Table of Contents
Removing Privilege
In this post is to understand the simple yet extremely effective method of reducing default privileges, which can help contain malware or an attacker by limiting the privileges they operate under.
Privilege Levels and Threats:
- Most attackers have the level of privilege of the logged-in user or the privilege of the process running the exploited application.
- If you’re logged in with administrative privileges (effectively “God” on the operating system), any malware that exploits the system through you or a process you’re running will have the same level of privileges.
- However, if you’re logged in with restricted privileges, the malware is also restricted.
Privilege Reduction Approach:
- Restricting privileges is a standard practice in Linux and Unix-like operating systems, where the admin or root account is rarely used directly.
- In Windows, however, administrative privileges are the default.
- To mitigate this, you should change your account in Windows to be a standard user and use an admin account only when needed (e.g., installing applications).
Benefits of Privilege Reduction:
- Reducing privileges forces an attacker to attempt privilege escalation techniques, which may not be available or built into the malware.
- According to Avecto’s annual Microsoft vulnerability report, removing user admin privileges in Windows would stop 86% of all Windows threats, a staggering statistic.
- This highlights the importance of not running as an administrator but as a standard user in Windows and other operating systems.
Best Practices:
- Train yourself not to blindly enter the admin password when prompted, and question the reason for the admin username and password prompt to ensure it’s genuine.
- Reducing privileges effectively reduces the attack surface and mitigates the impact of successful attacks.
Windows 7 – Not Using Admin Account
In this post, I will explain how to remove administrative privileges from your account in Windows 7 and create a separate administrator account for when you need elevated privileges.
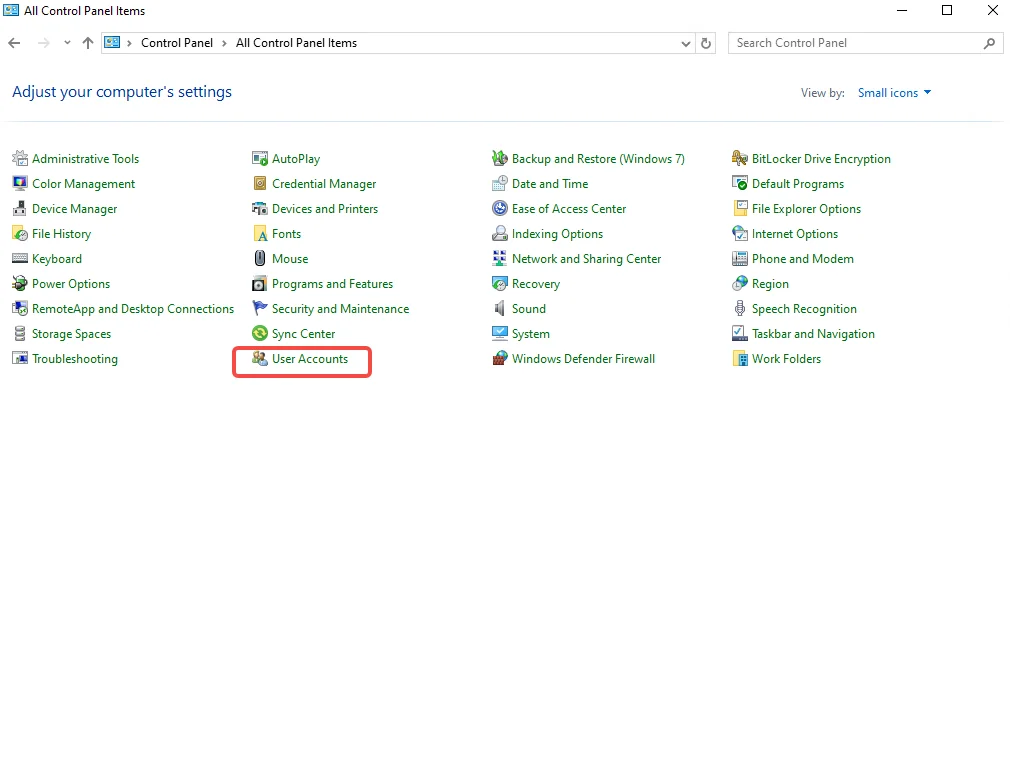
Step 1: Access User Accounts
- Go to Start > Type “user account” > Click on “User Accounts”
- Click on “Manage another account”
Step 2: Identify Your Current Account Type
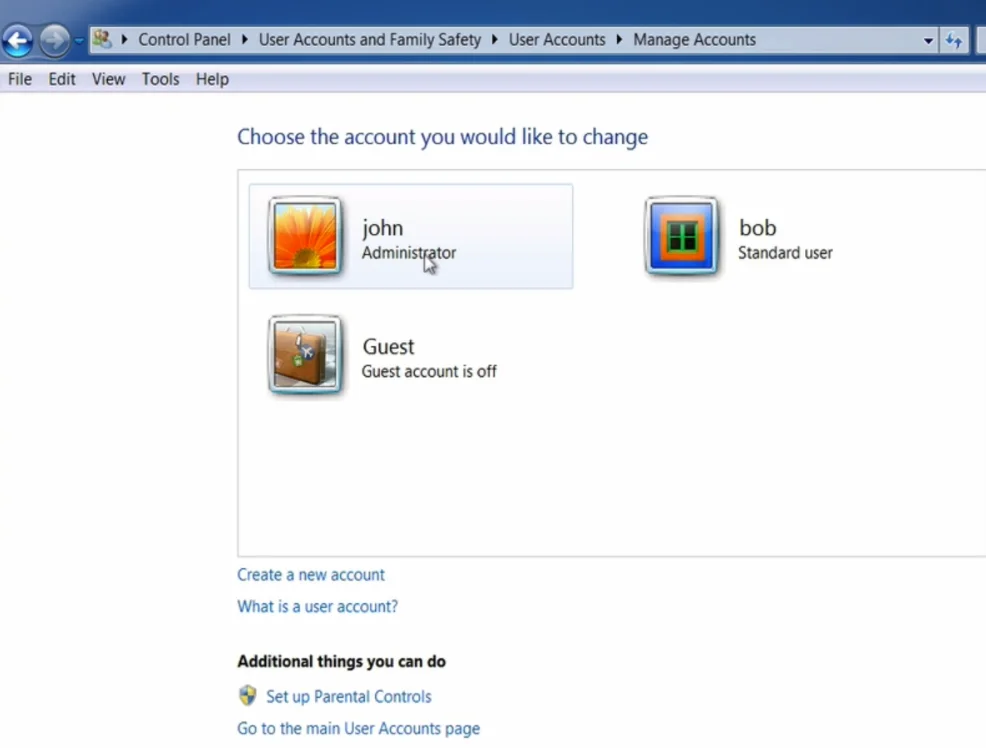
- Locate your account in the list and check if it is an administrator account or not.
- In this example, the account “John” is an administrator account.
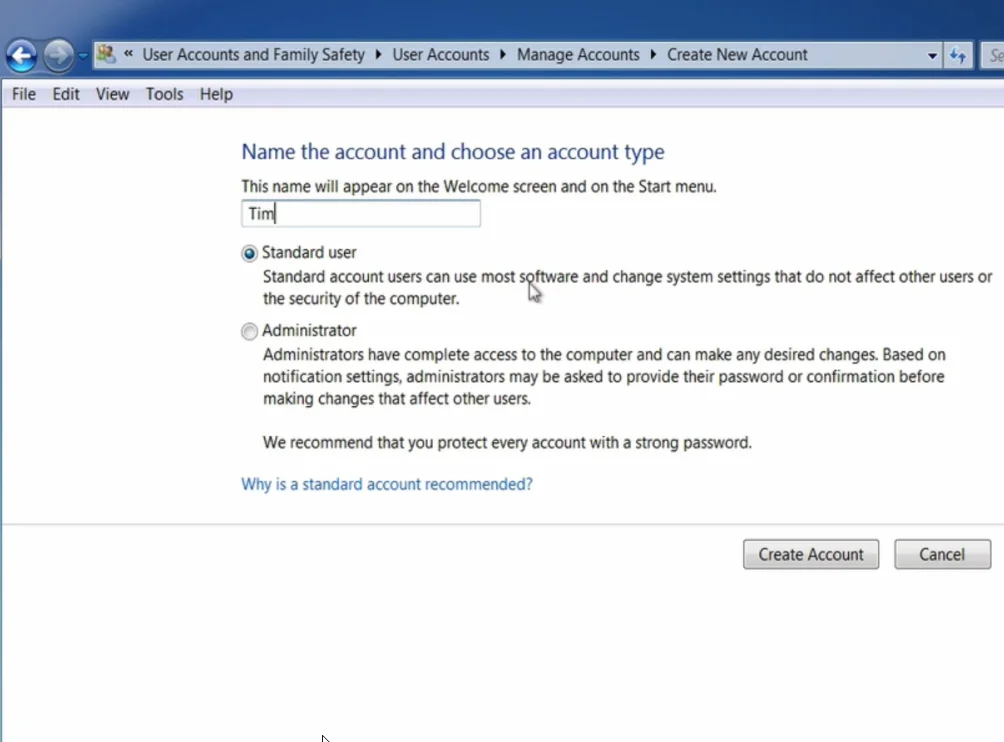
Step 3: Create a New Administrator Account
- Click “Create a new account” and provide a name (e.g., “Tim”).
- Avoid naming it “administrator” for security reasons.
- Select “Administrator” as the account type.
- Click “Create Account”.
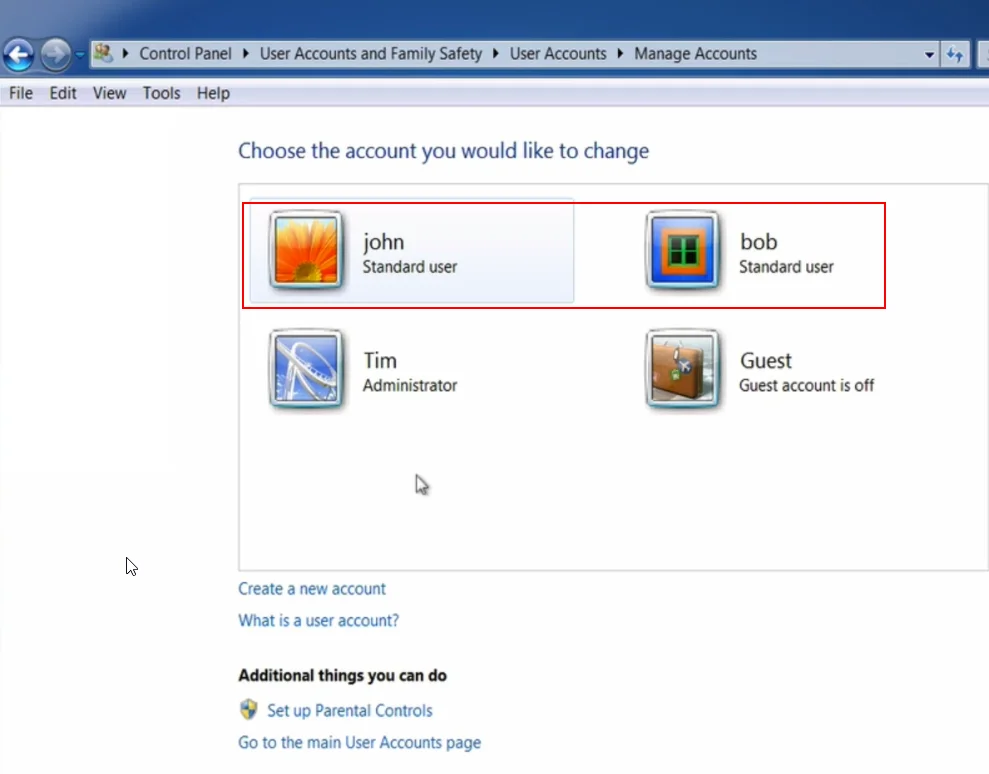
Step 4: Change Your Original Account to Standard User
- Click on your original account (e.g., “John”).
- Click “Change the account type”.
- Change the account type to “Standard user”.
Step 5: Set Passwords for Accounts
- Click on the new administrator account (e.g., “Tim”).
- Click “Create a password” and set a strong password.
- Follow best practices for creating secure passwords.
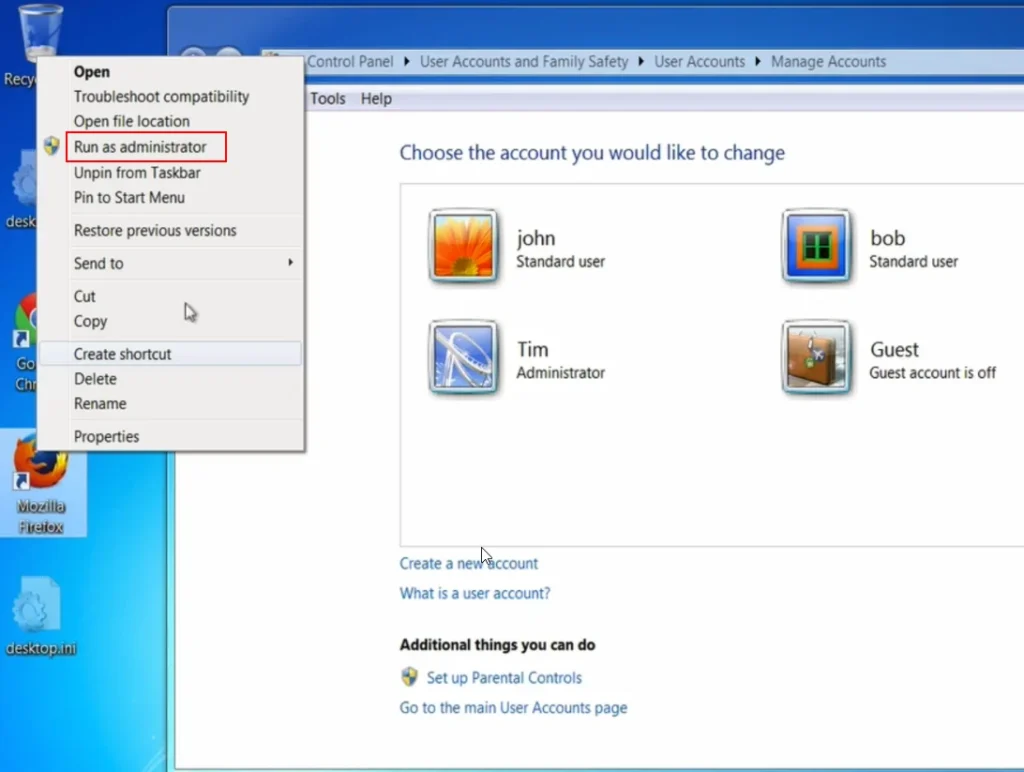
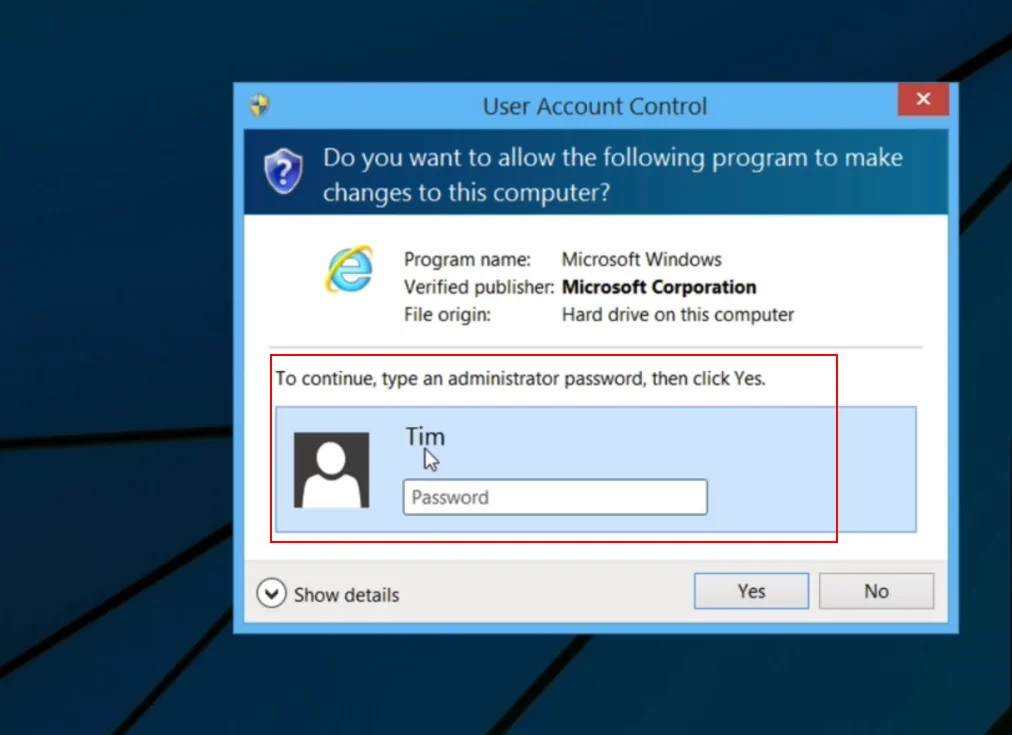
Step 6: Running Applications with Admin Privileges
- If you need to run an application with administrative privileges, right-click on the application and select “Run as administrator”.
- You will be prompted for the username and password of the administrator account (e.g., “Tim”).
- This will allow that specific process to run with elevated privileges.
Additional Recommendations
- Remove administrative privileges from any other user accounts on the machine.
- Disable or delete any unused accounts.
Windows 8 and 8.1 – Not Using Admin Account
I will explain how to remove administrative privileges from your account in Windows 8 and 8.1, and create a separate administrator account for when you need elevated privileges.
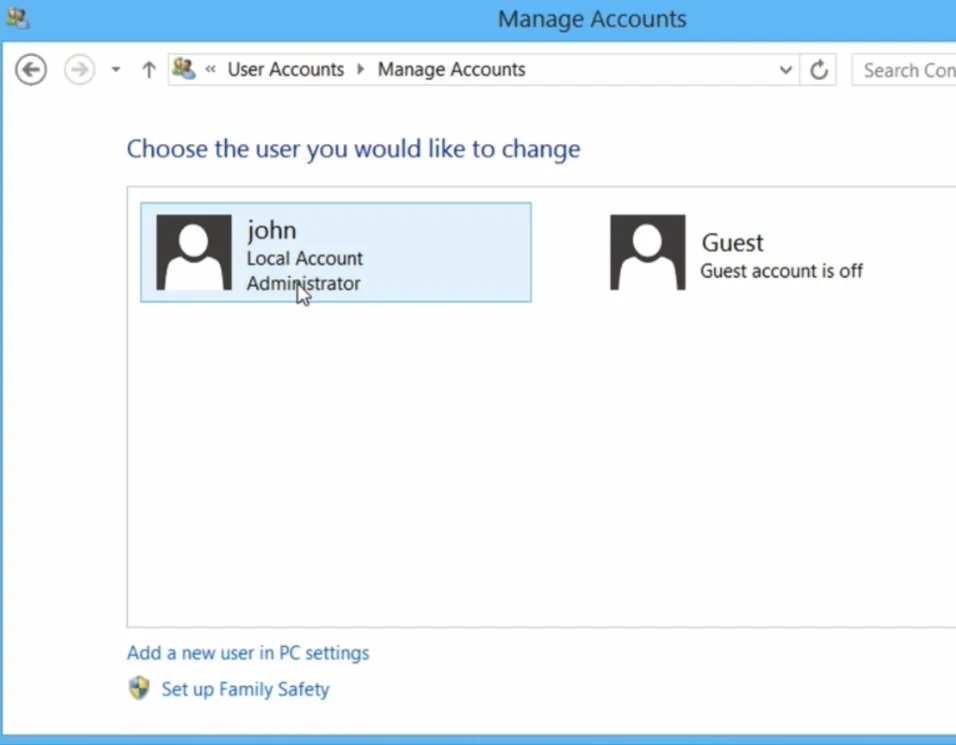
Step 1: Access User Accounts
- Click the Windows button or Start menu
- Type “user accounts” and click on “User Accounts”
- Click on “Manage another account”
Step 2: Identify Your Current Account Type
- Check if your logged-in account has administrator privileges or is a standard user account.
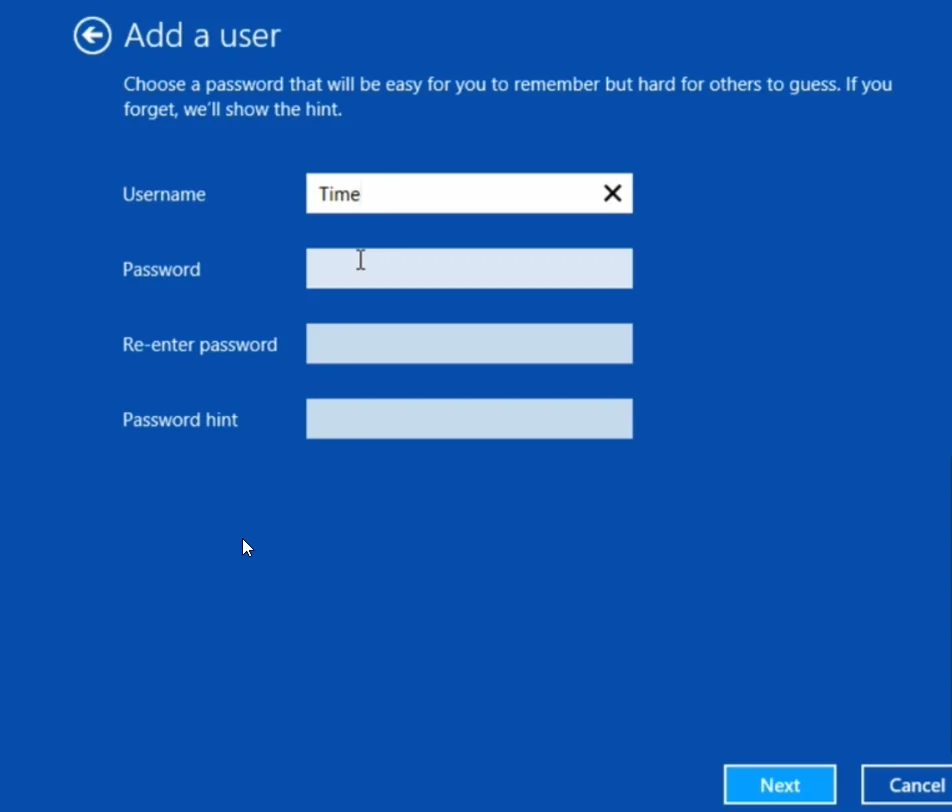
Step 3: Create a New Administrator Account
- Click “Add an account”
- Choose “Sign in without Microsoft account” > “Local account”
- Avoid naming it “admin” for security reasons (e.g., use “Tim”)
- Set up a strong password following best practices
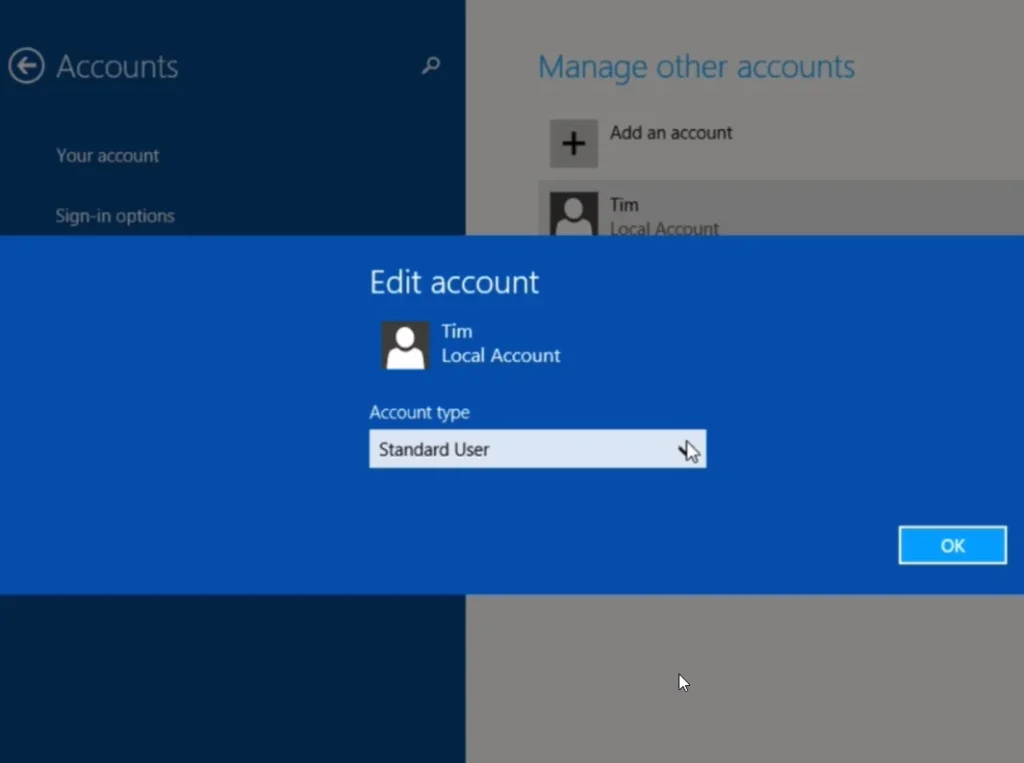
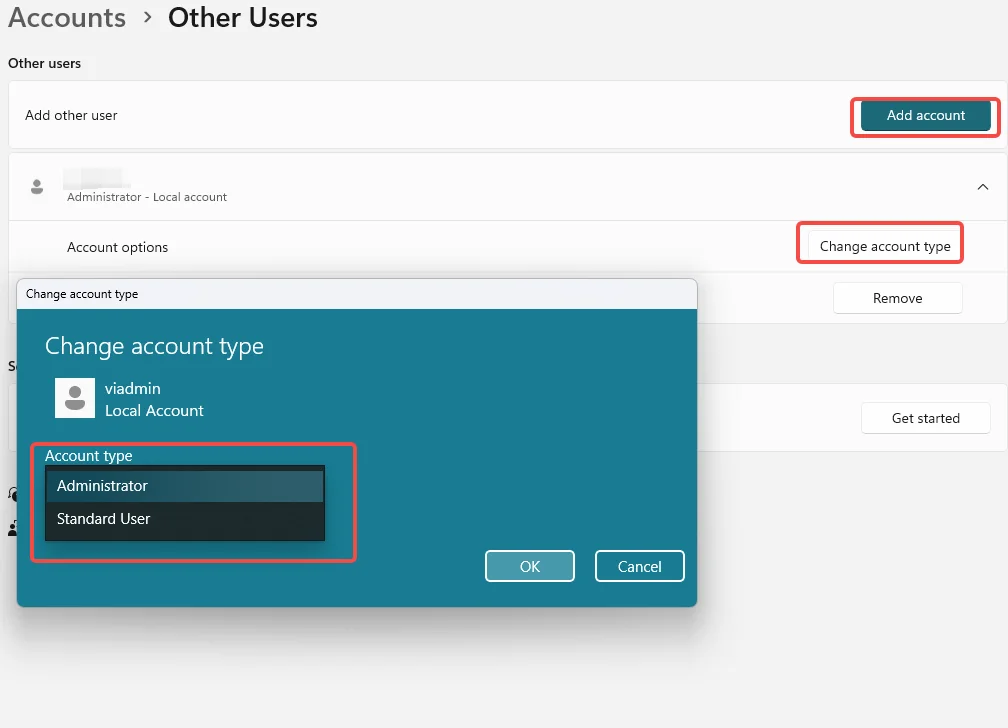
Step 4: Change New Account to Administrator
- Click on the new account (e.g., “Tim”)
- Click “Edit” > Change account type to “Administrator” > Click “OK”
Step 5: Change Your Original Account to Standard User
- Click the Windows button > Type “account” > Click “User accounts” > “Manage another account”
- Double-click on your original account
- Click “Change account type” > “Change to standard” > “Change account type”
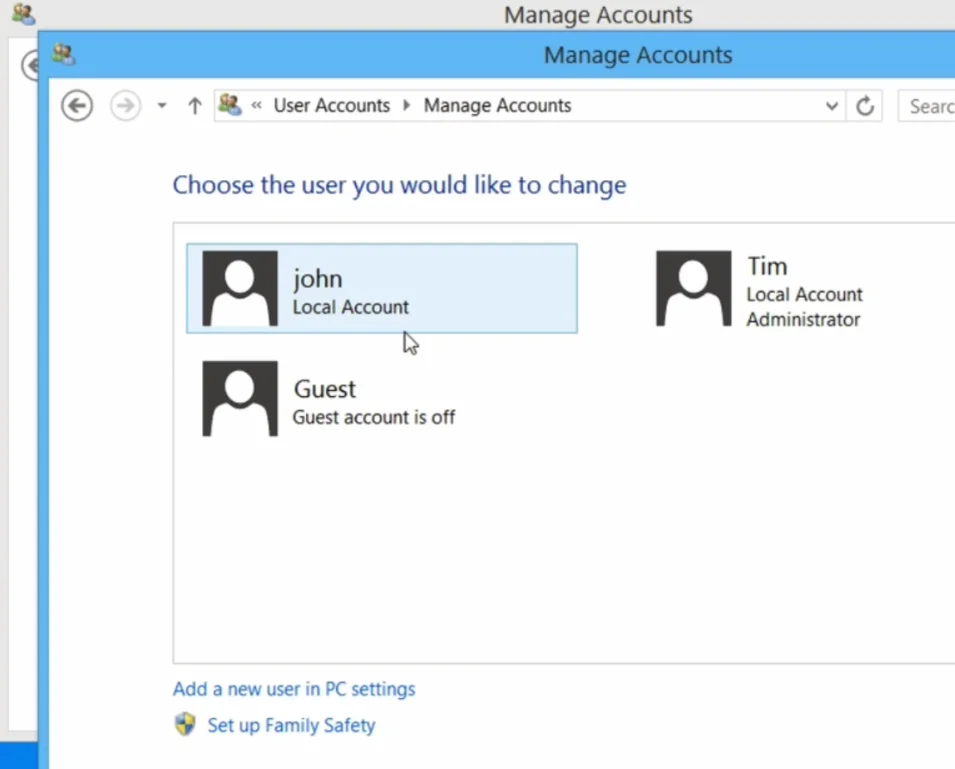
Step 6: Verify Account Changes
- Click “Manage another account” to verify the account changes
- Your original account should now be a standard user
- The new account (e.g., “Tim”) should be an administrator
Additional Recommendations
- Disable or remove any unused accounts
- Remove administrative privileges from any other accounts, except the dedicated administrator account
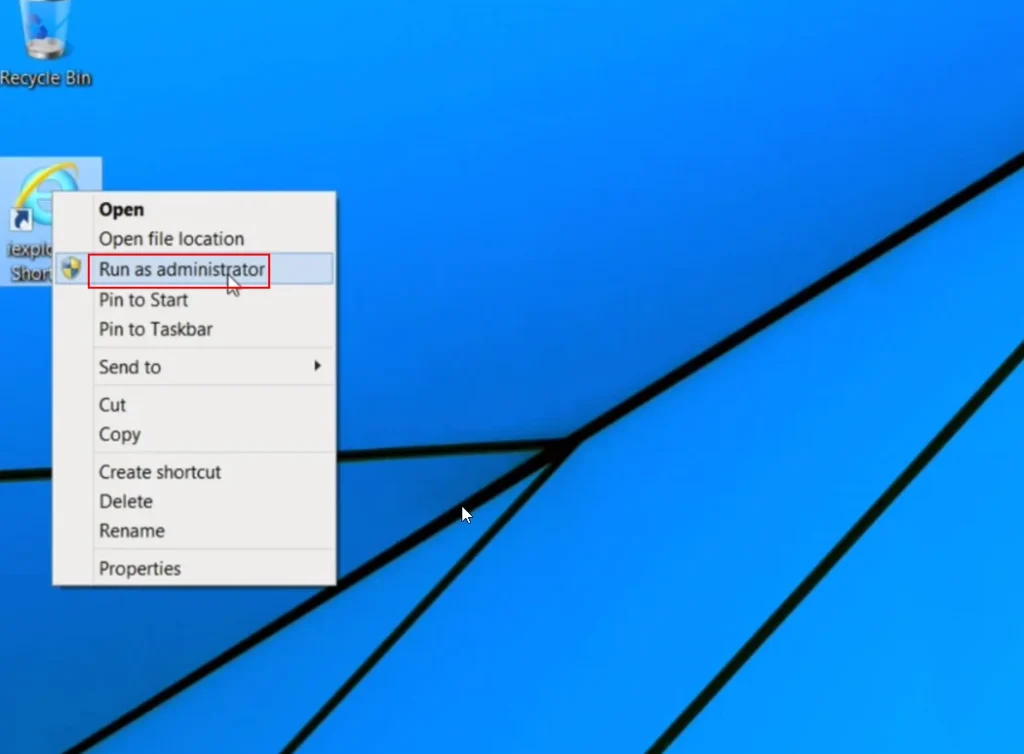
Running Applications with Admin Privileges
- If you need to run an application with administrative privileges while logged in as a standard user, right-click on the application and select “Run as administrator”
- You will be prompted for the administrator account’s username and password
- Use this feature judiciously, as running untrusted applications with elevated privileges poses a risk
Windows 10 – Not Using Admin Account
I will explain how to remove administrative privileges from your account in Windows 10 and create a separate administrator account for when you need elevated privileges.
Step 1: Access User Accounts
- Click on “User accounts” or “Settings”
- Click on “Manage another account” or “Accounts”
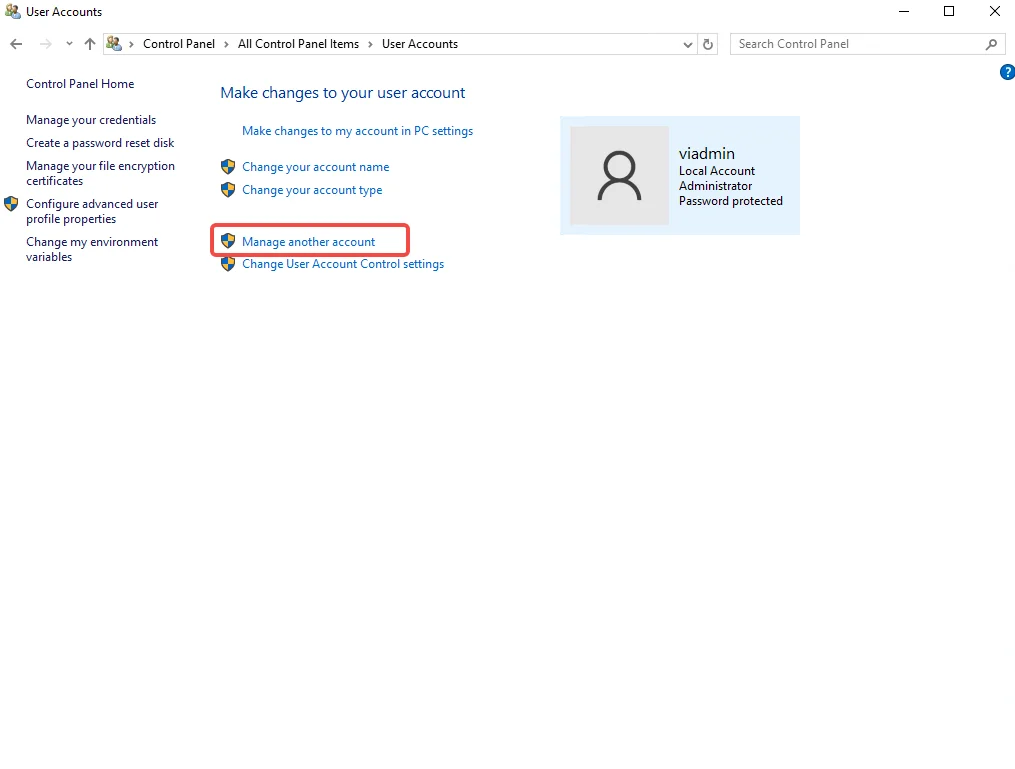
Step 2: Identify Your Current Account Type
- If your current account is not an administrator, you don’t need to change it.
Step 3: Create a New Administrator Account
- Click “Add someone else to this PC”
- Choose “The person who I want to add doesn’t have an email address”
- Click “Add a user without Microsoft Account”
- Enter a username (e.g., “Bob” or “Bobo”) – avoid using “admin” or “administrator”
- Click “Next”
Step 4: Change New Account to Administrator
- Click “Refresh” if the new account is not visible
- Click on the new account (e.g., “Bob”)
- Click “Change the account type” > “Change to administrator” > “Change account type”
- Click “Manage another account” to verify the change
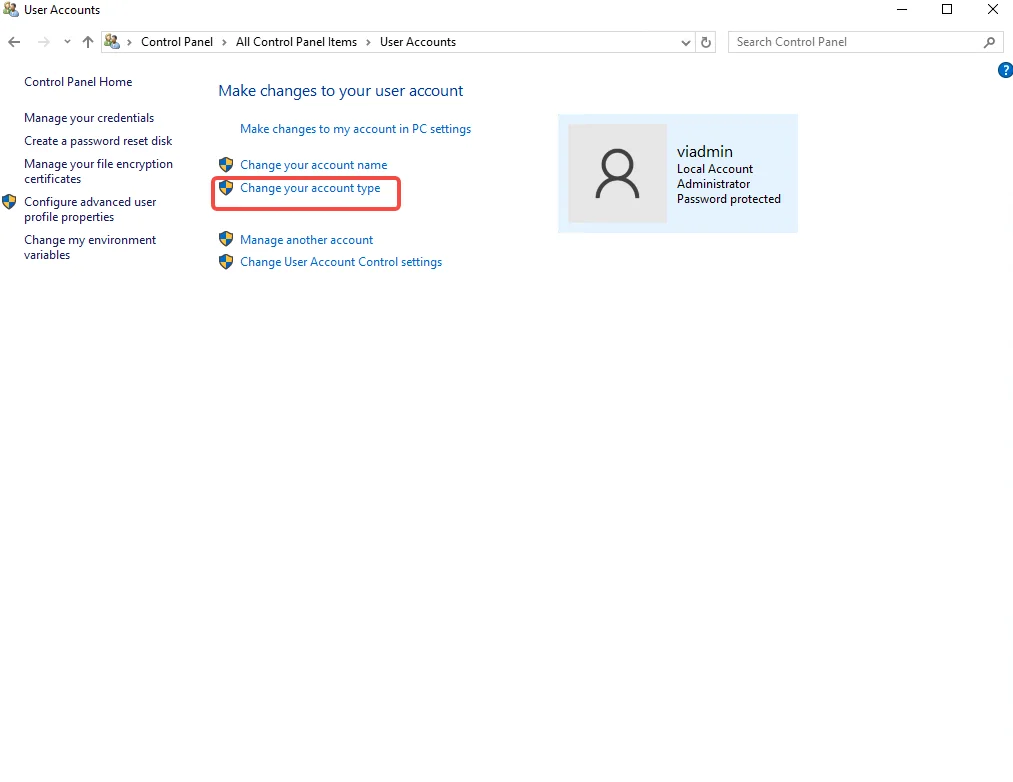
Step 5: Change Your Original Account to Standard User
- Click on your original account
- Click “Change the account type” > “Change to standard” > “Change account type”
- Click “Manage another account” to verify the change
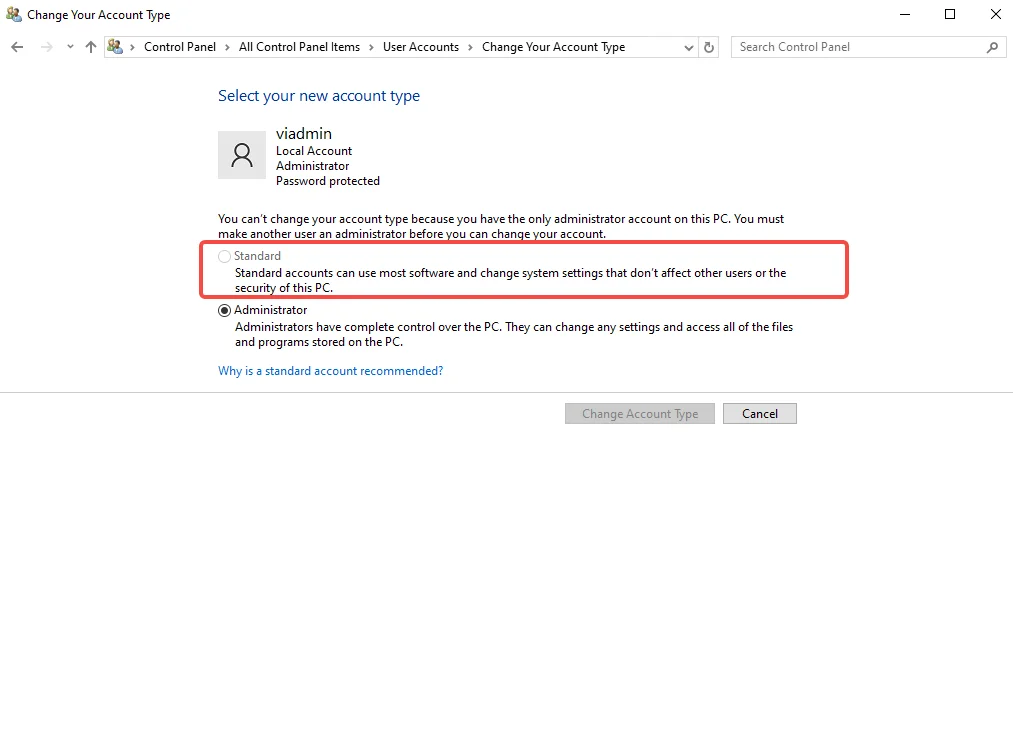
Step 6: Verify Account Changes
- Your original account should now be a standard user or local account
- The new account (e.g., “Bob”) should be an administrator
Additional Recommendations
- Disable or delete any other unused accounts
- Remove administrative privileges from all other accounts, except the dedicated administrator account (e.g., “Bob”)
Running Applications with Admin Privileges
- If you need to run an application with administrative privileges while logged in as a standard user, right-click on the application and select “Run as administrator”
- You will be prompted for the administrator account’s username and password
- Never run untrusted applications with elevated privileges
By following these steps, you will be running your daily tasks with a standard user account, reducing the risk of malware or attackers gaining administrative privileges. The separate administrator account can be used only when necessary, minimizing the exposure of elevated privileges.
Conclusion
This section emphasizes the importance of reducing default privileges to help limit the operational scope of malware or attackers. Attackers typically have the same privileges as the logged-in user, so using a standard user account with restricted permissions can effectively mitigate risks. Windows systems often default to administrative privileges, so it’s advisable for users to set their personal accounts as standard users and use a separate administrator account only when necessary.
This approach significantly reduces the attack surface and can prevent most threats. Best practices include being cautious about entering the admin password, regularly checking user account privileges, and ensuring unnecessary accounts are removed. Ultimately, using a standard user account for daily tasks while relying on an administrator account only when needed enhances system security and lowers the risk of being compromised.


