Table of Contents
By gaining a deep understanding of the workings, threat mitigation capabilities, and limitations of virtual firewalls, network firewalls, and host firewalls, you will be better equipped to make informed decisions about the appropriate firewall solutions for your organization’s or personal cybersecurity needs. Whether it’s on Windows, Mac OS X, Linux operating systems, through routers, or dedicated firewall devices, this knowledge will provide you with a solid foundation to make more precise and effective security decisions in the face of ever-evolving cyber threats.
Understanding Different Types of Firewalls
Host-Based, Network-Based, and Virtual Firewalls
Now we will delve deeper into host-based, network-based, and virtual firewalls.
Traffic Control
Firewalls function by allowing or denying traffic based on a set of rules, commonly known as an Access Control List (ACL). Most firewalls operate at the network and transport layers, filtering traffic based on:
- Port
- Protocol
- Address
For example, you could configure a firewall to permit only HTTP traffic on TCP port 80, HTTPS traffic on port 443, and DNS traffic on UDP port 53, while blocking everything else.
IP Address Management
Firewalls can also be customized to allow or restrict access to specific IP addresses or ranges of IP addresses.
Advanced Firewalls
More sophisticated firewalls operate at the application layer and perform Deep Packet Inspection (DPI). These are generally dedicated hardware firewalls that can:
- Enforce protocol and port-based rules.
- Inspect the content of the traffic to ensure it is legitimate.
For instance, they can analyze the TLS handshake to confirm that the traffic is truly HTTPS and not something unauthorized like SSH or Tor sneaking through port 443.
Ingress Filtering
Ingress filtering refers to filtering inbound traffic. In a home network, due to Network Address Translation (NAT), external network traffic cannot connect without explicit port forwarding or a demilitarized zone (DMZ) setup.
Host-Based Firewalls
Devices such as laptops can run their own firewalls (e.g., Windows Firewall, Linux’s IP Tables). These are known as host-based firewalls. When traveling on untrusted networks, it’s crucial to block all inbound traffic from potentially harmful devices.
Implicit Deny
All firewalls, whether host-based or network-based, should have an implicit “deny all” rule for external traffic unless specifically permitted.
Egress Filtering
Egress filtering is used to block outgoing connections. For instance, it can prevent a Windows machine from contacting Microsoft or blocking malware from communicating with its command and control servers. Outbound filtering is particularly effective in a home network to stop malware from sending data once it has breached the device.
Reverse Shells and Shell Code
Malware often uses outbound connections to communicate. This is done through reverse shells, which allow the attacker to control the infected device. The code used to establish these outbound connections is often referred to as shell code.
Network Isolation
Firewalls can also be utilized for network isolation, preventing attacks from propagating between internal devices. This is especially relevant for Internet of Things (IoT) devices, which should be considered untrusted.
Types of Firewalls for Home Networks
In a home network, you might consider three types of firewalls:
- Network-Based Firewalls: These handle traffic between the local network and the internet.
- Dedicated Hardware Firewalls: Less common in home networks but can be beneficial.
- Host-Based Firewalls: Installed on individual devices, these can be more effective at filtering specific applications.
Advantages of Host-Based Firewalls
Host-based firewalls can control applications based on a whitelist or blacklist. This allows trusted software to communicate while blocking untrusted applications, which enhances security.
While both network-based and host-based firewalls have their advantages, each has limitations, especially when malware is capable of bypassing defenses by using trusted processes.
Virtual Firewalls: Host-Based and Network-Based
What Are Virtual Firewalls?
A third option for firewalls can be a virtual one, which might be either host-based or network-based. Let’s explore how these can be set up:
- Example Setup: You could have a Xen server on your network with one of its virtual machines (VM) functioning as a firewall.
- Protecting Virtual Environments: Alternatively, you could use a VirtualBox with a PFsense VM to secure guest virtual machines.
Why Use a Virtual Firewall?
A virtual firewall eliminates the need for dedicated hardware. It can be particularly useful when you want to:
- Nest VPN services.
- Prevent VPN leaks in a virtual machine (VM).
- Filter traffic within a VM.
Example Configuration
- Using a PFsense firewall, you can configure network settings to create an internal network and firewall.
- By changing the virtual machine’s network to this internal PFsense network, traffic will be routed through the virtual firewall.
General Firewall Rules
Whether using a host-based or network-based firewall, certain general rules should be followed:
- Default Deny Rule: Deny all network traffic unless it is explicitly allowed.
- Specific Blocks: Block IPv6 and Universal Plug and Play (UPNP) on port 1900 if not in use.
- Service Blocks: Block any unused Windows, Mac, or Linux services.
To tailor firewall rules to your specific needs, monitor traffic and adjust rules accordingly. Some firewalls can automatically set rules based on traffic patterns.
Dynamic Packet Filtering and Stateful Packet Inspection
Modern firewalls use Dynamic Packet Filtering or Stateful Packet Inspection. Here’s what you need to know:
- Allows outbound connections without needing inbound rules for returning traffic.
- When a connection is made, a source port is assigned (e.g., port 1525).
- The firewall dynamically allows inbound traffic using this port while the session is active.
- Once the connection closes, the dynamic access control list is removed.
Virtual firewalls offer flexible solutions for various network setups, particularly when hardware resources are limited. Understanding general firewall rules and how dynamic filtering works can help you effectively manage and secure your network.
Windows Host-Based Firewall Overview
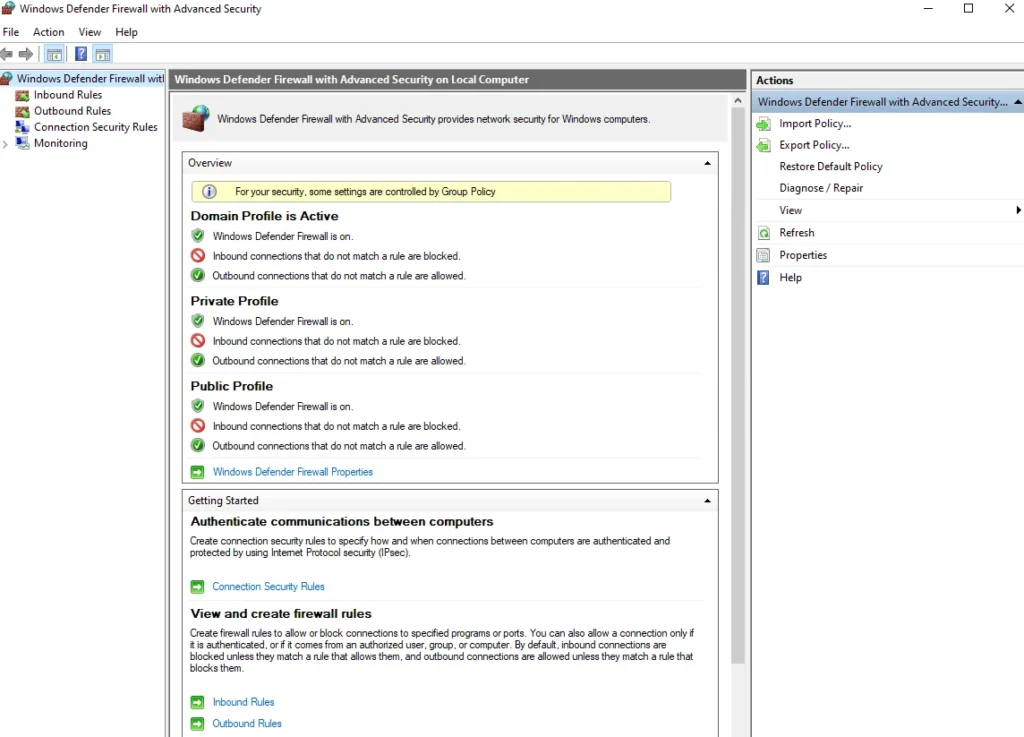
Introduction to Windows Firewall
Let’s explore the host-based firewall in Windows, starting with the default Windows Firewall:
- Accessing the Firewall: Go to the start menu and type “Windows firewall” to find it.
- Default Configuration: By default, it denies all inbound traffic and allows all outbound traffic. Allowing all outbound traffic simplifies configuration but doesn’t adhere to the security principle of denying all unless explicitly allowed.
Advantages and Disadvantages
- Advantages:
- Free and built-in to Windows.
- As powerful as many third-party options.
- Disadvantages:
- Might not block certain Microsoft domains or IP addresses.
- Most common firewall, hence more likely to have bypass strategies developed by malware.
Windows Firewall Interface
- Basic GUI: Simple interface for basic firewall management.
- Advanced GUI: Offers more detailed control but can be complex for standard users.
Firewall Profiles
Windows has different firewall profiles to manage different network types:
- Domain Profile: For corporate networks.
- Private Profile: For home networks.
- Public Profile: For untrusted networks like Wi-Fi hotspots.
Configuration Tips
- Inbound and Outbound Rules: By default, inbound connections are blocked, and outbound connections are allowed across all profiles.
- Locking Down the Firewall: To enhance security, set both inbound and outbound connections to “block” and explicitly allow required connections.
Creating and Managing Rules
- Default Rule Indicators:
- Green Tick: Rule is enabled.
- No Entry Sign: Rule is blocked.
- Gray: Rule is disabled.
- Creating Outbound Rules:
- Example: Allowing TCP connections on port 8080 for Firefox.
- Limitation: Rules are path-based, so they won’t apply if the executable runs from a different location.
General Considerations
- Essential Rules: Some rules are required for core functionalities like DHCP.
- Cleaning Up Rules: Remove unnecessary rules to reduce potential vulnerabilities.
- Outbound Allowances: Ensure outbound rules are set for essential activities like web browsing, SSH, and VPNs.
Enhancing Windows Firewall with Windows Firewall Control
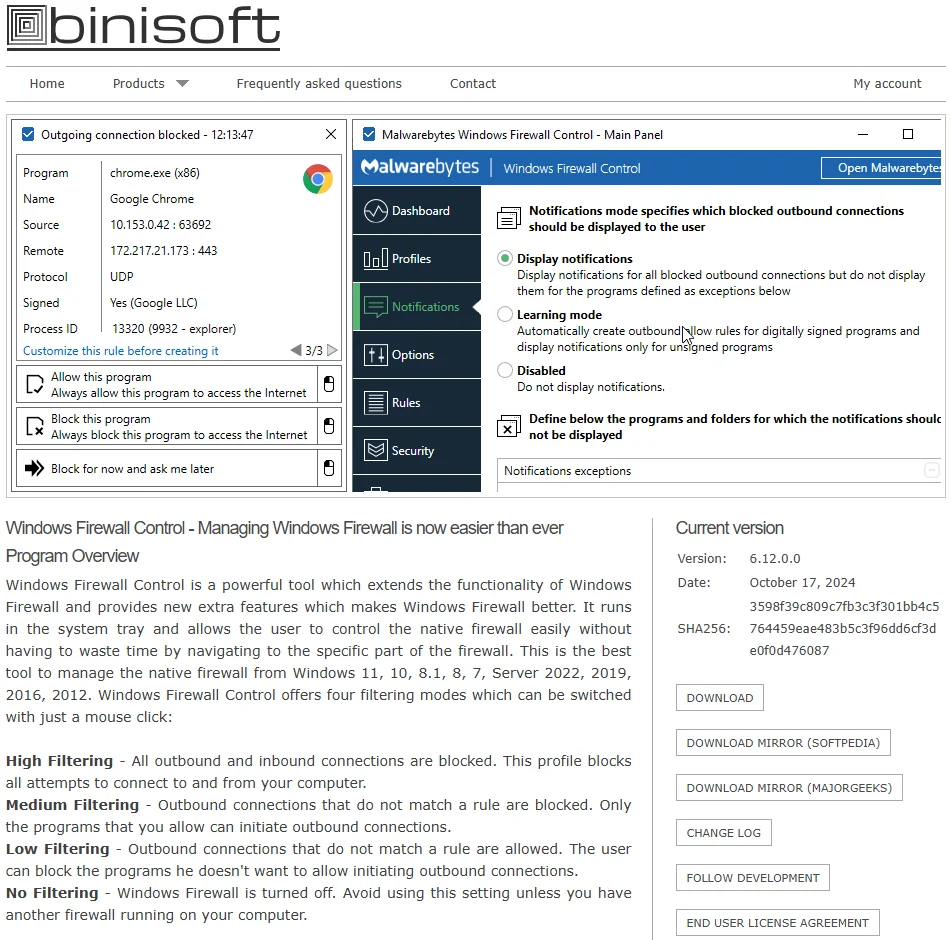
Solving the GUI Problem
If you’re looking to improve the user interface of the Windows Firewall, a free third-party application called Windows Firewall Control (WFC) can help:
- Recommendation: If you plan to use the Windows Firewall, it’s highly recommended to use WFC.
- Installation: Simply download the current version and install it. Note that it’s only available for Windows.
Key Features of Windows Firewall Control
- Profile Management: WFC has its own concept of profiles, separate from Windows profiles:
- No Filtering: Turns off the Windows Firewall.
- Low Filtering: Allows outbound connections not matching a rule and blocks only those with a specific block rule.
- Recommended Setting: Block outbound connections not matching a rule, allowing only those with an allow rule, setting both inbound and outbound to be blocked.
Using WFC Interface
- Rule Management: WFC acts as a front-end to the Windows Firewall, allowing you to manage rules without needing to access the Windows Firewall directly.
- Rule Creation: You can create rules for specific programs or all programs, choose protocols, ports, and profiles to apply.
Additional Features
- Click to Block: Allows you to block or allow connections by simply clicking on a program window.
- Import/Export Rules: You can save your rules and configurations, which is a handy feature for backup or transferring settings.
- High Filtering Profile: Automatically applies a high filtering profile at system shutdown or startup, blocking all network connections until manually changed.
Windows Firewall Control offers enhanced usability and features for the built-in Windows Firewall, making it a valuable tool for users looking to fine-tune their firewall settings. It’s particularly useful for those who want more control over inbound and outbound connections without diving into the complex Windows Firewall GUI.
Third-Party Firewall Solutions for Windows
Introduction
We’ve talked about the built-in Windows firewall and its interface enhancement with Windows Firewall Control. Now, let’s explore third-party firewall options for Windows.
Comodo Firewall
- Overview: Comodo is a popular free firewall that comes with additional software like Comodo browser and GeekBuddy, which may be unwanted or have security vulnerabilities.
- Installation Advice: Only install the firewall, not the full internet suite. Disable GeekBuddy after installation.
- Privacy Concerns: Avoid enabling cloud-based behavioral analysis and anonymous usage reporting due to privacy risks.
- Custom Policy Mode: Use this to manage which applications are allowed to connect to the internet.
TinyWall
- Approach: Offers easy whitelisting of allowed applications, making it simpler to manage permissions without needing to know specific ports and protocols.
- Recommendation: A lightweight firewall option worth considering.
Other Firewalls
- Privatefirewall: Another free option.
- GlassWire: Offers both free and paid versions, providing detailed live monitoring and features like ARP spoof detection.
Security Suites with Built-in Firewalls
- Advantages: Integration with antivirus, offering a unified security strategy.
- Popular Options: Kaspersky and Bitdefender, known for their strong features and reputation systems.
Considerations for Using a Host-Based Firewall
- Protection Level: While a firewall can’t stop all malware, it adds an extra layer of security, particularly against threats from untrusted devices on the same network.
- Use Cases: More critical if you frequently use public hotspots or have many untrusted devices on your network.
- Functionality: Useful for monitoring and logging network activity.
Having a host-based firewall on Windows is generally beneficial, especially for added security in public or untrusted network environments. Despite its limitations, it can serve as an important part of your overall security posture.
Linux-based Firewalls: An Overview of NetFilter and IPtables
Introduction to NetFilter and IPTables
- NetFilter: This is the firewall system used in all modern Linux kernels for packet filtering.
- User Interface: IPtables is the command-line interface used to interact with the NetFilter system.
- Functionality: IPtables allows you to set rules for network traffic, controlling what packets are accepted, modified, or rejected.
Configuring IPTables
- Installation: Almost all Linux distributions include IPtables. If not, it can be installed using the distribution’s package manager.
- Default Chains: IP tables uses three default chains:
- INPUT: Handles inbound connections.
- FORWARD: Manages packets that are forwarded to another device.
- OUTPUT: Deals with outbound connections.
- Default Policies: Each chain has a default policy, which could be set to:
- ACCEPT: Allows the connection.
- DROP: Silently ignores the connection.
- REJECT: Rejects the connection and informs the source.
Managing IPTables Rules
- Viewing Rules: Use the
iptables -Lcommand to list current rules. - Adding Rules: Use the
Aflag to append rules to a chain. - Deleting Rules: Use the
Dflag with a rule number to delete specific rules. - Dynamic Packet Filtering: This allows established connections to continue without needing explicit rules for return traffic.
- GitHub – meetrp/personalfirewall: Personal firewall for my laptop using iptables & ipv6tables. The idea is to protect my laptop while on open network.
Example Configurations
- Basic Setup:
- Allow local communication using the loopback interface.
- Accept established or related connections.
- Allow DNS (port 53), HTTP (port 80), and HTTPS (port 443) traffic.
IPv6 Considerations
- Separate Configuration: IPv6 uses
ip6tablesto manage its rules. - Disabling IPv6: Can be done by setting default policies to drop all IPv6 traffic if not in use.
Helpful Resources
- Scripts and Guides: There are scripts available that automate rule setup and harden firewall settings.
- Comprehensive Guides: Check definitive guides on IPtables for in-depth information and best practices.
Simplifying IPTables with Front-Ends
Challenges with IPTables
- Learning Curve: IPtables is powerful but complex, with many options and switches. Mastering it requires time and effort.
- Solution: Several front-ends have been developed to simplify the process, targeting different user needs.
UFW – Uncomplicated Firewall
- Overview: UFW is a command-line front-end for IPtables, designed to be user-friendly. It simplifies firewall management while still providing access to powerful IP tables features.
- Installation: Not installed by default on Kali Linux but can be added using
apt-get install ufw. - Basic Commands:
ufw enable: Activates the firewall.ufw status: Displays current firewall rules.ufw default deny: Sets default policy to deny incoming/outgoing traffic.ufw allow <port>/ufw deny <port>: Allows or denies traffic on specified ports.- IPv6 rules are also managed automatically, but can be disabled via configuration.
GUI for UFW – GUFW
- Introduction: GUFW provides a graphical interface for UFW, making it even more accessible for beginners.
- Installation: Available on Linux distributions via
apt-get install gufw. - Usage: Offers a user-friendly way to manage firewall rules without using the command line.
Alternative Tools
- Shorewall: A more powerful but complex IP tables management tool, suitable for advanced users.
- Comparison: GUFW is less powerful than Shorewall but provides a simpler interface for basic firewall tasks.
Application Awareness
- Limitations: Unlike Windows, most Linux firewalls, including IPtables and UFW, are not application-aware. Rules are based on ports, protocols, and IPs, not specific applications.
- NFTables: An upcoming project aiming to replace IPtables, providing improved functionality and potentially application awareness.
Considerations for Host-Based Firewalls on Linux
- Security Measures: While Linux has lower malware incidence, a firewall can still provide valuable protection, especially on untrusted networks.
- Use Cases: Important if you frequently connect to insecure networks or have untrusted devices on your network.
- Configuration: To be effective, firewalls should be configured to block unauthorized inbound connections by default, safeguarding against potential internal threats.
Application Firewall in macOS
Overview of macOS Application Firewall
- Version Requirements: macOS versions 10.5.1 and later come with an application firewall that controls connections on a per-application basis.
- Default Status: The application firewall is turned off by default. You can find it in System Preferences > Security and Privacy > Firewall.
- Functionality: This firewall primarily blocks incoming connections and does not monitor or block outgoing connections through the GUI.
Configuring the Firewall
- Adding Applications: You can add applications like Firefox to allow or block incoming connections specifically for them.
- Stealth Mode: Enabling stealth mode disables some ICMP traffic (like ping) for added security.
- Limitations: The firewall allows basic internet services like DHCP, Bonjour, and IPsec but lacks advanced features for controlling outgoing traffic.
Command Line Configuration
- Utilities: The application firewall can also be configured via the command line, with the configuration file located in
/etc/pf.conf. - Loading and Unloading: You can start or stop the application firewall using the
launchctlcommand. - PF Commands: The packet filter (PF) firewall, which is a more advanced option, is available from macOS Lion (10.7) and later, providing stateful packet filtering similar to IP tables in Linux.
Using PF Firewall
- Configuration File: The main configuration file for PF is
/etc/pf.conf, which can include various rules and anchors for managing firewall behavior. - Commands:
pfctl -sr: Shows the active rules.pfctl -ss: Displays the current state table.pfctl -si: Shows filter stats and counters.
- Setting Rules: You can enable or block specific inbound and outbound traffic by editing the configuration file.
Combining Application Firewall and PF
- Interaction: The application firewall generates dynamic rules for PF, allowing both systems to work together.
- GUI Management: You can manage PF rules through the application firewall GUI, which provides an easier interface for those not comfortable with command-line usage.
Resources for Learning PF
- Documentation: The manual pages and OpenBSD’s PF user guide provide detailed information on configuring and using PF.
- Cheat Sheets: There are various cheat sheets and beginner guides available online to help you get started.
GUIs for PF Firewall on macOS
Introduction to GUIs
- PFList: This is a simple graphical interface that displays the rules of the PF firewall. It’s straightforward and primarily for viewing rules.
ICEfloor
- Overview: ICEfloor is a more comprehensive firewall front-end but only supports macOS versions 10.7 to 10.10.
- Features: It offers useful presets to make using PF easier.
Murus: The Most Powerful Option
- Versions: Murus comes in three versions: Lite, Basic, and Pro.
- Murus Lite: Free but has limited features.
- Murus Pro: Offers the most features, including an application layer firewall called Valem.
Murus Features
- Control: Provides full control over both application and network layers.
- User Interface: Offers a drag-and-drop feature for managing services and configuring rules.
- Inbound and Outbound Rules: Allows for dynamic ports and basic services management.
Specific Functionality
- Creating Groups: Users can create groups of IP addresses to customize rules.
- Service Management: Easy drag-and-drop functionality to enable or restrict services, such as web servers.
- Configuration Strategies:
- Restore default configurations.
- Use configuration wizards to set up firewalls based on preferences.
- Choose from predefined configurations for safety.
Murus Pro Advantages
- Documentation: Comes with excellent documentation and video tutorials for ease of use.
- Advanced Features: Includes bandwidth control, traffic inspection, and more.
Murus Pro is highly recommended for users seeking a robust and user-friendly firewall management tool on macOS.
Little Snitch: A Recommended Firewall for macOS
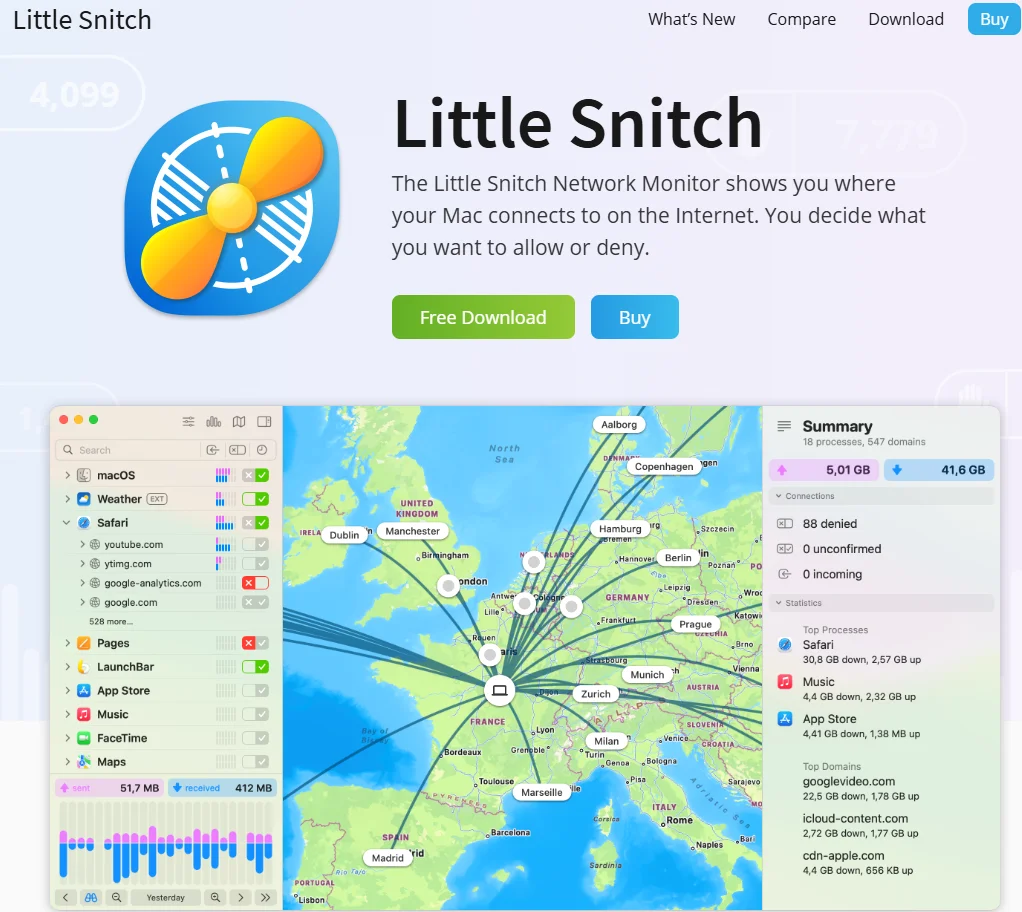
Overview of Little Snitch
- Application-Based GUI Firewall: Little Snitch is highly regarded for its user-friendly interface compared to other firewalls.
- Traffic Monitoring: It offers excellent live monitoring of both inbound and outbound traffic.
- Cost: The application is not free, priced at approximately 30 euros, but it provides significant utility in traffic management.
Features of Little Snitch
- User Interface: The interface is straightforward and easy to navigate, allowing users to see all rules clearly.
- Rules Management: Users can enable or disable rules with visual indicators (tick marks for enabled rules and colors for allow/deny status).
- Connection Management: It allows users to approve or deny connection attempts, particularly useful in silent mode where notifications are minimized.
Network Monitor
- Functionality: The Network Monitor displays all active connections and processes, allowing users to see which connections are being blocked.
- Traffic Capture: Users can capture traffic and create rules based on specific needs.
- Detailed Information: It provides detailed insight into what traffic is going in and out, enabling quick adjustments.
Security Considerations
- Host-Based Firewall Usage: The necessity of a host-based firewall on macOS depends on usage patterns. macOS faces fewer malware threats compared to other operating systems, but threats are increasing.
- Built-In Firewall Limitations: The macOS built-in firewall does not block outbound connections, which is a significant gap in malware protection.
- Application-Aware Firewalls: Tools like Little Snitch provide better protection against malware by blocking unwanted outbound communications.
Balancing Security and Usability: Users need to weigh the importance of security against the administrative overhead of managing firewall rules. For those using untrusted networks or traveling, a host-based firewall like Little Snitch is a practical choice.
Network-Based Firewalls
Introduction to Router Firewalls
- Router Firewalls: The primary place for a network-based firewall is on your router. High-end routers often come with robust firewall capabilities, whereas low-end routers may have limited or no firewall functionalities.
- Custom Firmware: Using custom firmware like OpenWRT or DD-WRT can provide more configurable firewall options, specifically through the use of iptables.
OpenWRT and DD-WRT
- iptables: Both OpenWRT and DD-WRT use iptables to manage firewall rules. This allows for advanced configuration, often requiring command-line access for full functionality.
- DD-WRT GUI: The graphical interface in DD-WRT allows for basic iptables management, including enabling/disabling rules and adding filters. However, more advanced configurations typically require command-line input.
Advanced Configuration in DD-WRT
- Accessing Commands: Within DD-WRT, users can navigate to the administration section to enter iptables commands, which will execute upon router startup.
- SSH Access: Users can also SSH into the router for direct command-line management of iptables.
Caution
- Avoid Lockouts: When configuring iptables, be cautious not to lock yourself out of the administrative interface.
Additional Tools
- Firewall Builder: This is a third-party GUI tool that can be run on a separate machine to manage iptables rules on the router remotely via SSH. It supports macOS, Windows, and Linux.
- Resources: Documentation and videos are available to help users get started with tools like Firewall Builder.
For those unfamiliar with command-line operations, tools like Firewall Builder can simplify the configuration of iptables, especially when used with custom firmware such as DD-WRT.
Dedicated Hardware and Virtual Network Firewalls
Overview
- Enhanced Functionality: For more powerful and user-friendly GUI configuration, consider using a dedicated hardware or virtual network firewall.
- Old PCs or Laptops: These can be repurposed as firewalls if they have sufficient processing power.
- Dedicated Hardware: Alternatively, you can purchase a dedicated firewall device, which is often more efficient.
Dedicated Hardware Options
- APU Devices: These are recommended for those looking to set up dedicated routing and firewalling. APU platforms are designed specifically for this purpose and come with multiple network cards.
- Functionality: With dedicated hardware, the device can serve both as a router and a firewall, potentially eliminating the need for separate devices in your network.
- Cost: Prices range from approximately $100 to $130 USD, which is reasonable given the functionality provided.
Configuration Considerations
- Separate Router and Firewall: Some configurations may benefit from having separate devices for routing and firewalling, providing additional isolation.
- Internet Connectivity: Ensure you have a modem or another device to connect to the internet alongside your firewall/router.
Open Source Hardware
- Prevention of Interdiction: For those concerned about security, open-source hardware is an option, though it may require additional research to find suitable suppliers.
Recommended Network Firewalls
PFSense Overview
- PFSense: This is a highly recommended free open-source firewall/router software based on FreeBSD. Unlike custom router firmware, PFSense is installed on a dedicated computer, allowing for more robust firewall and routing capabilities.
- Feature-Rich: PFSense offers a user-friendly interface and provides functionalities typically found only in expensive commercial firewalls.
Key Features of PFSense
- Firewall and Router: PFSense can serve as both a firewall and a router, and it includes features such as DHCP, DNS server capabilities, and more.
- Intrusion Detection and Prevention: You can install tools like Snort for enhanced security, allowing for network isolation and the management of trusted and untrusted devices.
- VPN Support: It can function as both a VPN client and server, offering privacy benefits by routing traffic through a VPN.
- Customization: Users can also add additional services such as Tor for enhanced privacy.
Hardware Options
- Dedicated Hardware: PFSense has its own hardware options, though they tend to be on the expensive side. The basic model starts at about $299.
- Installation: PFSense is installed similarly to any other operating system; you just need to download the ISO and set it up on your hardware.
Alternatives to PFSense
- OPNsense: This is a fork of PFSense that focuses more on open-source principles. It may be a preferable option for those who prioritize open-source software.
- Smoothwall: Another popular firewall with a free open-source version (Express option) and a commercial version.
- VYOS: A more technically-oriented choice, offering a unified command-line interface reminiscent of Cisco hardware.
Virtual Machine Option
- Virtual Firewalls: Instead of dedicated hardware, you can run a network-based firewall on a virtual machine. However, this requires robust hardware to ensure optimal performance.
Importance of a Network Firewall
- NAT and Security: While Network Address Translation (NAT) provides some protection by blocking unsolicited inbound traffic, implementing a network firewall is still beneficial, especially for outbound filtering.
- Traffic Management: You can configure your firewall to limit access to specific ports and services, enhancing security by controlling which services can communicate outward.
- Logging and Monitoring: A dedicated firewall can offer superior logging capabilities, allowing you to monitor network traffic for potential threats.
Network Isolation: A network firewall can aid in creating isolation within your network, enhancing security, privacy, and anonymity.
Ease of Use: While good routers offer some isolation capabilities, a dedicated firewall like PFSense provides more comprehensive functionality for network management.
Conclusion
This article delves into various types of firewalls, including virtual, network, and host-based firewalls. By understanding their mechanisms, threat mitigation capabilities, and limitations, users can select appropriate firewall solutions for personal or organizational needs. Whether on Windows, Mac OS X, Linux operating systems, through routers, or dedicated firewall devices, this knowledge aids in making more precise and effective security decisions in the face of evolving cyber threats.


