Table of Contents
This article focuses on how to best use authentication methods, including passwords, and multi-factor authentication (e.g., soft and hard tokens). You will learn how to use the best password managers and how passwords are cracked, as well as how to mitigate cracking by using better hashing and key expansion techniques, and choosing good passwords.
The Importance of Password Security
The Challenge of Passwords
- Passwords are a nuisance for many people. We are supposed to have strong passwords for every site we visit, for our email, for our laptop, for our work, and these are all supposed to be different and strong passwords. It’s simply not possible.
- Yet, at the same time, passwords are one of the weakest links in security, so we need to be using different and yet strong passwords.
Common Ways Passwords Are Compromised
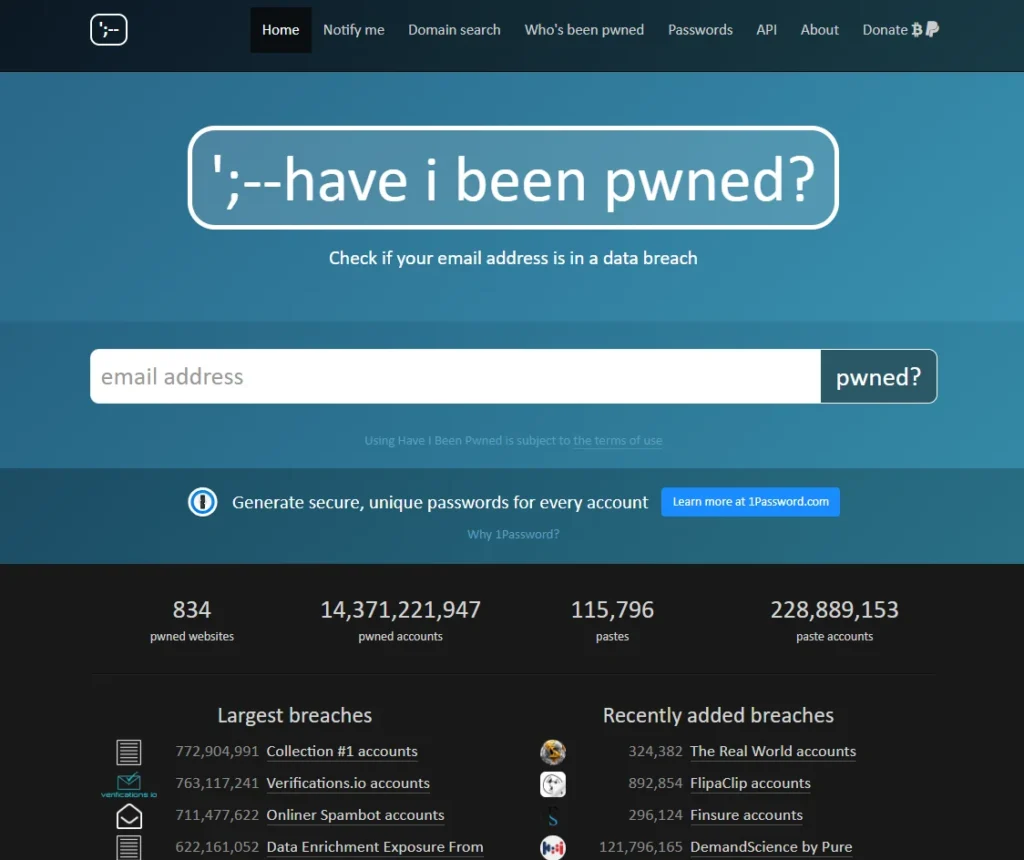
- The most likely occurrence of your password being compromised would be via a website that has been hacked, which you have registered on and they have stored your information and password in a way that has made it possible that it could be stolen.
- You can check if any of your passwords have been compromised by visiting haveibeenpwned.com.
Frequency of Website Hacks
- Websites being hacked is an unfortunate daily occurrence.
- Even large companies do a far from brilliant job of security because security doesn’t make money.
Password Security
- Your password is as secure as the least secure place it is being used, so you must assume that any password you use is known by that site or service.
- Sharing passwords is risky because if a weak site gets hacked and they have your email address and password, they can try that out on other sites.
Automated Attacks
- All these operations are automated and done with scripts, checking all the top sites and places where they can take advantage of those email address, username, password combinations.
- Phishing attacks are another common method of compromising your password.
Password Transmission Over the Network
- Your password could be captured in transit as it goes over the network and the internet to its destination.
- Passwords should always be sent encrypted or hashed to prevent interception.
Password Cracking Methods
Three Main Ways to Crack Passwords
- Dictionary Attacks: Attempt to crack passwords by trying all words from a massive dictionary of words, including common passwords that humans use.
- Brute Force Attacks: Try every possible password combination using every possible character combination.
- Hybrid Attacks: Combine the psychology of human behavior with dictionary and brute force attacks.
Detailed Password Cracking Methods
- Combination Attacks: Append each word of a dictionary to each word in a dictionary to generate possible password combinations.
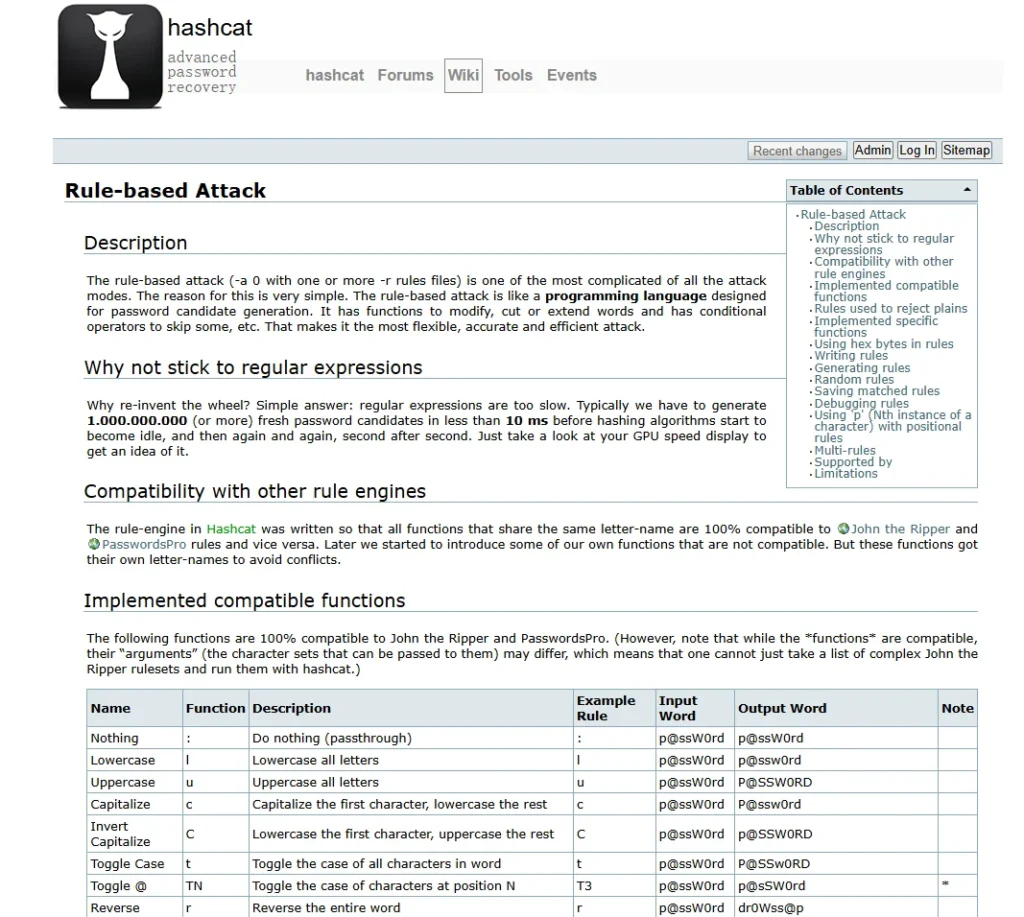
- Rule-Based Attacks: Design rules based on input words from a dictionary to produce variants of those words.
- Password Pattern Analysis: After cracking a percentage of passwords, look for patterns such as password length, character set, complexity, and mask to refine rules.
Online vs. Offline Attacks
- Online Attacks: The attacker interacts with the crypto system, usually a dictionary attack against a network-based service like SSH login or website login.
- Offline Attacks: The attacker has access to password hashes without interacting with the crypto system, such as cracking the Ashley Madison website.
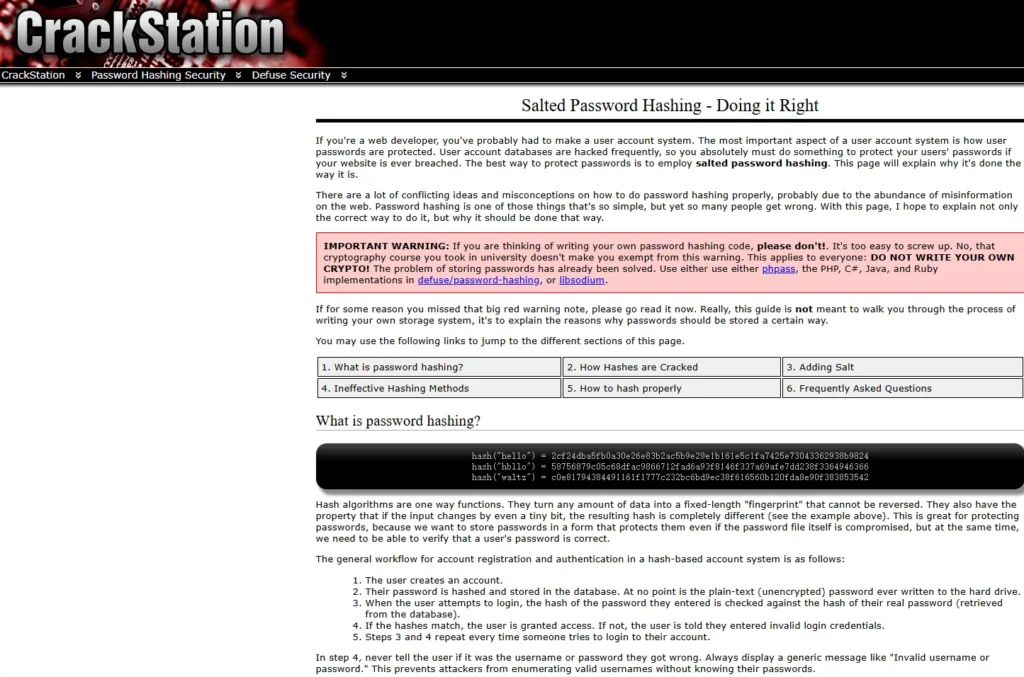
Hashing and Password Storage
- Storing passwords in plain text is insecure; instead, use a hash function to convert passwords to a fixed-length string.
- Hash functions are one-way, so they cannot be reversed to obtain the password, only cracked.
- To confirm login, either convert the password to a hash and compare it, or compare the user’s hashed password directly.
Salt and Password Cracking
- Salt is a random and non-secret value concatenated with the password hash to prevent the use of rainbow tables for quick cracking.
- Salt is more useful for protecting a large number of passwords but less effective for individual or small numbers of hashes.
Key Stretching Functions
- Key stretching functions (like PBKDF2, bcrypt, and scrypt) increase the time required for brute force attacks by repeatedly invoking a cryptographic hash.
- Storing passwords using key stretching functions makes them difficult to crack even if stolen.
- PBKDF2 Hash Generator
Hash Encryption
- To enhance security further, encrypt the hash value with a secret key before storing it in the database.
- Hardware Security Modules (HSMs) can be used to store the master password or perform password processing to prevent leaks.
Keyed Hash Algorithms
- Use keyed hash algorithms (like HMAC) to include a secret key in the hash value for additional security.
Complexity of Password Hashing
- Even security professionals often misunderstand the nuances of password hashing, leading to the use of weak hash functions for storing passwords.
- Therefore, it’s important not to share passwords across sites, especially for accounts you care about.
Sample password hash encoding strings [Openwall Community Wiki]
Methods of Stealing Password Hashes
Ways to Steal Password Hashes
- Password hashes can be stolen in various ways, such as through SQL injection attacks on a website that extracts the hashes from the database.
- A SQL injection attack occurs when a website does not validate the input data it receives, allowing you to send direct queries to the database and request the password hashes.
Examples of Hash Leaks
- Here is a website that collects hash dumps from compromised websites.
- You can see LinkedIn, eHarmony, and other dating websites, along with the hashing algorithms they use.
- MD5 and SHA-1 are not good choices, and even large websites can make mistakes.
- The site provides analysis that you can use to adjust your cracking process.
Extracting Hashes from Operating Systems
- If you have local access to the drive, you can extract hashes from the operating system.
- This can be done by mounting the hard drive in another operating system or using a live CD that can mount the file system.
- For example, in Windows, LM hashes, NT hashes, and NTLM hashes for user passwords are stored in the Security Account Manager (SAM), which is essentially just a file, and these hashes can be extracted with various tools.
Advantages of Offline Attacks
- Offline attacks do not interact with the crypto system, so they cannot defend themselves.
- Hashes are just a bunch of characters in a file and cannot defend themselves.
- Offline attacks can be much faster than online attacks, reaching billions or even trillions of guesses per second with powerful GPU crackers.
Password Cracking Tools
- In Kali, there are many password cracking tools available, such as HashCat, John the Ripper, Ofcrack, and more.
- HashCat is a powerful password cracking tool that can be used for various attacks.
The Cracking Process
- You need some hashes to crack first, so I’ve downloaded some public hashes from a random old cracking site.
- Use the hash ID tool to identify the type of hash.
- Use a dictionary attack as part of a hybrid attack.
- You can add rules to modify the words in the dictionary.
- HashCat can use a rules file to apply these rules.
- In just a few seconds, the cracking tool can crack a large number of hashes.
Online Cracking
- You can try online cracking, and there are many websites that offer online cracking services.
- Online cracking is fast and easy to rent powerful servers for short periods of time.
- If the right hash, key derivation function, key length, and password are chosen, it is unlikely to be cracked even with powerful servers.
Relay Attacks
- Sometimes you don’t need to crack the hash; you can capture it and relay it in a relay attack.
- If you are a man in the middle, instead of cracking it, you can just forward it on after capturing it, allowing you to access the destination.
- Windows LM or NTLM hashes can be relayed due to an authentication flaw, which can be done with Metasploit in Kali.
The Security of Operating System Passwords
Risk of Physical Access
- Operating system passwords offer virtually no protection against someone with physical access to the device.
- The password can be bypassed simply by booting the device using another operating system and examining the files.
Methods to Bypass Passwords
- You can use a live CD to do this, or just remove the hard drive and connect it to another machine.
- Operating system passwords don’t even need to be cracked in the conventional sense if you have physical access.
- The hash can be simply replaced, creating a new working password to access the operating system.
Bypassing Passwords on Linux Systems
- As an example, with Linux, you just boot it up, edit the grub parameters from recovery mode to a bash shell.
- Remount the root partition as read-write and use the passwd command to change the password.
Bypassing Passwords on Windows Systems
- In Windows, choose the recovery software of your choice to do this.
- There are quite a few options available, and they are usually a live CD or a USB that you boot from.
- Don’t bother with the versions that crack the password, like offcrack, as that’s really not necessary.
- Use one that simply swaps the password hash for a new one, which takes just a couple of seconds.
Bypassing Passwords on Mac OS X Systems
- Mac OS X is just as simple, and you can do a search for tools that can recover the password.
Limitations of Operating System Passwords
- The point is that operating system passwords provide no protection against someone who has physical access to your device, even if you use a very complex password.
- To slow down the process of swapping or cracking the password, you can add two-factor authentication to the operating system login.
- For example, Ubiqui supports Windows, Mac, and Linux for two-factor authentication, but this is only going to slow them down because it means they can’t use the conventional ways.
- It will still be relatively trivial to bypass for anyone with physical access.
Effectiveness of Full Disk Encryption
- What does work is full disk encryption to protect your operating system.
- Then, your password is very important because it is used as the key for your full disk encryption.
- More on that in the section on encryption.
The Security of Password Managers
Functionality of Password Managers
- Password managers are secure vaults for sensitive data, such as usernames, passwords, credit card information, PIN numbers, access codes, and they allow you to have both strong and unique passwords.
- When you use them, you often won’t even know what your password is because you choose a randomly generated password and use the password manager to input that password into the password field.
- Sometimes this is done by copy and paste, other times by some automated process.
Security of Password Managers
- Password managers are locked using a master password that you enter into the password manager to unlock access, decrypt the data storage of the password manager, and grant you access to the passwords.
- Obviously, you need to remember this master password.
- The master password must be very strong and memorable.
- We will discuss shortly how to create strong and memorable passwords.
Storage Methods of Password Managers
- Some password managers store their data on your local device, which is the only place they store it.
- You can refer to these as local password managers.
- Others sync in the cloud so you can share the information between devices.
- Some special ones don’t even store the passwords at all; they generate them, which I will explain in a moment.
Recommended Password Managers
- Password managers are a great tool that everyone should use.
- Even though they create a point of attack, they are much better than having weak and shared passwords.
- Using a password manager is the least risky option compared to weak and shared passwords.
- Now, I will take you through some of the password managers I recommend, starting with the one with the least attack surface and moving to the one with the most functionality.
- As with most things in security, it’s a balance between functionality and security.
Spectre: Passwords, Privacy-first
MasterPassword: A Stateless Password Generator
MasterPassword is a free tool that is available for various platforms, including iPhone, Mac, and desktop systems that can run Java. It can be downloaded via Homebrew on Mac and is also available in a Java version, a terminal version, an Android beta, and a web version.
Stateless Password Generation
- MasterPassword is a stateless password generator, meaning it does not store passwords in the applications. Instead, passwords are generated on demand based on the user’s name, the site they enter, and their master password.
- The tool uses sCrypt-based key derivation to slow down the cracking process, enhancing password security.
Demonstration
- The Java app, which is similar on Windows and Linux, allows users to input their username and master password. Users can also choose to go incognito, which does not store any information.
- Upon login, the app auto-generates passwords based on the user’s name, the site they enter, and their master password. Users can customize the password length and type, and the generated password can be copied and pasted into the required field.
- The iPhone version of the app also generates the same password based on the user’s name, site, and master password. Users can remember the site, change the default password type, add an avatar, and log out. However, saving the password is not recommended for security reasons.
Security Features
- MasterPassword does not require syncing, backups, or internet access, as it does not store any passwords. This reduces the attack surface significantly.
- The algorithm and design of MasterPassword are well-inspected and considered secure.
Limitations
- MasterPassword is primarily designed for password management and does not support storing usernames, filling forms, making secure notes, or storing credit card information, which other password managers offer.
- Users must remember the security questions they set up, as the tool does not store this information.
Recommendations
- MasterPassword is recommended for users who prioritize a low attack surface and do not require additional features like form filling or secure note storage.
- To further enhance security against local attacks and keyloggers, users can run MasterPassword in a secure virtual machine.
- It is important to note that MasterPassword does not support two-factor authentication, which could provide an additional layer of security.
Recommendations for Local Password Managers
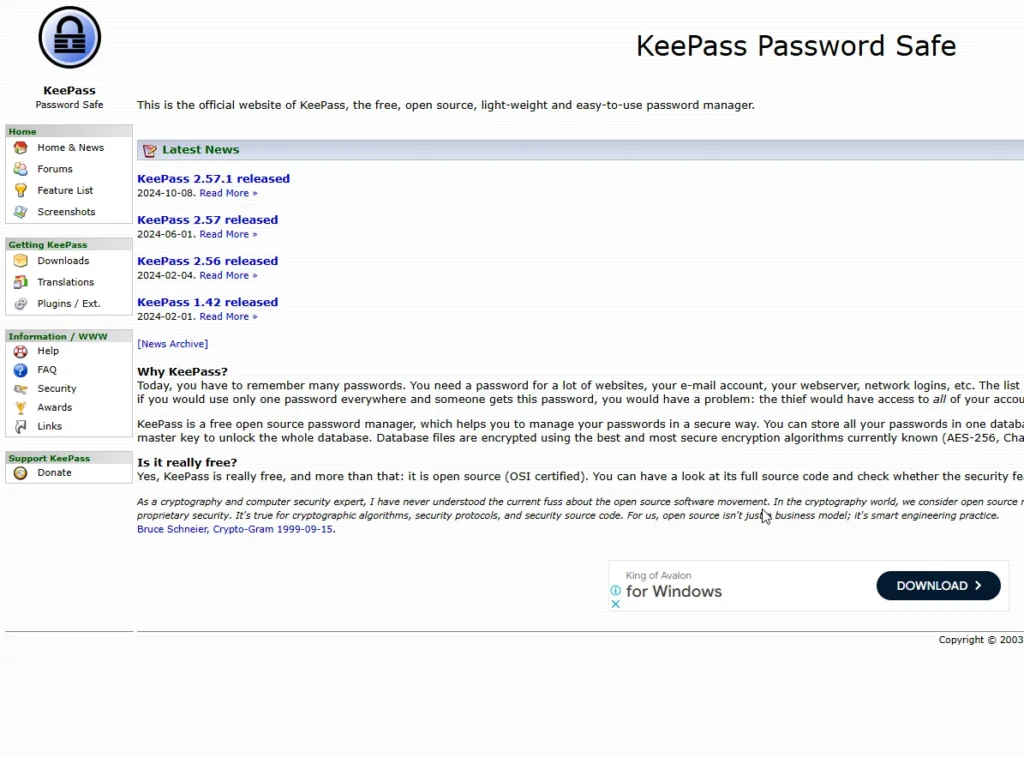
KeePass 2.x and KeePass X
- My recommendation for a local password manager is KeePass 2.x and KeePass X. KeePass, as you can see here, is the original for Windows, and it does actually work on Linux and Mac OS X with Mono.
KeePass X
- KeePass X is a fork of KeePass for Linux and Mac OS X, also free and open source.
KeePassXC
- In addition to KeePass and KeePass X, there is also KeePassXC, a community fork of KeePass X, a native cross-platform port of KeePass. KeePassXC is available for Linux, Windows, and Mac OS.
KeePass User Interface
- Let’s look at the KeePass GUI. This is what it looks like. First, you need to open a database, or create one if you’re just starting to use it.
- After opening, you need to enter the master password to decrypt the database, which obviously needs to be very strong.
- Here, you can see that key files are also available. For example, you could have an MP3 file that must also be present to log in.
- This is a two-factor authentication option.
Database Settings
- Once logged in, you can right-click and add entries here.
- KeePass auto-generates a password for you based on the settings you have here, and I’ll talk more about what these settings should be in its own section.
- Then you can save, right-click, copy the username and password, and paste them wherever you need.
Security
- KeePass uses AES-256 and SHA-256 to store the master password. The Pro version has other options as well that you can select, but the default settings are perfectly fine.
- To generate the final 256-bit key used for the block cipher, KeePass first hashes the user’s password using SHA-256, encrypts the result 6,000 times using the AES algorithm, and then hashes it again using SHA-256. I would suggest changing this to a random number between 10,000 and 20,000 to slow down cracking.
- If you use key files as an additional authentication factor, the hash of the master password is concatenated with the key file bytes and the resulting byte string is hashed with SHA-256 again. It also supports YubiKey for authentication.
- There are also plugins you can download and install, which you can see some of here. With these plugins, KeePass can actually become more than a local password manager. It can actually do cloud syncing. You can see support for Google Drive, Dropbox, and other online storage providers. Use it at your own discretion.
- I’m really only talking about using this as a local password manager. But if you were to sync it or back it up into the cloud using your own servers, that would add an extra layer of mitigation. And of course, because it is encrypted, even though it’s stored on Dropbox for example, Dropbox shouldn’t be able to get access to it. But it provides that opportunity and increases the attack surface. So it may be that syncing in the cloud using this is viable for you because you believe that’s an acceptable risk.
- Without this, there is no syncing between devices, obviously. So that can be a problem as you go from device to device because this is fundamentally a local password manager only.
- Of course, if you’re not doing syncing, and even if you are doing syncing, you should also do backups of the database yourself, a separate backup to the syncing, because the file could become corrupt and then synced, and then the synced file is corrupt, so you need a separate backup, or it could be deleted, and then it’s synced deleted. So please do a backup.
Security Recommendations
- Obviously, if an attacker is present on your device using a keylogger or other sort of malware, they will be able to capture the master password, which would compromise your database.
- Optimally, you would want to install KeePass in a virtual machine to provide the extra layer of isolation, or in cubes like as a separate VM to just give it that extra isolation.
- You may even store the file on an encrypted USB or some other form of physical isolation.
Recommendations for Cloud-Based Password Managers
LastPass
- Next, I recommend LastPass as a cloud-based password manager. It provides the most functionality of the password managers we have gone through so far and that I recommend, but it also has the greatest attack surface. This is because it integrates with the web browser and syncs across devices using the cloud, using the LastPass servers. Your private encrypted passwords and data is stored in the cloud on LastPass servers, making it much more convenient and easy to use. There’s no copying and pasting between the password manager and websites when you use this, and you can store every bit of information that you like, like credit cards, usernames, emails, pins, making it extremely convenient. It’s cross-platform for all the major browsers by edge, but I’m sure that will change soon, including Ice for Debian and portable browsers. This is the login for it here and the icon in the browser that you get. Let’s have a look at the difference because there are premiums and free versions. Premium costs around $12 for the year and free is free.
Premium vs. Free Versions
- And here are the major differences. With the free version, there’s no unlimited syncing across all mobile and desktop devices. That’s one of the major disadvantages of the free version, and some of the multifactor authentication methods are not available.
Competitors and Functionality
- It has lots of competitors in terms of being a cloud-based password manager and indeed just being a password manager. Here we can see KeePass and KeePassX, which we’ve gone through, and you can see here the delivery format of various password managers, cloud, cloud, cloud.
Demo of LastPass
- So let me give you a quick demo of this one. So once you have installed it, you’re going to get this icon here in your browser. As you install it, you can create an account or you can create an account here. And then you just have the option to log in with whatever email address you use and an extremely strong password for your master password. We’re going to talk about creating strong passwords in this section. So let me log in. I do not have a strong password for this demo. So there we are. We’re logged in. This goes red and we can see all of the options here.
Password Vault and Features
- Now let’s go on my LastPass vault. On the free account, you get this kind of annoying advert here on premium. That is gone, so effectively you can ignore all of that. And here are your various sites that you can log in. You can change the view. It looks like this, looks like this. It can be in different folders. I’m quite zoomed in here so that you can see, but on a normal monitor it displays quite well. And so you would try and find somewhere you want to log into, so Amazon, that will pop up, click launch, and that auto logs you into that site. It’s not logged in because that’s not the correct username and password. And if you were just browsing around, you would press here, type Amazon, and then just click here, and you’d log in.
Editing and Managing Entries
- You can edit by clicking on there. You can copy the username, password, URL, and here’s edit, delete. Click on edit. You can see we can change all the various information that we’ve stored about it. Let’s go back to the password vault and you can do the same editing here. You can see the password. You can generate a password. And a cool feature, you can auto change the password on sites that LastPass has developed scripting to auto log in for you and change the password for you all automated. So that’s actually pretty good.
Additional Features
- Go here, you can see we’ve got the same options here as we have over here. And these are our sites. You can put them into separate folders for each of your different sites. You’ve got secure notes. So literally, you know, you can just write a note about something. And form fills for automatically filling in forms, credit cards, let’s go over here. Secure notes. We can just add one here, add whatever we’re going to say. You can also have attachments, which is quite good. Form fills. Add those. So you can see you can put in the sort of information you want to add into forms. I actually find the form fills and credit storage actually not that great. The functionality is better in other password managers.
Sharing and Emergency Access
- Share Center where you can share your passwords and notes with families and friends. And Emergency Access. What happens if you’re incapacitated or die? Well, they have a solution for it here. And then you have account settings here. And there’s lots of options and security options here. And you also have preferences, which is another kind of settings. And you’ve also got more options as well. So there’s settings and options, a preference is a little bit confusing, but there’s more settings in here. And we’re going to go through some of these in a minute.
Auto-Login and Auto-Populate
- When you go to websites for which you have a username and password stored, it can auto-log in or it can auto-populate. You can also get this pop-up as well when you come to sites that you have not already saved the username and password and you can add the details that you enter. So as you go through logging into the sites that you normally log into, you can save those and it pops up with a message asking if you want to save, or simply you can go on here, type the site that you want, click there, and it logs in for you.
Zero-Knowledge System
- It’s a zero-knowledge system, meaning LastPass, the company, cannot find out your master password or view the private data that you have stored in this password manager, even though the data is on their servers. This is because the data is encrypted client-side before it is sent to the servers, so they have zero knowledge of what you are storing.
Encryption and Security
- It uses AES-256-bit encryption as we would want. It’s got salted hashing and it uses PBKDF2SHA256, which we have talked about and you know is good. By default, during the client-side encryption process, as you can see here, 5,000 iterations are used and you can customize a number of iterations as well if you want to, which is great here in account settings and advanced settings.
Multi-Factor Authentication
- It supports a number of multi-factor authentication methods, which you can see here. It’s introduced its own LastPass authenticator. You can use Google Authenticator or the Authy app and we’ll discuss more on this shortly. You’ve got Duo here, and you’ve also got YubiKey and the rest. So actually quite a lot of two-factor authentication and there’s a Salesforce integration which won’t be of interest for home users.
Security Architecture
- The security architecture is well designed. It’s just that it’s an increased attack surface over the other options that we’ve gone through. If your adversary is well-resourced and the consequences are high, I probably wouldn’t use this. I would stick with KeePass, I would stick with something local, not doing cloud sync not integrated into the browser, or maybe use Master Password because we want to decrease the attack surface if the consequences are seriously high and your adversary is well-resourced.
Vulnerabilities and Attack Scenarios
- LastPass and any password manager that uses syncing in the cloud and integrates with the browser are simply more vulnerable to attack. Let’s consider some of the possible attack scenarios here. So phishing and browser hacking. Imagine you click on a link or you visit a site that is hacked, a message pops up looking like LastPass, looking like the login screen because that’s where it pops up in your browser and you’re fooled into entering your master password or a pop-up like this appears. You can get that from visiting a site that’s trying to attack you or clicking on the wrong sort of link. An attacker could try to compromise the LastPass servers, which actually has already successfully happened. I’ll talk more about that in a little bit. A man-in-the-middle attack is viable too where the client, this browser, connects to the attacker instead of the LastPass server and the attacker forwards on the message and the password is relayed in some sort of way. This can defeat two-factor authentication. Also obviously if an attacker is present on your device using something like a keylogger or other such malware, the master password would be compromised.
Acquisition and Security Reputation
- Some other negatives, LastPass was acquired by LogMeIn, and the company will be combining the LastPass brand with a similar product called Meldium, which was also acquired by LogMeIn. LogMeIn doesn’t have a great reputation at all, not for security, so could make LastPass a no thank you pass if they mess about too much with this product. Currently it’s good but LogMeIn don’t mess it up.
Previous hacking and security design
- As I mentioned earlier, the LastPass server has been hacked before. In this incident, the encrypted user vault data was not stolen, but even if the user vaults were stolen, they would be much more resistant to cracking due to hashing, key stretching, and iteration, as long as people have good strong passwords.
The Future of Cloud Password Managers
- Since LastPass is one of the most popular password managers, it is likely to be a major target of attacks. Even though LastPass was successfully hacked, I wouldn’t blame them too much for that, they disclosed the hack in the right way and correctly advised people that due to the secure design, even if the hacker gets the encryption
Configuring LastPass for Enhanced Security
Customizing LastPass
- We can configure LastPass to be more secure than the defaults, because the defaults are a balance between security and usability.
Using the Binary Version
- The first thing is you can use the web version of LastPass. Don’t use it. Use the binary version, the plugin version. This is safer.
Avoid Storing Passwords
- You see here we’ve got “remember password,” “never remember the password,” “never store the password,” get used to typing it in.
- If you store it, it’s an attack vector. If you don’t store it, it’s not an attack vector. Therefore, don’t use a password reminder.
- Remember the password yourself or go old school and write the password down and lock it away somewhere safe that no one will find.
- Preferably when you write it down, don’t put “this is a password” or “that is a password”. Preferably no indicator of what it is.
- With a password manager, there’s only this one password that you need.
- So you simply make it strong and you remember it.
Advanced Settings
- If we go in here, my LastPass vault down to account settings, and we click on show advanced settings.
- We’ve got here reprompt for the LastPass master password. You could enable more granularity here on anything that you think is particularly sensitive.
- For example, if you have particularly sensitive secure notes, then make sure that there is a reprompt for the master password.
- But as a minimum, you want to have it on access and identity.
- You can set up different identities within LastPass.
- And if you’re going to the step of doing that, then there must be a reason for that separation to require a reprompt of the master password.
- Use a security email. This is a second email account for critical account notifications.
- Once you add a new email address here, this means that any sensitive notifications such as those for account recovery or disabling multi-factual authentication will be sent to this security email rather than your primary email address.
- So even if someone gets access to your primary email address, they won’t be able to log in to LastPass if you’ve locked it down with a strong master password, multi-factual authentication, or an obscure security email address, so add one of those in there.
Country Restrictions
- Then we’ve got country restrictions. You want to add a country restriction.
- If you’re not going to be logging in from Afghanistan or China, don’t enable access from there. It reduces the attack surface.
- Not impossible to get around, but still reduces the attack surface.
- Disallow Tor logins if you’re not using it from Tor. These settings should be, as you see here, you want this to be set, and do not set these.
Automatic Logoff
- And then this is optional really, automatically log off other devices when logging in from a different device.
- For me, I sometimes do log in from two devices at the same time, so I don’t check that, but if you don’t, then have this checked.
- Here are the password iterations that we talked about. Now, you want to change this.
- Set this to something between 10,000 to 20,000, a random number between there. That will make it harder to crack your password as they will not know how many iterations it has gone through.
- You’ve got website auto log off. You shouldn’t really be using the website. So you can reduce those down if you wish and uncheck these as you do not want to be sending this information and keeping this information.
- This one, if you’re concerned about local forensics and you never really want to send any data that you don’t know what that data is, are they doing a memory dump or your encryption key be in it? Don’t know. So never send data that you don’t know what it is.
Multi-Factor Authentication
- Here we’ve got the multi-factor authentication options. We are going to talk about multi-factor authentication.
- So you would want to use a multi-factor authentication method. This really mitigates password cracking.
- If you can, you want to use a couple of options in case you lose one, like if you have a hardware dongle and you lose it.
- So you could have a couple of options like UBKey and Google Authenticator here, or Authy. Make sure you have two-factor authentication.
- Two-factor authentication isn’t bulletproof, but is a significant security mitigation against your password being stolen or cracked.
- If you don’t know what two-factor authentication is, we’re going to talk about it in a second. But it simply means providing two factors of authentication, a password and something else.
- Something you know, something you have, something you are, are all authentication methods.
- When you’re setting up two-factor authentication, it will give you the option to trust the device that you are logged into on. So say, for example, you log in via your desktop, you can trust that device for 30 days, then you don’t have to continue doing two-factor authentication. Don’t do that. We’ve got trusted devices and mobile devices.
- You can restrict account access to only specific mobile devices UUIDs. This is helpful if your two-factor authentication method doesn’t work with mobile devices and is just generally a good idea if you know what mobile devices you’re going to be logging in from. So restrict mobile access.
Preferences
- Then if we close that, go here, preferences. You want to automatically log out when all browsers are closed and Firefox has been closed for a number of minutes.
- You really want this set to zero once you close a browser. That’s it. Must log in again.
- And you want to automatically log out when the system’s been idle. You’ve got 15 minutes here. Anywhere from 5 to 15 minutes should be fine.
Advanced Settings
- Let’s go to advanced. You want to disable account recovery. This is a little risky because often you may want to recover your account if you forget your password.
- But it is better if there is no method of recovering your account because you close an attack vector. You simply must remember your master passwords so you do not need to recover it.
- So this needs to be set like it is so that you are not saving a disabled one-time password locally for account recovery.
- And if you are ever prompted for the master password unexpectedly, do not enter it. Always think. Reset the browser. Clear All History. Make sure everything is OK, then log in.
- So that’s LastPass. I do use this myself, plus the others that I’ve gone through for different security domains. It’s a good product from a security perspective, but bear in mind it does have the increased functionality but it does have the increased attack surface.
- There are other password managers like this, but this is my preference from a security and functionality point of view. And in that vein, here’s another one that you could potentially look at. This is Crypto which is another cloud-based password manager. It’s from Spider Oak, and it uses the Zero Knowledge Krypton framework. It looks good on initial impressions, but I haven’t had time to really look at it. It stores passwords, credit card data, pins, etc. in the cloud.
- The Zero Knowledge Krypton framework is a thumbs up from a security point of view, but like I said, I’ve not really looked into it in depth so that’s a potential option as well. And for completeness, other options are available that you could explore. Let me know your experiences with these.
Creating and Remembering Strong Passwords
Utilizing a Password Manager
- We’re going to go through now how to create a strong password and a strong password that you can remember. But first, whenever possible, you should use a password manager to generate and store your passwords.
- This way they can be long, complex passwords that you don’t need to remember, and they don’t get reused.
LastPass Password Generator
- Here you can see the LastPass password generator. You want to use these to generate truly random passwords.
- The longer, the more complex, the better if the manager is storing it anyway for you.
- The length and complexity of the password will be limited by the site and services that you use as to how long it is and what characters that you can use.
- Some sites may only allow you to have, say, 12 characters and no special characters can be used, but nowadays you’ll find at the good sites you can enter in really, really long passwords with all sorts of characters and it handles it just fine. Make sure the password generator creates passwords that are a minimum, minimum of 12 characters. But what I recommend is 43 plus randomly generated characters that contain upper and lower case letters, numbers and symbols.
- Personally, because the password manager is storing them and if the site or service allows it, I use 43 characters on sites that I care about and that allow it.
Password Manager’s Advantages
- When you use a password manager, and when it works smoothly for the site or service it makes no difference if it’s a 4 character password or a 43 character password. In terms of any burden to you, you simply click on the same things anyway, and it is much, much more beneficial for it to be a long password.
- When it comes to disk encryption, whole disk encryption, file encryption, the password manager’s master password and anything that you really, really care about and you do not want to be decrypted if you are protecting something that is 256-bit encryption, which is strong enough in most cases and you want the optimal size password, a 43-character password or more, is best.
- If you’re going to step down your encryption to 128 bits, then 22 character passwords are fine or plus.
- If you’re going to really step it up to 512 bit encryption, then 86 character passwords are best.
- This provides optimal input for the encryption.
Creating Memorable Strong Passwords
- I appreciate this won’t always be practical, but we’re talking here about maximum security here for disk encryption, master passwords, things that you really, really care about.
- The sort of passwords that you don’t have very many of.
- But don’t worry, we’re going to talk how we can create these passwords and remember these passwords even when we can’t use a password manager.
- Like for example, the master password for the password manager.
- How do we create long, complex passwords that we can actually remember?
Three Properties of Passwords
- There are three properties to consider when creating a password.
- There is the difficulty to crack the password.
- There is the difficulty to remember the password, very important.
- And also important is how fast you can type the password.
- Because if you create a complex password where the keystrokes are difficult to make, it just becomes annoying to type in.
- So you also want a password that you can type in fast so you don’t mind using it.
Avoiding Patterns
- The difficulty to crack a password is based on its entropy and randomness away from human patterns. Let’s first talk through what you should avoid doing when creating a password.
- And the first thing you want to avoid doing is using patterns, especially if the password is short. If it’s below 20 characters, you should not be using patterns and especially not the obvious patterns. And what you can see here are the top obvious human patterns that are used in passwords. And you can see why, because they are easy to type on the keyboard. QWERTY, QWERTY UIOP, etc. These will be in every cracking dictionary just like a word. So it must be avoided and especially avoided with passwords that are than 20 characters.
- If you have a look at this site, you can see more of them. But to make sure you aren’t using common human patterns, we can use a couple of tools. Here’s one. This is credit to Dan Wheeler for creating this one. So let’s put in a sample password in here. There we go. Dog Rabbit House. And then if we look down here, we can see an analysis of it. We’ve got throttled online attack, un-throttled online attack, offline with a slow hash, offline with a fast hash. So if it’s something that we really care about like disk encryption, master passwords, then we need to be thinking about offline attacks.
- But if we’re using a good system, like the ones I’ve gone through, then they have slow hashes anyway. Websites that you use is no guarantee that they’ll be using a slow hash. They could be using a fast hash.
- So you can see here the patterns that we’ve got here, dog, rabbit, house, all in the dictionary. So it will literally take seconds or a few hours with a slow hash to crack that.
- So it shouldn’t be just a combination of words like this.
- You don’t want to use common short phrases either, as these are common patterns that humans create.
- And even if you have a capital at the front there, it’s still less than a few seconds.
- It should not contain a date, a name, or things that are associated with you.
- All dates are common patterns, and if they’re within your password, will be easily cracked.
- Even if we add a little bit more to this, it still can be unacceptably cracked.
- Add a little bit more.
- Again, we’re adding patterns here.
- And still, with fast hashes, can be cracked, even though it’s getting to become quite a long password here, and we’ve got a mix of characters.
- And another one that looks like it could be complex, but because it contains patterns spiderman, qwerty, 12345, and the symbols on the top of the keyboard, it can be cracked.
- These numbers here, by the way, with a really good implementation of key stretching and iterations, this number would go up here.
- This, of course, is just a rough estimate on the very many variations that there could be.
- If the password is short, less than 20 characters, try not to have capital letters that come at the beginning and have lowercase letters that come in the middle and then numbers and symbols that come at the end.
- This is a known pattern for how humans create passwords.
- This matters less when your passwords are longer than 20 characters, but when they’re less than 20 characters, you want to avoid this common pattern of uppercase, lowercase, number or symbol.
- Also, try to avoid LeetSpeak, where you change an E into a 3, for example, or an O into a 0.
- Again, if your password is less than 20 characters I’m talking about here, when they get longer, greater than 20 characters, it doesn’t matter so much.
- and I find that LeetSpeak also makes it harder to remember the password.
- So it’s better to simply have a longer password that allows you to still use English normally is easier to remember, and harder to crack.
- An example here of using the patterns, it’s a short password and we’re using the patterns here of uppercase and lowercase.
- Still crackable with a fast hash.
- Now, if we change this, and instead of having our uppercase at the beginning, we have our uppercase at the end of the words, see the difference it makes.
- This is not really what you want to do, it’s still too short.
- This is only if you’re forced into using short passwords, then you have to avoid these patterns.
- And this is another site that does very similar things, checks for patterns, but it has more patterns that it can actually find.
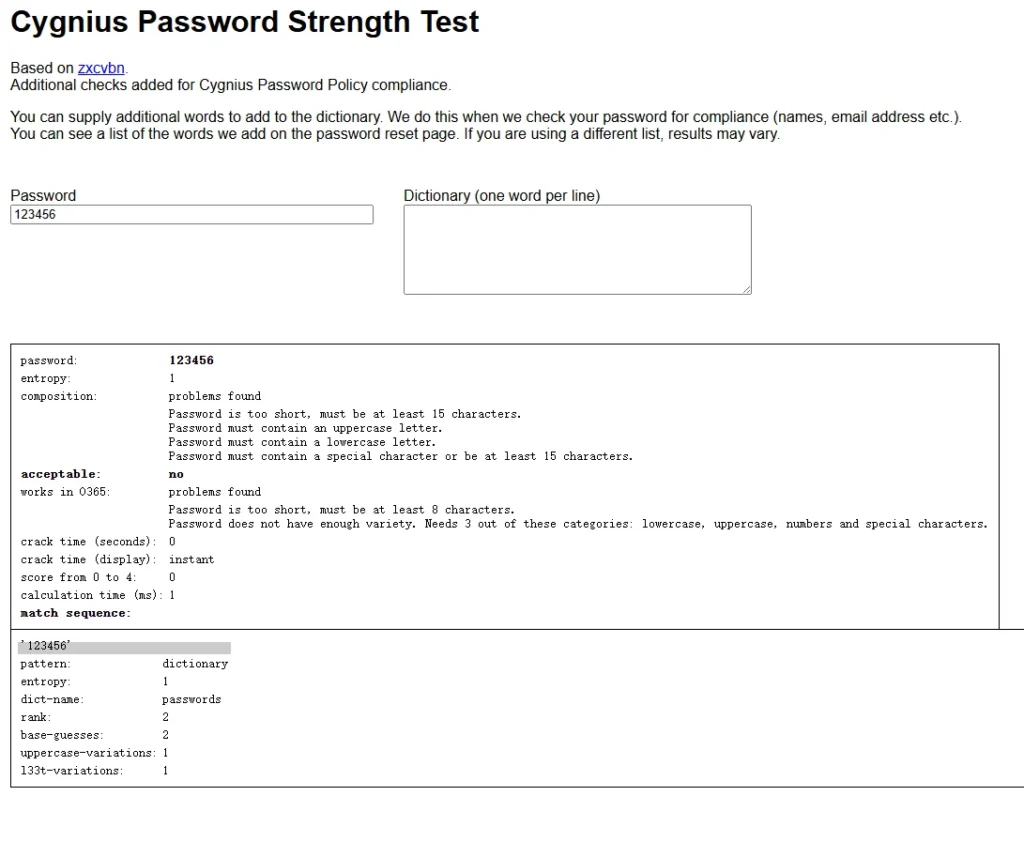
- So let’s put in password here. And instead of talking about cracking it gives you advice on a policy for how you should set up your passwords like it’s got no upper and lower case, etc. And you can see about the patterns and of course, it’s got examples here as well. So you can try this one as well.
Moving Away from Passwords
- So we’ve talked about what we shouldn’t do when creating a password. Now let’s talk about what we should do when creating passwords, so that they are memorable and strong.
- The first thing is, we want to move away from passwords. We want to be using pass phrases or sentences to increase the length, entropy, and randomness of the password.
Using a Base Phrase
- And when creating a passphrase, I recommend you use a base phrase to start with. Think about poems, lyrics, movie dialogue, songs, things that you know and can easily remember.
- Something memorable to you, but not ridiculously obvious.
Adding Randomness
- Here you can see in front of you this is a brute force password search space calculator by Steve Gibson.
- So what do we have here?
- The sun never sets on the British Empire. Press return there.
- We’ve got 42 characters. It’s a phrase. We’ve got uppercase characters, we’ve got lowercase characters, we’re missing digits.
- So we want to use whatever phrase you come up with as your base phrase and then you need to add randomness to it.
- You might want to put it in quotes or put it in brackets or put numbers at the side of it.
- Maybe change the spaces to another character, but spaces are good. Spaces can be used.
- If they can’t be used, you can put something else in there. You need to develop your own method.
Adding Complexity
- And we can see here we’ve got no digit. And because this is a long password, we can use LeetSpeak.
- So we could change that for a zero. And now we have a pretty easy to remember password.
- We’ve got the upper and lowercase letters in a position that is easy to remember. But because it’s long enough, patterns aren’t that relevant.
Using Foreign Languages
- So here’s another one. You miss 100% of the shots you don’t take. That gives us our uppercase, lowercase, gives us our digits, and it gives us our symbols.
- Every time we add a different alphabet, it essentially gives us that whole new alphabet of characters that could possibly be in here.
- And you can see this represented as search space depth, where we’ve got 26 plus 26 plus 10 plus 33.
Adding Padding
- Once the password is random enough but memorable, say like this one, you can also add padding of your own design.
- So maybe you add something at the end a total number of characters.
- Maybe you add one, two, three, four, five, six, seven, eight, nine, ten. That’s what I call padding.
- It does not matter now that this is a pattern because of the length of your password.
- For your padding, you can also add something that relates to where the password is being used.
- And whatever method you use absolutely do not tell anybody when you add a reference to the service if it does ever get cracked then you know which site got hacked and as I said it doesn’t matter if these are patterns now because by this stage the password should be very complex and long anyway before you’re adding the padding.
Typing Speed Considerations
- Also important is to think about how easy it will be to type this in and on all your manager master password and you’ve got to type it in on your mobile phone and you’re using symbols and lots of them that are three menus down on your keyboard, that’s going to be a total pain. You need to use characters that are fast for you to type. So you need to try it out and then change the password, tweak it until it’s one that you can type fast, remember, and is complex. Otherwise it will become just annoying to use that long password and you may change it to something simple. So maybe you realize that this part of your password is no good for speed so you just change it for easier padding instead. But hopefully you won’t need many of these self-generated passwords like these because you’re reusing a password manager.
General Tips
- There should only be a few passwords that you need to remember.
- And I’ll finish off now by giving you some general tips about passwords. So always change default passwords. Maybe your router has a default password. Applications of default passwords must change those, especially if they give access to any sort of administrative function.
- Don’t worry about changing your passwords frequently. It’s much, much better to create long, strong passwords that you can remember than to keep changing passwords that you don’t remember. But do change your password if somewhere gets hacked. Even if they say it wasn’t breached if you care about that service, then change the password.
- Don’t tell anyone your passwords, pretty obvious or the methods, like we’ve gone through here maybe you always add ones at the end for padding don’t tell people those methods.
- And don’t write down your passwords unless they are securely locked away somewhere.
- And then there’s a problem of security questions.
- Security questions like what is your mother’s maiden name? What was your first pet? These are highly dangerous.
- Many of the answers can be found out by using an internet search or simply by guessing.
- I worked on a banking system that will remain nameless, whose security reset question to reset the password was, what is your favorite color? I mean, come on, we know the most popular colors in the world. We know that blue is popular. We know that red is. We know that green is.
- Plus, this system allows you to try as many times as you like. So you don’t need to crack the password. You’re cracking the security question.
- The security question is effectively exactly the same as the password in this case. And in this case, it meant anyone’s account was accessible.
- I had to get that emergency changed once I spotted it.
- The point being, these security questions need to be as secure as the password. So don’t use security questions if you can avoid it.
- If you do have to enter a security answer to a security question then use another strong password and just store the question and answer in your password manager so you know how to respond to it.
- If you just have your mother’s maiden name as Smith that’s just the same as having Smith as a password which is terrible. If you want to be super cryptic and have a very very sensitive password that you store in your password manager, you can split it up and make it non-obvious what it is, just in case someone does crack your password manager.
- Use an email address that you trust is secure. If your email provider is hacked, all your passwords associated with it could also be too. Your email account is often a single point of security failure.
- You should consider changing usernames that give information away, because that isn’t necessarily a good idea. So, for example, if you have something like admin or root you might think about changing those.
- When it comes to your passwords, prioritize the accounts that are most important to you. And make sure they have the strongest passwords and or multi-factor authentication. Forget about the things that you don’t care about. Prioritize the accounts and things that you do care about.
- If it’s possible with the services that you use, set up notifications and alerts. So for example, you get sent an email when your account is accessed or funds are transferred.
- Set up notifications if you can.
- If possible, set a lockout after a given number of failed attempts and then that maybe resets itself, say, after 10 minutes. This will delay someone being able to try and crack a system online.
- And remember, always remember keep a backup of your password manager’s database.
Comprehensive List of Unique Password Suggestions
Cygnius Password Strength Test
GRC’s | Password Haystacks: How Well Hidden is Your Needle?
Multi-Factor Authentication – Soft Tokens – Google Authenticator and Authy
Principles of Multi-Factor Authentication
- Multi-factor authentication is a method of assigning access to a system based on presenting more than one piece of evidence to an authenticating system.
- For example, ATMs in the UK and many countries require both a PIN number and a bank card in order to access the ATM.
- Both the PIN and the bank card are required for authentication, that is multi-factor authentication.
- Enabling multi-factor authentication on a service makes it harder for an attacker to fraudulently authenticate as you.
- It mitigates things like identity theft, the stealing of money from your accounts, accessing your email, mitigates the cracking of your passwords, and is generally just a good idea.
Types of Authentication Factors
- As you can see here, there are three types of possible authentication factors.
- First being something that you know, also called authentication by knowledge, what you’ll be most familiar with using, passwords, PINs, passphrases.
- Then you have something you have, this is authentication by ownership, things like ID badges, smart cards, your credit card’s chip, your credit card’s magnetic strip, a soft token like Google Authenticator, a hardware token like YubiKey or NitroKey, an SMS or text message or email that’s sent to your phone, or even a phone call verification.
- And then finally, you have something that a person is, which is authentication by characteristic. So retina scans, thumb scans, biometric, probably most commonly associated with the iPhone thumb scanner. That is, something a person is, an authentication by characteristic.
Multi-Factor Authentication vs. Two-Factor Authentication
- Using these three possible methods, this is called multi-factor authentication. But when only two factors are used, this can also be referred to as two-factor authentication (2FA), or more recently, two-step verification, which is a term I think they’re now using just to make it simpler for people to understand.
Time-Based One-Time Password (TOTP)
- Let’s delve into some of the technology we can use to enable multi-factor authentication.
- The original time-based one-time password (TOTP) soft token was Google Authenticator, which you can see here.
- It’s available on Android, iPhone, and also BlackBerry, plus many third-party implementations.
- This is known as a soft token because the “something you have” part of the password is generated in the software.
- You can see the blue number there, that is the extra password, the one-time password, the second factor of authentication.
- Google Authenticator supports OAuth, which is the initiative for open authentication.
- It supports this standard here, which is the TOTP, time-based one-time password algorithm.
- If a site or service conforms to OTP, it means it will work with Google Authenticator as a second factor of authentication, and in fact it will work with any other soft token or hard token that supports OTP.
- OTP is adopted by many sites and services, and Google Authenticator is actually just one example of an implementation of an OTP client.
- Many sites will say they support Google Authenticator, but what they mean is they support OTP and any other client that supports OTP as well.
- So as I said, it is a time-based, one-time password, a dynamic password.
- Once you register with a site or service and your client and the server become in sync based on time, you can then use this password as your second factor of authentication.
- And it can be used once and for a limited time period.
- You can see the clock ticking down there. That’s as long as the password is available.
- Let me give you an example of how you can set up Google Authenticator for second factor authentication.
- I’ll do that using LastPass as the example.
- We go into LastPass for the demo.
- We go to the My LastPass Vault, Account Settings, and Multi-Factor Authentication.
- Here we can see it as Google Authenticator.
- With whatever service you are trying to use the authenticator with, it will have something similar to this.
- The easiest option is to see the QR code, or as it calls it here, the barcode.
- So if I click on View here, it’s going to prompt me for my password, it shows me the QR code.
- Now what I need to do is I need to go into my app here, I need to click on the plus and then I need to click on Scan Barcode, and then let’s scan it in.
- And there we are, it’s added.
- You can see reg at offsce dot net, which is the account that I’ve got.
- So there you go.
- It can literally be as simple as that.
- When you’re using a device where you cannot use a barcode, you can also view the key.
- You can see the key there.
- And on here, it would be plus, and that would be manual entry.
- And we’d have to enter the key in here, and close that.
- So let’s enable this.
- It’s asking me for my current verification code. This is to make sure that the sync is working. So we can see there it’s four, two, three, two, six, nine.
- Okay. Settings have been successfully updated. So that’s great. So you can see it’s enabled, you’ll be able to see something like that in your applications, whichever ones you try to add this to.
- Let’s log out and then let’s log in.
- We are prompted with this authentication, this second factor of authentication. So let’s enter 541-925. We don’t want to trust this computer if we’re looking for maximum security, authenticate and there we are. We have logged in. So that’s an example of time-based passwords, and in this particular example we’re using Google Authenticator. This is OTP, and it’s also called a disconnected token because you manually type in that extra factor.
- Instead of using Google Authenticator, I actually recommend something called Authy, which is available here at this link. It is available on all the major phones and desktops. It uses the same one-time password standard OTP, so it will work with any service that reports to be compatible with Google Authenticator or OTP, like I just showed you with LastPass.
- With Authy, instead of just using Google Authenticator, you just use Authy and you can see the screen here. You would just scan in with Authy instead or enter the private key, just the same as we did with Google Authenticator, just a different app. But we use Authy because Authy is better. We use Authy because you have the ability to lock the app with a PIN or touch ID to prevent people accessing the app, which you really want and need, which you don’t get with Google, unfortunately.
- Additionally, it also has the ability to sync to the cloud and between devices. It uses client-side encryption to do this. Your tokens are then in the cloud so it is a little risky, although they are encrypted but that is a feature you can use.
- I personally don’t bother to sync in the cloud and just sync my devices manually. There’s nothing stopping you doing that. You just scan that QR code in with device one and device two and then you’ve got two devices for backup which gets on to the next point, what happens if you lose your phone or the device that you have that has this second factor? Well, you can’t log in. That’s a problem. Some services will provide you with a recovery option like LastPass has, it has its SMS, it has its one-time passwords.
- Some services will send you an email, but these are less secure. Remember that the recovery method determines the strength of this authentication. If the recovery method is weak, then the second factor of authentication is weak also. I tend not to use recovery options. If the risks are high, you shouldn’t use recovery options. If you can, you want to disable them and just simply don’t mess up. The best way to not mess up is to have Authy set up on multiple devices, or whatever second factor you’re using. And as I said, the same QR code or key is used on all those devices. So you’ll see the same one-time password on each of the things that you use. And that is what the desktop version looks like. This is a Chrome extension for the desktop. If you want to use a desktop or maybe you don’t have another mobile device as a backup, you can back it up on your desktop. But you must must have multiple devices with your second token on or you could forever be locked out of your accounts. So I’ve just shown you Google Authenticator and Authy as OTP soft tokens.
- But as you can see from this list here, Android, iOS, Windows Phone, BlackBerry, these are all other OTP soft tokens that you can investigate and use.
- Moving away from soft tokens now, you can, as a second factor, or part of multi-factor have SMS or email that is sent to your phone or other device that you can use as a second factor of authentication.
- And you may have used this method to authenticate previously already on various services that you have used.
Multi-Factor Authentication – Hard Tokens – 2FA Dongles
Hard Token Manufacturers
- So we’ve just talked about soft tokens. Now we’re going to talk about hard tokens.
- What you can see here is a list of hard token manufacturers. And these are also called two-factor auth or two-FA tokens. You’ll notice they’re offering two types here. And you may recognize OTP, one-time passwords, which we were just previously talking about, and we’re talking about our soft tokens, Google Authenticator, Authy.
- They were OTP soft tokens.
- They were implementing this standard, the OAuth standard.
- These hard tokens are also implementing OTP, but just in hardware.
Universal Second Factor U2F
- Then we’ve got this.
- This is an open authentication standard.
- It was initially developed by Google and Ubico and it is known as a FIDO standard.
- So if you see FIDO, F-I-D-O anywhere, it means it supports these hard tokens here.
- The soft tokens, as I said, these are disconnected tokens, but these hard tokens are connected tokens.
- So let me show you an example of how they work and you can see how they are connected tokens.
- Let’s look at Ubico here.
- One of the Yubico is this one. This is a YubiKey 4.
- This is going to give us our second factor, our second password.
- So again, I’m going to use LastPass as the example application, but other applications will work in the same way.
- You just need to find the same settings with those particular services.
- Let’s go into LastPass, Vault.
- Of course, we need to set up the fact that it will use YubiKey as its second factor of authentication.
- If we go down to the bottom here, here we go, we can see YubiCo, so we would enable this.
- But actually, in this example, YubiCo or YubiKey only works with the premium LastPass.
- So we would enable this, and then we would log in.
- We get our prompt for our second factor, for YubiKey.
- We need to insert the YubiKey into the USB, and then we need to press the Y, the button that’s on it, and this will auto-generate, as you can see, the authentication, and it will log us in.
- That is a connected token.
- No copy and paste was required.
- If we see here, we’ve got the YubiKey for nano, so these hard tokens can work in different ways. This one supports, for example, NFC for Android phones. So you can swipe this near your phone to get your second factor of authentication without actually needing to plug it in because it supports NFC, which is pretty cool. This doesn’t work on iPhones though yet because Apple doesn’t support the Fido standard.
Details of Hard Tokens
- If you want to know more about YubiKey in particular and LastPass, there is a video here that I would recommend. Let’s have a look at these tokens in a little bit more detail so we can see what we might be buying. So here in the example we’ve got Yubikey 4.
- If we go a little bit further down we can see here what it’s offering. Secure static passwords. That means it’s just going to generate a static password for you. It’s not two-factor authentication but it might be useful for something. Yubikey’s own one-time password. So that would be compatible with any service that is compatible with it. And then we’ve got down to the ones that we know are more universally compatible.
- Now I mentioned before the time-based one-time passwords. That’s what Authy, Google Authenticator use.
- But another form of one-time password is an event-driven one-time password. So some sites and services that support OTP will also support this method as well.
- And that’s actually a HMAC-based one-time password. H for HMAC and T here, time-based one-time password.
- And then here, there’s the Fido U2F.
- And the Ubico keys support U2F because Ubico is one of the companies that helped create it along with Google.
- If we go down here, you’ll see that they’re promoting sites that do support it. Google, GitHub, Dropbox, etc.
- Let’s go to NitroKey.
- You can see with NitroKey they have one that supports U2F and the rest of them actually don’t support it.
- And then if we scroll down, you can see these two support OTP. Those are going to work with any of the OTP services.
- There’s a universal two factor, just that one.
- And we can see here the sort of prices you need to pay. About 50 euros there. About 40 dollars. 40 dollars.
- It’s that sort of range of price for the hardware-based second factor authentication tokens.
- Now, Universal Two-Factor, the FIDO standard, is actually more secure than OTP, one-time password.
- But both are much, much better than single-factor authentication.
- If you want to know the technical detail, give this a read, it explains the differences.
- But also, one-time password is more widely adopted.
- When it comes to businesses and business users, often they use these things here, RSA tokens which are RSA proprietary. They have hardware tokens like you can see here. They also have software token versions. They have connected and disconnected versions.
- To use these, you would need an RSA server in your business to use these. And they are used in many, many big businesses, especially for remote access into the office.
- But it’s the same principle, you can see there, that’s a time-based, one-time password.
Choosing a Method of Multi-Factor Authentication
Selecting the Right Method
- So how do you choose a method of second factor authentication? Should you use soft tokens? Should you use hard tokens? Should you use a combination of both? Should you be looking for using OTP, U2F? Do you want to use Authy, or do you want to use Ubiqui, or SMS? Well actually you don’t have the choice, because second factor authentication is only available on a limited number of sites and services. So you’ll be choosing a soft token or hard token based on what sites and services you use, and if you come to this site here, very very good, twofactorauth, and you put in the sites that you use. So let’s try one.
- So there we go, LinkedIn. Only does SMS. So you just need a phone. Pretty poor of LinkedIn.
- Let’s try another one. Facebook. It does SMS, and it also does soft token. But that doesn’t tell us which soft token, it’s likely to be Google Authenticator and OTP, because that’s the common one that everyone uses.
- So with Facebook it’s Authy, Google Authenticator, and potentially an OTP hard token.
Soft vs. Hard Tokens
- Soft tokens are obviously free, or mostly free, sometimes you pay extra for extra features like backup, hardware tokens obviously you need to pay for. With hardware tokens they automatically fill in your passwords so that’s an advantage. With a soft token you do have to enter in a PIN, in most cases at least you enter that into the phone or your desktop so that provides some sort of protection. With some hard tokens you just put it in the USB and press the button so there’s pros and cons to both.
Personal Preferences
- And if you look here this is another place to work out what supports Google Authenticator or OTP or Authy and OpenVPN and OpenSSH support the Authenticator, so great if you can get that running.
- And if you’re back on hard tokens here, sites like Google, GitHub, Dropbox, these all support hard tokens as well as LastPass and many password managers, but check out these sites I’ve shown you.
- Personally, I like Authy as a soft token and YubiKey 4 if you have an iPhone and YubiKey Neo if you have an Android for the NFC.
- If you’re using Lux for your full disk encryption, you can use YubiKey to create two-factor authentication for hard disk encryption
GitHub – cornelinux/yubikey-luks: Two factor authentication for harddisk encryption
Rublon Multi-Factor Authentication (MFA) – Secure Remote Access
Limitations of Multi-Factor Authentication
Enhancing Security
- Enabling multi-factor authentication on a service makes it harder for an attacker to fraudulently authenticate as you and crack your passwords.
Imperfection
- An attacker could gain access to another factor by, for example, and this has and does happen, especially with banking trojans, by hacking a phone.
- Some banking services send an SMS to the phone as that second factor.
- Hackers know this and therefore they have set systems up in order to hack phones in order to receive those SMSes and those second factors. This is a common method.
- Attackers could also hack the phone network to receive the SMS.
Advantages of Hardware Tokens
- With hardware tokens, there isn’t the same attack surface.
- The hardware tokens aren’t on an operating system that can have malware on it.
Other Attack Vectors
- But multi-factor authentication is still vulnerable to phishing, man-in-the-browser attacks, and man-in-the-middle attacks, even if you’re using one-time passwords. People don’t often seem to realize this. Let me give you an example. A man-in-the-middle attacker can receive the password and one-time password because they’re in the middle and relay them onto the destination providing the attacker with access. Then the attacker might be able to change how authentication is done, returning it back to a single form, providing them with permanent access. But if they can’t change it, they still have an active hacked session because of that man in the middle relaying of the password and one-time password.
Despite the additional security layer provided by multi-factor authentication, it is not foolproof. Attackers still have multiple methods to circumvent these measures, especially if they can exploit the phone network or phishing attacks to obtain users’ second factors. Therefore, in addition to using multi-factor authentication, users should take other security measures, such as keeping software up to date
The Future of Passwords
The End of Passwords
- But what does the future hold for passwords? Well, the future of passwords will actually hopefully be no passwords at all. The reasons passwords are still around after such a long time is because they are easy for users to understand now, because they’ve been trained in passwords, and they’re easy to implement and code and cheap. But passwords will slowly, slowly, slowly fade away and be replaced. And what you see here in front of you is something called Squirrel, which is one possible future for passwords.
- Here you can see this QR code.
- And with lots of clever encryption and authentication, you would scan this in with your phone and then you would be logged into the site or system that you want to log into.
- And there is no password stored and it’s much more secure than passwords.
- Essentially an entire alternative to passwords.
- And Squirrel actually looks pretty good.
- It’s all just a case of whether it gets adopted, or maybe something else, and this is by Steve Gibson.
Another Possible Alternative
- And another possible feature, similar in its look to Squirrel, is Clef here.
- And again you can see they’re scanning in, not a QR code, but something similar to that with their phone, and then they’re logged into their website or their service.
Conclusion
This article delves into the significance of password security, covering the use of passwords, multi-factor authentication (MFA) with soft and hard tokens, employing top password managers, and mitigating password cracking through enhanced hashing and key expansion techniques, as well as selecting strong passwords.
It emphasizes the importance of disabling password sharing, directory browsing, and leveraging password managers for improved security. The article also discusses MFA types, implementation, and their role in bolstering account security, acknowledging MFA’s imperfections and potential future password alternatives.


