Table of Contents
This article is to provide you with a comprehensive overview of how to use a VPN or Virtual Private Network for enhanced security and privacy protection. At the same time you will learn about the best protocols and encryption methods associated with VPN use and why, the weaknesses of VPNs and how to mitigate them.
Understanding VPNs and Anonymizing Services
Different Anonymizing Services
There are several anonymizing services available, such as Tor, Freenet, I2P, and VPNs (Virtual Private Networks). Among these, VPNs are considered simple and easy to use. However, they might not be as strong against determined and powerful adversaries like nation-states compared to options like Tor.
How VPNs Work
A VPN setup involves a VPN client on one end and a VPN server (also known as a VPN terminator or exit node) on the other. VPNs maintain privacy by creating an encrypted “tunnel” for your internet traffic between these two points. This tunnel ensures that the data is protected while traveling over the internet, though this protection only lasts from the client to the server.
VPN Client Setup Options
VPN clients can be set up in three main ways:
- On your operating system: You can use clients like CyberGhost or SafeJumper. They let you connect to a VPN server by selecting a country and configuring settings like DNS and ports.
- On a router: By installing a VPN client on your router, all devices on your network can be protected. This setup encrypts traffic from your devices to the VPN server.
- In a virtual machine: A VM can act as an isolated environment with its own VPN client. This allows for configurations such as nested VPNs, where you have multiple layers of VPN protection.
Limitations and Additional Security
Remember, the encryption is only between the VPN client and server. For complete protection, additional encryption (like HTTPS) is needed from the server to the final destination.
Benefits of VPNs
VPNs help protect against hackers and trackers by hiding your internet activity. They also prevent your ISP from logging your online actions. Furthermore, VPNs can bypass geographic restrictions and censorship by disguising your location.
VPNs vs. Geographic Restrictions
For example, if a website is restricted in your country, using a VPN server in another country can grant you access. This works because your real IP address is hidden, and only the VPN server’s IP is visible to websites, enhancing your anonymity.
VPNs and HTTPS
Despite HTTPS providing encryption from your browser to a website, VPNs offer additional security layers and can bypass some HTTPS vulnerabilities. They make certain attacks, like SSL stripping, much harder, ensuring safer online experiences.
VPN Protocols Overview
Common VPN Protocols
There are a number of VPN protocols available, such as PPTP, L2TP, IPSec, OpenVPN, SSTP, and IKEv2. These are the most common ones, with others like OpenConnect and SoftEther using SSL and TLS.
PPTP (Point-to-Point Tunneling Protocol)
- Not Recommended: Has major security flaws and is vulnerable to certain attacks.
- Easy Setup: Available in Windows OS but easily decrypted by advanced adversaries like NSA.
- Limited Use: Should only be used if no other options are available besides plain text.
L2TP/IPSec
- Combination Use: L2TP is paired with IPSec for encryption as L2TP alone doesn’t encrypt.
- Supported Platforms: Natively supported on Windows, Mac, Linux, iOS, and Android.
- Drawbacks: Relies on fixed ports making it inflexible and easily blocked by firewalls.
- Security Concerns: Not recommended against nation-state adversaries due to potential vulnerabilities.
OpenVPN
- Open Source Project: Uses OpenSSL library and configurable protocols and ports.
- Advantages: Can mimic HTTPS traffic by using TCP port 443, making it hard to detect.
- Encryption Options: Supports AES and Blowfish among others; AES-256 is recommended.
- Installation & Use: Requires third-party software; setup can be complex for non-technical users.
- Security: No known major compromises if using strong algorithms.
SSTP (Secure Socket Tunneling Protocol)
- Microsoft-Owned: Proprietary to Windows and not widely supported by VPN providers.
- Security Concerns: Closed source and not preferred due to Microsoft’s cooperation history with NSA.
IKEv2
- Mobile-Friendly: Offers fast and secure reconnections on mobile platforms.
- Viable Option: Good for mobile devices needing quick reconnections.
Conclusion on VPN Choices
- Preferred Choice: OpenVPN whenever possible.
- Mobile Option: IKEv2 is suitable for mobile devices.
- Fallback Options: L2TP/IPSec if nation-state-level security isn’t a concern, and PPTP as a last resort.
VPN Weaknesses and Limitations
Speed and Latency Issues
- Slower Connections: VPNs add an extra layer of encryption and an additional hop, slowing down your connection compared to using your ISP directly.
- International VPNs: Using a VPN server outside your country can worsen speed and latency, though good ISPs and VPN providers offer acceptable performance.
Suitability Against Advanced Adversaries
- Nation-State Adversaries: VPNs alone are not suitable for hiding identity from determined nation-state actors. Combining VPNs with tools like Tor might offer better protection.
- Public Wi-Fi as an Alternative: In some cases, using public Wi-Fi can be a less convenient but viable alternative to maintain anonymity.
Censorship and Geographic Restrictions
- Evading Censorship: VPNs can bypass restrictions, but consequences should be minor if detected. Some countries use Deep Packet Inspection to detect and block VPNs.
- Alternative Solutions: Services like Unlocator and SmartVPN Proxy can bypass restrictions faster by acting as intermediaries but require trust as they can see your traffic.
Detection and Obfuscation
- VPN Detection Risks: Observers can detect VPN usage, which may lead to targeted surveillance. Tools like S-Tunnel or OBS Proxy can help evade detection.
Subscription and Payment Concerns
- Cost Implications: Quality VPNs charge around $10 to $15 monthly. Free options are slower and less secure.
- Payment Traceability: Payments for VPN services can often be traced back unless done anonymously via methods like Bitcoin.
Traffic Confirmation Attacks
- Low Latency Vulnerability: VPNs are susceptible to traffic confirmation attacks, where adversaries correlate entry and exit points to track users.
- Multiple Hop Routes: Some VPNs offer multi-hop routes across nations to enhance anonymity.
Lack of Client Protection
- No Client Protection: VPNs do not protect against attacks targeting client systems, such as malware or phishing.
- Browser Security: VPNs don’t provide secure browsers; users should harden browsers against tracking and exploitation.
Web Traffic Fingerprinting
- Pattern Recognition: Despite encryption, adversaries can guess visited web pages by analyzing traffic patterns.
- Research Findings: Studies show high accuracy in identifying webpages through VPN traffic analysis.
Other Limitations
- Usage Signals Privacy Needs: Sporadic VPN use can signal attempts to hide activities, drawing attention.
- Service Restrictions: VPN providers may block services like SMTP to prevent spam, causing inconvenience.
- Account Security Risks: VPN usage may trigger security alerts from services, risking account suspension.
Privacy vs. Anonymity
- Not Full Anonymity: VPNs primarily protect privacy but often retain logs and payment details. Anonymity requires more layers, like nested VPNs or combining with other services.
VPNs are useful tools for privacy but have limitations, especially against powerful adversaries or in scenarios requiring complete anonymity. Understanding these weaknesses helps in deciding when and how to use VPNs effectively.
Trust and Security Practices of VPN Providers
Understanding VPN Trust
- Trust Analogy: VPNs are like dogs; even if you choose the right breed (provider), they might still “bite” or betray your trust.
- IP Address Exposure: Connecting to a VPN exposes your real IP address to the VPN server, making it traceable back to you.
- Man-in-the-Middle Potential: A VPN by design can perform man-in-the-middle attacks if they choose or are coerced.
Mitigating Trust Issues
- Choosing Providers: Opt for a VPN provider you trust more than your ISP, as it’s easier to change VPN providers and locations.
- Court Orders and Warrant Canaries: Even with a trusted provider, court orders can force them to disclose information. Warrant canaries are attempts to inform users of such events, but their effectiveness is debated.
Legal and Jurisdictional Considerations
- US and EU Differences: US has no mandatory data retention laws, unlike the EU. Research specific country compliance for data privacy.
- NSA and International Influence: VPNs in jurisdictions like the US may still be targets for national surveillance programs.
Real-World Examples and Risks
- LavaBit Example: Highlighted refusal to comply with secret surveillance demands, showing potential risks.
- Provider Reliability: Instances of providers cooperating with law enforcement, despite privacy claims.
- Avoiding 5/14 Eyes Countries: Consider avoiding VPN providers based in countries within the 5/14 Eyes alliances due to potential cooperation with surveillance.
Strategic Use of VPNs
- Distributed Trust: Use nested VPNs and combine with other services (like Tor) to enhance privacy and distribute trust.
- Purpose of VPNs: Useful for protection on public Wi-Fi, against ISP monitoring, but limited against powerful adversaries.
Proxy.sh VPN Provider Sniffed Server Traffic to Catch Hacker * TorrentFreak
Choosing a VPN involves understanding their security practices and trustworthiness, especially in relation to powerful adversaries and legal jurisdictions. Always consider distributing trust and enhancing privacy through additional methods.
DNS Security and Privacy Concerns
What is DNS?
- DNS Basics: DNS (Domain Name System) resolves domain names (like wikipedia.org) into IP addresses that computers use to connect to websites.
- DNS Process: Your computer first checks locally for the IP address, then sends a DNS request to an external server if needed.
DNS and VPNs
- Concerns with DNS: Without a VPN, DNS queries can be monitored by ISPs, governments, or others, as they are sent in plain text.
- Using VPNs: A VPN encrypts DNS queries, preventing them from being seen by anyone monitoring your traffic.
Transparent DNS Proxies
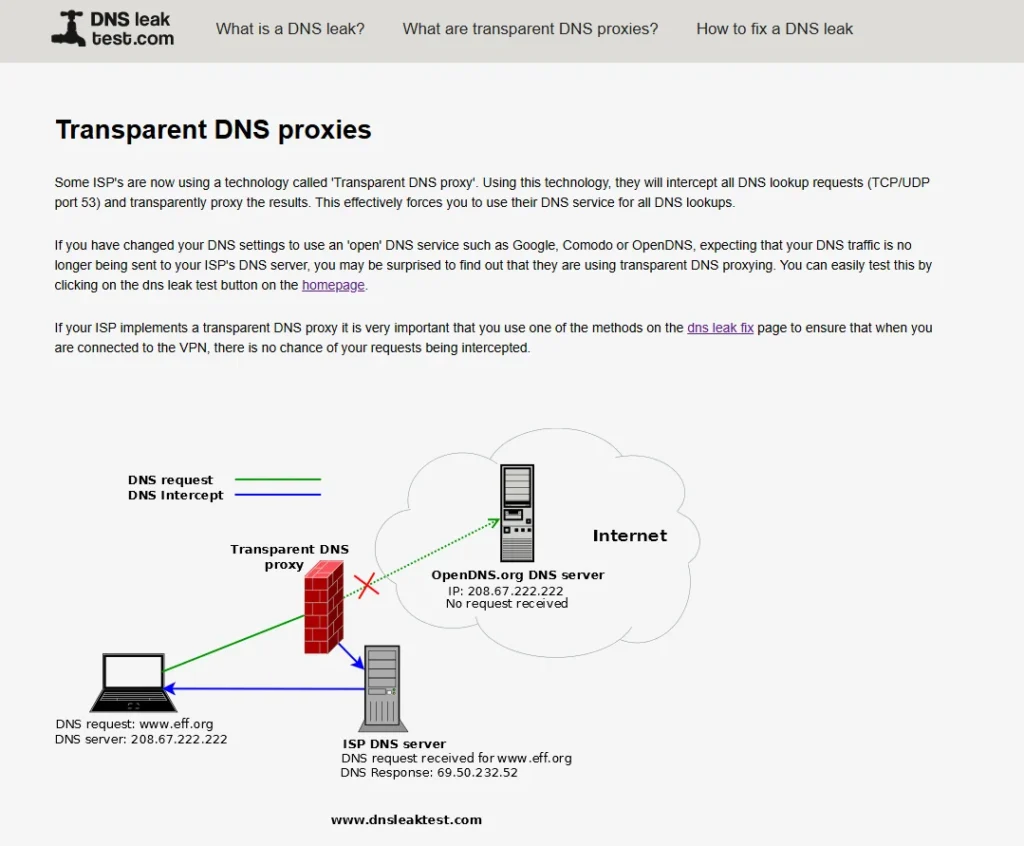
- ISP Interference: Some ISPs redirect DNS queries through proxies, overriding your chosen DNS server.
- Testing for Proxies: Change your DNS settings and use websites that display your DNS server to check if your ISP is using a transparent proxy.
DNS Poisoning and Spoofing
- What is DNS Poisoning: Manipulating DNS to redirect users to incorrect IP addresses, often used for censorship or malicious purposes.
- Historical Example: Turkey used DNS poisoning to block YouTube and Twitter in 2014.
Mitigating DNS Risks
- Using a VPN: Encrypt DNS queries and send them through a VPN to avoid monitoring and bypass DNS poisoning.
- DNS Crypt: A protocol that authenticates DNS communication, preventing spoofing by verifying responses from DNS resolvers.
Additional Considerations
- DNS Encryption Pitfalls: Even with DNS encryption methods like DNSCrypt or DNSSEC, there can still be privacy pitfalls.
- Further Reading: Reports like “Pretty Bad Privacy: Pitfalls of DNS Encryption” provide more insights into DNS security.
IP/DNS Detect – What is your IP, what is your DNS, what informations you send to websites.
Understanding DNS security is crucial for maintaining privacy online. VPNs and DNS encryption tools can help mitigate the risks, but users should be aware of the limitations and continue educating themselves on this topic.
Setting Up OpenVPN on Various Devices
General Setup for OpenVPN
- OpenVPN Client: When you subscribe to a VPN provider, they usually offer their own OpenVPN client with features like kill switches and leak protection.
- Configuration Files: If you don’t use the provider’s software or set up your own VPN server, you’ll need an OpenVPN client for your operating system, along with configuration files (ovpn files) provided by your VPN provider.
Windows Setup
- Download OpenVPN: Go to the OpenVPN website and download the appropriate client for Windows (32 or 64-bit).
- Install and Configure: Install the software and place the downloaded ovpn configuration files in the OpenVPN config directory.
- Connect: Run OpenVPN as an administrator, select the configuration file, and connect.
Mac OS X Setup
- Download TunnelBlick: Get the TunnelBlick client from its website and install the stable version.
- Configuration Files: Obtain the ovpn files from your provider.
- Install and Connect: Open TunnelBlick, import your configuration files, and connect to your VPN.
iPhone Setup
- Download OpenVPN App: From the App Store, download the official OpenVPN Connect app.
- Transfer Config Files: Use methods like Dropbox, email, AirDrop, or iTunes to transfer the ovpn files to your iPhone.
- Connect: Open the configuration file in OpenVPN Connect and connect using your credentials.
Android Setup
- Download OpenVPN App: Get the app from the Google Play Store.
- Transfer Config Files: Either download directly to your device or transfer from a PC using USB, SD card, or cloud services like Dropbox.
- Import and Connect: Use the app to import the configuration file and connect.
What If No Config File Provided?
- Provider Limitation: If your VPN provider doesn’t provide configuration files, they might require you to use their custom software.
- Own Server: For those setting up their own server, additional resources are available for creating your own client configuration files.
Setting up OpenVPN requires downloading the client app, obtaining configuration files, and using them to connect. Each OS has specific steps, but the process is largely similar across platforms.
Setting Up OpenVPN on Linux (Debian/Ubuntu)
General Overview
- VPN Client: Most VPN providers offer a client for Windows, Mac, Android, and iPhone, but not always for Linux.
- Configuration Files: You’ll typically receive
.ovpnfiles from your VPN provider, which are crucial for setup.
Installing OpenVPN
- Install OpenVPN Package:
- Open a terminal and run the command:
sudo apt-get install openvpn - This installs the main OpenVPN package and command-line tools.
- Open a terminal and run the command:
- Install Network Manager Plugin (GNOME Desktop):
- For a graphical interface, install the OpenVPN plugin for Network Manager:
sudo apt-get install network-manager-openvpn-gnome - This allows you to manage VPN connections via the GUI.
- For a graphical interface, install the OpenVPN plugin for Network Manager:
Configuring OpenVPN
- Access VPN Settings:
- Open Network settings, find the VPN section, and choose to add a new VPN connection.
- Select “Import from file” and locate your
.ovpnfile.
- Importing Configuration:
- The
.ovpnfile typically contains paths to additional files such as CA certificates, client certificates, and keys. - If these are not automatically populated, manually select them based on your provider’s instructions.
- The
- Enter Credentials:
- Provide your VPN username and password as required.
- Connecting:
- Once configured, select the VPN from your network options and connect.
Troubleshooting
- Logs and Syslog:
- View logs in
/var/log/syslogby usinggrep openvpnfor troubleshooting. - Ensure you’re running commands with
sudofor elevated permissions.
- View logs in
Important Considerations
- Disconnects and Leaks:
- OpenVPN might occasionally disconnect, which could cause data leaks; later videos will cover leak prevention strategies.
- Check Provider’s Documentation:
- Always refer to your VPN provider’s documentation for specific instructions tailored to Linux.
Setting up OpenVPN on Linux involves installing the necessary packages, configuring with the provided .ovpn files, and managing connections through your network settings. Always ensure your setup aligns with your provider’s guidelines for optimal security.
Preventing DNS and IPv6 Leaks in VPNs
Understanding the Issue
- DNS Leaks: Occur when DNS queries are sent outside the VPN tunnel, often to your ISP, revealing the websites you visit.
- IPv6 Leaks: IPv6 traffic can leak out of the VPN, revealing your identity even if IPv4 is secure.
- VPN Drop Leaks: When a VPN connection drops, the system may default to using the regular internet connection, exposing your data.
Preventive Measures
- Disable IPv6:
- Most systems don’t use IPv6 heavily, so disabling it can prevent leaks.
- Instructions vary by OS, but it’s generally a straightforward process.
- Use a VPN with Built-in Leak Protection:
- Look for VPN clients with built-in DNS and IPv6 leak protection, and a kill switch that blocks all traffic if the VPN disconnects.
- Implement Firewalls:
- Use host-based firewalls to block non-VPN traffic.
- On Windows, use the Windows Firewall or third-party options like TinyWall or Comodo.
- Testing for Leaks:
- Regularly test your VPN for leaks using online tools.
- Use network analyzers like Wireshark for a deeper inspection.
Platform-Specific Tips
- Windows:
- Use Windows Firewall to block non-VPN traffic.
- Consider TinyWall or Comodo for more control.
- Be cautious with Windows 10 as it may have more DNS leak issues.
- Mac:
- Use PF firewall with tools like IceFloor or Murus for GUI management.
- Little Snitch is another valuable tool for monitoring connections.
- Linux:
- Use IPTables to block non-VPN traffic.
- Consider VPN Fireball to stop traffic when the VPN goes down.
GitHub – adrelanos/vpn-firewall: Leak Protection (Fail Safe Mechanism) for (Open)VPN
Win – Mac – BSD Block traffic when VPN disconnects – How-To – AirVPN
GitHub – ValdikSS/openvpn-fix-dns-leak-plugin: OpenVPN plugin to fix Windows DNS Leaks
What is a DNS Leak? | What to know about DNS Leaks & how to fix them
How to Build A VPN Kill Switch On Windows Using Comodo
VPNCheck Free Edition | Guavi.com
For optimal privacy, ensure your VPN client is configured to prevent leaks. Supplement this with firewalls and regular leak testing to maintain a secure connection. These steps will help keep your online activities private and secure.
How to Choose a VPN Provider
Understanding Your Needs
- Identify the Threats: Consider if you’re guarding against censorship, passive surveillance, targeted attacks, hackers, hiding your IP, ISP monitoring, privacy concerns, anonymity, or a combination of these.
- Required Features: Your needs will determine the features necessary, such as obfuscation, fast and local servers, security settings, and payment privacy.
Evaluating VPN Providers
- Ignore Fake Reviews:
- Be wary of online reviews that may be biased due to affiliate marketing.
- Trustworthy reviews are rare, so base your decision on research and technical specifications.
- Trust Model:
- Adopt a zero trust model. Research VPNs thoroughly and verify their claims.
- Prioritize providers outside jurisdictions known for data retention, like the USA, EU, or other “Five Eyes” countries.
- Key Considerations:
- No Logging: Choose providers that don’t log IP addresses or user activity.
- OpenVPN Support: Ensure they offer secure encryption and OpenVPN protocol.
- Anonymous Payment: Opt for providers accepting Bitcoin or anonymous payments without personal information requirements.
- Device Support: Confirm support for the number of devices you plan to use.
- Client Software: Look for features like DNS and IPv6 leak protection, and a kill switch.
- Technical Infrastructure:
- Prefer providers with their own DNS service and physical control over their servers.
- Avoid shared virtual private servers for enhanced security.
- Service and Security:
- Read terms of service and privacy policies for clarity and user-friendliness.
- Ensure VPN gateways are secure, with no other services running on them.
Recommended Providers
- AirVPN: Based in Italy, known for security features like SSH and SSL tunneling.
- IVPN: Offers multi-hop VPN, located in Gibraltar.
- Mullvad: Based in Sweden, known for strong privacy laws.
- NordVPN: Based in Panama, politically strong location.
Additional Resources
- Research: Use subreddits like /r/VPN for community insights.
- Comparison Charts: Check PrivacyGuide’s VPN comparison for detailed provider specs.
HMA VPN user arrested after IP handed over to the FBI – Hacker 10 – Security Hacker
10 Best VPN Services 2024: Security, Features + Speed
Which VPN Providers Take Privacy Seriously
Choose a VPN based on your specific needs and security requirements. Research thoroughly, prioritize privacy features, and verify provider claims to ensure your online activities remain private and secure.
Setting Up Your Own VPN Server
Why Set Up a VPN Server?
- Control and Customization: You can disable logging and configure settings to your liking.
- Potential Drawbacks: There could still be a money trail, and technical competency is required.
Setting Up an OpenVPN Server
- Understanding the Setup:
- Setting up a secure OpenVPN server from scratch is complex and requires attention to detail.
- Mistakes can lead to vulnerabilities, but there are simplified methods to get started.
- Methods for Setting Up:
- Using Turnkey Linux:
- Offers a ready-made virtual OpenVPN appliance based on Debian 8 (Jessie).
- Appliances are free and open source, suitable for learning and practical use.
- You can download VM images or install an ISO.
- Cloud Deployment:
- Deploy your server on Amazon Web Services (AWS) for a small cost.
- Requires creating accounts on AWS and Turnkey Linux and following integration instructions.
- Using Turnkey Linux:
- Step-by-Step Guide:
- Choose Your Appliance: Download and deploy the OpenVPN appliance from Turnkey Linux.
- Select Server Type: For AWS, choose server location and type (e.g., micro version for cost efficiency).
- Configure Security: Set SSH passwords or key pairs, and configure firewall rules for added security.
- Testing and Customization:
- Launch the server and check its status.
- Customize firewall rules, limit open ports to necessary ones (e.g., OpenVPN port 1194).
- Creating a Client Configuration:
- Use OpenVPN commands to create client configurations.
- Transfer the .ovpn file to your client device for access.
I Am Anonymous When I Use a VPN – 10 Myths Debunked | VyprVPN
PIVPN: Simplest way to setup a VPN
Setting up your own VPN server provides control over your privacy, but requires technical skill and attention to detail. By utilizing services like Turnkey Linux and AWS, you can simplify the process and ensure a secure setup.
Setting Up a VPN Client on Debian with OpenVPN
Overview
- Environment: Debian system for running the VPN client, similar steps apply for Kali Linux.
- Goal: Download and configure the OpenVPN client using an OVPN file from the server.
Steps to Set Up the VPN Client
- Download the OVPN File:
- Use SCP (secure copy protocol) to download the
.ovpnfile from the server. - Example command:
scp root@server:/path/to/file.ovpn /local/path/demo/.
- Use SCP (secure copy protocol) to download the
- Examine the OVPN File:
- The file includes server URL, port, CA certificate, TLS auth key, client certificate, and private key.
- Important components include the CA (Certificate Authority), public and private keys.
- Importing OVPN File:
- Navigate to network settings, add a new VPN, and import the
.ovpnfile. - On Debian, the import might miss user cert, CA cert, private key, and TA key.
- Navigate to network settings, add a new VPN, and import the
- Separate Certificates and Keys:
- Use a
sedcommand to extract these components into individual files. - Example
sedcommand:sed -n '/<ca>/,/<\\\\/ca>/p' file.ovpn > ca.crt.
- Use a
- Configure VPN in Network Settings:
- Manually select the user certificate, CA certificate, private key, and authentication key.
- For TLS authentication, set the direction to
1.
- Connect to the VPN:
- After configuration, attempt to connect.
- Verify the connection by checking your IP address to ensure it’s routing through the VPN.
Troubleshooting and Tips
- Ports and Protocols: Default port is
1194. For more ports like TCP443, start a new OpenVPN instance. - Resource Management: Shut down the server when not in use to save costs.
- Long-Term Use: Consider paying upfront for a server if used regularly to reduce costs.
Setting up a personal OpenVPN server gives you control and the flexibility to manage your connections. Ensure you configure the server securely and verify settings to maintain privacy.
Connecting to Your Home Network with VPN
Options for Setting Up a VPN Server
- Using TurnKey on Internal Devices:
- Install TurnKey on a device or a virtual machine within your home network.
- This can be an effective way to set up a VPN server for secure remote access.
- Raspberry Pi Setup:
- If you have a Raspberry Pi, you can install an OpenVPN Server on it.
- Recommended OS: Use Debian Lite for Raspberry Pi for a lighter and efficient setup.
- If you don’t have a Raspberry Pi, the same script can be run on Debian Jessie.
- Home Router with Custom Firmware:
- Use a router with custom firmware like DD-WRT, which has a GUI for easy setup.
- Enable OpenVPN server, configure it on port 443, and choose encryption ciphers.
- You’ll need to input certificates and keys manually.
- Use PFSense:
- PFSense provides a robust OpenVPN server solution.
- It’s a good option for inbound connections to your home network.
- NAS Devices:
- Some NAS storage arrays and devices come with built-in VPN server capabilities.
- For better security, using DD-WRT or PFSense is recommended.
Configuration Tips
- Port Forwarding/DMZ:
- Ensure your network is set up to forward the necessary ports or set up a DMZ if the VPN server is internal.
- This involves configuring your router to point to the correct IP address.
These methods offer flexible and secure ways to set up an OpenVPN server for remote access to your home network. Choose the one that best fits your technical comfort level and device availability.
Conclusion
This article provides a comprehensive introduction to the use of VPNs, including a comparison of different anonymization services, how VPNs work, client setup options, an overview of VPN protocols, the limitations and weaknesses of VPNs, and how to choose the right VPN provider.
The article also discusses DNS security, how to set up OpenVPN on different devices, ways to prevent DNS and IPv6 leaks, and how to build a VPN server on your own. Finally, VPN setup options for connecting to your home network are provided.
Failure to successfully resolve the provided link due to network reasons may be a link issue or a network problem, so it is recommended to check the legitimacy of the link and retry appropriately.


