Table of Contents
By understanding the potential attack vectors and specific risks associated with IoT devices, you will be better equipped to construct a robust network architecture that can mitigate these threats and prevent the spread of attacks.
Key Points
- Attack Vectors:
- An attack vector refers to the method or pathway through which a cyberattack can occur. It is essential to identify these vectors to protect the network effectively.
- Examples of attack vectors can include:
- Phishing attacks
- Malware
- DDoS (Distributed Denial of Service)
- Man-in-the-middle attacks
- IoT vulnerabilities
- IoT Risks:
- IoT devices can introduce unique security challenges due to their often limited security features and the vast network of interconnected devices.
- Common IoT-related risks include:
- Insecure device configurations
- Lack of regular software updates
- Data interception
- Network Architecture for Mitigation:
- After understanding the attack vectors, the next step is learning how to design your network architecture to minimize the risk of these attacks.
- Effective strategies may include:
- Implementing segmentation within the network to isolate IoT devices.
- Using firewalls and intrusion detection systems.
- Regularly updating and patching software.
- Conducting regular security assessments.
Network Isolation and Network Attacks
Network isolation can be defined as the practice of physically or logically placing devices on separate networks and restricting how or if those devices can communicate with each other. This approach is crucial for mitigating potential threats.
Why Consider Network Isolation?
- Threat Mitigation:
- If an attacker or malware gains access to your network or one of the devices, they can attempt to spread the attack to other devices. Network isolation can significantly reduce the chance of such propagation.
- Untrusted Devices:
- Consider whether there are untrusted devices on your network. This could include guest devices or family members’ devices that may not adhere to good security practices. These potentially infected devices can be a gateway for attacks.
- Vulnerability Assessment:
- It’s essential to evaluate whether you trust all devices on your network. Are they all updated? Are any backdoors present? Untrusted devices can be exploited by attackers to spread malicious activities.
- Internet of Things (IoT) Devices:
- Many users now have IoT devices such as smart TVs, webcams, and even smart light bulbs connected to their networks. These devices often lack robust security measures and may not receive regular updates, making them attractive targets for attackers. Isolating these devices can help protect your network from potential threats.
The Growing Risks
As the number of IoT devices increases, so does the risk associated with them. Cybercriminals are likely to exploit these devices to gain access to internal networks. Numerous documented cases show IoT devices shipped with backdoors that attackers can use.
Potential Threats Once Attacked
If an adversary gains access to your network, they can:
- Traffic Sniffing: Observe and record traffic across the network.
- Man-in-the-Middle Attacks: Intercept and manipulate network traffic, potentially injecting malicious code or stripping encryption.
- Direct Device Attacks: Exploit open services on network devices. For instance, failing to secure a smart TV or utilizing vulnerable SSH can lead to direct attacks.
Principles of Network Isolation
Network isolation is based on the principles of isolation and compartmentalization. It serves as a defense-in-depth strategy that enhances security by reducing the potential attack surface. While network isolation can mitigate attacks, it may also introduce administrative burdens.
Balancing Need and Complexity
The decision to implement network isolation should be based on your specific circumstances and needs. While some levels of network isolation can be straightforward to implement without significant burden, others may require more intricate planning.
In the end, understanding the threats and implementing effective network isolation strategies can significantly enhance your network’s security posture. As we discuss further, we’ll explore practical steps to achieve network isolation effectively.
ARP Spoofing and Switches
Overview of Switches
Let’s revisit what switches are in a network. Switches are devices where network cables are plugged in, and they maintain a MAC (Media Access Control) address table, known as the MAC table. This table contains the unique MAC addresses of devices, which switches use to send traffic to the correct destination on a Local Area Network (LAN). Switches operate at the data link layer (Layer 2), meaning that when data is traveling on your local network, IP addresses are not employed. Instead, MAC addresses help traffic find its destination.
Security Features of Switches
Switches provide enhanced security compared to hubs because they create isolated collision domains. This means that traffic sent to a specific MAC address is only forwarded to the corresponding physical LAN port. Consequently, other devices connected to the switch do not receive this traffic, which enhances privacy and security on the network.
Vulnerabilities in Ethernet Networks
Despite their security features, Ethernet networks connected via switches can still be vulnerable to man-in-the-middle (MitM) attacks. In such attacks, an adversary tricks other devices into believing they are the router or gateway by exploiting the Address Resolution Protocol (ARP). This allows the attacker to observe, capture, inject, and manipulate the traffic on the network.
Understanding ARP
The Address Resolution Protocol (ARP) is responsible for translating IP addresses (network layer) into MAC addresses (data link layer). When a device wants to communicate with another on the local network but lacks the necessary MAC address, it issues an ARP request to resolve the IP address into a MAC address. The device with the corresponding IP address responds with its MAC address, updating the ARP table in the process.
ARP Spoofing Attack
Tools like ARP-SPOOF, EtherCAP (available in Kali Linux), and Kain & Able (in Windows) can enable attackers to spoof ARP messages. By responding to ARP requests with false information, attackers can convince devices that they are the legitimate router. This exploit leads to ARP poisoning, where the attacker can intercept and manipulate the traffic that would normally go to the router.
The Lack of ARP Authentication
The significant vulnerability in ARP is its lack of authentication; any device can claim to be another. ARP was developed under the assumption that all devices on a local network could be trusted, which is no longer valid. The lack of security means that ARP spoofing can easily occur.
Consequences of ARP Spoofing
Once ARP spoofing is successful, the attacker can monitor all traffic intended for the victim instead of the router, enabling them to perform various types of attacks like traffic manipulation, code injection, and SSL stripping.
Internal Attacker Requirements
For ARP spoofing to be a concern, the attacker must be on the internal network. Nonetheless, even if the attacker is internal, they must intend to execute these attacks. There are growing concerns that this technique could be a method for malware, such as ransomware, to propagate across networks once it infects a device.
Further Learning
If you wish to dive deeper into ARP spoofing, visit IonGeek’s website, which offers extensive resources and videos on the subject. This method of executing MitM attacks, along with other ARP weaknesses, can lead to various network vulnerabilities.
Denial of Service Attacks
Additionally, tools like TuxCut and NetCut can facilitate Denial of Service (DoS) attacks using the ARP protocol. Ironically, these tools can also serve protective functions against similar attacks. In future discussions, we will explore mitigations for ARP-related issues.
Designing a Home Network for Security
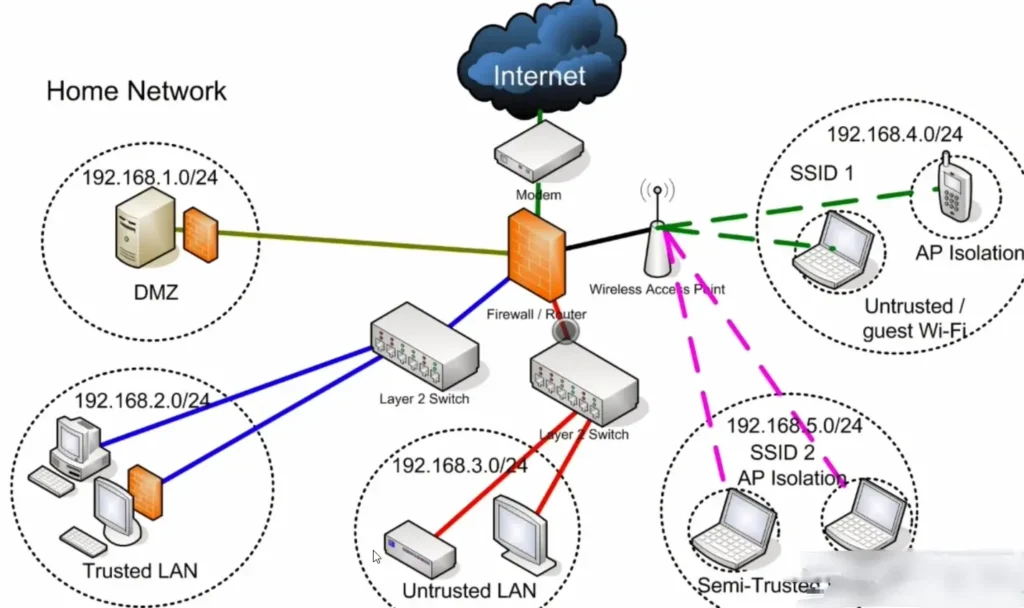
Today, we’re going to discuss how to design your home network in a way that protects you from attacks and the spread of those attacks through isolation. The first thing to consider is the creation of separate, routable networks for devices that have different trust levels.
Implementing Network Isolation
- Separate Networks:
- You can implement this separation using your router and/or firewall. They may be the same device or separate. Alternatively, you could use a switch for this purpose. For wireless devices, this can also be managed through your Wi-Fi access point or router.
- Network Example:
- In the example illustrated, you can see multiple subnets such as 192.168.1.x, where different devices are placed. Each subnet can represent a different trust level:
- DMZ (Demilitarized Zone): For devices that need direct inbound connections to the internet.
- Trusted VLAN: For devices that you trust completely.
- Untrusted VLAN: For devices that you do not trust.
- Semi-trusted Wi-Fi Network: For devices like guest Wi-Fi.
- In the example illustrated, you can see multiple subnets such as 192.168.1.x, where different devices are placed. Each subnet can represent a different trust level:
Understanding the DMZ
The DMZ is a special network that allows inbound connections from the internet, making devices in this zone more exposed and thus requiring extra security measures. Common devices that might reside in the DMZ include web servers, IoT devices, or CCTV cameras.
- Implementation:
- To set up the DMZ, connect the device physically to your router/firewall using an Ethernet cable, assign it a separate network (e.g., 192.168.1.x), and configure firewall rules to block outbound connections while allowing only inbound connections.
VLANs for Network Isolation
- What are VLANs?
- VLANs (Virtual LANs) are logical separations of networks rather than physical ones. They use tags in packets to differentiate between different VLANs, which helps in isolating traffic without requiring separate physical hardware.
- Benefits of VLANs:
- Devices connected to the same physical switch can be placed on different VLANs, effectively isolating the traffic. For example, ARP spoofing attacks in an untrusted VLAN won’t affect trusted devices on another VLAN.
- Tagging Mechanisms:
- VLANs typically use tagging mechanisms such as ISL (Inter-Switch Link) or IEEE 802.1Q to maintain separation.
Considerations and Limitations
- Security of VLANs:
- Although VLANs provide a certain level of security, techniques like VLAN hopping have been used in the past to bypass these protections. Modern VLANs have been patched and are now more secure.
- Physical vs. Virtual Isolation:
- While VLANs are convenient and easier to implement, physical isolation remains a more robust security measure. Physical networks require dedicated routers and distinct ports for each network.
Steps to Enhance Security
- Use Separate Physical Networks:
- If you feel VLANs aren’t sufficient, you can assign devices to separate physical networks directly through your router/firewall.
- Mitigating Attacks:
- This physical isolation helps mitigate ARP attacks and other vulnerabilities. However, various layers of protection can further enhance security.
Designing your home network with isolated segments can significantly improve your security posture. By using DMZs, VLANs, and considering physical isolation, you can effectively protect your devices from potential threats.
Mitigating Network Attacks
There are some additional options to help mitigate network attacks. It is possible to install ARP protection software on your devices like your laptops or your desktops. Some of the tools that can help you do that are:
Available ARP Protection Tools
- NetCut: This also has a mobile version.
- TuxCut: This is for Linux devices.
- SniffDet: This is a remote sniffer detection tool meant for Linux.
- XARP: This has a free and a paid version for Windows and Linux.
- ARP Watch: This is available for Linux, used for monitoring ARP requests.
On your router and/or firewall, see if ARP Watch or an equivalent service is available. For example, ARP Watch is available on PF Sense and helps mitigate ARP attacks.
Static ARP Entries
Consider the use of static address resolution protocol (ARP) entries. These are permanent entries in your ARP cache instead of dynamic ones, as dynamic ones can be spoofed.
Advanced Features
Now, we’re moving into more advanced options that are less likely to be available on simple devices, and you’re going to want higher-end devices to support this sort of technology.
- Port Protection and Security: On your router, firewall, and switch, look for functionality names such as Port Protection or Port Security. Cisco has its version called Port Security, which you would want to enable.
- 802.1AE Standard: This is an IEEE standard involving MAC security (MACsec), which enables network authentication and encryption and other services.
- 802.1X and EAP over LAN: This is a port-based network access control (PNAC) that means devices need to authenticate to connect to the network, which helps mitigate network attacks.
DHCP Snooping
Another option is DHCP snooping. This is a feature in some switches, namely Cisco switches, that watches DHCP requests and builds a table of IP addresses to MAC addresses similar to an ARP table. It relies on the DHCP server to be the trusted authority and can be used in conjunction with other switch security like port security to bring an interface down and block an adversary.
Using VPNs
For those extremely concerned with security, it’s possible to use VPNs on your local network to connect to local devices. For example, all your trusted devices could communicate via a VPN terminator, which would often be your router or firewall. You essentially create a virtual encrypted network on top of your physical network.
The router/firewall would have to be powerful enough to support all of this encryption, otherwise you’re going to have network delays and network lag.
Security Principle
In your design, follow the principle that all traffic should be denied unless explicitly allowed. This is usually the best way for security but does come with its administrative burden.
Device Requirements
So, we’ve talked a lot about separating and isolating your devices and your network. Obviously, you will need equipment that is capable of supporting the features I’ve discussed. You will need a good router, running more than likely custom router firmware. Simple home routers won’t cut it. If you want to use VLANs, whatever you use to implement and support those VLANs—your router, your firewall, and the network interface controller of those assigned to the LAN interface—must support IEEE 802.1Q VLAN tagging.
VLAN and Switch
You will need a switch connected to the LAN interface that is capable of supporting the creation, configuration, and trunking of port-based VLANs.
- PF Sense and DDWRT: For example, PF Sense supports VLANs and DDWRT supports VLANs as well.
Wi-Fi Security
For Wi-Fi, you will need a router and/or access point that supports something called AP isolation, and it will need to support multiple SSIDs on the same access point. Wi-Fi isolation security, we’re actually going to cover in its own section.
Conclusion
Understanding the attack vectors and risks associated with IoT devices helps in building a robust network architecture to mitigate threats. Key measures include identifying attack pathways, isolating IoT devices within the network, utilizing firewalls and intrusion detection systems, regularly updating software, and conducting security assessments. These strategies significantly enhance network security.


