Table of Contents
The main goal of this text is to provide a more in-depth understanding of the current threat and vulnerability landscape.
Have a good grasp of yourself when you are about to face some threats and malicious attackers – try to think of the techniques that hackers might use to attack using encryption rules, exploit kits, pop-ups and browser hijacking.
Based on these aforementioned malicious behaviors, combining them together constitutes a risky threat environment. So choosing the right security measures depends a lot on the risks you face, and this can be heavily influenced by the threat environment.
Why You Need Security – The Value Of A Hack
Let’s get real about cybersecurity. You might be thinking, “Why would anyone target little old me?” Well, it’s not some hacker sitting in a dark room manually targeting you. It’s automated attacks, scripts, and bots scouring the web for vulnerable targets—basically, anyone’s fair game. Your router gets scanned daily for weaknesses, and we’ve all fallen for those phishing emails or visited sketchy sites. The truth is, we’re all potential victims.
Now, there are bigger threats too, like targeted attacks by well-funded groups or even governments. But most of us just need to worry about the wide nets cast by cybercrime groups. These guys are after one thing: money. They’ll use your PC for web hosting, sell your info, or hold your data hostage. It’s a lucrative business, with billions lost to cybercrime annually.
So, why do we need security? To protect our digital selves and our assets. An email account, for example, can be a goldmine for hackers because it’s often the key to all your other accounts. That’s why there’s a thriving cybercrime underground. This course will help you understand the risks and take easy steps to lower your exposure. Let’s dive in and get our cyber defenses up!
The Top 3 Things You Need To Stay Safe Online
Hey there! So, you know how everyone’s always talking about how to stay safe online, right? Like using antivirus software, only going to websites you know, deleting cookies, and changing passwords all the time. Well, guess what? If that’s your game plan, you’re missing the mark. Google did this study where they asked both security pros and regular folks what the top three things to do are for staying safe online. And, surprise, surprise, the stuff most people think is crucial? Not so much, according to the experts.
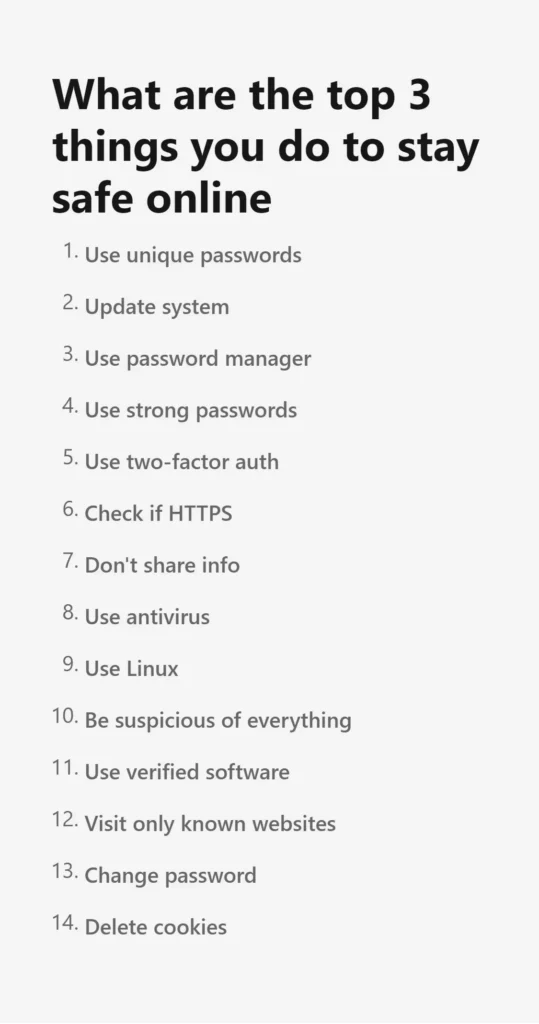
We’re going to be going over what really works to keep you safe in the digital world, not just the myths spread by security companies. So, buckle up and get ready to learn some real online security tips!
Security Bugs and Vulnerabilities – The Vulnerability Landscape
Alright, so let’s talk about security bugs and vulnerabilities in cyber security. You know, it’s like this ongoing battle between the good guys and the bad guys, and sadly, we’re not winning. We all love cool tech that helps us do more stuff, but the more we get, the more we depend on it, and the whole system gets more complex. And here’s the kicker: complexity is a real killer for security. It’s one of the big reasons we’re struggling in this fight.
So, security bugs and vulnerabilities, they’re basically the same thing, just two names for the same problem. When I say “security bug” or “vulnerability,” I mean the same thing. It’s a mistake in the software that leaves a door open for a hacker to sneak in. Take the Heartbleed bug, for example, which you’ve probably heard about. It was a flaw in Open SSL that let hackers peek at data meant to be secure, like your bank login details.
Now, these bugs aren’t going anywhere as long as humans are writing code. Think about it, the Windows operating system has millions of lines of code. We’re only human; we make mistakes, and that means security bugs happen.
Check out these diagrams – on the left, you got your computer, and on the right, the internet. Vulnerabilities can be anywhere – your operating system, firmware, apps like Outlook, even your browser and its add-ons. One wrong click on a website, and bam, you’ve got malware.
And it’s not just your computer; your online stuff is at risk too. Maybe you use Dropbox, and there’s a bug that lets a bad guy get into your files. Not cool, right?
There are two main types of bugs: Known and Unknown. Known bugs have patches, which is like a fix to the problem. If you keep your system updated, you’re safe from those. But Unknown bugs, also called zero-days, are tricky because there’s no patch for them. We’ll talk more about how to deal with these later.
Now, let me show you something interesting. There are these exploit kits that hackers can just buy. This spreadsheet here shows different kits and the vulnerabilities they can exploit. It’s like shopping for trouble. Say you want to target Internet Explorer; there’s a kit for that. And it’s as easy as visiting a website for your machine to get compromised.
So I hope this gives you a clearer picture of what security bugs and vulnerabilities are all about. Later on, we’ll dive into how to protect against both the Known and Unknown bugs.
Hackers, crackers and cyber criminals
So let’s dive into the current threat landscape. It’s all about understanding the bad stuff out there that we need to worry about. First up, we’ve got hackers, crackers, and cybercriminals. Check out what’s happening behind you – that’s an active IRC channel where they’re selling everything from stolen credit cards to malware, viruses, even hacking services. IRC, by the way, is a part of the internet, not the web, and you access it through an IRC client.
Now, the term “hacker” used to be a good thing, referring to someone who kept at a problem until it was solved. But nowadays, it’s mostly used for someone causing trouble online or on your computer. There are white hat hackers, who are the good guys, like when I do ethical hacking or penetration testing for a company. But we’re focusing on the black hat hackers, or just call them cybercriminals. They’re not just kids in their mom’s basement looking for a thrill; they’re out to make money off you and others.
You’ve got hacking groups or criminal organizations of all sizes. There are loose groups of hackers who hang out on the dark web, not tightly connected but linked by some web of common interests or agendas. And then there’s the lone wolf hacker. The skill level of these hackers varies a lot. Most of them, maybe 95%, are what we call script kitties – they just run scripts written by others. But don’t underestimate them. The other 5% are the skilled ones, and they’re the dangerous ones.
These days, the skilled hackers sell their tools to the script kitties, and there’s even an underground market for hacking services. That’s why script kitties can be just as dangerous. You can rent time on a hacking platform. If these guys put as much effort into legit businesses, they’d probably do really well.
Malware, Viruses, Rootkits and RATS
let’s chat about malware. Malware is this big umbrella term for all the nasty programs that are designed to cause harm. It’s got a bunch of different types, and we’re gonna run through some of the main ones. But we’ll also talk about the ones you really need to watch out for right now.
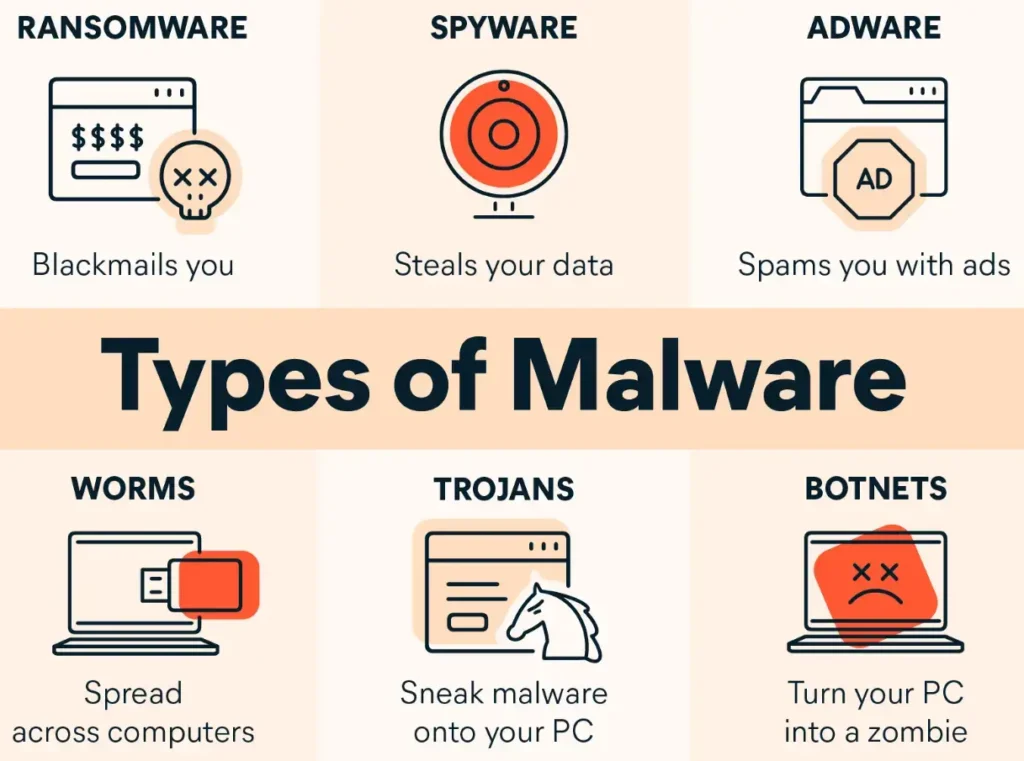
In addition to these, there are a number of other types of Malware:
- Trojan
- Macro Virus
- Stealth Virus
- Firmware Rootkit
- Remote Access Tool (RAT)
- Polymorphic Virus
- OS Rootkit
- Worms
- Bots & Zombies
- Self-garbling Virus
- Key logger
So, first up, we’ve got Macro viruses. These little buggers are written in macro languages, like VBS, and they can hide out in documents like Word or Excel. When you open the doc, pow, the virus runs.
Next, there are Stealth viruses. These guys are sneaky; they hide their tracks so antivirus software can’t find them. They’re like magicians, making things disappear.
Polymorphic viruses are crafty too. They change their shape every time they infect something, so they’re hard to catch with traditional antivirus tools.
Then there are self-garbling viruses, which mess with their own code to avoid being spotted by antivirus signatures.
Bots or Zombies, these are hacked devices under a hacker’s control. If your machine gets compromised, it could become part of a botnet.
Worms are viruses that just keep spreading from machine to machine, like a chain letter gone bad.
Rootkits are the worst. They bury deep into your operating system’s kernel, hiding from everything.
And Firmware Rootkits? They’re the nightmare scenario. They’re in your hardware, like your hard drive’s firmware, and even formatting won’t get rid of them. That’s some serious NSA-level stuff.
Key loggers, they log your keystrokes. Trojan horses pretend to be something else but are actually malware. And RATs, or Remote Access Tools, let hackers control your machine from afar. Think of it like a hacker’s version of Team Viewer.
Now, you don’t need to memorize all these types, but there are a few you should definitely know about. Ransomware is a big one. It sneaks in, encrypts all your files, and holds them hostage until you pay up. CryptoWall, CTB-locker, TorrentLocker – these are the bad guys you don’t want to meet.
Another one to watch out for is Malvertisement. That’s when online ads are infected with malware. You think you’re just browsing the web, and boom, you’re hit with a malicious ad.
And then there are Drive-by Attacks. Just visiting a website can get you infected if it’s got the right (or wrong) kind of code on it. So, don’t think you’re safe just because you stick to known sites. Even big-name sites can get hacked, like Jamie Oliver’s website, which got hit three times. Not cool.
Spyware, Adware, Scareware, PUPs & Browser hijacking
You know spyware, right? It’s like that pesky little program that hangs out on your computer, collecting info and sending it back to the bad guys. They’re not out to cause direct harm; they just want to invade your privacy and mess with your life. Spyware is basically malware that’s all about gathering intel.
Then there’s adware. It’s like that annoying friend who won’t stop showing you ads. Some people call it a type of spyware. It’s just software that forces ads on you, and there are tons of variants. One of the worst is Cool Web Search. It takes over your search engine, shows you ads, and even redirects you to places you didn’t want to go. And it fights back when you try to remove it, making it a real pain to get rid of.
Oh, and don’t forget about browser hijacking. That’s when malware or adware takes control of your browser. It’s a common term you’ll hear, and it’s a big reason to be careful during software installs. Always choose custom installations and watch out for those sneaky optional installs.
Lenovo had a big mess when they preinstalled Superfish adware. Not only was it showing you ads, but it also messed with your browser’s encryption, which is a major no-no.
And then there’s scareware. It’s like that fake security software that tries to scare you into thinking your computer’s infected when it’s not. They just want your money to ‘fix’ the fake problem. It’s a total scam.
Finally, there are PUPs, or Potentially Unwanted Programs. These are programs that tag along with software installs, and most of the time, you really don’t want them. They’re annoying and often bundled in without you knowing.
So, the takeaway is, be cautious with what you install, and always read the fine print during those software installations.
What is Phishing, Vishing and SMShing
Phishing, vishing, and smishing. Phishing is basically when someone tries to trick you into clicking a link or running some malware. They might be after your sensitive info like passwords, usernames, credit card details, or they might just want to get into your online accounts. Phishing is super common and effective because it’s easy to do, doesn’t cost much, and can really pay off for the bad guys. So, you’ve got to be on the lookout for this stuff.
Even big companies with all their security training, about 30% of people still fall for these tricks. Some countries are worse at clicking on stuff they shouldn’t, others are better, but the bottom line is, it’s hard to train people not to click on the wrong things. Phishing usually happens through fake emails or instant messages, directing you to a site that looks legit but isn’t. It’s all about exploiting human weakness and the fact that web tech isn’t super secure. For example, emails can be easily faked to look like they’re from someone they’re not.
Now, let’s look at some tricks they use to get you to click. One big one is link manipulation. They use subdomains, misspelled domains, and other sneaky stuff to make the link look real. Take a look at this email I put together. See these links that look like they’re for Google and Microsoft? They’re fake. One uses a subdomain, the other uses subdirectories, and the Microsoft one even has a typo in it.
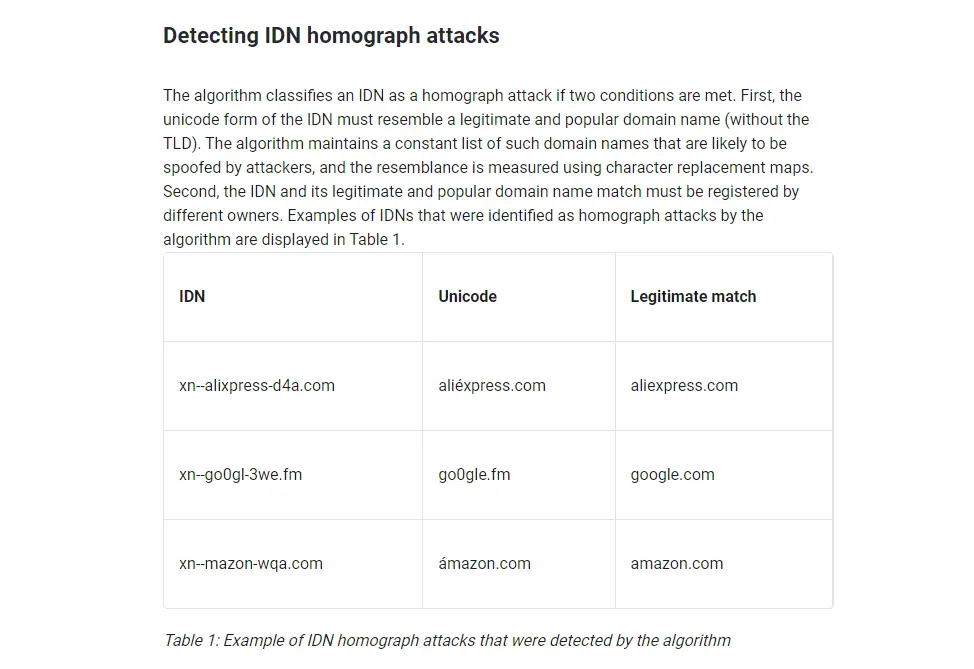
Then there’s IDN homographic attacks, where they use international domain names to create confusion. Look at these examples with different characters that look almost the same. And hidden URLs, where they use HTML to hide the real destination of the link. So, you think you’re clicking on one thing, but you’re actually being sent somewhere totally different.
Now, besides link manipulation, there’s also covert URL redirects that use vulnerabilities like Cross-Site Scripting and Cross-Site Request Forgery. They can combine these with URL manipulation to really mess with you.
<h4>Hidden URLs</h4> <a href=”<http://google.com.stationx.net>”>Click Here</a> <br> <a href=”<http://google.com.stationx.net>”><http://google.com.stationx.net></a>
www.gosaamer-threads.com/form/user.cgi?url=”><script>alert(“XSS vulnerability”)</sc...
..ds.com/forum/user.cgi?url=”><script>alert(“XSS vulnerability”)</script>”&from=rate...
.../user.cgi?url=”><iframe%20src=”<http://www.offsce.com/linksql.html%20sc> rolling=”No”%20align=”MIDDLE”%20width=”100%”%20height=”3000”&20frameborder= ”No”>
</iframe><!--&from=rate
Finally, there are two more types of phishing to watch out for: vishing and smishing. Vishing is voice phishing over the phone, and smishing is phishing through SMS or text messages. They’re trying to trick you the same way as email phishing, just through different channels. They might pretend to be from Microsoft or your bank, trying to get you to download something bad or give up your info. These calls and texts can be pretty convincing, and some people do fall for them.
So, that’s phishing, vishing, and smishing. Keep your eyes open and your guard up, ’cause these scams are everywhere.
Spamming & Doxing
spamming and doxing. Spam, as you probably know, is all those unwanted messages you get, usually in your email, like this one trying to sell you meds or some other stuff you don’t need. But it’s not just emails; it’s instant messages, forum posts, social media, even text messages and blog comments – basically, anywhere they can stick their ads.
You’d think no one would fall for it, right? But spamming is cheap to do, and if you send out millions of messages, even a tiny percentage of people responding can make it worth the spammer’s while. The email systems we use today were built back when everyone was more trusting, so they don’t have great defenses against spam. We’ll talk more about email security later, but for now, just remember: if you didn’t ask for it, be wary.
Now, doxing is a whole different ball game. Doxing is when someone digs up personal info on you – could be you, an organization, whatever – usually to cause trouble. Like, they might embarrassment you, try to blackmail you, harass you, or just generally make your life miserable by spreading your info around or threatening to do so.
If someone gets doxed, it means their private stuff has been made public. Doxing can be as simple as Googling someone or checking public records. There’s a lot of info out there that people don’t even realize is public. You can find stuff on social media, forums, even by calling phone companies or looking up IP addresses. It can involve tricking people into giving up info, or it could go as far as hacking into someone’s computer.
We’ve seen high-profile cases like Anonymous outing Klan members and Trump reading a senator’s phone number aloud. The ethics of doxing are pretty shady, to say the least.
Social engineering – Scams, cons, tricks and fraud
We’re gonna chat about social engineering scams, cons, tricks, and fraud. The Consumer Fraud Report is saying these are the scams you gotta watch out for right now. We call ’em Social Engineering Attacks in the security biz. It’s all about exploiting human weaknesses, ya know?
First off, we got Internet Merchant Scams. You order something online, and guess what? It never shows up, or it’s a piece of junk, or it’s just plain broken. Super common. Then there’s phishing and spoofed emails – we’ve talked about these. They pretend to be from some legit company or government agency, trying to get you to click a link, give up your info, or download some nasty malware.
Next, we got fake prizes, lotteries, and free gifts. You get an email saying you won, but you gotta pay a tiny fee to claim it. Legit lotteries don’t work like that, folks. That’s called Advanced Fee Fraud – it’s a classic con.
How about fake cheque payments? You sell something online, and boom, you get a phony cheque. Then there are recovery and refund companies. They say they’ll get your money back from a scam, but it’s just another scam. And don’t even get me started on computer performance scams. They say your PC’s got issues, but they just want your cash.
Scholarship and student loan scams are out there too. They promise to find you money for school, but they just take your money and run. Online dating scams? Watch out for those fake profiles. They’ll say they need cash for an emergency. I know a couple of people who fell for that.
Facebook Fake Friends scam is another one. You get a friend request from someone you thought you were already friends with. If you accept, you might just be friending a scammer. And with eBay and auction seller scams, they pose as buyers and trick sellers into shipping goods without payment.
My mom almost got scammed when she was selling something, but she knew better because of me. These scammers can be really pushy and aggressive. They’re usually not even in the same country as the item, and they ask for a ton of personal info. Don’t give them anything, not even your full name.
To stay in the know about scams, check out the Consumer Fraud Reporting website or Action Fraud if you’re in the UK. Throughout this course, we’ll talk about how to avoid these scams by changing your behavior and using tech security controls.
Darknets, Dark Markets and Exploit kits
Let’s chat about the Darknet. You know, that place on the internet that’s all hush-hush and hidden from the average Joe. Yeah, it’s not just for the cool kids—it’s used by governments, the military, companies, and even your average Joe who wants to keep things on the down-low. But, of course, it’s also a hotspot for the criminal crowd who values their privacy a bit too much.
Now, the Darknet isn’t some magical place you can’t find. It’s just a bit more hidden, like a secret club that you need a special password to get into. You can’t just Google your way into it—you need special software, like Tor, which is kind of like a secret decoder ring for the internet.
In the Darknet, there are all sorts of markets and forums where folks trade in everything from the shady to the downright illegal. Think of it as an eBay for the underworld. You can find malware, remote access tools, and even exploit kits that can turn your computer into a puppet for some hacker’s sick show.
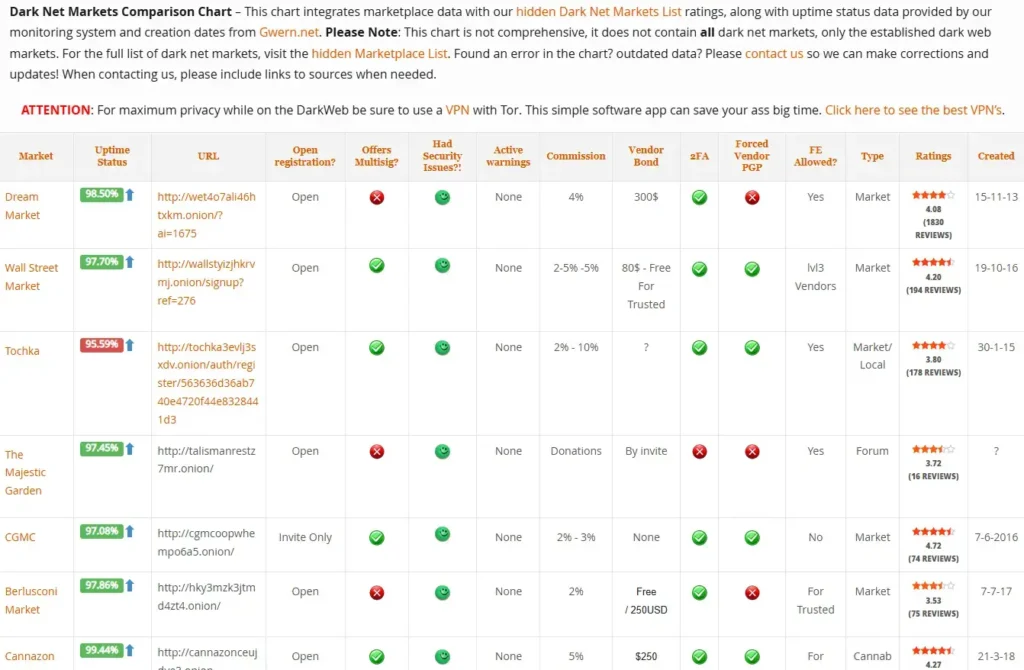
And these exploit kits, they’re like do-it-yourself crime kits. You can buy one, upload it to a hacked site, and then just sit back and wait for some poor unsuspecting soul to visit the site and get owned by your malware. It’s like a digital bear trap, but way more dangerous.
But hey, don’t freak out. If you keep your software up to date and have good security practices, you can avoid most of these pitfalls. It’s like wearing a suit of armor before you go wandering into the dark alleys of the internet.
And the cost of these exploit kits? Well, they’re getting cheaper and more accessible, which means that even the script kiddies with no real skills can cause some serious damage. It’s like giving a monkey a machine gun—hilarity does not ensue.
So, the Darknet is a wild west of the internet, and it’s growing. It’s a marketplace for mayhem, and the bad guys are getting more tools every day. But with the right knowledge and precautions, you can stay safe and sound.
Governments, spies and secret stuff – part I
Let’s talk about the big brothers watching—governments, spies, and all that hush-hush stuff. Depending on who you are and where you live, your government might be more than a little interested in your online activities. If you’re cool with what your government does, you can probably skip this. But if you’re, say, speaking out against human rights abuses, or you’re part of a group that’s targeted, like the LGBTQ+ community in some countries, or you’re just someone who wants to keep your business to yourself, then this is for you.
We know from Snowden and others that mass surveillance is a real thing. It’s not just one or two countries—it’s happening across the globe. The Five Eyes—UK, US, Australia, Canada, and New Zealand—are all in on this, sharing intel and spying on each other’s citizens to get around those pesky domestic spying laws. They’ve even got pals in the Nine Eyes and Fourteen Eyes, expanding their snooping network.
These agencies aren’t just peeking through your window; they’re tapping phones, reading emails, tracking movements, and even turning on your webcam when you’re not looking. And they’re building mega data centers in places like Utah to store all the info they collect. It’s a lot, and it’s not just on the bad guys—it’s on everyone.
So, you might want to ask yourself: Do you want everything you do online to be recorded and potentially exposed? Can you trust that all the people and organizations with access to this data will always have your best interests at heart? And is mass surveillance worth trading away personal privacy?
Governments, spies and secret stuff – part II
There’s been a brief overview above, so now, let’s get into the governments and spies that may not like you very much. They may be using some pretty advanced technology to spy on you and even hack into your devices. It’s not just the bad guys in the dark corners of the Internet that have this type of gear; your friendly neighborhood spy agency may also carry some serious surveillance tools.
You know those cool gadgets from the movies that can listen in on any conversation? Yeah, they’re real, and they’re tiny, so small they can run for years on practically no power. And since they don’t send out any signals, those cool bug sweeping scenes you see in the movies? Totally useless against these. They can even be made with stuff you can buy at any electronics store, so they’re almost impossible to track down.
Let me give you an example: Loudauto. It’s basically a listening device that uses radar to pick up sounds from a room. And it only works when someone sends a beam of radio waves to it. So it’s almost impossible to detect because it’s not sending out any signals on its own.
Or how about this one: a little gadget that sits inside your keyboard and records every keystroke. Same deal, it’s passive, doesn’t send out signals, so it’s tough to find.
And then there’s the really scary stuff, like Jetplow, which is a tool that can get into your router or firewall and hang out there, even if you wipe your system clean. Or Iratemonk, which implants itself in your hard drive’s firmware, so no amount of formatting or reinstalling is going to get rid of it.
Oh, and let’s not forget about the guys who will set up a fake cell tower to track you and hack into your phone. These aren’t just some random tools; these are things that governments have actually used, and if you’re a target, you better believe they will use them.
Regulating encryption, mandating insecurity and legalizing spying
Now, let’s talk about a big issue that’s affecting our online security, privacy, and anonymity: our own governments. Yep, the people who are supposed to protect us might be the ones watching our every move online. It’s a double-edged sword because while they say they’re going after the bad guys, they might end up weakening our security for everyone.
Think about it. Encryption is what keeps our data safe, right? But some governments want to weaken it, saying they need access to our data to catch the real bad guys. The problem is, if encryption is weakened, then it’s not just the terrorists who’ll find a way around it – our personal data could be at risk too. And once that horse is out of the stable, there’s no putting it back.
Plus, there’s no practical way to make this work. Even top experts are saying it’s not possible to create a system that lets the good guys in while keeping the bad guys out without compromising everyone’s security. It’s like trying to build a house with a secret door for the police, but that door is also an invitation for burglars.
And let’s not forget about mass surveillance. It’s not just about catching criminals; it’s about giving up our freedom. If we’re always being watched, are we really free? That’s what terrorists want – to take away our freedom. And by creating a world where we’re constantly monitored, we’re playing right into their hands.
So, what can we do? Well, we can start by educating ourselves and others about the importance of encryption and privacy. We can also support organizations that are fighting for our right to privacy. Because in the end, it’s not just about protecting our data; it’s about protecting our freedom.
Trust & Backdoors
Encryption – that’s the tech that keeps our secrets safe, right? But here’s the twist: some governments want to water it down. They say they need to snoop on our data to catch the real baddies. The catch? If we weaken encryption, it’s not just the terrorists who’ll find a workaround – our personal info could be up for grabs too. And once that door’s open, it ain’t closing.
Plus, let’s get real. There’s no practical way to build a system that lets only the good guys in and keeps the bad guys out without putting everyone’s security at risk. It’s like having a backdoor for the cops in your house – which also gives burglars an open invitation.
And what about mass surveillance? It’s not just about nabbing crooks; it’s about giving up our liberties. If we’re under the microscope all the time, are we truly free? That’s what the terrorists are after – to strip us of our freedom. By living in a fishbowl, we’re playing into their hands.
So, what’s the plan? For starters, we can learn and spread the word about why encryption and privacy matter. We can back groups that are in the trenches fighting for our privacy rights. Because at the end of the day, it’s about more than just keeping our data safe; it’s about safeguarding our freedom.
Censorship
Censorship isn’t just some far-off thing that happens in other countries. It’s happening in the West too, and it’s not always obvious. You know how in Canada, the bigwigs at the Supreme Court said a company had to scrub their competition’s name from search results, even outside Canada? Or how about in Europe, where a guy got Google to wipe away search results that made him look bad? That’s called the “Right to Be Forgotten,” and it’s a big deal.
Then there’s the model from Argentina who made Google and Yahoo take down pictures linking her to adult sites. In the UK, people can’t just visit any website they want; the internet providers filter what you can see, and you have to ask to see the blocked stuff. In the US, the government can’t just block stuff directly, but they’ve tried. Instead, they often get private companies to do the dirty work, like making them take down content or face legal trouble.
All this means that what you can see online might be getting more limited, and it’s not just in other countries—it’s happening in the West too. So, depending on who you are and where you’re at, this could be a problem for you.
Security News and Alerts – Stay Informed
In the world of cybersecurity, things move fast. New threats pop up all the time, and it’s crucial to stay in the loop. To help you keep your finger on the pulse of the latest security and privacy news.
All you need to do is sign up here, and make sure to use the same username you used to access the course. That way, I can keep track of who’s who and make sure you get the updates that matter most to you. By joining the list, you’ll be among the first to know about any developments that could impact your security, privacy, and anonymity.
So don’t miss out! Stay informed, stay safe, and let’s keep an eye on the ever-changing landscape of cybersecurity together.
Conclusion
At the present time, we’ve covered a wide range of topics essential for understanding the current threat and vulnerability landscape. We’ve explored the importance of security, the value of a hack, and the top three things you need to stay safe online. We’ve delved into security bugs and vulnerabilities, the roles of hackers, crackers, and cybercriminals, and the various types of malware, including viruses, rootkits, and RATs. We’ve also discussed spyware, adware, scareware, PUPs, and browser hijacking, as well as phishing, vishing, and smishing.
Additionally, we’ve touched on spamming, doxing, social engineering, darknets, dark markets, exploit kits, and the involvement of governments and spies in online surveillance. We’ve examined the regulation of encryption, the concept of trust and backdoors, and the issue of censorship. Finally, we’ve highlighted the importance of staying informed through security news and alerts.


