Table of Contents
The main purpose of this article is to delve into the technical details of the security field, enabling you to understand how to effectively implement virtual and physical isolation and compartmentalization techniques. These techniques are crucial in mitigating the impact of attacks by confining them within isolated environments.
Understanding Isolation and Compartmentalization
What is Isolation?
Isolation refers to the practice of separating different aspects of a system to ensure that if one part is compromised, the others remain secure. This can be achieved both physically and virtually, depending on the specific needs and resources available.
- Physical Isolation: This involves using separate hardware to run different systems or tasks. For instance, having one computer for sensitive tasks and another for general use.
- Virtual Isolation: This involves running multiple virtual machines or containers on the same hardware, each with its own isolated environment.
What is Compartmentalization?
Compartmentalization is the process of dividing a system into distinct sections, or compartments, each with its own security controls and policies. The idea is that if one compartment is breached, the others remain unaffected.
- Application-Level Compartmentalization: Restricting access and permissions of applications to minimize potential damage.
- Network-Level Compartmentalization: Segregating network traffic to prevent unauthorized access between different network segments.
Applying Isolation and Compartmentalization
Across Common Platforms
- Windows: Use features like User Account Control (UAC) and Windows Sandbox to execute applications in isolated environments.
- macOS: Leverage System Integrity Protection (SIP) and create separate user accounts for different tasks.
- Linux: Utilize namespaces and cgroups for process isolation, and tools like AppArmor or SELinux for enforcing security policies.
In Security-Focused Operating Systems
- Qubes OS: An operating system designed around the concept of security through isolation. It uses Xen-based virtualization to compartmentalize different tasks into isolated qubes.
- Tails: A live operating system that runs from a USB stick or DVD, focusing on privacy and anonymity by isolating internet activity.
Benefits of Isolation and Compartmentalization
- Reduced Attack Surface: Limits the number of potential entry points for attackers.
- Containment of Breaches: Prevents an attacker from moving laterally within a network or system.
- Enhanced Security Controls: Allows for specific security measures to be applied to different compartments based on their risk profile.
Implementing isolation and compartmentalization effectively can significantly enhance the security posture of a system. By understanding and applying these techniques, you can mitigate the impact of potential attacks and protect your systems more robustly. As you continue through this course, you’ll explore practical examples and tools to implement these strategies across various platforms.
Introduction to Isolation and Compartmentalization
Isolation and compartmentalization are among the most effective security controls at your disposal. When used correctly, these techniques can mitigate the majority of security threats. They are essential for creating security domains, which provide different levels of usability and security, while also supporting various identities or aliases for privacy and anonymity.
The Power of Isolation and Compartmentalization
When an attacker exploits a vulnerability, isolation and compartmentalization help limit the impact to just the isolated security domain. Let’s consider a simple but effective example: using a virtual machine (VM) for web browsing. If the web browser within the VM is compromised, the isolation and compartmentalization ensure that the host system remains protected. This reduces or even completely negates the potential impact of the compromise.
- Control the Attack: By using isolation and compartmentalization, you can effectively manage and contain attacks.
Implementing Security Domains
In this section, we’ll explore various best practices for implementing security domains through isolation and compartmentalization. Multiple methods can be combined, such as using a virtual machine alongside a sandbox with encrypted partitions. You need to assess your personal risk, potential consequences, and define your threat model to determine the appropriate security domains.
- Assess Your Needs: Consider what security domains you require based on your specific situation. This involves isolating and compartmentalizing your important assets and applications that interact with untrusted sources, like the internet. Your web browser and email client are typical examples.
Designing Your Own Methods
While we won’t cover every method of isolation and compartmentalization due to the vast number of possibilities, I’ll guide you through some of the best practices and general methods. This will help you design your own isolation and compartmentalization strategies as needed.
Physical and Hardware Isolation – How to Change the MAC Address
In the previous article, we discussed security domains, focusing primarily on physical security and the use of independent devices such as secure laptops, USB drives, and SD cards. Now, I would like to delve deeper into the topics of privacy and anonymity, with a particular emphasis on physical security domains.
Understanding Hardware Serial Numbers
Devices have hardware serial numbers that uniquely identify them. These unique identifiers can potentially trace back to you through purchase records or other means, especially if the hardware wasn’t acquired anonymously. If you prioritize non-attribution and anonymity, you need to isolate your unique hardware identifiers to prevent adversaries from enumerating them.
The MAC Address
The first unique hardware ID to be aware of is the MAC address (Media Access Control address). This address can be accessed via your network card, which is always a unique number. An adversary could retrieve your MAC address, and this method has been exploited in the past, such as by the NSA to deanonymize TOR users through a Firefox exploit on the TOR browser.
- MAC Address: Similar to an IP address but used only for your local network. If an adversary has access to your machine, they can view this unique MAC address, which could potentially be traced back to you through the device’s purchase.
Checking Your MAC Address
For Windows:
To check your MAC address in Windows, you can open the Command Prompt and type:
ipconfig /all
You’ll see the MAC addresses listed under your network adapters.
Example output:
Ethernet adapter VMware Network Adapter VMnet8:
Physical Address: 00-50-56-C8-24-08
For Mac and Linux:
You can use the following command in the terminal:
ifconfig
On Linux, you may need to use sudo to run it:
sudo ifconfig
Example output:
eth0: <BROADCAST,MULTICAST,UP,LOWER_UP>
link/ether 08:00:27:3e:2b:59
Alternatively, you can use the ip command on Linux:
ip addr show eth0
Changing Your MAC Address
If privacy and anonymity are your goals, you should change your MAC address. This can be done because it could be exposed via malware and is visible on local networks, both Ethernet and Wi-Fi.
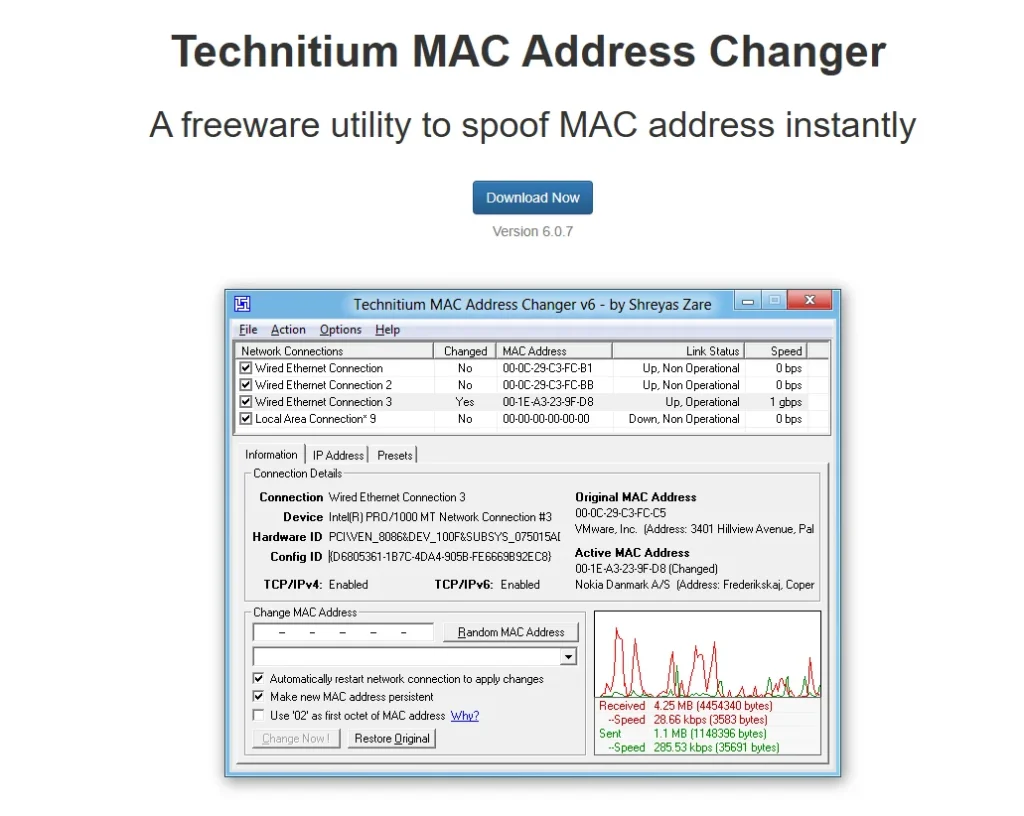
Tools for Changing MAC Address
- For Windows: You can use a tool like Technitium MAC Address Changer, which is free and works well.
- For Linux: There’s a tool called MAC Changer, which can be installed in distributions like Kali. It allows you to change your MAC address randomly or manually.
Steps to change your MAC address in Linux:
- Install MAC Changer:
sudo apt-get install -y macchanger - Bring down the network interface:
sudo ifconfig eth0 down - Change the MAC address:
sudo macchanger -r eth0 - Bring the network interface back up:
sudo ifconfig eth0 up
Changing MAC Address on Mac OS X
On Mac, you can change your MAC address using the Terminal. The command format is:
sudo ifconfig en0 ether <new_mac_address>
Alternatively, for a graphical interface, you can use tools like MacDaddy X or WiFiSpoof.
Virtual Machines and MAC Addresses
Virtual machines hide your real MAC address and allow you to set a virtual MAC address. It’s important to remember to frequently change the virtual MAC address to avoid static ties to your virtual machine.
Best Practices for MAC Address Mitigation
To minimize risks associated with MAC address tracking:
- Use anonymously purchased hardware, such as laptops, network cards, and Wi-Fi dongles.
- Combine anonymous hardware with a MAC changer tool.
- Consider using multiple cheap USB network adapters to regularly change your MAC address.
Example: Tails OS uses MAC changers by default, ensuring that your real MAC address is not exposed. Always verify the MAC address when using Tails by running the command ifconfig to ensure it has changed.
Physical and Hardware Isolation – Hardware Serials
When it comes to anonymity and non-attribution, there are several unique hardware IDs beyond just the MAC address that you should be aware of and mitigate risks associated with. Let’s start with CPUs.

CPU Serial Numbers
Most modern CPUs do not have a software-readable serial number. Intel attempted to introduce serial numbers with the Pentium 3 in the 1990s, but due to public backlash, they discontinued this feature. Therefore, with most CPUs, you can identify the model but not a unique serial number.
- Tools for CPU Information:
- Windows: You can use CPU-Z to examine your CPU details. Download CPU-Z.
- Linux: Use I-Nex, a similar tool for viewing CPU information. Download I-Nex.
- Mac: For Mac CPUs, you can find information through various similar tools.
Motherboard Serial Numbers
Motherboards may contain unique identifiers in the System Management BIOS (SMBIOS). Major OEMs typically include these serial numbers, which can potentially allow an adversary to tie the motherboard back to the purchaser.
- View Motherboard Information:
- Windows: Use the Windows Management Instrumentation (WMI) tool. You can run the following commands in the command prompt:
wmic bios get name,serialnumber,version wmic scproduct get name,identifyingnumber,uuid - Linux/Mac: Use DmiDecode to view hardware information. Install it via:
- Linux:
sudo apt-get install -y dmidecode - Mac: Install via Homebrew:
brew install dmidecode
- Linux:
- Windows: Use the Windows Management Instrumentation (WMI) tool. You can run the following commands in the command prompt:
Hard Drive Serial Numbers
Hard drives also have unique serial numbers that can be accessed:
- Windows: Use the following command:
wmic diskdrive get serialnumber - Linux: You can use LSHW or dmidecode to find hard drive serial numbers.
- Mac: Check the hard drive information through GUI or via terminal commands.
Operating Systems and Hardware IDs
Any operating system licensed to a machine must uniquely identify that machine to control and track product key use. This means if you’re using Windows or Mac OS X, Microsoft and Apple are aware of your unique hardware IDs, typically tied to the motherboard. If your hardware ID is compromised, the seller could link the device back to you, which poses risks for anonymity.
Mitigating Hardware Serial Number Issues
To mitigate the risks associated with hardware serial numbers:
- Change Unique Identifiers: Use proprietary tools to alter some hardware serial numbers, similar to changing a MAC address. Tools like VolumeID and Chameleon can help with this.
- Anonymous Purchases: Buy devices anonymously to prevent a money trail that could be linked back to you.
- Virtual Machines: Use virtual machines for isolation. They have their own unique physical machine IDs, reducing the connection to your real hardware’s unique IDs.
Other Isolation and Compartmentalization Methods
Consider additional methods for physical isolation and compartmentalization:
- Separate Devices: Use a dedicated phone or burner phone for sensitive communications.
- Physical Storage: Store files, emails, and data separately on external drives or in the cloud, away from potential adversaries.
- Security Tokens: Utilize hardware security modules and store encryption keys separately, such as using Nitrokey or YubiKey.
- Network Isolation: Separate trusted and untrusted devices using LANs, VLANs, and routers/firewalls.
- Physical Locations: Operate from different physical locations, like an internet café, to enhance anonymity.
Isolation and compartmentalization can create layers of defenses in your security posture. Ensure your physical devices are properly isolated through unique IDs to maintain anonymity and prevent attribution.
Virtual Isolation
We’ve already discussed physical isolation, now let’s delve into virtual isolation and compartmentalization methods. These techniques are crucial for maintaining security, privacy, and anonymity in the digital world.
Encryption and Compartmentalization
One of the key methods for virtual isolation is through encryption and compartmentalization. Here’s how you can use these methods:
- Data Separation: You can separate data by its level of importance using different encrypted volumes. For example, have one encrypted volume for confidential data, another for secret data, and another for top-secret data, each with a unique encryption key.
- Secure Storage Devices: Use a NAS (Network-Attached Storage) device with separate volumes, each encrypted with a unique key. Secure volumes can remain unmounted and decrypted to reduce the risk of exposure to ransomware or other attacks. The encryption keys won’t reside in memory unless the volumes are mounted.
- Hidden Encrypted Volumes: These make data harder to find. With transport security, using separate session keys for encrypted messages is a form of compartmentalization.
Portable Applications

Portable apps are standalone applications that do not require installation. They offer several security and privacy benefits:
- Self-contained Apps: All data related to the app, like browser history, is contained within the portable app’s folder. This makes it easier to conceal or destroy evidence.
- Encrypted and Movable: These apps can be stored on encrypted USB drives, making them easy to move and secure. They can be placed on encrypted or hidden encrypted volumes for extra security.
- Multiple Instances: You can create multiple instances of a portable app, each with its own settings and security extensions. This allows for separate profiles, security domains, and aliases.
- No Admin Rights Required: Portable apps can run on any system without needing admin rights, providing plausible deniability.
Free Portable Apps and Games for USB
Remote Access and Cloud Browsers
- Remote Services: Use remote desktop services (e.g., Citrix, TeamViewer, SSH) to control a remote machine. This setup isolates you from potential threats because malware cannot propagate through screen updates.
- Cloud Browsers: These services allow you to browse via remote servers, preventing malware from reaching your machine. Examples include Authentic8, Maxthon’s cloud browser, and Spikes’ AirGap. While effective against hackers, they may pose privacy concerns as the service provider can track your activity.
Combining Virtual and Physical Isolation
Some solutions provide both virtual and physical isolation. For instance, using a webmail service to store data with a third-party provider helps keep data out of the adversary’s reach. Similarly, by setting up your remote access software on a virtual server, you can achieve virtual isolation when performing activities like web browsing.
Dual Boot
Most physical machines come pre-installed with a single operating system, like Windows 10 or macOS. However, it’s entirely possible to have multiple operating systems installed on the same physical machine, even if it has just one hard drive. This setup allows you to create different security domains, where one operating system could be used for general purposes, while another is specifically locked down for enhanced security and privacy.
How Dual Boot Works
When you power on your machine, you’ll be presented with a boot menu that allows you to select which operating system you wish to start. Here’s an example of what this boot screen might look like, particularly in Windows environments.
Benefits and Limitations
Benefits:
- Separation of Environments: Dual booting allows you to maintain a separation between different operating systems, providing a balance between privacy and security.
- Different Use Cases: For instance, you could use Windows as your standard OS for everyday activities while utilizing a Linux-based operating system like Debian for tasks requiring heightened privacy and security.
Limitations:
- Lack of Flexibility: Unlike virtual machines, dual booting does not allow you to access multiple operating systems simultaneously.
- File System Vulnerabilities: There is no true isolation within the file system when dual booting. Depending on how you store files, there is a risk that one operating system could compromise files on another. They might have different file system types, complicating access to files across operating systems.
- File Sharing Challenges: If you need to share files between the two systems, you’ll require a solution. This could be a shared file system they can both access or using remote storage/external disk options.
Setting Up Dual Boot
Setting up a dual boot system depends on the specific operating systems you choose to install. Here are a few things to consider:
- BIOS Access: Different machines provide access to BIOS in various ways, which is necessary for configuring your dual boot setup.
- Research Specific Guides: Websites like How-To Geek offer excellent resources on dual booting options. A quick Google search using the terms “dual boot” along with the names of your desired operating systems will yield a wealth of information on how to configure your setup.
Dual booting could be a viable solution if you’re interested in maintaining separate environments on a single machine.
Built-in Sandboxes and Application Isolation
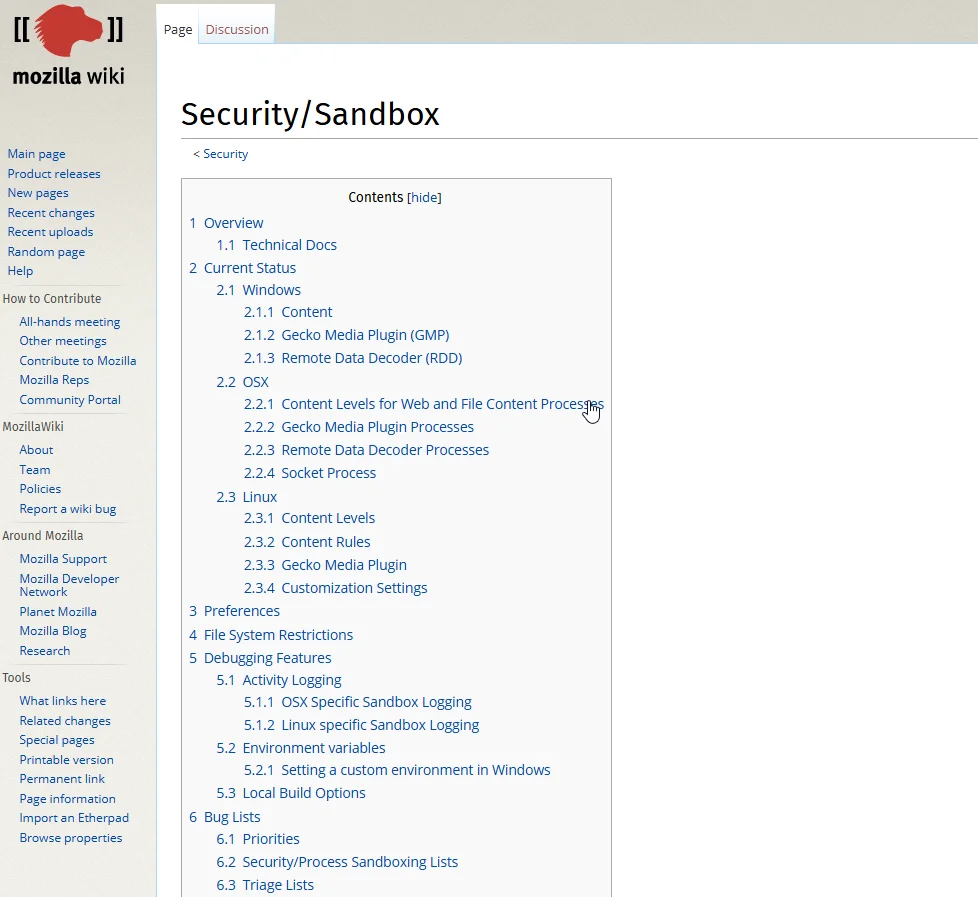
A sandbox is a powerful security control used to isolate and contain applications or code in a virtual environment, preventing potential threats from affecting the entire system. It is an excellent tool for threat prevention, detection, and mitigation.
What is a Sandbox?
A sandbox creates an isolated environment where applications or code can run without affecting other parts of the system. Think of it as a virtual container that confines its contents, preventing any interference with external systems.
Key Uses for Sandboxes
Sandboxes are particularly useful for high-risk applications, especially those that interact with untrusted sources such as the internet. Common applications that use sandboxes include:
- Web Browsers: Chrome (based on Chromium) uses sandboxes extensively, and Firefox also implements sandboxing. They sandbox browser plugins and extensions like Flash, Silverlight, and Java.
- PDF Viewers: Adobe Reader runs PDF files in a sandbox to prevent malicious code from escaping and affecting the computer.
- Office Applications: Microsoft has a sandbox mode to prevent unsafe macros from causing harm to your system.
Limitations and Additional Measures
While built-in sandboxes are a great starting point, they can still be bypassed. Vulnerabilities in applications can allow threats to escape the sandbox and reach the operating system. Here are some considerations:
- Not All Sandboxes Are Equal: Some are more robust than others. Unfortunately, sandbox breakouts can occur, allowing attackers to bypass the protection.
- Defense in Depth: You can enhance security by adding additional application sandboxes on top of the built-in ones. This layering makes it harder for attackers to succeed as their exploits may not anticipate the additional sandbox.
- Custom Sandboxes: Attackers design exploits to target well-known sandboxes like those in Java or browsers. By using custom or additional sandboxes, you increase the likelihood that attackers’ exploits will fail.
In summary, sandboxes are based on the principle of containing threats within a virtual environment. By implementing both built-in and additional sandboxes, you can strengthen your security posture and reduce the risk of successful attacks.
Windows Sandboxes and Application Isolation
Let’s explore some sandbox applications that can enhance the security of your Windows applications, particularly those interacting with untrusted sources such as the internet. At the very least, consider sandboxing your browser and email client.
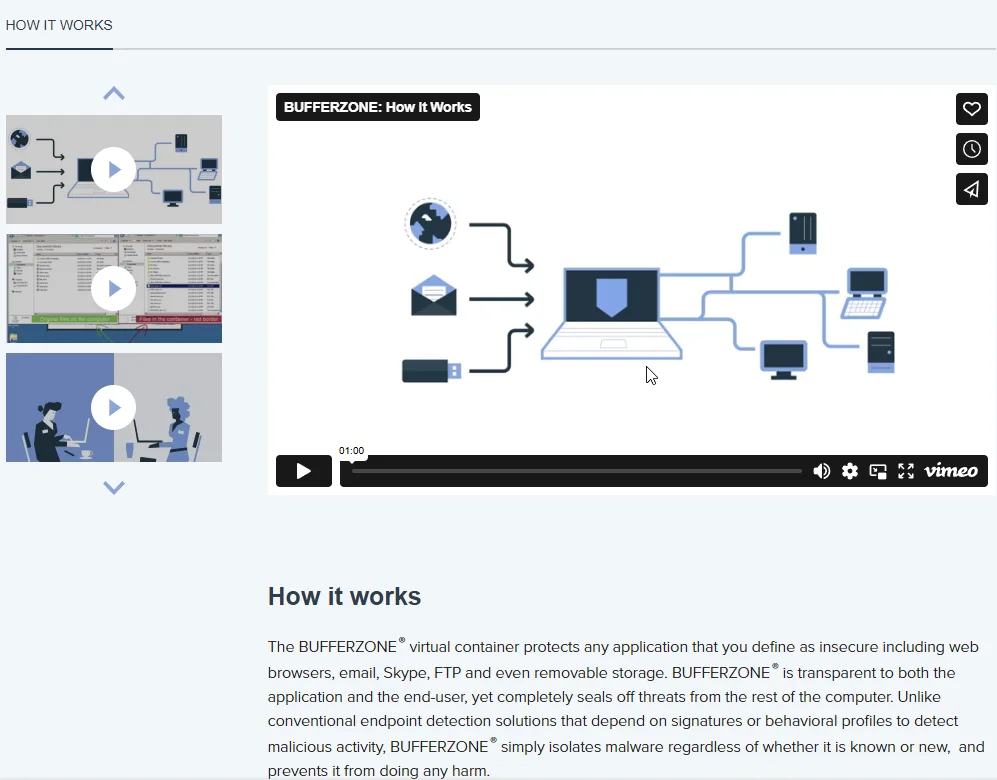
Bufferzone
- Overview: Bufferzone is a commercial sandbox that uses virtual container technology to block ransomware and other exploits. It prevents them from accessing your files and keeps them from infecting other users in your organization.
- Functionality: When an infected file is opened, it runs in an invisible virtual container. This segregates it from the file system, registry, and memory. Any ransomware encrypts only a copy of the files, keeping the originals safe. Bufferzone also isolates the network to prevent spreading to other computers.
- Conclusion: This product targets the business market and is Windows-only. It’s a promising option but not extensively tested by me.
Shadow Defender
- Overview: Shadow Defender runs your system in a virtual environment called “shadow mode.” It redirects changes to a virtual environment without affecting the real one.
- Functionality: Each system change occurs in a virtual environment, and changes are not saved to the real environment until rebooted.
- Conclusion: Windows-only and not personally tested.
Deep Freeze
- Overview: Deep Freeze is a kernel-level driver that protects hard drive integrity by redirecting writes, maintaining original data intact.
- Functionality: Upon reboot, the system restores to its original state at the disk sector level.
- Conclusion: Available for Windows, Mac, and Linux. Offers protection only upon reboot.
Comodo Firewall
- Overview: Comodo Firewall includes a built-in sandbox and virtual desktop.
- Concerns: Recent security product issues reduce trustworthiness.
Avast Antivirus
- Overview: Avast antivirus offers sandboxing functionality.
- Concerns: Avast has been criticized for selling user data.
Bitdefender Safepay
- Overview: Bitdefender Safepay is a limited-functionality browser providing sandboxing.
Note: While these sandboxing tools offer security enhancements, each has its strengths and weaknesses. It is important to evaluate them based on your specific requirements and verify their effectiveness through testing.
Windows – Sandboxes and Application Isolation: Sandboxie
Introduction to Sandboxie
Sandboxie, or SandboxIE, is a popular sandbox application recommended for Windows users. It’s shareware, meaning there is both a free version and a paid version with additional features. After 30 days of using the free version, you’ll receive reminders to upgrade, but it remains functional. Here are some features and tips for using Sandboxie:
Key Features and Usage
- Automatic Program Execution: The paid version has the functionality to automatically run programs under Sandboxie, even if they are not started directly through it. This feature is useful for ensuring all programs operate within the sandbox for added security.
- Multiple Sandboxes: Only the paid version allows running programs in more than one sandbox at the same time. This feature can be handy for separating different tasks or applications.
- Installation and Configuration: Sandboxie is easy to install and use initially. For optimal use, spend time configuring it to suit your needs. You can download and install it like any other Windows program, or use Choco for installation.
- Running Programs in Sandboxes: You can launch programs like your web browser or email client through the sandbox by right-clicking and selecting “Run Sandboxed.” Each sandbox can have different settings, and you can choose whether to run an application within a sandbox or outside of it.
- Identifying Sandboxed Applications: Applications running in a sandbox will have a yellow border, and the sandbox icon will display red dots to show it is in use.
Configuration and Tips
- Display Settings: Enable border display around sandboxed windows to avoid confusion.
- Immediate Recovery: Decide whether to keep downloaded files in the sandbox or recover them to the real system immediately. This helps manage files securely.
- Automatic Deletion: It’s advisable to automatically delete sandbox contents upon closing to maintain a clean environment.
- Forced Programs: In the registered version, you can force specific programs, like browsers and email clients, to always run sandboxed.
- Storage Space: Increase allocated space for sandbox storage to handle larger downloads comfortably.
- Access Restrictions: Limit internet access, start/stop permissions, and administrator rights for sandboxed programs. Set access levels for files, registry, and other resources.
- Specific Application Settings: Configure settings for individual applications, like allowing Firefox to access phishing databases or managing cookie access.
Additional Resources
- Documentation: A recommended document provides guidance on using Sandboxie with browsers and email clients.
- Forums: The Sandboxie forums are a valuable resource for information and community support.
By using Sandboxie, you can add an extra layer of protection to your Windows environment, particularly for applications that interact with potentially risky sources.
Linux – Sandboxes and Application Isolation
Sandboxes for Linux
AppArmor
One of the primary sandbox tools available for Linux is AppArmor. It is a mandatory access control framework that controls programs according to a set of rules. These rules define what files a program can access. AppArmor is available on several Linux distributions, including Debian and Arch Linux. I highly recommend learning and using AppArmor as it enhances the security of your Linux environment. Learn more about AppArmor here.
Sandfox
Another sandboxing tool for Linux is Sandfox. It runs Firefox and other applications in a sandbox, limiting their file system access. Sandfox supports distributions like Debian, Arch, and Ubuntu. You can find Sandfox here.
Firejail
Firejail is another tool for sandboxing in Linux. It acts as a SUID program that reduces the risk of security breaches by restricting the running environment of untrusted programs using Linux namespaces and seccomp-bpf. Firejail is considered a lightweight sandbox, easier to use compared to AppArmor. For detailed usage and documentation, visit Firejail’s website.
To install Firejail on Debian, you can use the following commands:
wget <http://sourceforge.net/projects/firejail/files/firejail/firejail_0.9.38_1_amd64.deb>
sudo dpkg -i firejail_0.9.38_1_amd64.debAfter installation, you can launch applications, like IceWeasel (Firefox for Debian), in a sandbox using:
firejail firefox
firejail --private firefox
firejail --listTrustedBSD for BSD
For BSD systems, the TrustedBSD system is used for sandboxing, another mandatory access control framework. If you’re a fan of BSD, it’s worth exploring. More information is available at TrustedBSD’s website.
Mac – Sandboxes and Application Isolation
Introduction to Mac Sandboxing
Mac OS X includes a built-in sandboxing facility, originally code-named “Seatbelt,” which was introduced with OS X 10.5 Leopard. This sandboxing system is implemented via the TrustedBSD mandatory access control framework, which is possible because OS X is a BSD derivative. To use sandboxing on Mac, you must create configuration files for each application you want to isolate. This process requires technical knowledge and cannot be achieved through a simple point-and-click interface.
Using the Sandbox
The main command for sandboxing applications on Mac is sandbox-exec. This command allows you to execute applications within a sandbox using a specified profile. The profiles are configuration files that define what resources and permissions the application is allowed or denied.
Creating a Sandbox Profile
To create a sandbox profile, you need root privileges. Below is an example of a configuration file for sandboxing Firefox:
(deny default)
(allow file-write* file-read-data file-read-metadata
(regex #"^/Users/[^.]+/Downloads"
#"^/Users/[^.]+/Library/Application Support/Mozilla"
#"^/Applications/Firefox.app"))
(allow network*)
(import "/System/Library/Sandbox/Profiles/bsd.sb")This profile restricts Firefox’s file system and network access according to the specified rules.
Running an Application in a Sandbox
To run Firefox with the created sandbox profile, use the following command:
sandbox-exec -f /usr/share/sandbox/firefox.sb /Applications/Firefox.app/Contents/MacOS/firefoxThis command specifies that Firefox should be executed within the sandbox environment defined by the profile at /usr/share/sandbox/firefox.sb.
Resources and Tools
- Sandbox Guide: A comprehensive guide on using the Mac sandbox.
- Example Profiles: GitHub repository with example profiles.
- Buckle Up: A tool to assist in creating sandbox profiles, available here.
- Quick Start Guide: Quick start guide for setting up sandboxing on Mac.
- Security Report: A report by a security researcher on the Apple sandbox.
Additional Sandboxing Tools for Mac
Apart from the built-in sandbox, there are limited third-party sandboxing solutions available for Mac. One such tool is SuperDuper, which offers some sandboxing functionalities, although they are limited.
Sandboxing on Mac OS X is a powerful method for isolating applications and enhancing security. However, it requires technical expertise to set up and maintain. By using tools and guides available, you can effectively sandbox applications like browsers and email clients to protect against potential security threats.
Virtual Machines

Introduction to Virtual Machines
Virtual Machines (VMs) are powerful tools for creating separate security domains and enforcing isolation and compartmentalization. They act like sandboxes, providing a controlled environment that can help reduce risks, limit impacts, and control potential attackers. VMs are particularly useful for operational security (Op Sec) purposes, allowing you to create isolated environments for different aliases or identities.
Advantages of Virtualization
- Interface Reduction: Virtualization reduces the interfaces between security domains, allowing them to exist and communicate securely.
- Testing and Development: VMs are ideal for testing new software or configurations without affecting the main system.
- Security: By isolating applications, VMs can minimize the risk of cross-contamination from malware or attacks.
Types of Hypervisors
Type 2 (Hosted) Hypervisors
These hypervisors run on top of an existing operating system. Examples include:
- VirtualBox: Free, open-source, and offers features like snapshots for returning to a known good state.
- VMware Player/Workstation/Fusion: Commercial options with robust features. Fusion is specifically for Mac.
- Parallels Desktop: A popular choice for Mac users.
- Vagrant, VPC, Citrix Desktop Player: Other options worth exploring.
Type 1 (Native/Bare Metal) Hypervisors
These run directly on hardware without a host OS, offering better performance and security:
- VMware ESX/ESXi: Commercial products for enterprise environments.
- Oracle VM Server: Another enterprise-level option.
- Microsoft Hyper-V: Integrated in Windows Server, it’s a robust choice for Windows environments.
- XenServer: Free and open-source, popular for local network setups.
Linux Virtualization
- KVM (Kernel Virtual Machine): An open-source hypervisor that comes with Linux. It works well with Virtual Machine Manager for GUI management.
- **OpenVZ and Linux Containers**: Container-based virtualization solutions for Linux.
- Whonix: A security-focused Linux OS that pairs well with KVM.
BSD and Solaris Virtualization
- FreeBSD Jails: Lightweight virtual environments for isolation and security in FreeBSD.
- Solaris Zones: Similar to FreeBSD Jails, providing isolated environments within Solaris.
Containerization with Docker
Docker is a popular containerization platform that offers lightweight and efficient virtualization by sharing the host OS. It’s widely used for server-side applications and provides an efficient alternative to traditional VMs.
Virtual Appliances
Virtual appliances are pre-configured VMs that can be deployed quickly. TurnKey Linux offers a range of appliances that integrate with Amazon Web Services for rapid deployment.
Windows 10 Virtualization
Windows 10 incorporates virtualization-based security features like Device Guard, which uses hypervisor technology to isolate critical system components, providing enhanced protection against malware and attacks.
Virtual machines and containerization provide robust methods for isolation and security. They are increasingly becoming integral to operating systems’ core security functionalities, as seen with Windows 10. By leveraging virtualization, you can create secure, isolated environments that enhance overall system security.
Virtual Machine Weaknesses

Introduction to VM Weaknesses
While virtual machines (VMs) provide significant isolation and security benefits, they also have potential vulnerabilities that can compromise their effectiveness. It’s essential to understand these weaknesses to mitigate risks effectively.
Potential Weaknesses in Virtual Machines
- Host and Guest Isolation Breaches:
- If the host system is compromised, it could lead to the compromise of guest VMs. For example, a remote access tool on the host could capture screenshots or keystrokes from the guest. Conversely, vulnerabilities in the guest can affect the host.
- Hypervisor Vulnerabilities:
- The hypervisor, which manages VMs, can have security flaws that allow attackers to perform VM escapes. One such vulnerability was VENOM (CVE-2015-3456), affecting multiple platforms and enabling arbitrary code execution on the host.
- Shared Resources and Information Leakage:
- VMs share physical resources like CPUs and memory with the host, leading to potential information leakage. For instance, data from the VM could be swapped onto the host’s disk.
- Advanced malware can detect when running in a VM and may attempt to exploit VM software vulnerabilities or shut down to avoid analysis.
- Network-Based Attacks:
- If the host and guest share the same network, a compromised VM can perform attacks on the network, such as SSL stripping, affecting other devices.
- Covert Timing and Side-Channel Attacks:
- These attacks exploit shared CPU resources to transmit information or extract sensitive data across VMs and hosts.
- Feature-Based Vulnerabilities:
- Features like shared folders, clipboard access, and drag-and-drop can reduce isolation and become potential attack vectors.
- Underlying Hardware Vulnerabilities:
- Bugs in technologies supporting virtualization, such as Intel’s VT-d, can bypass VM protections.
Resource Limitations and Economic Barriers
Running multiple VMs requires a robust computing setup, which can be costly. This presents a challenge for individuals in resource-limited settings who need security, privacy, and anonymity but lack the financial means to acquire powerful hardware.
Virtual machines are a vital part of a layered security strategy but should not be solely relied upon. They must be used in conjunction with other security measures, such as hardening practices, to ensure comprehensive protection.
Virtual Machine Hardening
Ensuring Security for Your Virtual Machine
When using a virtual machine (VM), it’s essential to ensure it’s secure or “hardened.” This involves both physical and virtual measures to protect both the host and guest systems.
Physical Isolation for Security
- Dedicated Secure Device:
- Use a separate, secure device as the host for your VM to ensure physical isolation. This reduces the risk of the day-to-day device being compromised and affecting the VM.
- Network Isolation:
- Use a USB network dongle instead of the host network adapter.
- Place the VM on a separate network from the host or use a VLAN for virtual isolation.
Mitigating Virtual Machine Leaks
- Unwanted Data on Host:
- VMs can leave traces, like log files and cache, on the host OS. One way to mitigate this is through whole disk encryption on the host, which protects against data leaks when the system is off.
- Disable Caching:
- Disable or delete caching features like swapping or paging, though this carries risks of causing issues with the host OS.
Protecting Data Within the Virtual Machine
- Encryption:
- Enable encryption for each VM using the hypervisor. However, this protection is only effective when the VM is off.
- Consider using well-known encryption technologies like LUKS, FileVault 2, BitLocker, and VeraCrypt for additional security.
- Reducing Attack Surface:
- Disable unnecessary features like audio, microphone, shared folders, drag-and-drop, clipboard, video acceleration, and serial ports.
- Avoid installing tools like VirtualBox Guest Additions or VMware Tools unless necessary.
Use of Non-Persistent Systems
- Non-Persistent Operating Systems:
- Use live CDs or USBs that don’t retain data between sessions to maintain anonymity and security.
- VM Snapshots:
- Use snapshots to create a clean VM state and revert to it after use, removing any unwanted changes or potential malware.
Security Issues with Power Saving Features
- Handling Encryption Safely:
- Avoid pausing, suspending, or hibernating systems with encrypted VMs, as encryption keys can be stored insecurely.
- Always log out, shut down, and power off systems to ensure decryption keys aren’t stored on disk.
By implementing these hardening strategies, you can significantly improve the security of your virtual machines and protect sensitive data from potential threats.
Whonix OS – Anonymous Operating System
Introduction to Whonix
Whonix is a free, open-source operating system designed with a focus on anonymity, privacy, and security. It utilizes the TOR network to protect user identity online and is based on Debian GNU/Linux, a highly recommended operating system.
Security through Isolation
Whonix achieves security by implementing isolation principles. It consists of two parts:
- Whonix Gateway: Runs TOR and acts as a gateway.
- Whonix Workstation: Operates on an isolated network, only accessible through TOR.
This separation helps mask your IP address, prevent ISP spying, and avoid identification by websites or malware.
Using Whonix
- Whonix can be run on VirtualBox, KVM, and Qubes. For optimal security, using Whonix with Qubes is recommended, followed by KVM and then VirtualBox.
- The Gateway and Workstation are available in OVA format for easy setup with VirtualBox.
- The setup involves two network adapters: one for internet access and another for an internal network, ensuring the workstation only communicates with the Gateway.
Features and Configuration
- The Whonix Gateway enforces TOR connections, ensuring DNS leaks are impossible.
- The network configuration is pre-set in the OVA file, requiring no additional changes.
- The use of VMs provides additional protection for hardware IDs and MAC addresses.
Network and TOR Configuration
- Whonix uses the ARM tool to monitor TOR network status and resource usage.
- Time synchronization is crucial for TOR operation, managed by SDWdate in Whonix to avoid deanonymization risks.
- Whonix Check ensures the system is updated with the latest security patches and TOR configurations.
Extending Whonix
- Whonix can be used with custom workstations by connecting them to the Whonix network and configuring appropriate IP settings.
- Whonix supports transparent TOR proxying and socks proxying for enhanced security and stream isolation, providing different TOR circuits for applications.
Recommendations and Best Practices
- Keep a master copy of the Whonix Workstation updated and create regular snapshots for clean states.
- Avoid using the master copy for activities requiring anonymity.
- Perform necessary updates and configurations before browsing or connecting to the internet.
By following these practices, you can leverage Whonix’s robust security features to maintain anonymity and privacy online.
Whonix OS – Weaknesses
Considerations and Limitations of Whonix
While Whonix provides robust anonymity and privacy features, it’s important to understand its limitations and what it isn’t designed to do:
- Visibility of TOR Usage:
- When using Whonix, it’s apparent to observers that you are using TOR. It may also be identifiable that you’re using Whonix due to possible fingerprinting.
- Lack of Document and Email Encryption:
- Whonix does not encrypt documents by default, nor does it clear metadata from documents or encrypt email subjects and headers.
- Contextual Identity Separation:
- Whonix is not designed to separate different contextual identities. It’s not advisable to use the same Whonix workstation for tasks requiring separate identities.
- Protection Against Firmware and Hardware Attacks:
- Whonix does not protect against firmware rootkits, BIOS attacks, or hardware compromises like those listed in the NSA ANT Catalog.
- Potential Vulnerabilities:
- As with any software, security vulnerabilities or backdoors could exist, though Whonix primarily consists of scripts rather than compiled code.
- Complex Setup and Maintenance:
- Setting up Whonix is more complex compared to the TOR browser or Tails, requiring virtual machines and a hypervisor, and involves higher maintenance than static live CDs.
Non-Amnesic Nature
- Whonix is not an Amnesic Live CD like Tails. It leaves traces on the hard drive, and any files created will persist unless securely deleted.
- It doesn’t prevent host memory swaps to disk. If amnesic capabilities are needed, consider using VM snapshots or full-disk encryption as workarounds.
Threat Model Focus
- Whonix is not designed to protect against local forensic examination. Its primary focus is to mitigate protocol-level leaks and ISP snooping.
- It’s not a one-click solution for security, privacy, and anonymity. It requires technical knowledge and customization for personal needs.
Recommendations
- Whonix is recommended for technical users or those willing to invest time in understanding and configuring it.
- The documentation is thorough and offers extensive insights into security, privacy, and anonymity.
In summary, Whonix is a powerful tool for anonymity and privacy but is best suited for users who understand its limitations and are comfortable with its complexity.
Qubes OS
Overview of Qubes OS
Qubes OS is designed to provide strong security through isolation and compartmentalization. It’s a free and open-source operating system that primarily focuses on desktop computing, rather than server environments. Built on the Xen hypervisor, X-Windows system, and Linux, Qubes uses virtualization to create secure domains, allowing different security levels for various applications and tasks.
Key Features of Qubes OS
- Virtualization for Security:
- Qubes OS operates using a Xen bare metal hypervisor, which creates a separation between different virtual machines (VMs). This reduces the interfaces between security domains while still allowing them to communicate.
- Multiple Operating System Templates:
- User environments are based on various operating systems, including Fedora, Debian, Arch Linux, Whonix, and Windows. These are known as Qubes templates.
- Isolation of Applications:
- Each application runs in its own virtual machine, providing compartmentalization. For instance, you can run an untrusted browser alongside a secure banking application without risk of cross-contamination.
- Network Security:
- Qubes includes a dedicated network virtual machine (NetVM) that protects against exploits at the network layer, isolating potential vulnerabilities from impacting other domains.
- Disposable VMs:
- Disposable VMs can be used for single-use tasks, like browsing or opening suspicious attachments, which are discarded after use to prevent data retention.
- USB VM:
- To mitigate risks from potentially harmful USB devices, Qubes features an optional USB VM that safely handles USB connections.
- Integration with TOR:
- Qubes OS comes with support for Whonix, which allows users to leverage TOR for enhanced privacy and anonymity while maintaining the security features of Qubes.
Security Architecture
- Microkernel Design:
- Unlike traditional operating systems that use a monolithic kernel, Qubes employs a microkernel architecture. This minimizes the trusted computing base (TCB) and reduces the attack surface, making it more challenging for attackers to compromise the system.
- Dom0:
- The administrative domain (Dom0) handles the user interface and manages communication between VMs. It has no network connectivity, adding an extra layer of security by minimizing potential attack vectors.
Challenges and Considerations
- Hardware Compatibility:
- One of the major drawbacks is the lack of widespread hardware support. To run Qubes effectively, your hardware must support virtualization technologies (Intel VT-x or AMD-V and Intel VT-d or IOMMU).
- Installation Complexity:
- Installing Qubes can be complicated, requiring users to manage BIOS settings and CPU capabilities, which can deter less technical users.
- Performance Limitations:
- Qubes may not perform well with resource-intensive applications like games. It serves as a security platform rather than a performance-centric operating system.
- Learning Curve:
- Users need to be somewhat technically proficient to effectively utilize Qubes, as it does not provide the simplicity of single-layer operating systems.
Qubes OS is a powerful security tool that excels in providing a high level of isolation, making it suitable for users who prioritize security, privacy, and anonymity. It is still in its early stages of development, and while it offers unrivaled features, potential users should ensure they have compatible hardware and are willing to invest time in learning how to effectively use the system.
Security Domains, Isolation and Compartmentalization
Understanding Security Domains
Implementing security domains effectively requires conscious consideration of how to partition your digital environment. Security domains may be as straightforward as distinguishing between work and personal domains, or trusted and untrusted domains. The structure of these domains will depend on your specific risks, consequences, adversaries, and overall threat model.
Use Case Examples
- General Use with Security Concerns:
- A user who prefers a straightforward operating system for general tasks (like document creation) might choose macOS with relaxed security settings. However, to safeguard against malware and hackers during internet use, they could create a high-security domain using a lockdown Debian virtual machine, with VirtualBox serving as the interface between these domains.
- Privacy and Local Forensics:
- Someone concerned about privacy might maintain a separate, secure laptop stored in a physically secure location. They would run Debian as the host OS and utilize Tails within a VirtualBox setup to enhance security against local forensics.
- Gaming and Security:
- A gamer worried about tracking and hacking could operate a Windows host for offline activities while employing a live operating system like Knoppix for online activities, balancing performance and security.
- Simplified Isolation:
- For users seeking minimal isolation, they might simply sandbox their browser within Windows, which provides a basic level of protection without complex setups.
- High-level Threats:
- Those facing nation-state-level adversaries might use a secure laptop configured with Qubes and Whonix tailored to their specific privacy needs.
- Traveling with Sensitive Data:
- For travel, where confidentiality is crucial (like carrying sensitive documents from major companies), it is advisable to use a separate physical laptop devoid of sensitive data. Any necessary sensitive information can be stored encrypted in the cloud with two-factor authentication, ensuring that there is nothing on the laptop that could be compromised if seized.
Security Controls within Each Domain
Within each security domain, you would implement the various security controls discussed throughout the course.
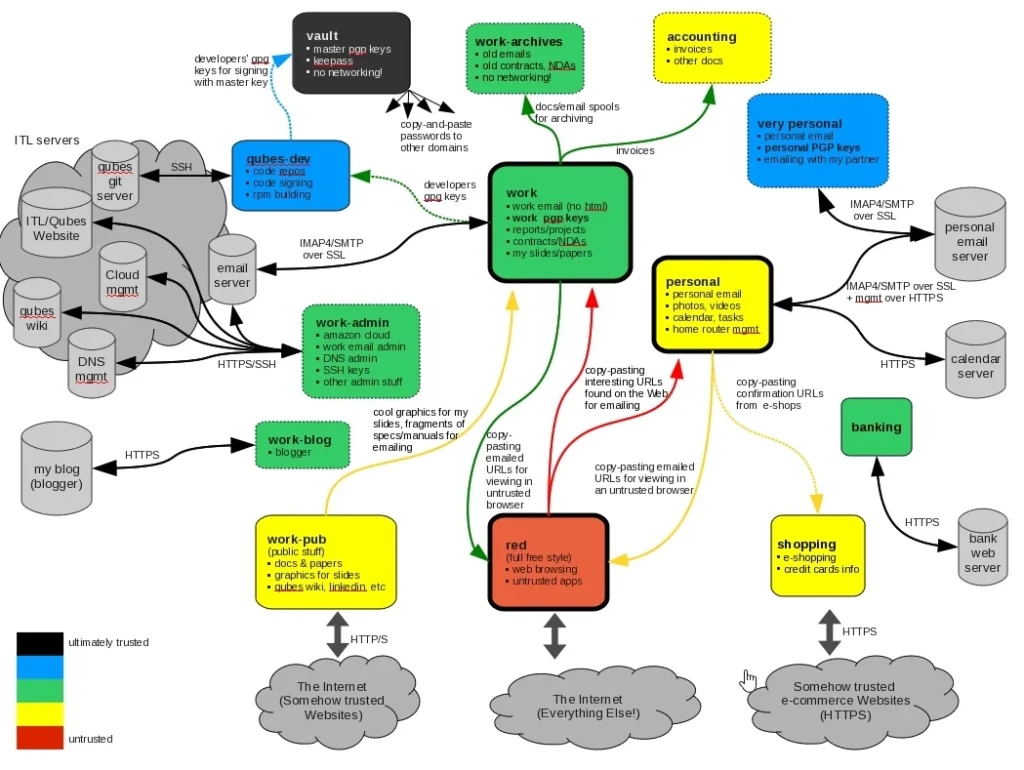
Diagram and Trust Levels
Referencing a diagram by Joanna Rutkowska, the Qubes OS Project Lead, we see a more intricate setup utilizing Qubes. Each color in the diagram represents a different trust level, with black being the most trustworthy and red the least trustworthy.
- Vault Domain: The most secure area, containing master PGP keys and passwords, with no network connections.
- Development and Work Domains: These hold code and administrative activities with progressively lower trust levels.
- Least Trustworthy Domains: Activities like web browsing and using untrusted applications are isolated in their own domains.
This structured approach to security domains within Qubes allows for advanced isolation and compartmentalization based on the user’s specific needs and threat landscape.
Conclusion
This article primarily discusses how to use isolation and segmentation techniques to protect computer security. In simple terms, it involves separating different components of a computer so that if one area is compromised by a hacker, the others remain secure. This can be achieved through various means, whether in hardware or software.
For instance, different computers or virtual machines can be used to handle distinct tasks, or different security zones can be established on the same computer. The article also highlights specific tools and operating systems, such as Qubes OS and Whonix, which leverage virtualization technology to enhance security. Overall, these techniques make it more difficult for hackers to breach the system.


