox by going to: Options -> Advanced -> Certificates -> View Certificates -> Authorities. There, you’ll find a list of all the root CAs your browser trusts.
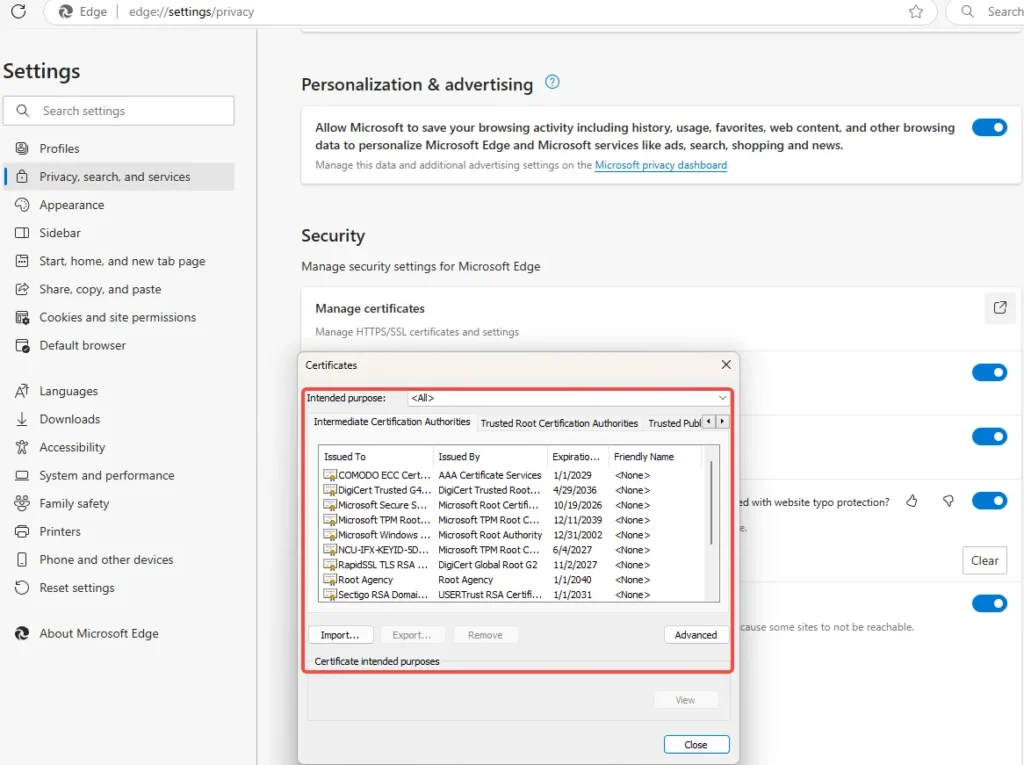
Understanding Self-Signed Certificates
You might also come across self-signed certificates. For example, CA Comodo might have a self-signed certificate, which means it’s signed by itself rather than a trusted CA. The authority of a CA comes from their ability to meet various security requirements set by organizations that oversee them.
In Summary
Digital certificates are crucial for secure communication online. They help authenticate identities and establish trust through a chain of trust. When you see that padlock icon, it means the site is verified, and your data transmission is encrypted. Always check the certificate details to ensure you are connecting to the right site!
Certificate Authorities and HTTPS
We’re diving into Certificate Authorities (CAs) and HTTPS. Basically, HTTPS relies on certificates to ensure that a website is genuine and that its public key is legit. Without these certificates, HTTPS security falls apart.
The Problem with Certificates
The whole certificate system is pretty fragile and can be attacked. If there’s a weak link in the chain of trust, it can lead to the creation of fake certificates that people trust. If someone can get a fake certificate that your browser accepts, they can intercept and read your HTTPS traffic without you even knowing. Everything might look normal—padlock icon and all—but the attacker can decrypt the data because they possess the private key.
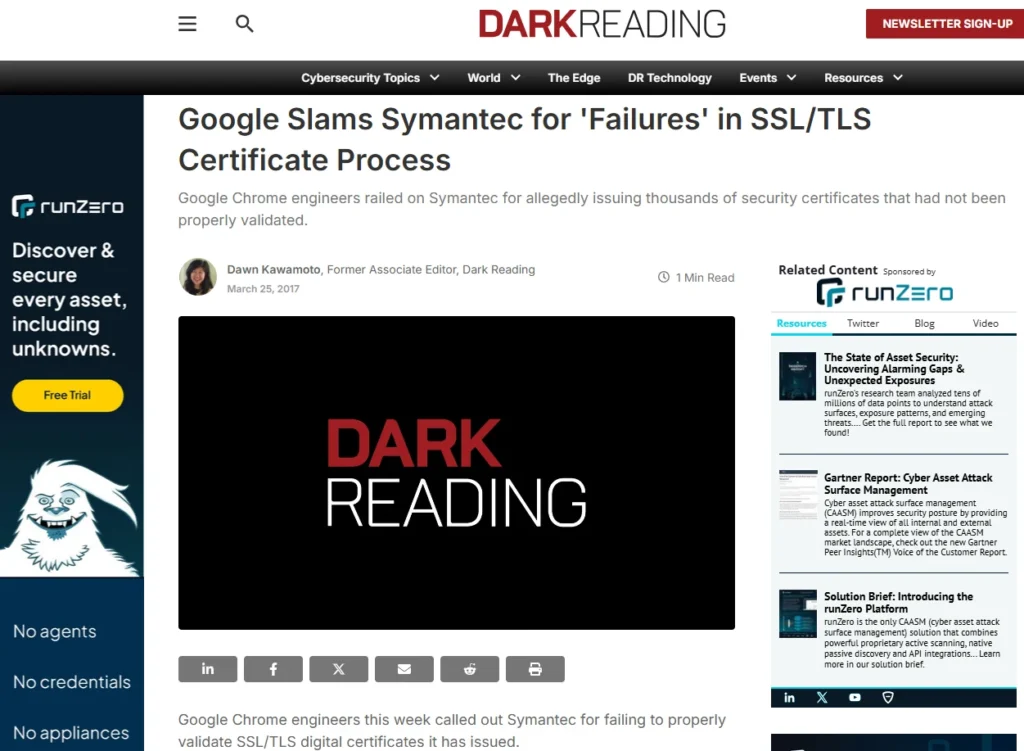
Real-World Examples
Now, let’s get into some examples of why we can’t fully trust certificates. One major issue comes from the certificate authorities themselves. Recently, there was a headline about Google confronting Symantec because they issued certificates for Google that Google never requested. Symantec is a big player in certificate issuance, and they should set the standard. Initially, they claimed only 23 unauthorized certificates were issued, but after scrutiny, it turned out there were over 2,000. This shows how serious the issues with CAs can be.
There was also a case with bogus certificates issued for Google domains by a smaller authority based in Egypt. Even large CAs can mess up, and those certificates would still be trusted by your browser.
Too Many Trustworthy Parties
There are over 1,400 certificate authorities that browsers like Microsoft and Mozilla trust. That’s a lot of potential sources of error! Some countries even have their own CAs, which can lead to nation-states issuing fake certificates. This means countries like the US, UK, China, and Russia could potentially issue fake certificates and decrypt HTTPS traffic, making it look normal to you while they can read it.
Issues with Certificate Standards
The X.509 standard for certificates has its flaws too. It’s poorly designed and flexible, which has led to vulnerabilities. For example, there were incidents where people got certificates for domains they didn’t own due to flaws in the issuance process.
Protecting Yourself
What can you do to avoid these risks? Here are some strategies:
- Reduce Trusted Certificates: You can check the certificates your browser trusts and remove the ones you think are unnecessary. Most sites don’t need many certificates.
- Monitor for Changes: Use add-ons like “Certificate Patrol” in Firefox to alert you when a site’s certificate changes.
- Certificate Pinning: If you manage a server, you can use certificate pinning so that your application only accepts a specific certificate or public key. This can prevent man-in-the-middle attacks.
- Stay Anonymous: Using methods like VPNs or Tor can help anonymize your traffic, making it harder for attackers to associate it back to you, even if they can read it.
- Use VPNs: A VPN can help protect your data, especially if you’re in a location where you might be at risk of fake certificates being issued.
In summary, while HTTPS is generally secure, there are vulnerabilities, especially related to certificate authorities and their practices. To protect yourself, use multiple layers of security—known as defense in depth—and be vigilant about the certificates your browser trusts.
End-to-End Encryption (E2EE)
This is when the data is encrypted by the person sending it and only decrypted by the person receiving it. It’s a solid way to keep your data safe while it’s being sent, especially if you’re worried about tracking, mass surveillance, hackers, and all that jazz.
Why E2EE Matters
With everything going on, using HTTPS across all websites has become crucial, no matter what type of data you’re sending. As we dig deeper into how tracking, mass surveillance, and browser hacks work, you’ll see just how essential end-to-end encryption really is.
Examples of E2EE
There are several technologies that use end-to-end encryption, like PGP, S/MIME, and OTR (which stands for Off-the-Record). Protocols like SSL and TLS can also be set up for E2EE when implemented correctly. Companies that create software with end-to-end encryption and zero-knowledge systems can’t reveal what you’re communicating, even if they’re pressured to do so. That’s the beauty of E2EE combined with zero-knowledge—your data stays private.
We’ll cover various software examples that use these features throughout the course. Some popular messaging apps that provide end-to-end encryption are Signal, Chat Secure, and Crypto Cat.
The Impact of Widespread E2EE
If everyone started using end-to-end encryption for all their online activity, all the traffic would look alike. But when only a few individuals use it, those who do stand out as different. E2EE protects your data while it’s on the move, but keep in mind it doesn’t secure the data once it’s received. So you’ll need other protective measures for that.
Steganography
It’s the art of hiding information or files within other non-secret text or data. Think of it as “hiding in plain sight.” For instance, you can hide a text file with secret info inside an image file, like a picture of a dog. The image looks totally normal, but it contains a hidden message. The file that holds the secret data is called the “carrier.”
How It Works
The cool thing about these modified carriers is that they look just like the original files with no noticeable changes. The best types of carriers are videos, images, and audio files since they’re common and not suspicious. But remember, steganography is different from encryption. The data is just hidden, not encrypted. Someone with the right skills could easily compare the original and modified files and figure out that steganography was used and what the secret message is.
If you’re using videos or images to hide messages, be careful where you upload them. For example, uploading to YouTube would mess up the hidden message because of compression. Sending a video via email, however, should work just fine.
Why Use Steganography?
Steganography is useful when you want to hide the fact that you’re sending a secret message. If you’re just using encryption, it’s pretty obvious you’re trying to keep something private. But with steganography, it’s not apparent at all that you’re sending a message. Some tools even combine encryption with steganography to make it even harder to detect.
One tool I recommend for Windows is called OpenPuff. Let’s walk through how it works. You can download it from their website. Once you start the program, you’ll see options for hiding or unhiding data within a carrier.
Using OpenPuff
To hide some data, click on “Hide.” You’ll need to enter three passwords—these are part of an algorithm that helps with the steganography process. Make sure to use complex passwords for better security. You add your carrier (for example, the dog picture), then select the secret message you want to hide.
You can even add a decoy message. This is where plausible deniable encryption comes in—if someone suspects you’re hiding something and asks for the password, you can give them the decoy password, which only reveals the decoy message instead of the actual secret.
After hiding the data, you’ll have a carrier file that now contains both the decoy and the real message. The neat part is that if you compare it to the original file, there won’t be any noticeable difference.
Caution with Carriers
It’s important not to use a file from the internet without modifying it first, as someone could compare it and discover the steganography. Always resize or compress a downloaded file or, better yet, use your own.
When you want to unhide the data, just add the carrier file and enter the passwords, and you’ll extract your secret message. If you need to, you can use the decoy to maintain plausible deniability.
Other Tools
There are other tools for steganography as well. For example, one lets you encode text into spam-like text, which you could send in an email. Just keep in mind that it doesn’t include encryption, so you’d want to encrypt the text first if privacy is a concern.
If you’re curious to explore more steganography tools, there are plenty of resources out there for different platforms.
How Security and Encryption is Really Attacked
We’ve covered a lot about encryption, and it’s truly a powerful tool for privacy and security. In fact, I’d argue that encryption is one of the few security measures that actually works. Because it’s so effective, attackers usually won’t go straight for the encryption itself; instead, they’ll try to work around it.
How Attackers Operate
Experienced adversaries always go for the “low-hanging fruit.” They’re not going to brute-force a password for your disk encryption when it’s way easier to install a keylogger on your system, peek over your shoulder, or send you a phishing email. So, they focus on ways to bypass encryption instead.
The Weak Link Phenomenon
This brings us to the “weak link phenomenon” in security. The overall strength of your security is only as good as its weakest link. Often, good encryption is a strong link, but humans tend to be the weakest link. In the OPSEC (operational security) section, I cover how human errors can compromise security and what you can do about it.
If you invest a lot of effort in security but overlook something important—like failing to patch your browser or using weak passwords—you’re just as vulnerable as if you hadn’t done anything at all. This is the crux of security issues.
The Advantage of Attackers
Take the example of the IRA’s attempt on British Prime Minister Margaret Thatcher’s life; after they failed, they famously said, “Today we were unlucky, but remember, we only need to be lucky once. You will have to be lucky always.” This highlights that attackers have the upper hand. They only need to strike successfully once, and they usually target the weak spots first.

Prioritize Weak Links
So, make sure to tackle your weakest links before stressing over the finer details. Your security system needs to be set up properly before you even think about fine-tuning it. Many people and companies make the mistake of not taking a risk-based approach. I’ve seen organizations pour time and money into encrypting laptops while neglecting their biggest vulnerabilities, like threats from browsers and email, which can easily bypass disk encryption.
Conclusion
Encryption protects data by turning it into unreadable gibberish. Symmetric encryption uses one key, while asymmetric uses two keys. Hash functions verify data integrity, and digital signatures authenticate senders. SSL/TLS secure web communications, but can be vulnerable to attacks like SSL stripping. Certificates confirm identities but issues with certificate authorities can weaken trust. End-to-end encryption ensures data privacy across networks. Steganography hides data within files, but isn’t foolproof. Security is only as strong as its weakest link, so focus on addressing vulnerabilities first.


