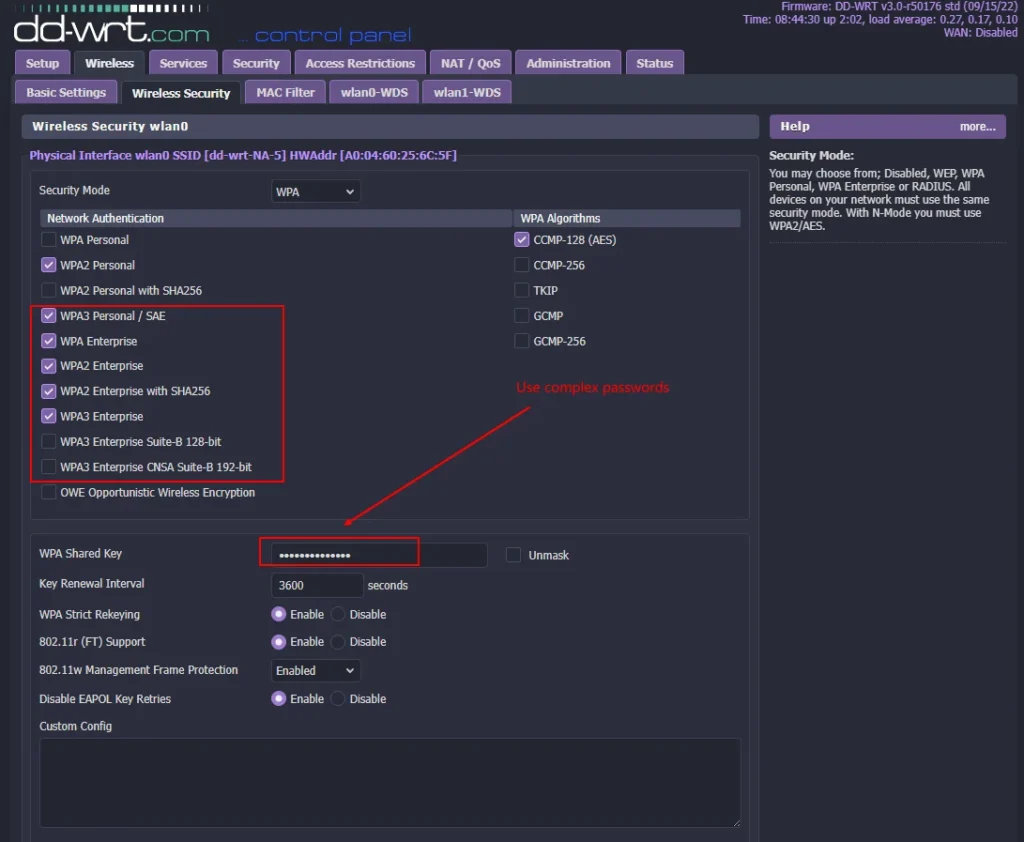
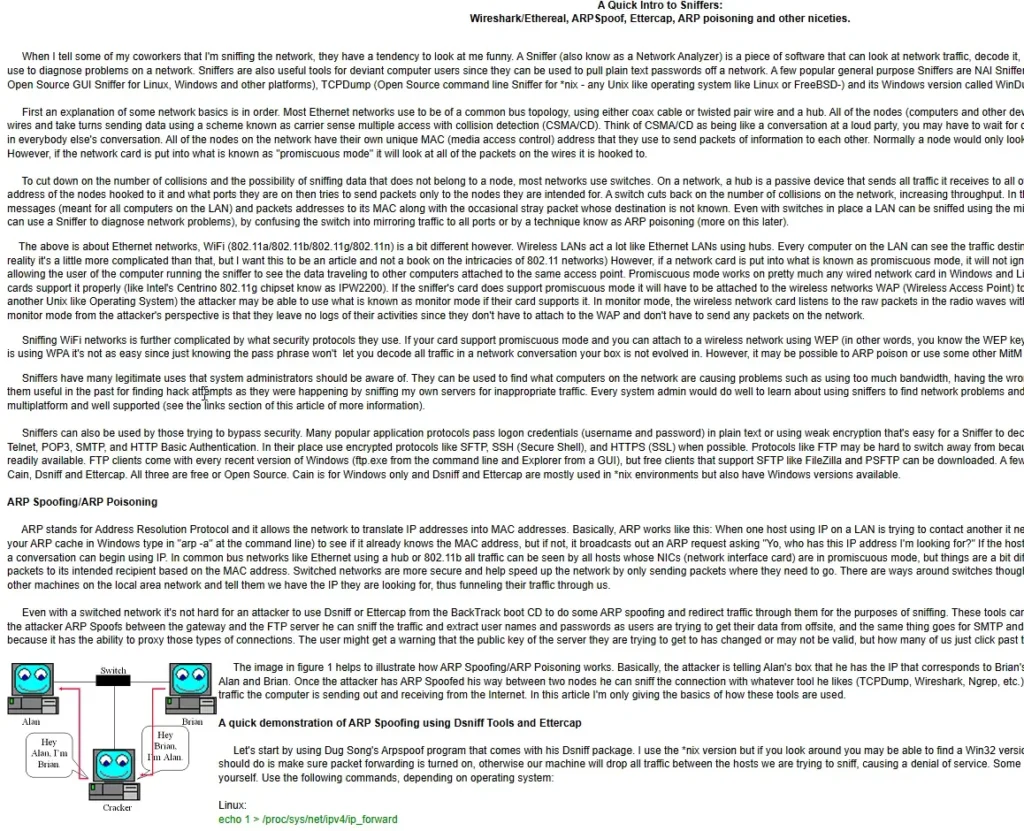
Wireless and Wi-Fi Security
The objective of this post is to understand the possible attack vectors on a wireless network, understand the weaknesses in wireless and how to test for those weaknesses, then how to best architect and configure your wireless network for maximum security. And we also cover mitigating radio frequency attack vectors and how to monitor your ...