Table of Contents
In this post, we need to focus on understanding security, privacy, and anonymity, and on top of this foundational principle, we need to know how to respond to a wide variety of situations, especially your own personal situation.
I will use this post to enable you to assess, select, implement and monitor the appropriate security controls for this purpose in an easy to understand manner that can be used to reduce risk.
Foremost among these is the need for a deeper understanding of the relationship and tension between security, privacy and anonymity.
Protect What You Value
Hey there! Time is super valuable, right? We don’t want to spend hours upon hours dealing with security stuff when we could be doing what we love. My goal for you is to make sure you get the most out of your time when it comes to security. What we really want to do is protect the things that matter the most to you and make sure you can do your thing online safely.
So, take a moment to think about your accounts, files, emails, the websites you visit, and all that. Ask yourself, “What’s the stuff I can’t afford to lose? What would hurt the most if it got stolen or destroyed? What could mess up my reputation?”
Maybe you’ve got photos, credit card info, bank details, personal info, or login details for sites like LinkedIn, Facebook, Amazon, PayPal, and your email. Think about how bad it would be if these things got into the wrong hands.
Make a list of these precious items – we’re calling them your ‘security assets’. These are the things you care about a lot. Later on, we’ll use this list to focus our security efforts. No point in spending ages backing up files that are easy to replace, right? But for files that are irreplaceable, we’ll be extra careful.
The point is, we want to put most of our effort into protecting the things that are truly important to you and not waste time on stuff that isn’t a big deal or can be easily replaced.
What is Privacy, Anonymity and Pseudonymity
let’s chat about privacy, anonymity, and pseudonymity. These are things that might be really important to you, especially when it comes to protecting your valuable stuff.
Privacy is like when no one sees what you’re doing, but they might know who you are. It’s all about keeping things secret and confidential. Imagine sending an encrypted email to a friend; only you two can read it. That’s privacy. Or if you use a cloud service like Dropbox, you’re not anonymous, but if you encrypt your files with a key only you have, your data stays private.
Anonymity is different. It’s about no one knowing who you are while maybe seeing what you do. It’s keeping your actions separate from your real identity. Like using Tor to post a message online without revealing who you are. Your message is out there, but you’re anonymous.
Pseudonymity is a bit of a mix. It’s when you want to keep a reputation but hide your real identity. Like using an alias on social media or a forum. People might know your alias, but not who you really are.
Now, why is this important? Well, different situations call for different levels of privacy, anonymity, or pseudonymity. And understanding the difference helps you figure out the right security measures for your needs.
Security, Vulnerabilities, Threats and Adversaries
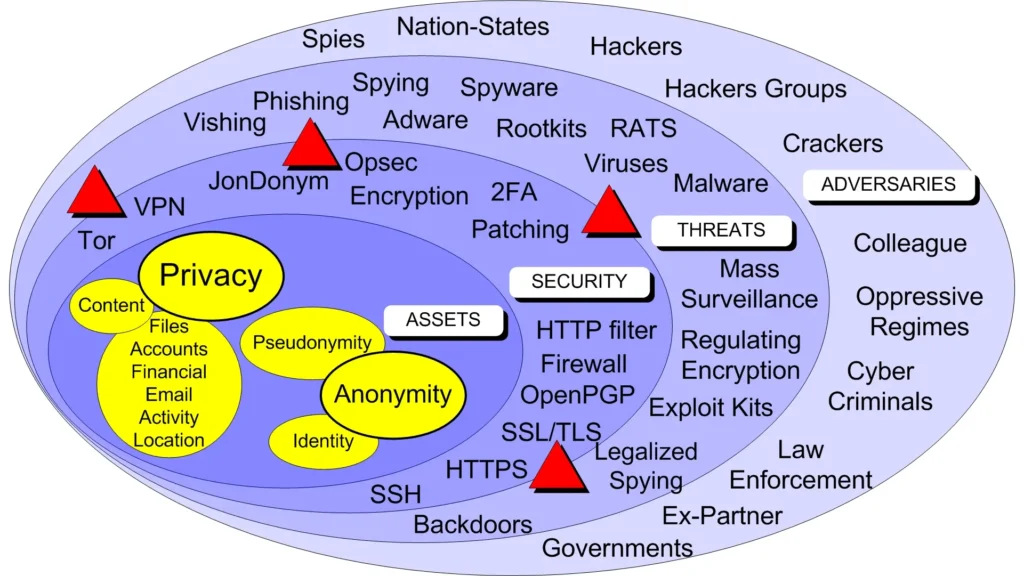
Alright, let’s break this down. First off, we’ve got our assets—these are the things we really care about, like our files, accounts, financial info, emails, and anything that relates to our identity or anonymity, like our browser history or what we download and post. These assets are personal to each of us.
Now, to keep these assets safe, we use security measures. Think of things like VPNs, encryption, operational security (Opsec), keeping software updated, using HTTP filters, OpenPGP for emails, and lock screens. Basically, security is all about how well we can protect our assets from threats posed by adversaries.
So, what are these threats? They can be things like malware attacks, mass surveillance, exploit kits, or viruses. These threats come from adversaries, which could be hackers, cybercriminals, government agencies, oppressive regimes, or even an ex-partner if you’re unlucky.
Now, let’s talk about vulnerabilities. These are the bugs or weaknesses in our security measures. A threat tries to exploit these vulnerabilities to harm our assets. For example, if your computer isn’t updated, malware could get in through that vulnerability.
We can think of risk like this: Risk = (Vulnerabilities x Threats x Consequences). Basically, it’s about how likely it is that a threat will exploit a vulnerability and what the fallout would be. This risk is specific to you, your privacy, and your anonymity.
Your unique set of threats and adversaries is called your threat landscape or threat model. While we might share common threats like hackers and cybercriminals, not everyone has to deal with an ex-partner who might cause trouble.
The key takeaway is that security isn’t one-size-fits-all. You need to choose your security measures based on the specific threats and adversaries you face and the potential consequences of those threats. For example, if you’re worried about mass surveillance from an oppressive regime, you might use Tor to help with that.
Remember, security isn’t just about technology. It’s also about actions and processes. Your behavior is one of the most crucial security controls. The right mix of technology, actions, and processes will help protect your assets, privacy, and anonymity.
Threat Modeling and Risk Assessments
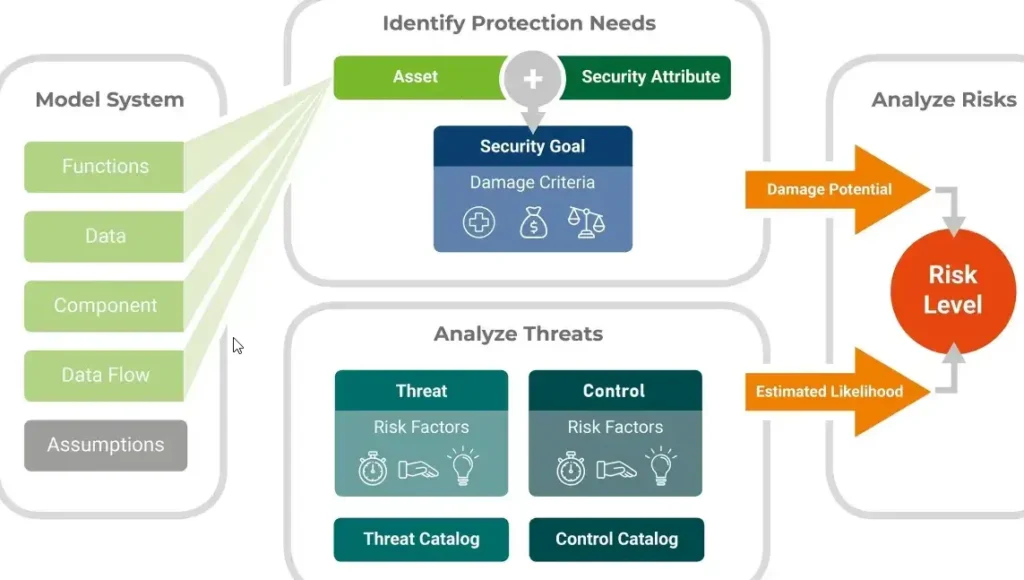
Alright, let’s dive into threat modeling and risk assessments. By now, you should have a grasp of vulnerabilities, threats, adversaries, consequences, and the resulting risk. You should also understand that security is all about the processes, actions, and technologies that protect your assets, privacy, and anonymity. Now, we’re going to explore how to apply some of this knowledge in a more practical way.
First off, a crucial point: you can never achieve 100% security, just like you can never have zero risk. So, you can’t completely protect your assets or maintain perfect privacy or anonymity. If someone claims to offer 100% security, run away. They clearly don’t know what they’re talking about. As long as you’re engaging in activities, there will always be some level of risk. Living life comes with risks, and so does using the internet. We accept these risks because of the incredible opportunities and benefits the internet offers. To take advantage of these opportunities, we have to accept a certain level of risk. You need to decide what your personal risk tolerance is based on your circumstances.
If you have a low tolerance for risk—meaning the consequences of losing security, privacy, or anonymity are high—you’ll need more security controls. These controls might be more advanced and could make things less convenient. On the other hand, if you have a higher tolerance for risk—where the consequences are less severe—you won’t need as many security controls. So, security is about finding a balance between usability and security, between risk and opportunity. Security often complicates ease of use, which is why we must choose security controls that are appropriate for our risk appetite.
This course, especially the sections on “Know Yourself” and “Know Your Enemy,” will give you background information on the threats and vulnerabilities you might face online. This will help you make informed decisions about your security, privacy, and anonymity needs, and your tolerance for risk. So, wait until we cover those sections, and then you’ll start to understand more about the threats and adversaries out there, and things you might not have known about before.
Another important point: you should take a risk-based approach to your security. Since we can’t have 100% security, you need to apply the right level of security to mitigate risk without making the system too cumbersome to use. Only you can decide how much security is necessary to protect your assets.
To take a risk-based approach, you should do basic threat modeling and risk assessments when selecting your security controls. Let me walk you through an example of how to do this. Risk equals vulnerabilities times threats times consequences. Let’s go through an assessment process.
First, start with your assets. You should have a list or at least an idea of what you care about and want to protect. Next, consider vulnerabilities, threats, and adversaries. You might have some idea of what your threats and adversaries are, or you might have no clue. In the “Know Your Enemy” section, we cover many vulnerabilities, threats, and adversaries. Go through that section to determine which apply to you to assess your risk.
Think about the consequences if your assets are compromised. Consider what happens if they are lost, stolen, destroyed, or encrypted, or if they end up in the hands of adversaries, criminals, hackers, or law enforcement. How would this impact your reputation, privacy, or anonymity? Focus on the consequences if the threats and adversaries are less tangible, which is often the case. Concentrate on the impact to determine the risk and the security controls you need.
Once you understand your assets, threats, vulnerabilities, adversaries, and the available security controls (which you might not know all about yet), and you understand the consequences of threats being realized, you can determine a general level of risk. You might identify specific risky behaviors, threats, adversaries, or vulnerabilities that require the strongest security controls and the most attention.
Let me give you an example. Maybe you’re concerned about your laptop being stolen. The adversary would be a thief, the vulnerability is the data on the laptop being in clear text, and the consequences are reputational damage and possibly identity theft. Based on your risk tolerance, you would select security controls to mitigate this risk. You should apply the strongest security controls to the greatest risks first.
You can apply these security controls by selecting, implementing, evaluating, and monitoring them as you operationally execute them in real-world environments. When selecting, choose the security control that best mitigates the risk.
For example, for the stolen laptop we just discussed, you might choose full disk encryption, locking and encrypting the boot sector, and preboot authentication as your security controls. Then, implement these controls. You install the lock, set up full disk encryption and configure it. Next, evaluate the effectiveness of the selected controls.
Check that full disk encryption is working properly and that data is actually encrypted. Finally, monitor the effectiveness of the security controls, for example, checking for security updates and lock vulnerabilities. If weaknesses are found, return to the selection phase.
So, that’s threat modeling and risk assessments. Once you’ve gone through part of this course, you should start to feel more confident in assessing threats and adversaries, understanding where your vulnerabilities might be, and applying security controls to protect what you care about—privacy, anonymity, files, or email.
Select > Implement > Assess > Monitor
I hope this helps you select the correct security controls and gives you the maximum benefit to protect your assets.
Security vs Privacy vs Anonymity
Security, privacy, and anonymity can sometimes be at odds with each other. For instance, a feature in your browser might check every website you visit to see if it’s on a known malware distribution site. This feature boosts security because it can prevent you from visiting sites with malware. However, it could potentially interfere with your privacy and anonymity since the malware distribution site is maintaining constant contact with your browser and might be constantly updated on which sites you visit and when. In situations like this, you need to make a decision between security, privacy, and anonymity.
People have different tolerances for being tracked and the disclosure of their personal information and online activities. If you’re a political dissident fighting for human rights, you might need total privacy and anonymity online against your government. If you’re an average internet user in the West, you might just not want your emails read and your surfing history revealed, finding that to be an imposition. The consequences of disclosure and de-anonymization range from mild privacy invasions to life-threatening situations.
The amount of privacy and anonymity you require is directly proportional to the amount of security you need. Keep that in mind as we go through the course and you choose which security controls you want and need to apply. Let me say that again: the more privacy and anonymity you need, the more security controls you require.
“Privacy isn’t about hiding something. It’s about being able to control how we present ourselves to the world. It’s about maintaining a public face while at the same time being permitted private thoughts and actions. It’s about personal dignity.” – Bruce Schneier, cryptographer, computer security and privacy specialist, writer, fellow at the Berkman Center for Internet & Society at Harvard Law School, a program fellow at the New America Foundation’s Open Technology Institute.
Defense In Depth
There’s a principle in security called “Defense in Depth.” The idea is to provide layers of defenses so that if one defense fails, another continues to protect you in its place. So, there are three main types of defenses you can think of.
First, there’s Prevention. This is like encrypting your files and making sure the key or password isn’t available. So, prevention is about setting up defenses to stop people from compromising those files and accessing confidential information.
Next is Detection. Detection could be setting up something called a “Canary.” This is planting a deliberate trap so that if a hacker or malware triggers this canary or trap, you’re notified that something is amiss.
And then there’s Recovery. Recovery is like having backups or the ability to recover a lost file or a lost account. The principle here is, if you can’t prevent something, you detect it; if you can’t detect it, you recover from it.
Throughout the course, we will employ the principles of “Defense in Depth,” having multiple defenses at each stage for the assets we want to protect. This isn’t complex; it’s simply a matter of changing your behavior if needed and using the right technology in the right place to provide you with that “Defense in Depth” approach.
The Zero Trust Model
Trust is a key factor in your security, privacy, and anonymity. The less you trust, the lower your risk. The zero trust model suggests minimizing the number of things you trust, including yourself. This means evaluating instead of blindly trusting. Everything presents a level of risk, some acceptable, some not. You can mitigate this risk by distributing trust.
For example, if you want to store files online, you might choose a popular service like Dropbox. However, you shouldn’t trust that they won’t get hacked, view your files, or lose/change them. Instead, you should make a risk-based choice. If privacy is important, you might back up your files in a separate location and encrypt them with a key only you have. This way, you distribute trust to the backup and yourself via encryption.
Another example is running applications in isolated virtual machines or sandboxing them to prevent communication. Instead of trusting proprietary software, you might choose free and open-source software (FOSS) that has been security-audited.
Throughout the course, I’ll emphasize the use of the zero trust model: evaluate instead of trusting, mitigate risk by distributing trust.
Conclusion
We’re all about keeping what matters to you safe and sound. Whether it’s your photos, your bank details, or your secret cookie recipe, we want to make sure that only you have access to them. We’re talking about privacy, which is about keeping things under wraps, anonymity, which is about being incognito online, and pseudonymity, which is like wearing a cool mask at a party.
We also need to understand that security isn’t just about having a fortress; it’s also about knowing when to let your guard down a bit. You can’t be 100% secure all the time, and that’s okay. It’s about finding a balance that works for you. Maybe you’re super careful with your data, or maybe you’re a bit more relaxed. Either way, we’re here to help you figure out the best way to protect your digital life.
And remember, security is not just about the tech; it’s also about what you do and how you behave online. It’s about being smart, being aware, and taking the necessary steps to keep your stuff safe. So, let’s get started on this journey to lock down your digital world!


