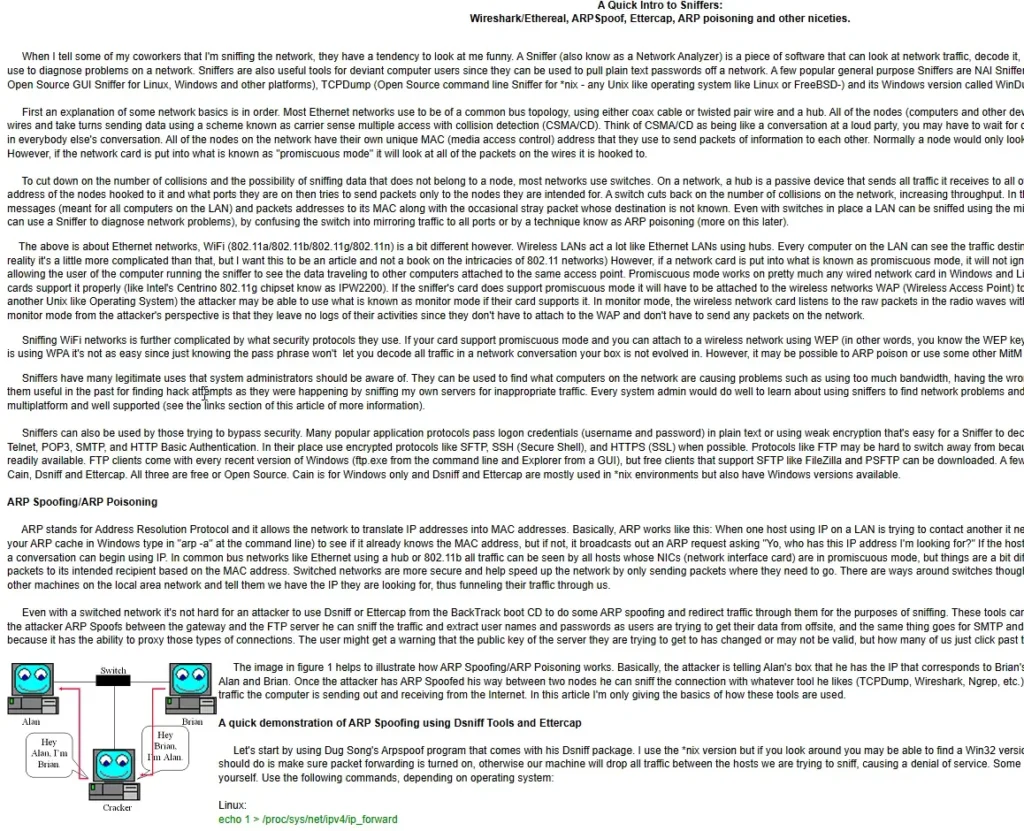
Network Attacks, Architecture and Isolation
By understanding the potential attack vectors and specific risks associated with IoT devices, you will be better equipped to construct a robust network architecture that can mitigate these threats and prevent the spread of attacks. Key Points Network Isolation and Network Attacks Network isolation can be defined as the practice of physically or logically placing ...