Table of Contents
Choosing the right operating system is essential for your security, privacy, and anonymity, as different systems cater to varying needs. This section aims to help you understand which operating system suits your specific requirements based on risk factors and usage. By learning to evaluate risks and make informed decisions, you can select an operating system that balances usability and risk management. Additionally, you’ll gain the skills necessary to optimize your OS for maximum privacy.
Security Features and Functionality
Let’s dive into how choosing an operating system impacts your security, as the OS is the foundation of your overall security. There are many misconceptions surrounding operating systems and their security. For instance, some people believe that Macs are immune to viruses, while others claim that Windows is notoriously insecure. Then there’s the Linux community, which often champions it as the best option.
Windows Security
- Track Record:
- Windows has faced criticism for poor security from the start.
- Improvements:
- Recently, Microsoft has made significant strides in security with features like:
- BitLocker
- EMET (Enhanced Mitigation Experience Toolkit)
- Device Guard
- Windows Hello
- Trusted Windows apps
- However, the privacy concerns, especially with Windows 10, have raised some flags for users.
- Recently, Microsoft has made significant strides in security with features like:
Mac OS X Security
- Security Features:
- Mac OS X also has a solid foundation with features like:
- Address Space Layout Randomization (ASLR)
- Application sandboxing
- FileVault 2 for disk encryption
- Strong privacy controls
- Apple’s trusted apps
- Mac OS X also has a solid foundation with features like:
Linux Security
- Overview:
- Linux and UNIX-like operating systems encompass a wide variety, but they are generally recognized for their strong security.
- Examples:
- SELinux is a notable example, providing fine-grained mandatory access control.
- Standard distributions like Debian, Arch Linux, and Ubuntu also boast robust security features.
Security Bugs and Vulnerabilities
When it comes to security, it’s not just about the features—it’s crucial to assess the actual risks based on the history of security bugs and vulnerabilities in different operating systems. So, which OS has been the most vulnerable over time?
Top 50 products having highest number of cve security vulnerabilities

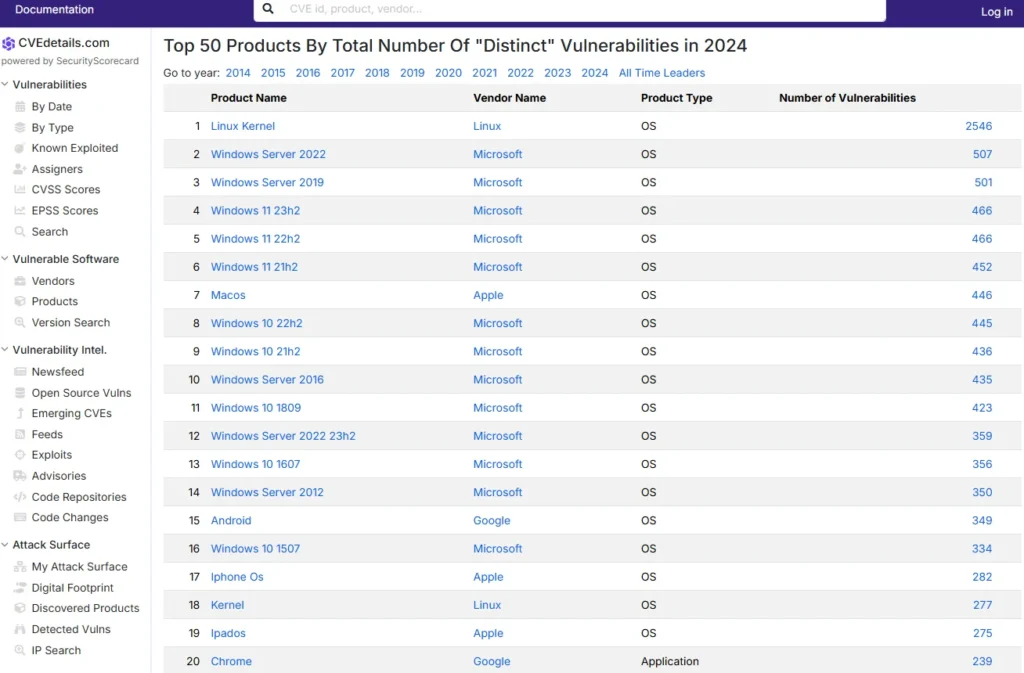
Vulnerability Overview
- Linux Kernel:
- Historically, the Linux Kernel has had the most vulnerabilities.
- Mac OS X:
- Surprisingly, this comes in second, while older Microsoft products like Windows XP rank lower.
- Recent Trends:
- In 2015, Mac OS X showed the highest number of vulnerabilities, followed by various Windows platforms and Ubuntu Linux.
Severity of Vulnerabilities
- It’s not only the quantity but also the severity of vulnerabilities that matters.
- For Mac OS X, there seems to be an upward trend in finding severe vulnerabilities, particularly those that allow for code execution.
- Windows still has significant issues, especially with Denial of Service vulnerabilities.
- The Linux Kernel shows a downward trend in severe vulnerabilities, but many distributions are grouped together, making it hard to generalize.
Fixing Vulnerabilities
- The speed at which vulnerabilities are patched is also important. While Apple and Microsoft handle fixes reasonably well, obscure Unix/Linux systems may lag behind due to a lack of resources.
Usage Share and Cybercrime Risk
- One of the biggest factors influencing the likelihood of being a victim of cybercrime is the market share of the operating system.
- Windows dominates with a massive market share, making it a primary target for cybercriminals.
- Mac users should be cautious as the growing number of vulnerabilities might attract more attacks.
- Android is also gaining popularity, leading to an increase in attacks. Users should purchase devices from reputable manufacturers that provide timely security updates.
Conclusion: Which OS to Choose?
- Linux: Offers the most secure environment but has a tiny market share, meaning a lower threat landscape. However, it may lack some application support.
- Mac OS X: A decent balance for average users, with moderate security features and usability, although vulnerabilities are on the rise.
- Windows: The highest market share and thus the most targeted, but this post will provide solutions to mitigate those risks. With simple steps, you can significantly reduce your vulnerability and avoid becoming a target.
Usage Share
So, we’ve talked about security features and bugs, but what’s the biggest factor in determining your risk of cybercrime? It’s actually the market share of the operating system you’re using.
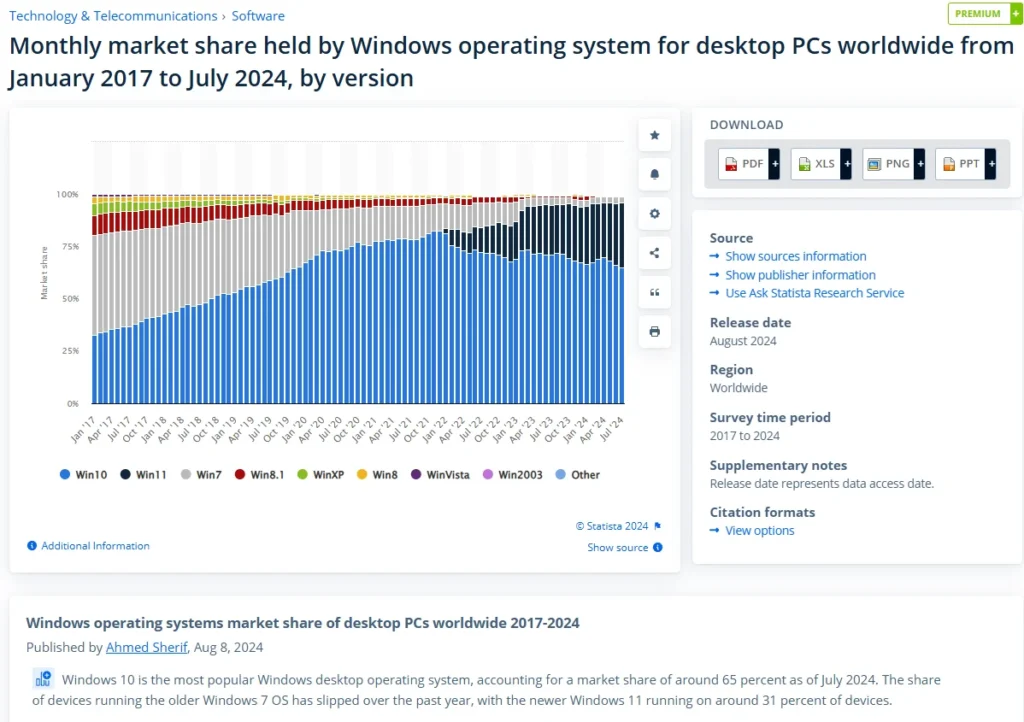
Statistics Overview
- Windows Dominance:
- Microsoft operating systems hold a huge market share, The data analysts firm NetMarketShare revealed that Windows 10 has seen another uptake in users and it went up to 64.04% from 61.26% last month. Linux (multiple distros) went from 1.14% to 1.65% and Ubuntu now holds a market share of 0.51%.
- Mac and Linux:
- Mac OS X has a tiny share at 8%, and Linux is even smaller.
Cybercriminal Targeting
- Return on Investment:
- Just like any savvy entrepreneur, cybercriminals want the biggest return on their time and effort. Hence, they focus on the largest group of users, which is Windows. Most malware is designed specifically for one type of operating system, and with Windows leading in market share, that’s where attackers set their sights.
- Mac Users Beware:
- Mac users should be cautious; as Mac becomes more popular, and vulnerabilities increase, it’s likely that criminals will shift their focus there.
Mobile OS Trends
- Android Popularity:
- Looking at mobile OS statistics, Android is becoming increasingly popular, which has led to a spike in attacks against it.
- Vulnerabilities:
- Many Android devices are at risk due to unpatched vulnerabilities like Stagefright, which allow attackers to take control through a simple picture message.
What OS Should You Choose?
- Linux:
- Linux is the most secure option available, with a tiny market share, making it less appealing to attackers. However, the downside is that it might not support all the applications you need.
- Mac OS X:
- Mac offers a decent balance—it’s not a primary target and has reasonable security features. However, vulnerabilities are rising, and the cost can be higher.
- Windows:
- Windows has the highest market share and, unfortunately, the most attacks. But this course aims to provide solutions to help mitigate those risks. With some straightforward steps, you can significantly reduce your chances of being targeted, steering attackers toward easier prey.
Windows 10 Privacy & Tracking
Let’s kick things off by saying if privacy is a top priority for you, Windows 10 probably isn’t the best choice. However, if you just have general concerns about privacy, you can tweak some settings to minimize data sharing—but be warned, it’s an ongoing struggle since updates and new features constantly pop up that want to communicate with the cloud.
Cloud-Centric Design
- Cloud-Based Features:
- Windows 10 is built around cloud functionality, which means features like synchronization, sharing, and even the virtual assistant Cortana require a Microsoft account—no local accounts here. This design inherently opposes privacy goals.
Privacy Sacrifices
- Data Syncing:
- By default, data syncing is turned on, which means Microsoft collects data about your websites, browsing history, Wi-Fi passwords, and more. You can turn this off, but it’s something you need to keep an eye on.
- Advertising ID:
- Windows 10 gives each installation a unique advertising ID used to tailor ads from third-party companies. Good news is, you can opt out of this.
Cortana’s Data Collection
- Cortana Overview:
- Cortana is Windows 10’s voice assistant, similar to Siri. It collects a vast amount of data, including:
- Browser history
- Keystrokes
- Microphone input
- Search history
- Calendar events
- Location data
- Payment info (like credit card details)
- Communications from email and texts
- The amount of data collected can seem excessive, so it’s crucial to weigh the value of using Cortana against the personal information you’ll have to share.
- Cortana is Windows 10’s voice assistant, similar to Siri. It collects a vast amount of data, including:
The New Norm
- Changing Definitions of Privacy:
- As technology evolves, the concept of privacy is shifting. Features like Cortana may become essential for the next generation, but that comes at a cost in terms of personal data.
Useful Resources
- If you’re considering using Windows 10 and care about privacy, check out:
Data Collection Agreements
- By downloading and using Windows 10, you are essentially agreeing to let Microsoft collect your information and share it with third parties. Here’s a glimpse of the type of data involved:
- Personal info: name, email, addresses, phone numbers
- Account info: passwords, access info, and interests
- Location data: collected via GPS or nearby Wi-Fi and cell towers
- Content: documents, photos, videos uploaded to OneDrive, and communication content (emails, texts, etc.)
In summary, using Windows 10 means trading some of your privacy for features. It’s essential to understand what data you’re giving up and how it’s being used before fully committing to this operating system.
Windows 10 – Disable Tracking Automatically
You can manually adjust privacy settings in Windows 10, but that can take a lot of time and requires a bit of know-how. Fortunately, there are several automated tools available to help you. However, you still need to be proactive about disabling privacy features, as Microsoft frequently updates the system, and you’ll have to keep up with those changes. If privacy is your top concern, Windows 10 might not be the best fit for you. But if you just want to minimize tracking, you can manage it as long as you stay informed about what needs to be blocked.
Automated Tools for Privacy Issues
Here’s a rundown of tools designed to help tackle Windows 10 privacy problems:
- Destroy Windows 10 Spying
- This tool only modifies the host file, which isn’t very effective on its own.
- Disable Windows 10 Tracking
- Written in Python and open-source, this is a solid option.
- DoNotSpy 10
- Closed source, but it explains the fixes it applies and offers backup options.
- Windows 10 Privacy and Share
- A batch file that is open-source.
- Windows 10 Privacy Fixer
- Another open-source tool.
- ShutUp 10
- Comes with backup functionality.
- Spybot Anti-Beacon for Windows 10
- From a reputable anti-spyware company, which adds a bit of trust.
- Ashampoo AntiSpy for Windows 10
- Also includes backup functionality.
- Windows Privacy Tweaker
- Yet another option for tweaking privacy settings.
Trust Considerations
Many of these tools are developed by smaller, less-known developers, so trust is a critical factor. If the tool is open-source and you understand the programming language, you can verify the software yourself. This is why open-source options are generally preferred; you can check for any hidden malicious features that could undermine your privacy and security.
How These Tools Work
These tools generally perform the following actions:
- Disable services
- Modify app access
- Disable telemetry
- Remove unnecessary apps
- Add firewall rules
- Edit host files
Understanding the Host File
- The host file is a plain text file that helps the operating system resolve web addresses into IP addresses without querying DNS servers. For instance, if you add Google to the host file with its corresponding IP, the system will bypass the DNS query and directly refer to the host file.
- Many of these tools use the host file to redirect “phone home” domain names (like those from Microsoft) to false IP addresses, such as 0.0.0.0.
Limitations of the Host File
However, the host file is not foolproof in Windows 10. Microsoft has hard-coded certain IP addresses into the system’s Dynamic Link Libraries (DLLs), which makes some domains and IPs effectively unblockable. While the host file can still block some phone home requests, it won’t cover everything.
Alternative Blocking Methods
Some tools also create software firewall rules through the Windows firewall to block these requests. However, because the Windows firewall is a Microsoft product, using it to block Microsoft’s IP addresses can be tricky and may require constant monitoring.
Windows 10 – Tool to Disable Windows 10 Tracking
The tool I recommend most for privacy is Disable Windows 10 Tracking by 10se1ucgo. It can be a bit confusing since many tools have similar names, but you can find it Name Disable Windows 10 Tracking. You can download either the Python version or the executable version, and it’s all open source.
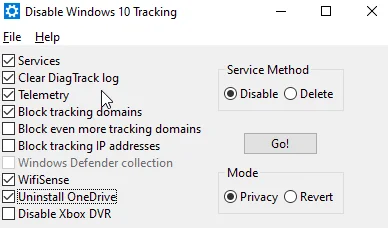
Key Features
- Revert Changes: You can easily revert back to previous settings after making changes.
- Explanations: The tool provides explanations for each setting, which is super helpful.
- Change Log: It keeps a log of the actions it takes, so you can track what’s been modified.
Backup Recommendations
Before using this tool, make sure to back up your important files and create a system restore point if possible. This way, you can recover your system if anything goes wrong.
Using the Tool
- Run as Administrator: You’ll need to run the executable as an administrator to make necessary changes, especially modifications to the host file.
- Interface Overview:
- Modes: There are two modes: Privacy and Revert. Start in Privacy mode to make changes.
- Services:
- You can disable or delete two key services:
- Diagnostics Tracking Service
- WAP Push Message Routing Service
- Disabling is generally safe, while deleting is more drastic.
- You can disable or delete two key services:
- Clear DiagTrack Log:
- This option clears and disables access to diagnostic logs.
- Telemetry:
- Blocking tracking domains is essential here, as this method effectively disables telemetry by adding specific IP addresses to the host file.
- The host file is usually located in the Windows System32 directory under ETC.
- Block More Tracking Domains:
- You can add domains you want to block by searching online for additional Windows 10 IP addresses. Be cautious, as blocking certain domains may affect functionality.
- Block Tracking IP Addresses:
- This uses the Windows Firewall to block specific tracking IP addresses, creating new firewall rules.
- Disable Defender and Wifisense:
- Stops messages from Windows Defender and disables Wifisense data collection, which shares Wi-Fi passwords with others.
- Uninstall OneDrive:
- You can opt to uninstall OneDrive if you don’t use it.
- Application List:
- Review and remove any applications you don’t use for added privacy.
Executing Changes
- Once you’ve made your selections, just click Go. If you deselect unnecessary options, it will speed up the process for demonstration.
- After clicking Go, you’ll see a log of the results, including any errors (like access denied for Windows Defender).
Verifying Changes
- You can check the host file in Notepad to confirm that IP addresses have been redirected to 0.0.0.0.
- Reviewing the firewall settings will show which IP addresses are being blocked.
Reverting Changes
If you decide to revert any changes, right-click the tool, run it as an administrator again, choose the settings you want to revert, and click Go. You’ll receive a report confirming the changes.
In summary, this tool is a handy way to manage privacy settings in Windows 10 effectively.
Windows 10 – Cortana Privacy Settings
Let’s dive into the privacy settings in Windows 10. If you’ve already installed it, great! Just follow along with these settings. But if you haven’t installed it yet, there are a couple of things you should know.
Installation Options
When you’re installing Windows 10, you’ll have two choices:
- Express Install: This uses default settings, which may not be tailored for your privacy needs.
- Custom Install: This option allows you to specify your privacy and security settings during installation. If privacy is important to you, go for the Custom Install.
Even after setting your privacy and security options, be aware that Windows 10 can still send some information to Microsoft.
Account Types
Windows 10 no longer defaults to local accounts; instead, it uses Microsoft accounts that sync with the cloud. If you’re concerned about privacy, it’s better to stick with local accounts. You can set this up, but doing so means you’ll miss out on features that rely on cloud synchronization.
Exploring Cortana
- Accessing Cortana Settings:
- Type “Cortana” in the search bar and then click on Cortana & Search settings.
- Cortana Toggle:
- You’ll see the main on/off toggle for Cortana. Right now, you want it set to off—this is the best choice for privacy.
- Enabling Cortana:
- If you decide to turn it on, you can click the icon and go into settings to enable or disable Cortana. You’ll also be able to view Microsoft’s privacy policy regarding Cortana here.
However, in the latest version of Windows 11 – Cortana as a standalone app has been eliminated
Windows 10&11 – Privacy Settings
Let’s take a look at the privacy settings in Windows 10. To access these settings, go to Settings and then click on the Privacy icon. You’ll see various options on the left for different types of privacy settings.
General Settings
- Advertising ID:
- The first option is to allow apps to use your advertising ID for personalized experiences. Turning this off will reset your ID. Windows generates a unique advertising ID for each system to customize ads from third-party companies, which raises privacy concerns.
- SmartScreen Filter:
- This helps identify phishing and malware sites and informs your decisions about downloads. It checks sites against a dynamic list of reported threats. While it’s a good security feature, enabling it logs your web activity, which could be a privacy issue. If privacy is a concern, consider turning it off.
- Typing Data:
- This option sends Microsoft info about how you write to improve typing features. It logs your keystrokes, which is a privacy concern. If you’re worried about this, turn it off.
- Local Content:
- This allows websites to provide content based on your language preferences. It’s another setting that sends out information, so you might want to disable it.
- Microsoft Advertising:
- You can manage your advertising settings here. Disable personalized ads in your browser and for your Microsoft account to enhance your privacy.
Location Settings
- Location Services:
- When enabled, apps can request your location. There’s a global switch to turn it off, and you can also manage permissions for individual apps. For privacy, it’s best to keep this off unless necessary.
Camera and Microphone
- Camera:
- Decide which apps can access your camera. If privacy is a concern, disable it for all apps until you need it.
- Microphone:
- Similar to the camera, choose which apps can use the microphone. It’s a good idea to turn it off if you’re concerned about it being used without your knowledge, especially by Cortana.
Speech, Inking, and Typing
- Voice Recognition:
- Cortana can learn your voice and writing patterns to make suggestions. This involves collecting personal data, so if you’re concerned about privacy, turn off the “Stop getting to know me” option.
Account Information
- Account Info:
- Disable apps from accessing your name, picture, and other account info for better privacy.
- Contacts:
- Control which apps can access your contacts. Again, this could be a potential privacy issue.
- Calendar:
- Disable apps from accessing your calendar to maintain privacy.
- Messaging:
- Apps may want to read or send emails. If you don’t need this functionality, it’s safer to disable it.
Device Radios and Other Devices
- Radios:
- Some apps use Bluetooth or Wi-Fi. If you don’t want apps controlling these settings, turn them off.
- Other Devices:
- Turn off the option for apps to sync info with wireless devices that aren’t explicitly paired with your PC to protect your privacy.
Feedback and Diagnostics
- Feedback Requests:
- Set Windows to never ask for feedback to keep your information private.
- Diagnostic Data:
- Set the diagnostic and usage data to Basic to minimize the information sent to Microsoft.
Background Apps
- Background Apps:
- Choose which apps can run in the background. Turning these off not only conserves power but also prevents apps from gathering information when you’re not using them.
Mac – Privacy & Tracking
Mac OS X has its share of privacy issues. Let’s break down some of the key points regarding privacy and tracking, especially with the introduction of Yosemite.
Key Issues
- Spotlight Search:
- When using Spotlight to search for files, your location and the names of your searched files are regularly sent to Apple. Even if you don’t see a location notification icon, Apple collects this data when you have location services enabled.
- Notably, this data is transmitted before you even start typing. For example, while searching for a document called “secret plans Obama leaked me,” Apple receives this info alongside your location and user ID, which is a unique identifier assigned to you. Apple claims that this ID changes every 15 minutes, but the privacy implications remain a concern.
Disabling Tracking Features
- Spotlight Suggestions:
- To turn off these tracking features, start by going to System Preferences.
- Select Spotlight and disable Spotlight Suggestions and Bing Web Searches. This is essential for privacy.
- Safari Settings:
- If you use Safari, open it, go to Preferences, and click on the Security tab. Deselect the option that includes Spotlight suggestions.
Helpful Resources
- Here are some useful websites that provide information about privacy issues in Mac OS X:
Automation with Python
- If you’re comfortable with Python, you can download a script from Fix Mac OS X that automatically disables various privacy-related settings.
- To run the script, use the command
python fix-macosx.py, and after execution, make sure to log out and back in for the changes to take effect.
Location Services Notifications
- To receive notifications when location services are used, go to System Preferences > Privacy & Security.
- Unlock it, navigate to Location Services, click Details, and check the option to show the location icon in the menu bar when system services request your location. This way, you’ll be notified whenever Apple is accessing your location.
Linux and Unix-like Operating Systems
When we talk about privacy in conjunction with security, it’s time to turn our attention to Linux and BSD distributions. While Mac has solid security features, it tends to fall short on privacy.
Security and Privacy
- SELinux:
- This is a security feature specific to the Linux kernel, but it’s not a complete distribution, which is what we need.
- Linux and BSD Distributions:
- These types of operating systems provide both security and privacy benefits, but this often comes at the cost of interoperability and usability. For instance, you won’t be able to run Photoshop or Microsoft Office natively. However, there are alternative applications available for these operating systems.
Multi-OS Usage
- Don’t be discouraged! It’s completely possible to use multiple operating systems with relative ease, and I’ll show you how.
Recommended Distributions
For those with modest security and privacy needs, I recommend the following three distributions:
- Debian
- OpenBSD
- Arch Linux
A Brief Overview of UNIX-like Systems
- If you’re primarily familiar with Windows and maybe macOS, you might not know that many operating systems have evolved from UNIX, which dates back to the mid-1960s.
- UNIX-Linux History Tree:
- At the top, you have UNIX, which eventually led to various derivatives such as BSD (the basis for OpenBSD) and the inception of Linux itself.
- Linux, initiated by Linus Torvalds, is free software supported by a global community of programmers.
Other Notable Derivatives
- From Linux, we have systems like Android and Chrome OS. Notably, macOS is a derivative of BSD, tying it back to the UNIX heritage.
Differences in Operating Systems
- Windows NT:
- Unlike UNIX-like systems, Windows is based on the NT kernel developed by Microsoft.
Desktop Environments
- The desktop experience in these UNIX-like operating systems varies based on the chosen desktop environment. Examples of popular environments include:
- GNOME
- KDE
- XFCE
- MATE
- Cinnamon
- LXDE
Embracing UNIX-like Systems
- Don’t be intimidated by these UNIX-type operating systems. They may be different, but with persistence, you can adapt. If you’re familiar with macOS, you’ll find some similarities since it’s also based on BSD, making the command line interface more approachable.
Linux – Debian
Let’s take a look at Debian, a Linux-based operating system and distribution. Here are some key points about it:
Overview of Debian
- Open Source:
- Debian is made up entirely of free and open-source software, with most of it released under the GNU General Public License. It’s maintained by a community known as the Debian Project.
- Software Packages:
- Debian comes with over 5,000 pre-compiled software packages, all neatly packaged for easy installation on your machine. The best part? It’s all free!
Structure of Debian
- Tower Analogy:
- Think of Debian as a tower:
- Base: The kernel sits at the bottom.
- Middle Layers: Above that are the essential tools.
- Top Layer: Finally, all the software you use sits at the top, with Debian organizing everything to ensure compatibility and functionality.
- Think of Debian as a tower:
Privacy and Security
- No Phoning Home:
- Using Debian means you won’t have to worry about “phoning home” to Microsoft or any other company. This makes it a great choice for anyone who prioritizes security and privacy.
Personal Preference
- My Favorite:
- Personally, I consider Debian my favorite operating system for users with modest security and privacy needs. Its balance of usability, stability, and freedom makes it a solid choice.
Linux – Ubuntu
Let’s dive into Ubuntu, but just a heads up—it’s not my top pick. Here’s what you need to know:
Privacy Issues
- Data Sharing:
- By default, Ubuntu sends some of your information to third parties without asking for your permission. If you’re using the default settings, every time you type in the dash to open an app or search for files, your search terms get sent to various third parties, including some advertisers.
How to Protect Your Privacy
- Adjusting Settings:
- If you want to stop this from happening, you’ll need to change some settings.
Overall Recommendation
- Personal Opinion:
- Honestly, I wouldn’t recommend Ubuntu, but I’m sharing this for your awareness if you happen to be using it.
- That said, Ubuntu does offer better privacy and anonymity compared to Windows or macOS.
Ideal Users
- For New Users:
- I think Ubuntu is a decent choice for those new to Linux who might find Debian, Arch Linux, or OpenBSD too complex. It’s user-friendly and a good starting point.
Conclusion
Choosing the right operating system is crucial for ensuring your security, privacy, and anonymity, as each OS serves different needs and comes with its own risk profile. Windows, while widely used, has significant privacy concerns and is a major target for cybercriminals due to its large market share. Mac OS X offers solid security features but has seen a rise in vulnerabilities, making users cautious. Linux, particularly distributions like Debian and Arch, is regarded as the most secure option, with lower market share and therefore a reduced threat landscape, but may lack support for certain applications.
However, users must also consider usability versus security. While Linux provides robust security, it may not be suitable for everyone, especially those reliant on specific software. Ultimately, understanding the security features, vulnerabilities, and privacy implications of each OS will empower users to make informed choices tailored to their specific needs, enhancing their overall digital safety.


