Table of Contents
The objective for this post is for you to understand the high risks that security vulnerabilities and bugs can pose. These vulnerabilities and bugs can lead to serious security issues if not addressed properly.
The Importance of Patching
Updating or Patching:
- It’s crucial to update all software applications, firmware, operating systems, basically everything.
- An update or patch is essentially a fix to a bug. When it’s about a security bug, it’s called a security update.
- Security updates are the most important because they fix vulnerabilities that could be exploited by attackers.
Key Points:
- Updating your software is the most important action you can take to stay safe online.
- If you do just one thing after this course, make sure it’s applying patches promptly.
- Although updating software might seem simple, I’ll go through it step-by-step because it’s vital to keep your patching up to date.
Security Bugs and Vulnerabilities:
- Unfortunately, each piece of software may have different methods and interfaces for updating, which can be a hassle. But we will explore ways to make it easier.
- Products that need the most updating include:
- Direct Interface with the Internet: Browsers (e.g., Opera, Edge, Firefox, Chrome), browser extensions & plugins (e.g., Java, Flash, Silverlight), email applications (e.g., Outlook, Thunderbird).
- Applications for Handling Downloaded Files: Examples include Windows Media Player, Adobe Reader, Image viewers, Excel, Word.
- Operating Systems: Such as OS X, Windows 7, 8.x, 10, Android.
- Direct Internet Interface: Browsers and their extensions/plugins are the biggest attack vector because they interact directly with the internet.
- Applications for Downloaded Files: These can process files from untrusted sources and become attack vectors, like macro viruses in Excel and Word.
- Operating Systems: They are crucial for maintaining core security, so keeping them updated is important.
Potential Downsides:
- Occasionally, patches might introduce new bugs, causing functional issues, although this is rare with major companies like Microsoft.
- Automatic updates are the most secure option, but you can set them to download only and evaluate them before applying.
Real-World Example:
- A friend had not updated his laptop since 2011 and experienced strange behavior. The lack of updates meant the system likely had vulnerabilities and issues. The recommendation was to reinstall the operating system and start fresh.
Conclusion:
- Don’t neglect updates; they are critical for maintaining security and preventing attacks.
Windows 10 & 11 – Auto Update
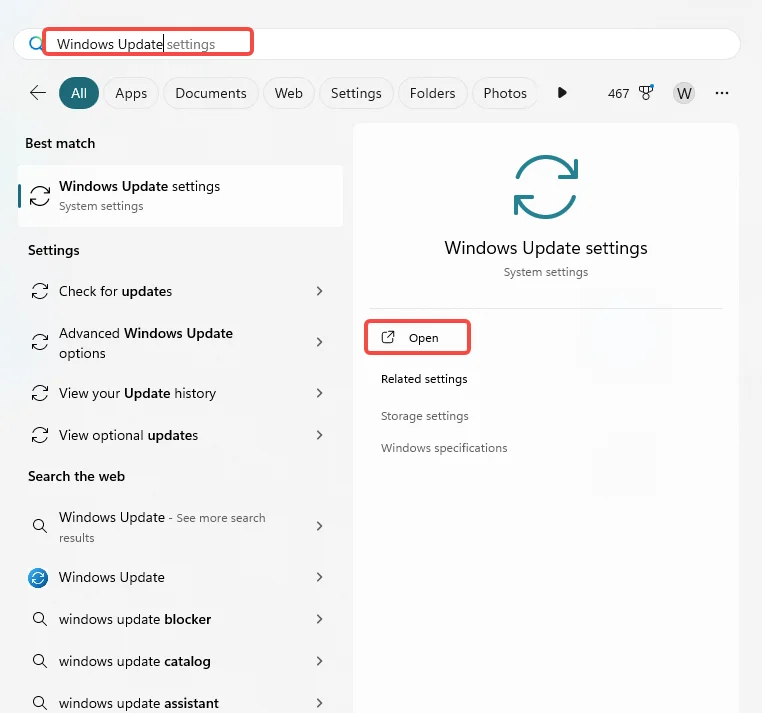
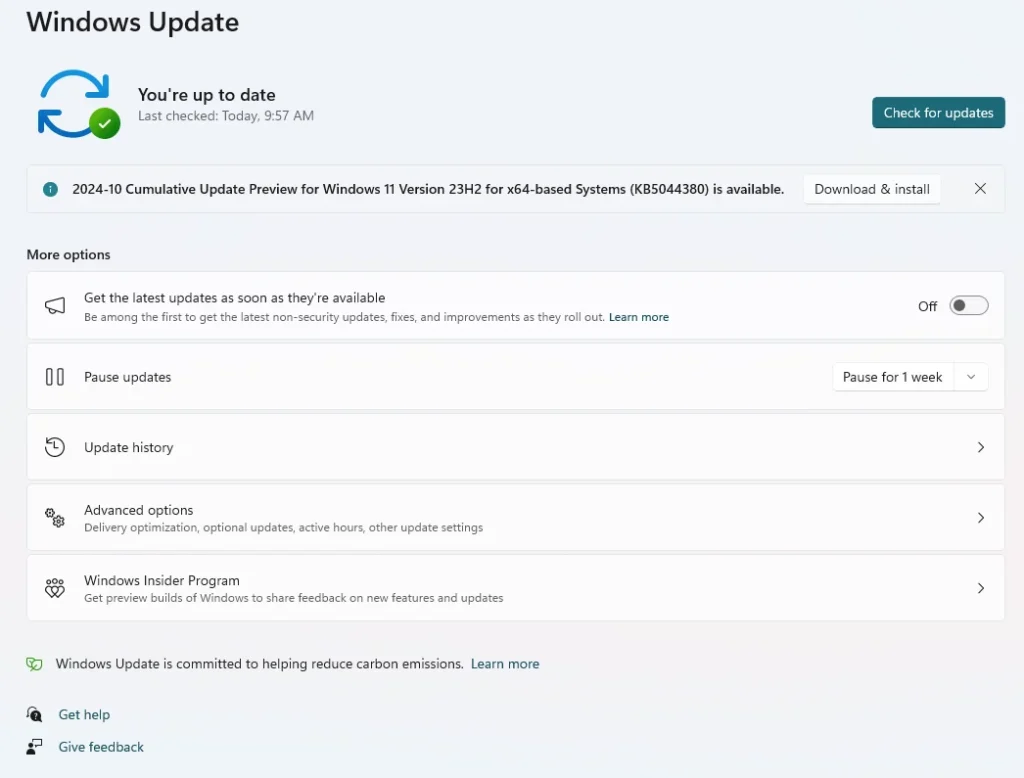
Setting Up Auto Updates on Windows 10&11:
- Access Windows Update:
- Go to the Start menu and type “Windows Update”.
- Select “Windows Update” from the search results.
- Change Settings:
- Click on “Change settings”.
- Make sure all the options are checked, especially “Give me updates for Microsoft products…”. This option is crucial for updating Edge and other Office applications, as it’s not always enabled by default.
- Set Updates to Automatic:
- Ideally, you should set your updates to be automatic. This ensures your system stays secure without needing manual intervention.
- If you prefer to review updates before installing them, you can set it to “download only” and check them manually. However, the recommendation is to keep it automatic for ease and security.
- Checking for Updates:
- To manually check for updates, click “Check for updates”.
- The system will inform you if there are new updates available.
- Viewing Update Details:
- You can view more details about the updates by clicking on the available options.
- For example, if there’s one important update, you can click to get more information about what it includes.
This setup ensures that your system gets the necessary updates, keeping your Windows secure and running smoothly.
Windows-Criticality and Patch Tuesday
Patch Tuesday:
- Patch Tuesday is an unofficial term for the day Microsoft releases security patches for its software products.
- It typically occurs on the second, and sometimes the fourth, Tuesday of each month in North America.
Finding Security Patches:
- You can visit Microsoft’s security bulletin to see the latest security patches.
- One patch can address multiple vulnerabilities.
Installing Patches:
- It’s crucial to install all critical patches and advisable to install important ones as well.
- The KB number of a patch will match the details shown in the Windows operating system, making it easier to identify which patches are needed.
- CVE (Common Vulnerabilities and Exposures) numbers are unique identifiers for vulnerabilities.
Example of a Patch:
- For example, patch KB3089656 addresses vulnerability CVE-2015-2507.
- You can click on the CVE number to get more information about the vulnerability.
Researching Vulnerabilities:
- You can search for more information about a vulnerability using resources like CVE Details.
- CVSS (Common Vulnerability Scoring System) scores help indicate the severity of a vulnerability. A score of 9.3 indicates a critical vulnerability that allows remote attackers to execute arbitrary code, making it imperative to patch.
Resources for Vulnerability Details:
- CVE (Common Vulnerabilities and Exposures): cve.mitre.org
- National Vulnerability Database: nvd.nist.gov
- CVE Details: cvedetails.com
These resources provide comprehensive information about vulnerabilities across various software and operating systems.
Automating Software Updates on Windows 7, 8, 8.1,10 & 11
The Importance of Automation:
- Keeping up with the latest security patches for all your software can be a hassle. Automating this process ensures updates are not forgotten, making your system more secure against attacks.
Recommended Tool – FLEXERA PSI (formerly Secunia PSI):
- FLEXERA Personal Software Inspector (PSI) is a free tool to automate software updates. It’s maintained by a security-focused company, ensuring a strong emphasis on updating security-critical software.
- Note: It doesn’t cover all software, but it does cover the essential ones for security.
Installation and Setup:
- Download and Install:
- Visit the FLEXERA PSI website.
- Fill in your details, download the executable, and run it.
- During installation, select your language, accept the license, and choose your settings.
- Configuration:
- Initially, set it to “Download updates automatically”, then “Let me choose whether to update”.
- This allows you to decide which software to update, in case there are reasons not to update certain programs immediately.
- After setup, switch to “Update programs automatically” for convenience.
- Using FLEXERA PSI:
- The program will scan your software to check what’s installed, which can take time. Ensure you have an internet connection for this process.
- If the program seems unresponsive, it’s likely scanning your files in the background.
- Settings and Views:
- Use the Detailed view to see which apps need updates and manage settings.
- You can ignore updates for specific software if needed (e.g., to avoid compatibility issues with your developed code).
- Additional Features:
- Check the “More information” option for details about patches and vulnerabilities.
- Keep track of installed/updated programs via the History tab.
- Request Secunia to add monitoring for any missing programs.
Alternative Tools for Automating Updates:
- Appupdater
- FileHippo App Manager
- Ninite
- Software Informer Client
- Software Update Monitor (SUMo lite): Avoid the non-lite version due to adware.
- Heimdal Free: Security-focused.
- Dumo: For automated driver updates.
Best Practices:
- If your machine has been offline, update your patches before using internet or browsing.
- Ensure your system is up-to-date first for maximum security.
Debian Linux – Security Patching
Choosing Debian for Security:
- Debian is highly recommended as a general-purpose operating system for those who prioritize security, privacy, and anonymity.
- It’s foundational for many security-focused distributions like Kali, Tails, and Whonix.
Security Updates:
- Debian is committed to providing timely security updates. You can find details on the Debian Security page.
- Debian coordinates with other software vendors to release updates on the same day a vulnerability becomes public.
Package Management Tools:
- DPKG (Debian Package Manager):
- Basic tool for installing, removing, and providing information about
.debpackages. - Command example:
dpkg -i filename.deb
- Basic tool for installing, removing, and providing information about
- APT (Advanced Package Tool):
- A command-line front-end for DPKG, used to install packages with administrative privileges.
- Command example:
sudo apt-get install nmap
- Aptitude:
- A front-end for APT, used similarly to
apt-getfor managing packages. - Command example:
sudo aptitude install zenmap
- A front-end for APT, used similarly to
Updating Debian:
- APT Commands for Updates:
sudo apt-get update: Synchronizes the package index files.sudo apt-get upgrade: Installs the latest versions of all installed packages without removing any.sudo apt-get dist-upgrade: Similar toupgradebut intelligently handles changing dependencies and may remove packages if necessary.
Repository Configuration:
- The
/etc/apt/sources.listfile maintains a list of sources for package retrieval.
Automatic Updates:
- Debian can be configured for automatic security updates using several methods:
- GNOME Update Manager: A graphical interface for managing updates.
- Unattended Upgrades Package: Automates the installation of security updates.
- Cron Scripts: Schedule regular updates with custom scripts.
- Cron-apt: Automates the update process using
cron.
Setting Up Automatic Updates:
- Install Unattended Upgrades:
sudo apt-get install unattended-upgrades
- Edit Configuration Files:
- File:
/etc/apt/apt.conf.d/10periodic - File:
/etc/apt/apt.conf.d/50unattended-upgrades- Customize the Origins-Pattern section to automatically update security patches.
- File:
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Download-Upgradeable-Packages "1";
APT::Periodic::AutocleanInterval "7";
APT::Periodic::Unattended-Upgrade "1";Once configured, Debian will handle security updates automatically, enhancing system security with minimal user intervention.
Mac Security Patching
Overview of Apple Security Updates:
- Apple regularly releases security patches for its operating systems. You can view details of these security issues on the Apple security updates page.
- It’s generally recommended to install all security updates unless there’s a specific reason not to.
Automatic Updates in OS X:
- Setting Up Automatic Updates:
- Go to
System Preferences. - Click on
App Store. - Ensure
Automatic Updatesis checked:- Download newly available updates in the background: Notifies you when they’re ready to install.
- Install app updates: Automatically installs app updates.
- Install OS X updates: Automatically installs OS X updates.
- Install system data files and security updates: Ensure this is selected for security updates.
- Go to
- Checking for Updates:
- You can manually check for updates by clicking
Check Now.
- You can manually check for updates by clicking
Updating Non-App Store Apps:
- Apple and the App Store do not update apps not downloaded from the App Store. You need to update these manually or use a tool like MacUpdate.
MacUpdate Tool:
- Website: macupdate.com/desktop
- Functionality: Acts like an additional App Store for non-App Store apps, detecting outdated software, allowing you to download and install the latest versions.
- Limitations: It may have bugs and show the same app twice but is generally effective.
Using Brew for Package Management:
- Brew: A package manager for macOS, useful for installing extra tools and keeping packages updated.
- Installation:
- Run the following in Terminal:
/usr/bin/ruby -e "$(curl -fsSL <https://raw.githubusercontent.com/Homebrew/install/master/install>)" - Requires admin privileges.
- Run the following in Terminal:
Useful Brew Commands:
brew helporman brew: Help guides for using Brew.brew search nmap: Searches for the packagenmap.brew install nmap: Installsnmap.brew update: Checks if Brew is up-to-date.brew outdated: Lists outdated packages.brew upgrade: Upgrades all or specified outdated packages.
Using these tools and methods ensures your Mac remains secure with the latest updates and packages.
Firefox Browser and Extension Updates
Keeping Firefox Up-to-date:
- To check for the latest updates in Firefox, click on the question mark (
?) icon and selectAbout Firefox.- This checks if Firefox is up-to-date; if not, it starts downloading the latest version.
- Automatic Updates:
- Go to
Options>Advanced>Updatetab. - Set Firefox to automatically install updates.
- Check the box for “Warn me if this will disable any of my add-ons” to avoid unexpected add-on issues after updates.
- Go to
- Update History:
- You can view past updates and their details by clicking “Show update history”.
Updating Extensions and Plugins:
- Ensure extensions are up-to-date for security and functionality.
- Go to
Add-ons, thenPluginsorExtensions. - Use the dropdown box to select
Update add-ons automatically.
- Go to
- Check for Updates:
- Click “Check to see if your plugins are up to date” to manually verify for updates.
- Regularly check this area to ensure everything is current.
Security Features:
- Built-in updates for malware and phishing protection are already enabled for security purposes.
Advanced Information and Troubleshooting:
- about:support:
- Type
about:supportinto the address bar for detailed configuration information. - Click the
Pluginslink to see detailed information on installed plugins.
- Type
- Safe Mode:
- If Firefox is experiencing issues, start it in Safe Mode by selecting “Restart with Add-ons Disabled”.
- Configuration Settings:
- Access
about:configfor advanced configuration settings. - Be cautious when changing settings, as improper changes can negatively affect browser performance.
- Access
Using these methods ensures your Firefox browser and its extensions remain secure and up-to-date, while also allowing you to monitor and troubleshoot issues effectively.
Chrome Browser and Extension Updates
Overview of Chrome Updates:
- Chrome automatically updates the browser and its extensions. There is no action required on the user end to keep Chrome up-to-date, as it handles updates by default. You would need to manually disable updates if you don’t want them to occur, though this is not recommended.
Browser Auto-Updates:
- The Chrome browser itself updates automatically without requiring any user intervention.
Extension Updates:
- Chrome extensions also auto-update, provided they have an auto-update URL specified in their manifest file.
- Extensions from the Chrome Web Store and Extensions Gallery typically have this setting enabled by default.
Forcing an Update Check:
- If you want to manually check for updates, you can do so by navigating to
Help>About Google Chrome.- This triggers Chrome to check for the latest updates. If an update is available, Chrome will download and install it.
Using these methods ensures that your Chrome browser and extensions remain current and secure.
IE and Edge Browser Updates
Automatic Updates Based on Windows Settings:
- For both Internet Explorer (IE) and Microsoft Edge, the update settings are tied to your Windows operating system settings.
Ensuring Automatic Updates:
- To ensure that IE and Edge are updated automatically, you need to configure your Windows Update settings:
- Navigate to
Windows Update. - Select
Change settings. - Make sure the option “Give me updates for Microsoft products and check for new optional Microsoft software when I update Windows” is checked.
- Navigate to
With this setting enabled, both IE and Edge will receive updates automatically through Windows Update.
Browser Recommendations:
- It’s important to note that while you can keep IE and Edge updated this way, Internet Explorer is generally not recommended for use due to outdated technology and potential security vulnerabilities.
By keeping your Windows Update settings configured correctly, you can ensure that your browsers are as secure as possible through regular updates.
Auto-updates: The Impact on Privacy and Anonymity
Balancing Security and Privacy:
- While installing security updates and automating these updates is crucial for maintaining security, it may not align well with privacy and anonymity goals.
- This concern is particularly relevant for systems by Microsoft, Apple, and similar companies where there is a “money trail” linking back to the operating system purchaser.
Operating System Considerations:
- Windows 10 is not designed for high levels of privacy and anonymity. Windows 8 and Windows 7 offer slightly better privacy.
- To enhance privacy and anonymity when updating, consider using services like VPNs, Tor, or JonDonym.
- These services help mask your physical location and IP address during updates.
Potential Risks with Updates:
- It’s important to recognize that updates themselves can be a vector for attacks.
- For instance, iOS updates are device-specific. If Apple were compelled or chose to do so, they could theoretically send a malicious update to a specific device.
Open Source and Money Trail:
- Using free or open-source operating systems can enhance privacy and anonymity as there is no financial link back to the user, thus less knowledge of who the user is.
While security updates are essential, it’s important to be mindful of the potential privacy and anonymity implications when installing them.
Conclusion
The post emphasizes the critical importance of addressing security vulnerabilities and bugs through timely updates and patches. Regularly updating all software, operating systems, and applications is essential to protect against potential exploits by attackers. Key points include the necessity of automatic updates, particularly for software that directly interfaces with the internet, and the risks associated with not applying patches, such as exposure to malware and security breaches.
Real-world examples highlight the consequences of neglecting updates, while tools like FLEXERA PSI and Debian’s automated upgrade options are recommended for managing software updates efficiently. Furthermore, the discussion touches on privacy and anonymity concerns in relation to updates, particularly for proprietary operating systems. While maintaining security through updates is critical, users are cautioned about the potential risks involved and are encouraged to consider privacy-enhancing measures when applying updates. Overall, proactive patch management is vital for maintaining a secure and functional system.


