Table of Contents
This article will provide you with a comprehensive understanding of online tracking and profiling, allowing you to take effective measures to protect your privacy based on this knowledge and your own situation.
Key Tracking Techniques
- Cookies:
- Small pieces of data stored on your device by websites to remember your preferences and track your activities.
- Super Cookies:
- More persistent cookies that are harder to detect and remove, often used to track users across different browsing sessions.
- HTTP eTags:
- A browser feature that allows websites to determine whether the content they are serving has changed. These can also be used to track users.
- Web Cache:
- Temporary storage of web pages and content that can be used to track user behavior by analyzing accessed content.
Tracking Methods
We’re going to break down how tracking works online. After this, we’ll discuss ways to protect yourself from these tracking methods.
How Tracking Occurs
- Website Tracking:
- When you log into a site, your actions are typically logged. Even if you don’t log in, websites you visit still monitor your activities.
- Third-Party Tracking:
- If you encounter third-party elements, like a Facebook “like” button on a webpage, those external sites can track you.
- Ad Networks:
- Companies like Yahoo and Google track you based on the ads you see from them or their affiliates.
- Email Providers:
- Your email service provider knows who you message and can access your emails, allowing them to track your online behavior when those sites reference back to them.
- Internet Service Providers (ISPs):
- ISPs log the websites you visit and your DNS queries, which translates domain names to IP addresses. This information can be held for up to a year.
- Mobile Network Providers:
- Similar to ISPs, they log your internet activity, along with your location data.
- Government and Law Enforcement:
- These agencies can monitor parts of the internet and track specific individuals if they are under scrutiny.
- Educational Institutions and Employers:
- Schools and workplaces can log your web activity and may have tools to monitor the actual content, especially if they control the devices you use.
Risks of Shared Networks
When using public or shared Wi-Fi:
- Assume that the Wi-Fi provider logs the sites you visit, possibly including the content accessed.
- If you own the device, it’s harder for them to monitor encrypted traffic, but not impossible.
Man-in-the-Middle Attacks
Anyone who places themselves between you and the websites you visit can potentially monitor you, which is known as a man-in-the-middle attack. While encryption helps, it’s not foolproof.
Local Monitoring Risks
- If someone has physical access to your machine or is on your local network, they can monitor your activities through various tools.
Ways to Protect Yourself
Encrypting your traffic is a strong barrier against tracking, but it isn’t completely impenetrable. There are ways to bypass encryption that we’ll cover in future sections.
Understanding Your IP Address and Its Role in Online Tracking
Let’s dive into how your IP address is used to identify you online and the implications of this for your privacy.
The Basics of IP Address Identification
- IP Address as an Identifier:
- The most straightforward way to identify you online is through your IP address. Any internet connection you make requires your IP address to enable responses to your requests.
- TCP/IP Protocol:
- The nature of the TCP/IP protocol, which supports the internet, means that privacy and security aren’t inherently built into the system. This creates challenges in ensuring online privacy.
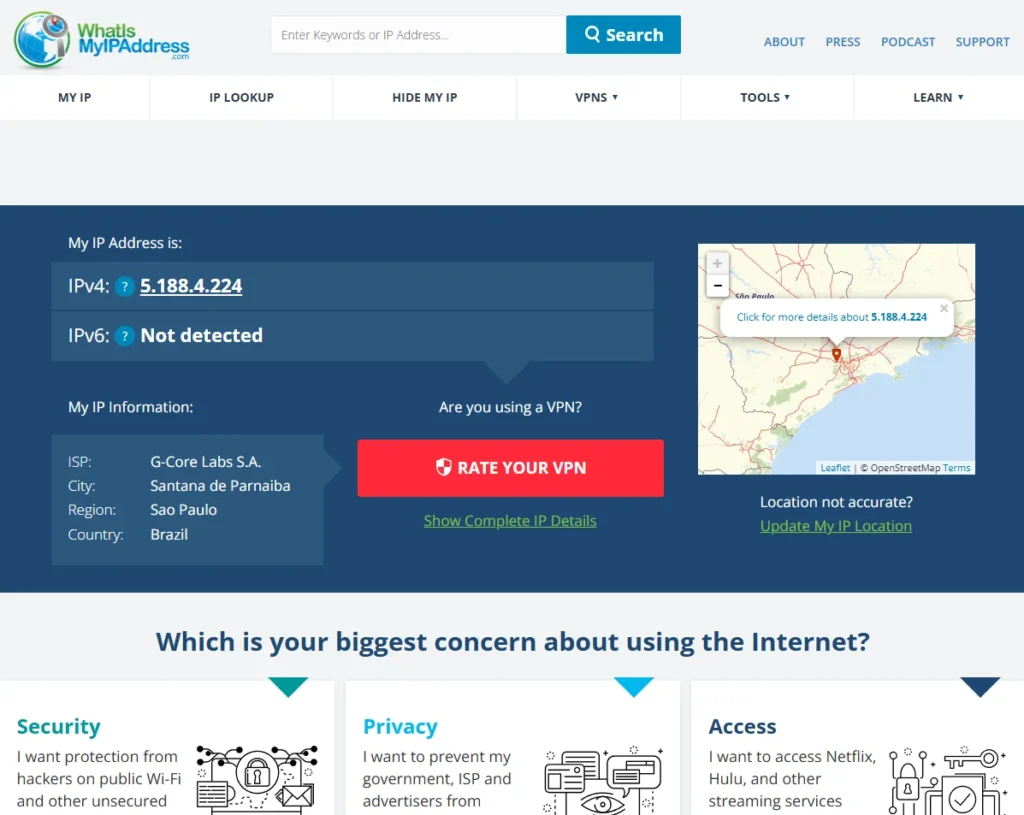
- Geographic Location:
- By visiting sites like whatismyipaddress.com, you can find out that your IP address allows others to estimate your general geographic location (not exactly to the street, but typically to your city).
- Ad Targeting:
- Advertisements often use your IP address to tailor their content to you based on your location. This is done through databases that link IP addresses to specific geographical areas.
Understanding Your IP Address Dynamics
- Shared IP Address:
- Your computer often shares the same IP address with other devices in your home or office. This IP address is assigned to your router, which is directly connected to the internet.
- Dynamic IP Addresses:
- Your IP address changes dynamically when you connect to the internet. It remains associated with you for a limited period until the ISP assigns it to someone else.
- Local vs. External IP Addresses:
- Your router has an external IP address that the internet sees, while your local devices have internal IP addresses (often beginning with 192.168.x.x). You can check your local IP by typing
ipconfigin the command prompt.
- Your router has an external IP address that the internet sees, while your local devices have internal IP addresses (often beginning with 192.168.x.x). You can check your local IP by typing
Analyzing IP Addresses
- Identifying IP Addresses:
- You can easily find the IP address of a website you visit. For example, using the command
ping www.offsce.comshows you the site’s IP address.
- You can easily find the IP address of a website you visit. For example, using the command
- Monitoring Traffic:
- Tools like Wireshark can help analyze network traffic. By setting up filters, you can track the IP address associated with specific domains and see the full conversation over HTTP.
Network Address Translation (NAT)
- Connection Process:
- When you connect to the internet, the connection goes through your router using Network Address Translation (NAT). This adds a layer of protection by hiding your internal IP addresses from the outside world.
Web Connections and Proxies
In this section, we’re going to talk about what happens when you connect to a website, using a proxy to observe the traffic and understand the complexities involved.
Connecting to a Website
- Using a Proxy:
- To illustrate the connection process, I’m using a proxy tool called Burp Suite, commonly used by penetration testers for ethical hacking. This proxy sits between my browser and the website, allowing me to see all incoming and outgoing traffic.
- Sending Requests:
- When I navigate to www.forbes.com, the proxy captures the request my browser is sending. This request includes information like the method used to access the site and any cookies that the site has previously set.
- Cookies Explanation:
- Cookies are small pieces of data stored on your computer that websites use to remember information about your visits. Since I’ve visited Forbes before, my browser sends back the cookies it received earlier.
Observing the Traffic
- Forwarding Requests:
- After capturing the initial request, I can forward it to the Forbes website. As I move through the process, I notice that it’s not just connecting to Forbes; it’s connecting to many other domains.
- Multiple Domain Connections:
- Websites often connect to numerous other domains for additional resources. This includes images, ads, and scripts. For example, the request might involve connecting to a domain for images, and then others for analytics and ads.
- Impact of Multiple Connections:
- Each time you visit a website, you may unknowingly interact with many other sites. This increases your exposure to ad networks and tracking services.
Analyzing Code and Third-Party Connections
- Inspecting JavaScript:
- By using tools like Firebug, I can inspect the website’s code to find calls to third-party services like Google Analytics. These services collect data about users and their interactions on the site.
- The Chain of Connections:
- When navigating from a primary site to a third-party site, you may find that the third party connects to yet another site for additional resources. This chain can continue to a fourth or even fifth party.
HTTP Referrer and Tracking Methods
I will explore how tracking works through the HTTP referrer and other tracking methods commonly used online.
What is the HTTP Referrer?
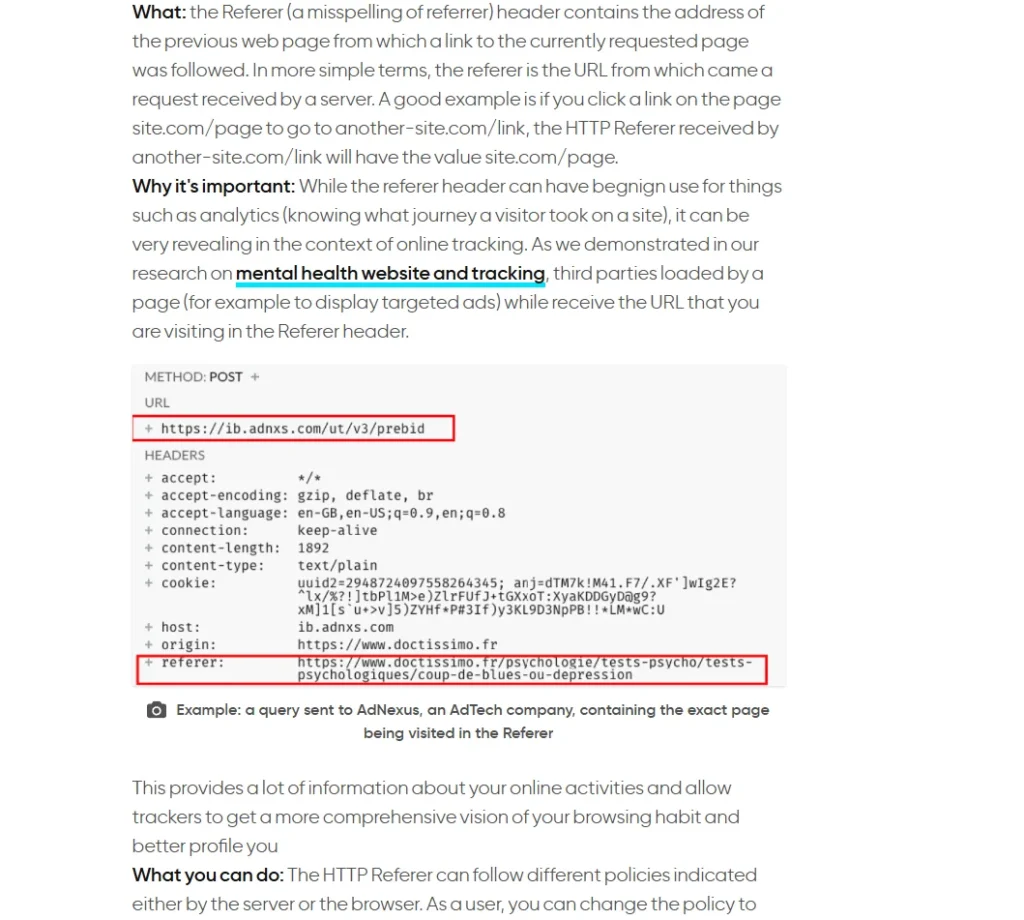
- Definition:
- The HTTP referrer is a part of the HTTP header that informs a web page about the previous page from which a user has navigated. When you click a link, your browser sends this information along with the request to the new page.
- Example:
- For instance, if I click a link from Google to another site, that site will know I came from Google. This can be observed in the browser’s address bar or by using tools that monitor traffic, like a proxy.
- Proxy Demonstration:
- By disabling my proxy, I can directly check what the referrer is. In this case, the page might reveal that I came from google.co.uk.
Tracking Through Referrer Data
- Referrer in Action:
- When visiting a site like Forbes, the HTTP referrer indicates that traffic is coming from Forbes when it redirects to an ad site like offsce.com. The request sent to wikinvest includes the referrer information.
- Multiple Referrers:
- It’s essential to note that navigating from one site can lead to multiple referrer instances. For example, moving from Forbes to WikiInvest might also send referrer data to Google Analytics.
- Usage in Tracking:
- The HTTP referrer is essential for tracking because it helps advertisers and analytics services understand where traffic is coming from whenever content is loaded on a webpage from a third-party source.
Additional Tracking Methods
- Conversion Pixels:
- These are tiny one-pixel images, often invisible, that use HTTP referrer data to track users. They don’t appear on the website but are loaded in the background to gather data.
- Email Tracking:
- HTTP referrers are also utilized in email tracking. When you open an email in services like Gmail or Hotmail, if images are automatically processed, they may include tracking pixels that send referrer data back to the sender, indicating that the email was opened.
Cookies and Tracking Scripts
Cookies are integral to the web experience but also raise privacy and security concerns. Understanding their function and how they are used for tracking can empower you to make better choices about your online activity.
What are Cookies?
- Definition:
- Cookies are small pieces of information sent from websites to your browser, which stores them. The browser sends these cookies back to the website with every request, allowing the site to recognize you as the same user.
- Demonstration:
- For example, when visiting the BBC website, I can use a tool like Firebug to view all the cookies being sent. Each cookie has a name and a corresponding value.
The Role of Cookies
- Legitimate Uses:
- Cookies have many legitimate purposes, such as maintaining your login state on a site so you don’t have to log in every time you refresh or navigate to a new page.
- They also store user settings, ensuring that preferences persist across different pages.
- Session Cookies:
- A session cookie allows the website to track your activity during a particular visit. Even as a guest on the BBC, I receive a session cookie to track what I’m doing.
Types of Cookies
- First-Party vs. Third-Party Cookies:
- First-party cookies are set by the website you are visiting (e.g., BBC).
- Third-party cookies come from other sources, often related to advertisements or tracking scripts present on the site.
- Tracking Across Sites:
- If multiple sites use the same advertising network, like DoubleClick, your browsing history can be linked across those sites, allowing these networks to track where you go.
Tracking Scripts
- Social Media and Advertising:
- Scripts from social media platforms, like Facebook, can also track your visits. For instance, if you’re logged into Facebook and visit a site with a Facebook like button, Facebook records your visit.
- Google and Data Collection:
- Google Analytics scripts are commonly found on many websites. They track user activity linked to your Google account, providing Google valuable insights into your browsing habits.
Security Concerns with Cookies
- Session Hijacking:
- Cookies can be exploited if they are not generated securely. Weak or predictable cookies can allow an attacker to steal a session and impersonate a user.
- Importance of HTTPS:
- It’s crucial for cookies to be sent over secure HTTPS connections to prevent interception. Encryption helps protect cookies from being accessed or manipulated by attackers.
Managing Cookies
- Viewing Your Cookies:
- You can use tools like Cookie-Editor (a Firefox add-on) to view and manage the cookies stored in your browser. This can help you understand what data is being collected.
- Familiarizing with Cookies:
- Exploring your cookies can provide insights into the tracking mechanisms that websites use and help you make informed decisions about your online privacy.
Super Cookies and Tracking Methods
Super cookies represent a significant challenge to user privacy by facilitating persistent tracking across the internet. Understanding their workings and implementing measures to protect your online activity are vital in this digital age.
What are Super Cookies?
- Definition:
- Super cookies are a general term for methods designed to permanently track users by placing data in the browser in ways that are harder to detect and remove than regular cookies.
- Example:
- A well-known example is EverCookie, which employs various techniques to avoid detection and removal.
Methods of Implementing Super Cookies
- Different Techniques:
- Super cookies can use flash cookies (local shared objects), Silverlight isolated storage, and can even store data in RGB values of generated images or use HTML5 canvas elements to read pixels.
- Color Value Tracking:
- By assigning unique color values to pixels, super cookies can create a unique identifier for users, making it challenging to delete them since clearing cookies alone doesn’t remove these identifiers.
- Storage Locations:
- Super cookies can be stored in various locations such as web history, HTTP eTags, web cache, and even within the user’s local storage through HTML5.
Resilience of Super Cookies
- Zombie Cookies:
- Cookies that are recreated after deletion from backups outside the browser’s dedicated cookie store are referred to as zombie cookies. They can repopulate even after attempts to erase them.
- Telco Super Cookies:
- Telecommunication companies (telcos) can inject super cookies into HTTP requests. As users browse the internet, these cookies are added to the HTTP headers, allowing the telco to track users across different websites without their knowledge.
Privacy Implications
- Tracking Across the Internet:
- Super cookies allow ad networks and media publishers to follow users online, enabling them to build detailed profiles based on browsing habits, even if users clear their regular cookies.
- Ad Targeting:
- This tracking capability allows networks to serve targeted advertisements, with telcos often taking a cut from the profits made through targeted advertising.
- Mitigating Tracking Risks:
- To combat this tracking, limiting web browsing to HTTPS-only sites can help, as HTTPS encrypts data making it more difficult for telcos to inject tracking data.
Recommendations
- Using HTTPS:
- Browsing over HTTPS ensures that data remains encrypted, making it difficult for telcos or ISPs to inject super cookies into your requests.
- Switching Providers:
- If feasible, consider switching to a telco or ISP that does not engage in this intrusive tracking technology.
- Awareness and Tools:
- Staying informed about tracking techniques and using privacy tools can help you maintain control over your online presence.
Browser Fingerprinting and Information Leakage
Understanding browser fingerprinting and the information your browser shares is crucial for maintaining your privacy online. By taking steps to reduce the uniqueness of your browser, you can help protect yourself from being tracked.
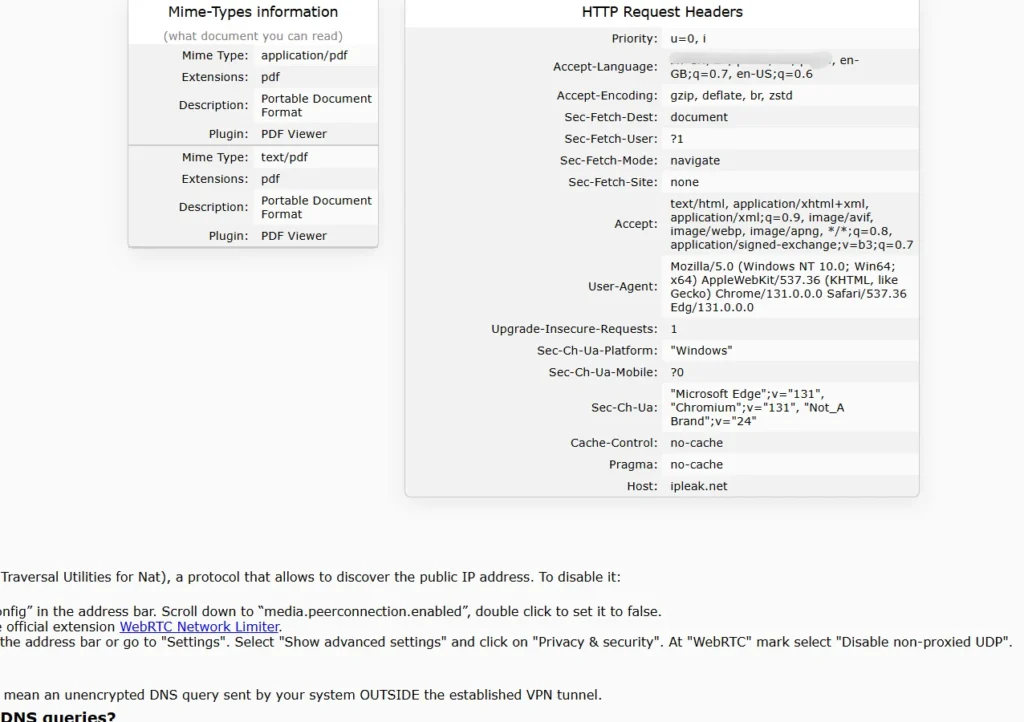
IP/DNS Detect – What is your IP, what is your DNS, what informations you send to websites.
What is Browser Fingerprinting?
- Definition:
- Browser fingerprinting is a technique that collects information about your browser’s configuration and settings, such as user agents, installed fonts, browser types, and add-ons. This data can create a unique identifier for users.
- Volunteered Information:
- When you visit a webpage, your browser voluntarily sends this information, and if the combination is unique enough, it can be used to identify and track you online.
- Irony of Security Plugins:
- Ironically, some plugins designed for security can make your browser more unique, inadvertently increasing the chances of being fingerprinted.
Tools for Testing Fingerprinting
- Panopticlick:
- The Electronic Frontier Foundation (EFF) created a tool called Panopticlick to help users test how unique their browser fingerprint is.
- By running a test, users can see if their fingerprint is unique among millions of testers and how much identifying information it conveys.
Reducing Your Fingerprint
- Be Less Unique:
- To avoid being fingerprinted, the key is to make your browser appear less unique. This can involve using more default settings and configurations to blend in with the average user.
- Testing Other Information:
- Besides testing fingerprint uniqueness, you can also check what information your browser is leaking via the website ipleak.net. This site shows details like your IP address, DNS information, general location, and more.
Information Leakage Details
- Visible Information:
- Your IP address is always visible, and you can see if you are using Tor or what type of browser you have.
- The site reveals details about whether you accept cookies or Java, your screen size, and installed plugins.
- Functionality vs. Privacy:
- While it’s impressive how much information browsers can provide, much of it is necessary for functionality. For example, removing the ability for your browser to disclose certain information can limit its usability.
How Browser Functionality Can Lead to Tracking
Understanding how browser functionality can lead to tracking is essential for maintaining your privacy online. By being aware of these features and potential risks, you can take steps to safeguard your personal information.
Geolocation Tracking
- Definition:
- Browsers, such as Firefox, have the ability to determine your exact location using geolocation services. This information can be used to provide relevant content or targeted advertisements.
- User Prompt:
- When you visit certain websites, a pop-up may appear asking whether you want to share your location. You can choose to disable this feature or opt-out of sharing your location altogether.
Security Features and Privacy Issues
- Safe Browsing and Phishing Protection:
- Many browsers offer security features that check if a site is known for malware or phishing. While this enhances security, it can also raise privacy concerns since the browser communicates with servers each time you visit a site.
- Pings and Tracking:
- Some browsers send out “pings” to track your activity, which can lead to potential tracking by third parties.
Additional Tracking Methods
- WebRTC:
- WebRTC (Web Real-Time Communication) can be used for tracking and discovering your IP address, which can compromise your privacy.
- Extensions and Plugins:
- Installed browser extensions and plugins may communicate with their developers, potentially leaking information about your activity.
- Canvas Fingerprinting:
- HTML canvas fingerprinting uses JavaScript to create a unique identifier based on how your browser renders graphics.
- Browser History:
- If someone has access to your device, they can view your browser history and other cached data, which can happen either remotely or locally.
Tracking Through Operating Systems and Applications
Understanding how operating systems and applications can track you is crucial for maintaining privacy. By being aware of these practices, you can take proactive steps to protect your personal information.
Content Security Policy – Wikipedia
Operating System Tracking
- Overview:
- Modern operating systems, particularly Windows 10, can send various types of information out to external servers, potentially tracking user behavior.
- Applications and Software:
- Any application you install can also send data. This includes not only regular applications but also security software like antivirus programs that constantly communicate with servers for updates.
Deliberate Tracking Applications
- Spyware:
- There are applications specifically designed to track users, such as parental control software and general spying apps used by suspicious partners.
- Malware:
- Various forms of malware, including keyloggers, Remote Access Trojans (RATs), and others, are methods of tracking and can compromise user privacy.
Network Devices and Tracking
- Devices:
- Network devices like routers, switches, and firewalls log the data that passes through them on the internet.
- DNS Concerns:
- There are two main concerns regarding DNS (Domain Name System):
- Logging: Your DNS queries can be logged by your Internet Service Provider (ISP) or any entity managing the DNS server you are using. This is something you can change by using different DNS services.
- DNS Leaking: This can occur when using a VPN (Virtual Private Network). If a DNS request is sent through the unencrypted network instead of through the secure tunnel, it can expose your true IP address and ISP.
- There are two main concerns regarding DNS (Domain Name System):
Automatic Updates and Connections
- Auto-Updates:
- Applications that automatically update themselves can be great for security but may compromise privacy by sending back information.
- Error Reports:
- Automatic error reports sent to developers can also be a method of tracking user behavior.
Tracking Arms Race
- Continuous Tracking:
- The landscape of tracking is an ongoing arms race. As users learn to protect their privacy, new methods of tracking are developed to circumvent these protections.
- Privacy Measures:
- We will cover various methods to secure your privacy, depending on your level of concern, from general awareness to wanting complete anonymity.
Mass Surveillance and Tracking on a Larger Scale
The motives behind mass surveillance, such as protecting national security, may seem commendable. However, the methods used raise serious questions about privacy and individual freedom. Does mass surveillance truly enhance safety and security for the populace?
Capabilities of Nation-States
- Resource Availability:
- Large adversaries like nation-states have the resources to conduct tracking at a population level. They can create usage profiles for every visible user on the internet by collecting various types of data.
- Data Collection:
- To enable mass surveillance, entities need to gather information such as cookies, super cookies, IP addresses, browser fingerprints, referrer data, and other identifying indicators.
Target Detection Identifiers
- Definition:
- Organizations like GCHQ (Government Communications Headquarters) refer to these data points as target detection identifiers or presence events. On their own, these identifiers might seem insignificant, but when linked, they contribute to building a comprehensive profile of an internet user.
- Building Profiles:
- By associating various identifiers, surveillers can understand an individual’s political views, religious beliefs, sexual orientation, social connections, and more. This extensive profiling can only happen if the data passes through infrastructure that the surveilling entity controls.
Example of GCHQ
- Internet Traffic Monitoring:
- GCHQ, similar to the NSA in the U.S., records internet traffic using probes connected to international fiber optic cables, which allows them to monitor a significant amount of global internet traffic.
- Collaboration with Corporations:
- If associations are made between target identifiers and major tech companies (like Google, Microsoft, Apple, etc.), surveilling entities can instantly identify users based on the information these companies have collected.
Risks of Exposure
- Pre-existing Data:
- Individuals may have unwittingly provided their identity through cookies, IP addresses, or email addresses in the past, which can be stored in surveillance databases for later use.
- Profiling in Advanced Countries:
- In countries with advanced technology, such as the 14 Eyes countries (a coalition of countries involved in international intelligence sharing), China, and Russia, users can expect to have profiles built based on their internet usage.
Consequences of Mass Surveillance
- Direct Targeting:
- Profiles might not initially be directly associated with individuals but can become so if users are targeted. For example, if a user demonstrates secular leanings in a religious state, their profile may trigger alerts for further investigation.
- Data Sources:
- Profiles are built from various data sources, including browsing history, communication records, emails, social media interactions, and more.
Anonymity Concerns
- Flagging Activities:
- Any effort to anonymize oneself online, such as searching for VPNs or using Tor, can raise suspicions and lead to investigation.
- Encryption:
- While encryption can mitigate passive data collection, nation-states are developing methods to bypass these protections through legislation and technical means.
Conclusion
This article provides a comprehensive understanding of online tracking and profiling, empowering you to protect your privacy based on this knowledge and your personal circumstances. It covers key tracking techniques including cookies, super cookies, HTTP eTags, and web cache, and explains how tracking occurs through website visits, third-party elements, ad networks, email providers, ISPs, and mobile network providers. The article also discusses the risks of shared networks, man-in-the-middle attacks, and local monitoring.
It offers ways to protect yourself, such as encrypting your traffic, and delves into the role of IP addresses in online tracking, including geographic location inference and ad targeting. The dynamics of IP addresses, including shared and dynamic IP addresses, are explored, along with network address translation (NAT) and web connections via proxies. The article further examines HTTP referrer tracking, cookie and tracking script functions, super cookie resilience, browser fingerprinting, information leakage, and how browser functionality can lead to tracking. It also covers tracking through operating systems and applications, mass surveillance, and the ongoing arms race between tracking and privacy measures.


