Table of Contents
This article mainly introduces fundamental concepts of networking and its security, aiming to help you identify potential vulnerabilities in routers and other network devices from both internal and external attackers. Additionally, you will learn about the use of custom router firmware to enhance the available network security services.
Understanding Your Network Setup
Overview of a Typical Network
Most people’s networks are structured similarly. At the center is the router—which could be a Linksys, Netgear, or other brands. This router connects directly to the internet through a cable.
- Connected Devices:
- You likely have wireless or Wi-Fi devices such as laptops, phones, and tablets connected to the router.
- There may also be wired connections through Ethernet, including devices like printers or desktop computers, and possibly Internet of Things (IoT) devices, such as smart TVs.
The router functions as the central component of both your network and its security, serving as the default gateway for all internet traffic.
Finding Your Router’s IP Address
To find your router’s IP address, look for the default gateway on your devices. Here’s how to do it on different operating systems:
- Windows:
- Open the command prompt and type
route print. Look for the IPv4 route table to find the gateway IP. - Alternatively, you can use
ipconfigand check the right adapter for the default gateway.
- Open the command prompt and type
- Linux:
- Use the command
sudo route -nto find the IP address of your router.
- Use the command
- macOS:
- You can use the terminal command
netstat -nr | grep defaultto see your default gateway.
- You can use the terminal command
If you are still unable to find your router’s IP address, you can check a list of common default router IP addresses online.
Understanding Ports
When accessing a device via an IP address, you also need to specify a port. Ports act as doorways into the device and each doorway corresponds to a different service. Here are some commonly used ports:
- Port 22: SSH (Secure Shell) for remote command line access.
- Port 23: Telnet for unencrypted command line access.
- Port 25: SMTP (Simple Mail Transfer Protocol) for sending emails.
- Port 80: HTTP for web traffic.
- Port 443: HTTPS, which is HTTP over SSL/TLS for secure web traffic.
Most routers can be configured through a web interface accessible via these ports.
Router Configuration
You will typically set up your router using its web interface, which requires an admin or root username and password. This information may often be found on the back of the router or on websites like routerpasswords.com.
The Role of Routers in Network Security
The router plays a crucial role in protecting your internal devices from the internet. It has both an external IP address and an internal IP address, the latter being the default gateway for your devices.
To find out your external IP address, you can use a service like WhatIsMyIP.com. This will show you the IP address that represents you to the internet, assigned by your Internet Service Provider (ISP).
Due to a feature called NAT (Network Address Translation), your internal devices are not directly accessible from the internet. NAT requires specific configuration to forward traffic to a specific device on a specific port, often referred to as port forwarding.
Port Forwarding Example
Here’s a simple configuration example of port forwarding:
- If you want external devices to connect to an internal device (like a Slingbox), the router will redirect traffic from the external IP on port 5001 to the internal device (192.168.1.55 on port 5001).
Without such port forwarding rules, your internal devices remain isolated from direct internet access.
Maintaining Connection State
When you connect to the internet, the router keeps track of your outbound connections, allowing incoming responses back to your device. This is known as maintaining state and is configured by default in routers.
Router Components
Modern home routers typically combine several devices into one, including:
- Switch: Connects devices on the local network. It creates a MAC table to send traffic to the right destination using MAC addresses.
- Firewall: Controls traffic based on a set of rules, often using software like IP tables.
- Modem: Modulates and demodulates signals to connect to your internet service provider.
- Wireless Access Point: Allows wireless devices to connect to the network.
Networking encompasses a variety of components and functions. If you find any of these concepts challenging, additional study may be necessary since this course is not solely focused on networking. Understanding these basics is essential as we progress through the material.
Security, Privacy, and Anonymity of Routers
Importance of Routers
Since routers act as the main gateway into your network, both locally and via the internet, they are essential for maintaining security, privacy, and anonymity. However, routers have a history of vulnerabilities and poor default configurations, often being left running without updates, which can leave them susceptible to attacks.
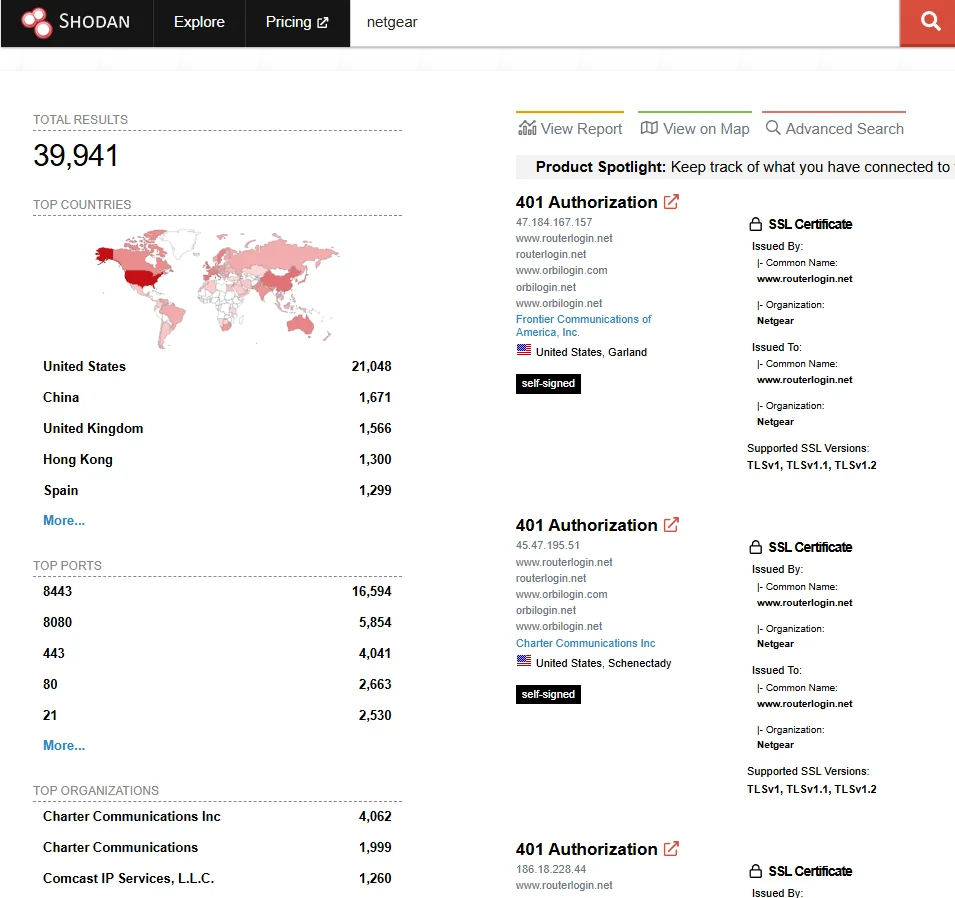
Discovering Vulnerable Routers with Shodan
One tool that highlights this issue is Shodan, a search engine for internet-connected devices. Shodan allows users to find vulnerable devices by searching for specific strings associated with devices, like router brands or default passwords. For example, searching for “Netgear” might show devices with open ports like HTTP and FTP, indicating vulnerability.
- Shodan Usage:
- Hackers and security researchers use Shodan to identify potential targets and secure their infrastructure.
- Searching for terms like “default password” can expose devices still using factory login credentials.
Access Vulnerability Risks
Any router that exposes its admin interface to the entire internet increases the risk of being compromised. Ideally, router management interfaces should only be accessible from internal networks or through secure VPN connections.
- Port Forwarding and DMZ:
- Misconfigurations like port forwarding or DMZ settings can unintentionally expose devices to the internet.
Securing Your Router
It’s crucial to secure your router to protect your network:
- Check IP Address:
- Use services like “What is my IP address?” to find your router’s external IP and test its visibility on Shodan.
- Access Router Interface:
- Access your router’s web admin interface using its internal IP, typically something like
http://192.168.1.1.
- Access your router’s web admin interface using its internal IP, typically something like
- Secure Settings:
- Ensure features like UPnP (Universal Plug and Play) are disabled unless absolutely necessary, as they can auto-configure port forwarding without your knowledge.
- Patch and Update:
- Regularly update router firmware to patch vulnerabilities and disable unnecessary services.
Checking Open Ports
To determine which ports are open on your router, you can:
- Use SSH or Telnet:
- Access your router via SSH or Telnet to view open ports using commands like
netstat -tu -l.
- Access your router via SSH or Telnet to view open ports using commands like
- Test with Online Tools:
- Use online services to scan your router for open ports, though remember that scanning devices you don’t own can be legally ambiguous.
Full Vulnerability Scan
For a more thorough security check, consider using a vulnerability scanner like Nessus FreeScan. This tool can:
- Perform comprehensive scans for exploits beyond mere open port checks.
- Provide detailed guidance on remediating specific vulnerabilities.
Qualys Community Edition | Qualys
Ensure your router is up-to-date with patches and that only necessary services are active. Any exposed services should be secure, requiring authentication and having no known vulnerabilities.
Mapping and Scanning Your Internal Network
Mapping Your Network
To understand what devices are on your internal network, including their IP addresses, ports, and services, you can use network mapping tools.
- IP Addresses:
- Devices will receive an IP address via DHCP (Dynamic Host Configuration Protocol) or be statically assigned. DHCP typically assigns IP addresses automatically via a DHCP server, often your router.
- Checking DHCP:
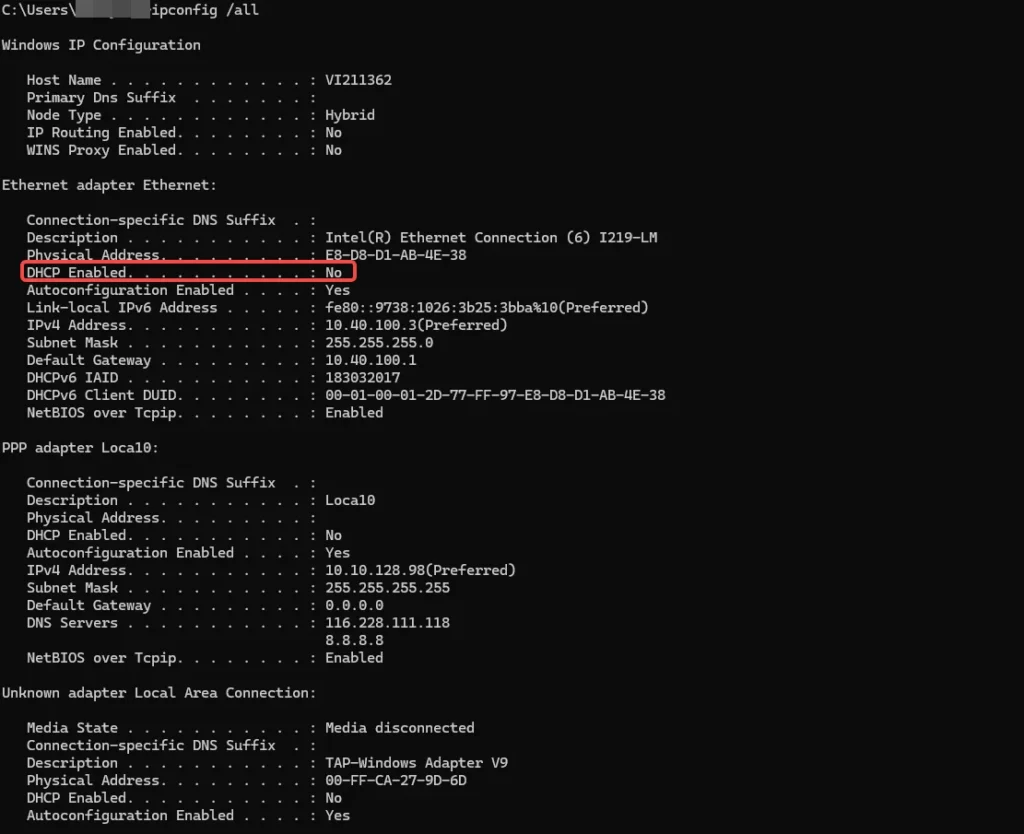
- Windows: Use
ipconfig /alland check for “DHCP Enabled”. - Linux: Check syslog for DHCP requests or use network manager tools.
- Mac: Check in System Preferences under Network settings.
- Windows: Use
Using Nmap and Zenmap
Tools like Nmap and Zenmap are excellent for mapping your local network:
- Nmap: A versatile port scanner available for Windows, Mac, and Linux.
- Zenmap: A graphical interface for Nmap, providing a visual representation of your network.
- Scanning Your Network:
- Identify your network’s IP range, for example,
192.168.1.0/24. - Run Nmap or Zenmap to see active devices and open ports.
- Identify your network’s IP range, for example,
Mobile Tools
For mobile devices, Fing is a great option for both iOS and Android to scan your network easily.
Vulnerability Scanning
Beyond mapping, it’s crucial to scan for vulnerabilities:
- MBSA (Microsoft Baseline Security Analyzer): A Windows tool for scanning and reporting security issues.
- OpenVAS: A free vulnerability scanner available on Kali Linux. It can scan your network for known vulnerabilities.
- Nessus: A leading vulnerability scanner with a free home edition for up to 16 IP addresses. It can perform authenticated and unauthenticated scans.
Considerations for Vulnerability Scanning
- Authenticated vs. Unauthenticated Scans:
- Authenticated scans provide more detailed information by logging into devices.
- Unauthenticated scans mimic external attackers and check for vulnerabilities without logging in.
- Security Precautions:
- Be cautious when granting admin access to scanners as it may potentially alter device configurations.
- Regularly update your devices to mitigate known vulnerabilities, especially IoT devices like smart TVs or routers.
Utilizing network mapping and vulnerability scanning tools helps maintain the security posture of your internal network. Keep your devices updated and regularly scan for vulnerabilities to ensure robust security.
Custom Router Firmware for Enhanced Security
Understanding Router Firmware
Router firmware is the operating system that powers your router. It’s often basic, especially on home routers, which limits advanced security configurations. Manufacturers typically design them for mass-market appeal, avoiding complexity to prevent user complaints.
Need for Custom Firmware
To gain more control and enhance security, you can install custom open-source firmware on your router. This can provide features like:
- VPNs (Virtual Private Networks)
- VLANs (Virtual Local Area Networks)
- Isolated Wi-Fi networks
- Authentication servers
- IP tables for firewall configurations
- Live traffic monitoring and logging
Risks and Considerations
Using the standard firmware can expose your router to security risks, such as backdoors. Custom firmware can mitigate these risks, but be aware:
- Installing custom firmware incorrectly can “brick” your router, rendering it unusable.
- Manufacturers are unlikely to support routers with custom firmware.
Popular Custom Firmware Options
- OpenWRT:
- A Linux-based system supporting a wide range of devices.
- Offers extensive features and package support but can be complex for beginners.
- LibreWRT/LibreCMC:
- Built on OpenWRT, adheres to free software guidelines.
- Limited device support and not beginner-friendly.
- DD-WRT:
- Also based on OpenWRT, easier to install and use.
- Supports many home routers, including the common brands.
- Offers features like real-time monitoring and VPN support.
Installing Custom Firmware
- Download the appropriate firmware for your router model from the firmware’s official site.
- Use the router’s admin console to upload and install the firmware. This process is called “flashing.”
- Ensure compatibility to avoid damaging your router.
Bought and Pre-Flashed Routers
If flashing your router seems daunting, pre-flashed routers are available, but they can be expensive. They come with custom firmware installed.
Advantages of Custom Firmware
- TOR Network: Run TOR for anonymous internet browsing.
- VPN Configuration: Set up a VPN client directly on the router for all or specific devices.
- More Control: Custom firmware provides more power and flexibility, especially for advanced users.
Other Options
- Tomato Firmware: Easier to use but not well-maintained.
- PFSense: A robust option for firewall needs, discussed further in network firewalls.
Conclusion
This article provides an overview of networking fundamentals and security, focusing on router vulnerabilities and how to protect against internal and external threats. It covers network setup, router configuration, and the importance of understanding ports and NAT. The article also discusses enhancing security with custom firmware like OpenWRT and DD-WRT, which offer advanced features and better control over network security.


